The modern workplace has expanded beyond email. Attackers now exploit collaboration tools, supplier relationships and human trust to bypass defences and compromise accounts. This five-part blog series raises awareness about these shifting attack tactics. And it introduces our holistic approach to protecting users.
In our previous posts, we covered how one determined attacker thrives in today’s evolving digital workplace and why platforms like Microsoft Teams, Slack and Zoom are the new frontline for cyberattacks. In this instalment, we’ll dig deeper into how attackers compromise trusted business communications and what you can do to better protect your organisation.
Manipulating people with impersonation
Trust is a fundamental aspect of how people communicate and make decisions. Whether they’re interacting in personal relationships, businesses relationships or even making purchases online, trust is what makes everything work. Unfortunately, cybercriminals know this, which is why they have mastered the art of manipulating it. They know that if they can make people trust them, then they can execute their attacks with alarming success.
A common way attackers exploit trust is through business communications. Attackers regularly pretend to be executives, human resources (HR) personnel, partners, institutions and brands. When recipients believe they’re communicating with a person or a brand that’s legitimate, they’ll willingly share sensitive information, download malware or authorise fraudulent transactions.
Below are some of their key impersonation tactics. When you know how attackers exploit trust, you can better protect your organisation.
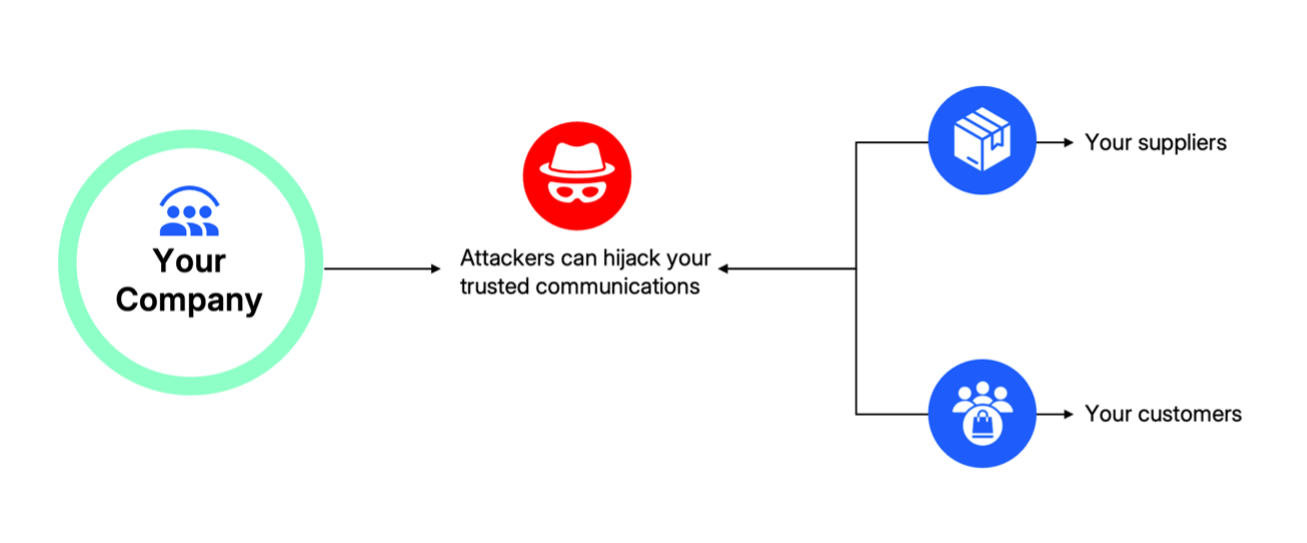
Attackers injecting themselves into business communications using impersonation.
Using unprotected domains for email spoofing
Email spoofing is when an attacker forges a sending address so that a message looks like it’s being sent by a legitimate company, institution or person. Recently, Proofpoint researchers found that active domains that were unprotected sent an average of 44,000 unauthorised messages—per domain, per month.
Unprotected domains and email spoofing are used by bad actors to initiate attacks like phishing, malware, ransomware and business email compromise (BEC).
Here is a closer look at these strategies:
- Phishing attacks. A bad actor sends a spoofed email, pretending to be from a legitimate source like a bank, government agency or a known company. Their aim is to get the recipient to reveal sensitive information, like login credentials, financial information or personal data.
- Malware. Spoofed email can contain malicious attachments or links. When a user clicks on them, they trigger the delivery of viruses, ransomware, spyware or other types of malicious software. These tools help attackers steal data, disrupt operations or take control of systems.
- BEC. Many threat actors use spoofed email to trick employees, partners or customers into transferring money or giving up sensitive information. It can be a lucrative endeavour. Consider a recent report from the FBI’s Internet Crime Complaint Center, which notes that losses from BEC attacks in 2023 alone were about $2.9 billion.
Exploiting trust through lookalike domains
Another tactic used by bad actors to exploit trust is through lookalike domains. Lookalike domains are deceptive domain names crafted to closely resemble legitimate ones. They’re then used in the same type of attacks as spoofed domains.
|
Misspellings |
Character substitutions |
Adding/subtracting characters |
|
Attackers register domains with minor typos that closely resemble real ones |
Bad actors exploit characters that look similar in different alphabets or use numbers instead of letters |
Attackers add or subtract subtle characters to the domain name |
|
Example: |
Example: |
Example: |
Common lookalike tactics.
Even though these domains are not actually owned or associated with the legitimate company, they can still cause a loss of trust. To guard against these attacks, your employees should be educated in how to spot them. But that’s only one important step. You’ll be in a stronger position if you actively monitor for these lookalikes. You should also have a process to gather evidence about them so you can work towards getting them shut down altogether.
Compromising supplier accounts to exploit trusted business relations
Threat actors take advantage of established financial relationships between businesses and their suppliers. It’s common for suppliers to discuss terms or payments via email. If a bad actor can insert themselves at the right point in an email exchange or strike up an email conversation while impersonating someone, they can increase their odds of stealing payments or goods. This is especially true if they’re communicating from a legitimate account that’s been compromised.
Cybercriminals use compromised partner and supplier accounts for BEC, phishing and malware attacks. Security teams typically can’t see which supplier accounts have been compromised. Instead, they often rely on their partners to notify them that they’ve been compromised. This can delay investigations, which are highly manual and time-consuming. A better approach is to use an advanced solution that can spot user behavioural changes and combine these insights with threat data. Automated detection and prevention can also streamline workflows and save on costs.
Conclusion
Trust is a critical part of business communications. That’s why it needs to be protected. By recognising the tactics cybercriminals use to exploit trust, you can take proactive steps to ensure your people don’t fall victim to these deceptive schemes. Your best defence against trust-based cyberattacks is a holistic approach addressing the entire attack surface, not just email.
Protect your people with human-centric security
As digital workspaces expand, attackers continue to target people. While email remains the primary threat vector, cybercriminals are exploiting new channels, like messaging collaboration platforms, cloud apps and file-sharing services. This has created a fragmented security landscape with disconnected point products, resulting in higher operational costs and increasing security gaps. This is where Proofpoint can help.
Proofpoint Prime Threat Protection provides a single, comprehensive solution to defend against all human-centric threats, both current and emerging. It combines a wide range of security protections to help you maximise threat prevention. It features:
- Accurate threat detection—Prevents the widest variety of threats
- AI-powered account protection—Defends against account takeovers and compromised supplier accounts
- Risk-based targeted training—Guides users to make safer choices when faced with threats
- Phishing protection across platforms—Blocks malicious links from multiple platforms
- Impersonation protection—Protects your brand reputation from being abused
- Human-risk management—Identifies high-risk users and automates adaptive security controls
With Proofpoint Prime, you can better protect your people and business by reducing alert fatigue with highly accurate threat detection, improved efficiency through detailed risk insights and automated security workflows. Combined with pre-built integrations and shared threat intelligence, your security and IT teams can accelerate deployments while reducing costs by eliminating fragmented point solutions across your organisation.
Learn more about Proofpoint Prime.
Stay tuned to learn more
In our next blog, we’ll explore social engineering at scale—and why security awareness must evolve.
Read our Expanding Attack Surface series
Learn more about the threat landscape and get insights into how to stop evolving attacks:

