Regulatory compliance, while often seen as a demanding and oppressive task forced upon an organisation, can have many benefits. Regulation on data storage and security is in place not just to protect the customer but to safeguard the organisation from information breaches.
In the United States, the Sarbanes-Oxley Act (SOX) and Payment Card Industry Data Security Standards (PCI DSS) are the two most prominent examples of measures put in place to protect organisational data. Adherence to these policies could create a strain on resources and may feel like a secondary process for organisations that have their own security standards in place.
A recent IS Decisions survey yielded some pretty dismal results in the compliance department. Perhaps, the most disheartening result of the survey is the finding that 57% of U.S. respondents “don’t know” whether they are compliant with SOX or not. The participants in this survey were the people largely in charge of making IT decisions at their respective companies.
Compliance can seem like an arduous process. Let’s break down the two big regulations we just mentioned:
Sarbanes-Oxley Act (SOX)
The US Senate’s 2002 act is federal law relating to standards for public company boards and accounting firms. It closely relates to insider threats in its strict terms around the reporting it requires, and how unauthorised users must not be able to modify these reports, as well as granular requirements for internal controls of financial reports. Firms must be wary of insiders taking advantage of their access to financial records and accounts.
SOX is designed to ensure both the accuracy of financial data and to combat fraudulent activity in reporting. It is applicable to all public companies and very specifically addresses an area among the greatest security challenges to larger organisations: insider threats.
To be fair, most U.S. organisations are not publicly-listed entities, so IT staffs can be excused from meeting SOX compliance on a legal level. However, even if the federal law does not explicitly place restrictions on your organisation, it’s very telling when an organisation does not even consider its implementation.
Payment Card Industry Data Security Standards (PCI DSS)
A set of requirements laid out by the PCI Security Standards Council, which is made up of the world’s main payment card brands, PCI DSS applies to any business taking card payments. It relates to the protection of cardholder data, and has specific IT security requirements for firewalls around that data, password protection, network access restriction at a user-level as well as access tracking and monitoring.
PCI DSS is another security standard that legally applies to plenty more businesses than it is actually being applied to. This international regulatory standard focuses on best practices for securely storing, processing, and protecting credit card information. The regulation applies to all businesses that accept credit and debit card payments, yet two out of three of the IT professionals surveyed aren’t sure if their organisation meets the standards of PCI DSS compliance.
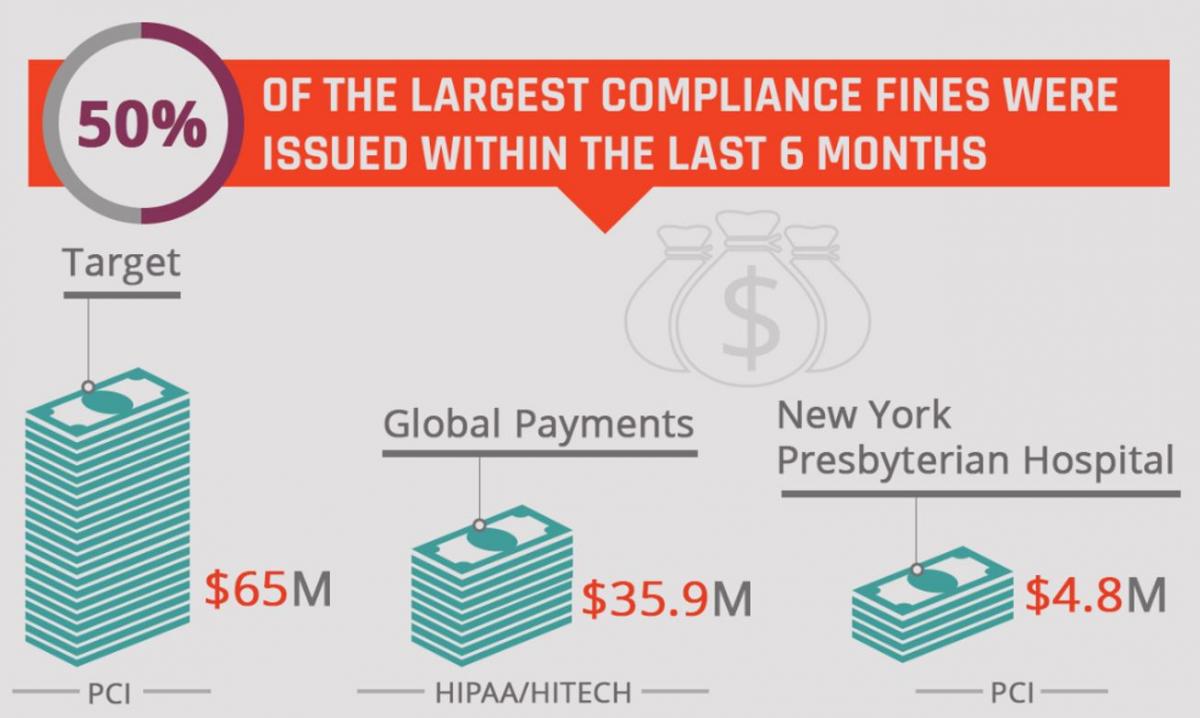
The situation at Target represented a slightly different occurrence, yet one that isn’t entirely rare. Target was not only deemed PCI DSS compliant prior to their well-publicised security breach, but they were approved as such by Trustwave, an independent security firm. Yet, after the attacks levied on the retail giant became public, a lawsuit was filed against both Target and Trustwave. The lawsuit alleged that auditors noticed some warning signs in Target’s security, including a lack of network segmentation between card data and the rest of the corporate network, yet gave the retailer a passing grade.
The lawsuit has since been dropped, but the lesson that should still resonate from this story is that compliance regulations are not just there to burden your organisation; they’re there for your own protection.
Compliance through User Activity Monitoring
User activity monitoring brings you the most comprehensive solution for your compliance needs, by recording all user activity in all applications and system areas. User session video playback provides unequivocal proof of user activity during audit reviews. Real-time alerts can be configured to proactively address out-of-policy behaviours.
There are more than 2,500 internal security breaches that occur in U.S. businesses every single day. Don’t view compliance standards as an afterthought. Instead, closely follow their guidelines as a standard minimum requirement in your organisation’s security approach.
Achieving this compliance requires overcoming the complexity of auditing dozens or hundreds of deployed applications. And equally importantly, your compliance solution should also allow your business to grow naturally, without artificial restrictions.
Whether your compliance requirements are for financial data protection, medical patient privacy, government oversight inquiry or 3rd party outsource compliance, Proofpoint ITM gives you the coverage and ease of use that you need to audit users.
To learn more about how customers use Proofpoint ITM to achieve PCI compliance, check out an recorded webcast, Insure Security: How AIG Leverages User Activity Monitoring.
