Business Email Compromise (BEC) and Email Account Compromise (EAC)—a collective $26B problem—are issues that organizations of all sizes, in all industries, must address.
For security practitioners, every second matters to prevent irreparable damage. You need tools in place to streamline and automatically identify threat actors attempting to gain unauthorized access so you can maintain control of your employees' cloud accounts. Attackers use tactics such as password spraying, phishing, malware, malicious third-party applications and brute force attacks to compromise these accounts. You need a simple and effective way to identify what is happening across your user’s cloud accounts.
Proofpoint TAP now provides extended visibility into suspicious login threats targeting Office 365 and G Suite cloud accounts. Context about the suspicious login detection: user, source, why it is considered to be a risk, will help you identify potential account takeovers more efficiently and in an automated way.
To do this, follow the three simple steps below:
1. Log-in to the TAP Dashboard and click the TAP SaaS Defense button
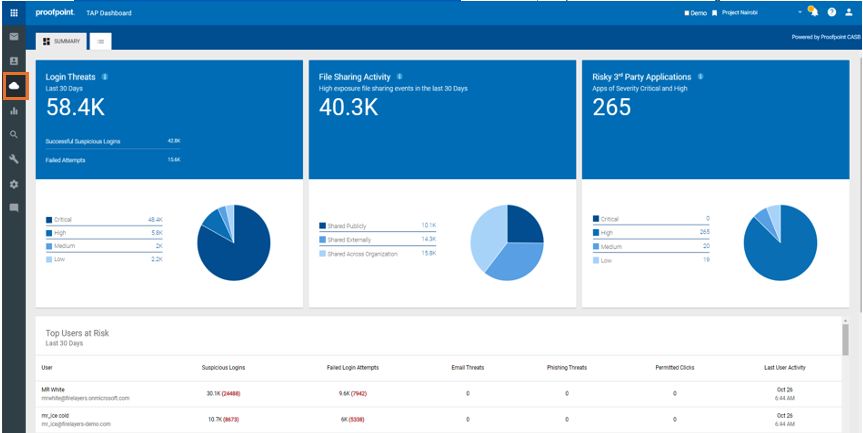
2. Click on any figure in the Login Threats area

3. Gain visibility into potential account compromise

You can see all the suspicious logins that were detected along with the necessary details needed to locate and identify which accounts need attention. From there, you can take the proper remedial actions to protect your user’s cloud accounts before any damage to your organization. For example, enable step-up authentication, force reset passwords or disable the account altogether.
If you have adopted Office 365 or G Suite, but are not using TAP SaaS Defense, you can turn it on at no additional cost to your organization. In addition to helping you detect compromised accounts, TAP SaaS Defense also helps identify high exposure file sharing and risky third-party applications in the cloud.
To implement policy-based remediations, adaptive access control, data loss prevention (DLP), application governance and additional cloud application protection, customers should look into the Proofpoint CASB offering.

