Have you ever wondered what the most prevalent cyberattack type is? It is a hard question to answer. Attacks operate at so many different levels and are often chained together to complete the malicious mission. Some readers are probably thinking of ransomware, others phishing, and others malicious URLs. All are certainly common elements of an attack, whether endgames or steps along the way. And all are also very prevalent.
I would like to add account takeovers (ATOs) or account compromises to the mix. Consider how useful it is for a threat actor to gain control over a legitimate user account as they try to penetrate an organization for any number of malicious endgames. A perfect, very public example of this was last year’s Snowflake breach.
Here, we’ll present some fresh Proofpoint proprietary data that should put account takeovers, or at least attempts at ATOs, into the discussion for the most prevalent type of attack.
Threat data is at the center of ATO detection
Proofpoint has access to tremendous amounts of security data. It is safe to say that if Proofpoint hasn’t seen it, then there’s a good chance it never happened. This data takes many forms, including emails, malware, URLs, domains, IPs, identity vulnerabilities and attacker tooling. Importantly, for the purposes of this blog, it also includes account takeover attempts and successes.
Proofpoint also has a vast global customer base. What’s more, we have thousands of direct integrations with key cloud services such as Microsoft Entra ID, O365, Okta and Google Workspace as well as tens-of-millions of monitored user accounts. As a result, we see millions of account takeover attempts every year. This data is tremendously valuable when tuning our detection algorithms.
In 2024, 99% of all the customer tenants that we monitor were targeted for account takeovers. In the same period, 62% of these organizations experienced at least one account takeover (the average was 12). 99% and 62% are some serious ATO prevalence numbers. In addition, some organizations experienced dozens or hundreds of successful ATOs.
Where attacks are coming from
What countries were the source of these attacks in 2024? The Top 5 were the United States, Germany, Russia, India and the Netherlands. And the Top 5 domains that served as sources for these attacks were Datacamp.co.uk, Microsoft.com, Amazon.com, Biterika.ru and Cyberassets.ae.
One clear takeaway is that geo or domain blocking is not sufficient to defend against account takeover attempts. With some exceptions, attackers use the same service providers and hosting countries as legitimate organizations.
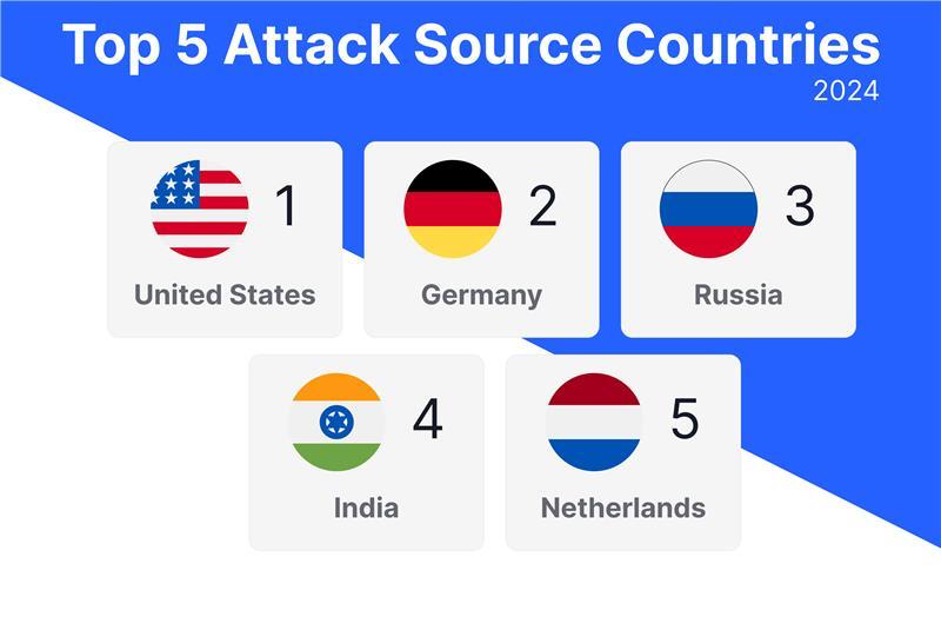
Top country sources of account takeover attacks.
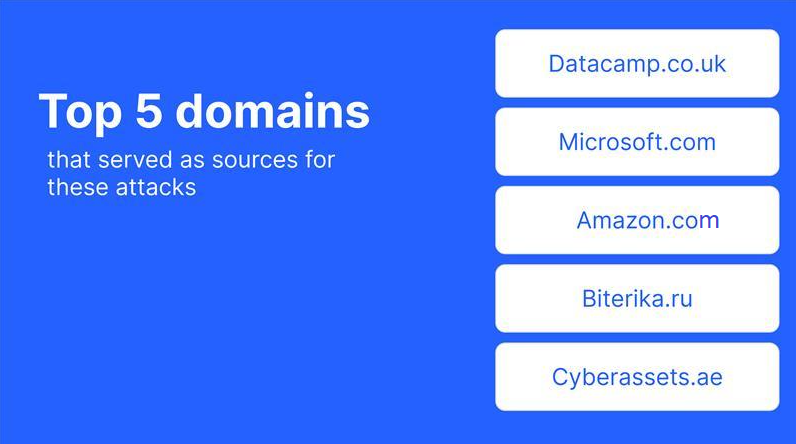
Top domain sources of account takeover attacks.
Industries that are most impacted
Are there more attempts at account takeovers in certain industries? In the chart below, look at the darker blue bar. It shows the percentage of organizations that experienced ATO attempts in 2024. The percentages vary only between 95% and 100% of organizations across the board. It’s not an overstatement to say threat actor attempts at account takeovers are ubiquitous across all industries.

Percent of customer tenants that are targeted and experienced ATOs in 2024.
Next, look at the light blue bar. It represents the percentage of organizations that experienced successful ATOs. Notably, there is significantly more variability in this category. On one end of the ATO spectrum sits education (88%), electronics (88%) and aerospace (86%). And on the other end sits legal services (50%), food & beverage (50%) and financial services (47%). While 47% is far better than 88%, it is still a high percentage.
MFA is good, but not good enough
Now let’s move the discussion over to the user accounts housed at these organizations. Of the approximately 63M monitored accounts in this data set, nearly 5%—approximately 3 million—were targeted for account compromise last year. Of that group, 17K were successfully compromised, or about .6%.
Certainly, multifactor authentication (MFA) is a good practice, but it is not an account takeover defense silver bullet. If you are wondering how an account that’s configured with MFA can still be taken over, check out this demo video and this recent Proofpoint blog.
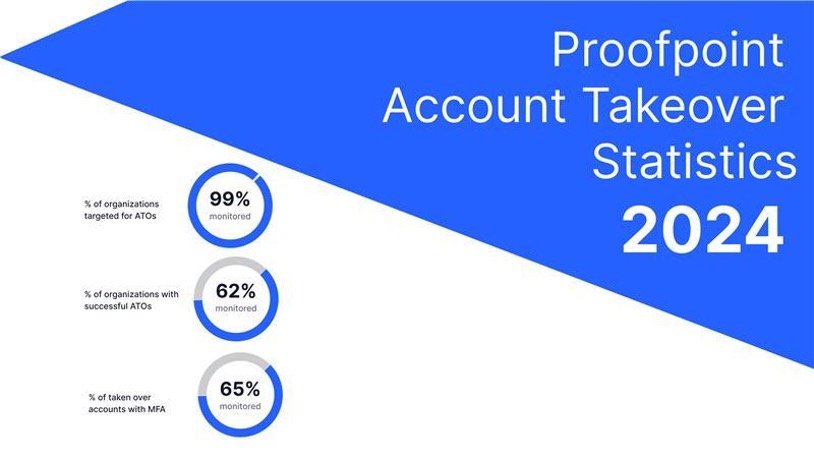
Proofpoint account takeover statistics for 2024.
Detecting ATOs with high-fidelity
What does it take to successfully detect an ATO with extremely high fidelity? The reality is that there is no single indicator of account compromise that is a sure tell. For example, if your detections are heavily dependent on detecting anomalies using login location or analyzing impossible travel, you can expect a high rate of false positives.
To do detection right requires a combination of real-time data elements that are continuously analyzed with a sophisticated detection engine that uses multiple techniques including:
· Pre- and post-access behavior monitoring
· Proprietary and third-party threat intelligence
This data must be continuously monitored and regularly optimized by an expert team of threat researchers and engineers to maximize the detection fidelity.
The bottom line is doing ATO detection right is hard. Maybe this is why Microsoft has seemingly backed off from detecting ATOs and is focused on supplying behavioral information instead. There are multiple implications for this switch. Does this mean that their false positives will go down, but their false negatives will go up?
Protect against ATO attacks with Proofpoint User Protection
Attackers’ focus on compromising accounts is part of their larger attack strategy of focusing on your users. It follows that an optimal ATO defense must be equally strategic. This is why Proofpoint provides a comprehensive ATO defense-in-depth solution that is proactive with security awareness training, preventive with email security, and is reactive with ATO detection and response. We refer to this combined solution as Proofpoint User Protection. With Proofpoint User Protection you can get the most comprehensive and integrated protection on the market. While you can’t stop your organization from being targeted for ATOs, you can certainly add a lot of friction to this attack path.

