Proofpoint introduces inline, pre-delivery QR code detection engine to help protect against imaged-based QR code phishing attacks
QR code phishing, also known as quishing, is the latest attack hitting inboxes. This emerging threat is able to get around traditional email defenses and is forging a new way to deliver email attacks directly to users. Along with email phishing, executive impersonation, spear phishing and business email compromise (BEC), this threat has become one of the top concerns for security and IT teams.
In response, Proofpoint has launched new inline sandboxing capabilities for QR code detection and stopping suspicious QR threats. Not only do we support behavioral and sandbox detection engines, but we also provide pre- and post-scanning for malicious QR codes. When combined, these capabilities more accurately detect and better protect against this new threat vector. Most API-based email security tools rely on behavioral signals, which means they can only detect a suspicious QR code email after it has been delivered to the user’s inbox. In contrast, Proofpoint stops attacks pre-delivery, so threats can never make it to users’ inboxes.
In this blog post, we’ll cover what you should know about malicious QR code phishing and detection—and how Proofpoint can help.
Why QR codes?
When Microsoft disabled macros to prevent threat actors from exploiting them to deliver malware, threat actors started to test various new attack delivery techniques, such as malicious QR codes. Used by marketers as a quick and easy way to connect with consumers and drive engagement, QR codes have become a part of our daily lives and are now used in retail stores, airline tickets, contactless menus and scan-to-pay, among many others.
While it’s common knowledge that standard QR codes can be used in malicious ways, a recent Scantrust QR code survey found that “over 80% of US-based QR code users said that they think QR codes are safe.” It’s this inherent trust of QR codes that threat actors depend on. That and the fact that QR codes do not expose malicious URLs make them very hard to detect with traditional email security tools.
What is QR code phishing?
A QR code scam is when a bad actor creates a malicious QR code phishing campaign to trick a user into navigating to a malicious URL. This leads them to a malicious website that then harvests their credentials or downloads malware onto their device. These campaigns include payment scams, package scams, email scams and even donation scams during the holiday season. Because all QR codes look similar, detection is difficult and users are easily fooled.

Figure 1: How a QR scam typically works.
Why are QR codes getting through?
Legacy email security providers and most API-based email security tools have a very difficult time detecting these attacks. That’s because these tools scan email messages for known suspicious links—they don’t scan images for links that are hidden inside malicious QR code images.
This attack method also creates a new security blind spot. QR codes are scanned by a separate device, like a smartphone, from where the email is delivered. And smartphones are less likely to have robust security protection, which is needed to detect and prevent these attacks. For this reason, it’s essential that an email security tool includes QR code detection to block phishing emails before they reach users’ inboxes. When messages are scanned post-delivery, like with API-based tools, there’s a chance that users will get to them first—before they’re clawed back.
Post-delivery-only QR code detection risks
Post-delivery-only email security tools claim to “detect and block” QR code phishing emails, but they simply cannot. While they may include a level of suspicious QR code detection, it’s only after the threat has been delivered to the user’s inbox. Moreover, these tools do not sandbox suspicious QR codes. This means they have a high miss rate—which creates more risk for your company.
Besides creating more risk, they also create more work for your teams. By relying solely on behavioral anomalies, these tools will flag numerous legitimate business emails, which generates a high number of false positives. This means there’s a lot more work for security and IT teams when they’re probably already inundated with threat alerts.
In short, a post-delivery approach doesn’t scale with the needs of today’s modern enterprise and is extremely costly. That’s why Proofpoint came up with a far more effective and scalable approach.
Proofpoint’s giant leap forward: inline, pre-delivery sandboxing of malicious QR codes
Not only are QR code phishing attacks getting more advanced, but they’re proliferating at a rapid pace. That’s why Proofpoint is innovating quickly to stop these attacks. Our newly launched QR code detection and prevention capabilities take a defense-in-depth approach to helping companies protect against these attacks. Figure 2 shows how our approach works.
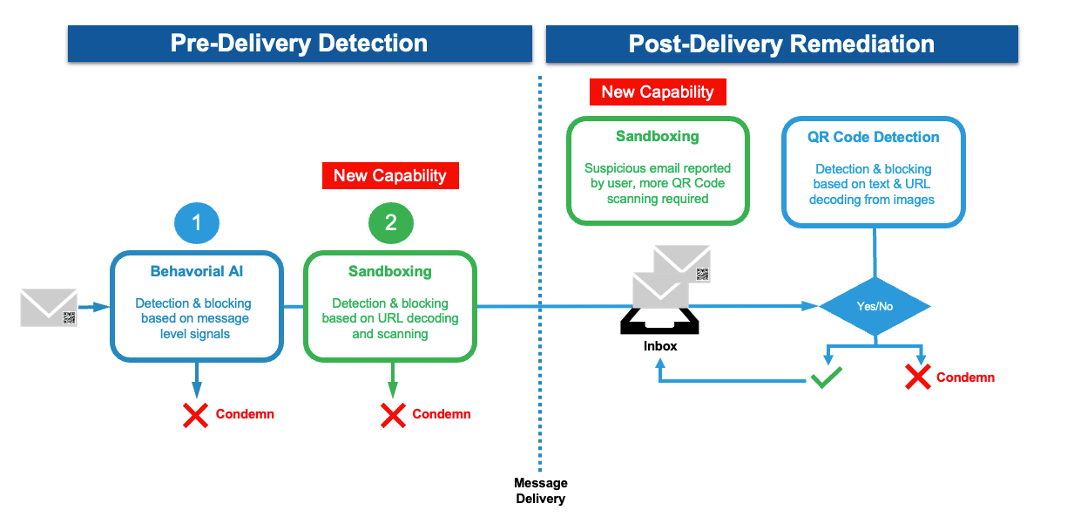
Figure 2: The Proofpoint pre-delivery approach to QR code detection and prevention.
Step 1: Proofpoint uses its behavioral AI detection engine to identify key message attributes that indicate a message may be malicious, like sender, receiver, headers, images, URL links, attachments and more. By analyzing these attributes, we are able to detect and block thousands of QR code attacks per day across our 230,000 customers. And we do this all before these malicious QR code emails are delivered to users’ inboxes.

Figure 3: Proofpoint uses behavioral AI and threat intelligence signals to detect and block malicious QR codes.
Step 2: With our new inline, pre-delivery QR code detection engine, Proofpoint adds an additional layer of email inspection for deeper analysis. Specifically, we can more accurately detect malicious QR code phishing attacks by scanning and parsing QR codes in attached PDFs and Word documents, as well as images from within a suspicious message.
By extracting encoded URLs from the QR code itself, we can automatically sandbox the suspicious URL to determine if it’s malicious or not. Unlike other email security solutions, we sandbox all URLs, not just the ones that lead to a payload. If the email contains a malicious payload, we will block the hostile email. If it is not deemed malicious, then we will allow the email to be delivered to the user’s inbox.

Figure 4: Proofpoint QR code detection forensics in action.
Post-delivery QR code threat reporting just got easier
In addition to post-delivery QR code detection and automated remediation, Proofpoint also has a new capability where users can directly report malicious QR code emails from their desktop, laptop or mobile device. So, if an email with a QR code is delivered to a user’s inbox and they think it’s suspicious, they can report the email from within their email UI. In turn, we will sandbox the suspicious QR code post-delivery. If the email is found to be malicious, then it will be automatically condemned and removed from all users’ inboxes across the company.
Benefit from our investments in AI and QR code detection
Email remains the number one threat vector, and QR code phishing attacks are on the rise. To protect against these threats, you need to prevent these emails from ever reaching your users.
Unlike post-delivery-only tools that take a simple, single-layered approach to detecting QR code email attacks, Proofpoint continues to out-innovate the market with a defense-in-depth approach. In fact, for the past two decades Proofpoint has continuously invested in innovation. During that time, we have secured more than 250 patents to protect our AI, machine learning and detection engine technologies.
By layering behavioral AI analytics with the scanning, parsing and extracting of encoded URLs from QR codes, pre- and post-delivery, Proofpoint provides the most comprehensive QR code email threat protection.
Additional recommendations for protection against QR code phishing scams
To keep your company safe from QR code-enabled emails, we recommend the following:
- Pre-delivery email security. Preventing and blocking messages is the only sure way to keep users safe. Your company needs a cybersecurity tool that uses both machine learning and advanced threat detection to identify and stop these threats, such as the Proofpoint Aegis threat protection platform. Post-delivery email security tools claim to include QR code detection against these threats. But even when they do, they do so later in the attack chain—after the threat is already in users’ inboxes.
- User education. Your employees and customers are your first line of defense. Make sure they get security awareness education about all types of phishing attacks. Topics should include deceptive emails and fake login pages. This can greatly reduce their chances of being a victim.
- Account takeover protection. A good cloud security platform can identify account takeover attacks and prevent unauthorized access to your sensitive cloud resources. This security control should cover both initial- and post-compromise activities. And it should let your security team get a closer look into which services and applications are being abused by attackers. Make sure to look for a solution that automates remediation. This reduces attackers' dwell time and keeps damages to a minimum.
- Supply chain protection. Defend your organization from emails sent from potentially compromised vendors and partners. Proofpoint Supplier Threat Protection uses advanced AI and the latest threat intelligence to detect the supplier accounts that have been compromised and prioritize any that should be investigated.
Break the attack chain with Proofpoint
With our in-depth approach to QR code threat detection, you can break the attack chain and protect your company from even the most sophisticated attacks. Our new QR code detection and prevention capabilities are now available to all Proofpoint Aegis threat protection platform customers. Our platform features multi-layered detection and prevention that help companies stay ahead of the growing threat of QR code phishing attacks. We provide high-fidelity detection, efficacy and explainability for the modern enterprise.
To learn why 87% of the Fortune 100 trust Proofpoint to protect their organizations, download the Proofpoint Aegis threat protection solution brief.

