The Cybersecurity Maturity Model Certification (CMMC) program enforces the protection of sensitive unclassified information that the U.S. Department of Defense (DoD) shares with its contractors and subcontractors.
Threat actors know how to hijack your trusted organization communications. They can impersonate you, your brand or your organization partners. And they can make a nice profit doing it. The FBI’s 2023 Internet Crime Report notes that last year’s adjusted losses from organization email compromise (BEC) cases exceeded $2.9 billion—up 7.4% from 2022.
Bad actors use spoofed domains, lookalike domains, compromised supplier accounts and other tactics in their attacks. So it’s important to keep communications with trusted partners, customers and suppliers safe. This should be a top focus for government agencies and the organizations that they work with since they are key targets for bad actors.
Proofpoint helps you mitigate the risk of impersonation abuse with a holistic, multilayered approach. With Proofpoint Impersonation Protection, you can:
- Protect your organization’s communications from impersonation threats
- Stop attackers from impersonating your brand
- Detect and defend against risky suppliers, including compromised supplier accounts
- Secure user and application emails so that they can be trusted
We help our federal and defense industrial base customers with Level 3 CMMC controls around the Risk Assessment (RA) and Identification and Authentication (IA) Practices. Here’s how.
CMMC overviews for Level 3 controls
In this section, we match CMMC compliance requirements with the capabilities of Proofpoint Impersonation Protection.
CMMC Level 3 – Risk Assessment Practice
-
RA.L3-3.11.1e – Threat-Informed Risk Assessment
CMMC compliance requirement
Employ threat intelligence, at a minimum from open or commercial sources, and any DoD-provided sources, as part of a risk assessment to guide and inform the development of organizational systems, security architectures, selection of security solutions, monitoring, threat hunting and response and recovery activities.
-
RA.L3-3.11.3e – Advanced Risk Identification
CMMC compliance requirement
Employ advanced automation and analytics capabilities in support of analysts to predict and identify risks to organizations, systems and system components.
-
RA.L3-3.11.6e – Supply Chain Risk Response
CMMC compliance requirement
Assess, respond to and monitor supply chain risks associated with organizational systems and system components.
-
RA.L3-3.11.7e – Supply Chain Risk Plan
CMMC compliance requirement
Develop a plan for managing supply chain risks associated with organizational systems and system components; update the plan at least annually, and upon receipt of relevant cyber threat information, or in response to a relevant cyber incident.
How Proofpoint Impersonation Protection meets the Risk Assessment (RA) Practice needs above
Proofpoint Nexus Supplier Risk Explorer gives you insights into supplier risk. This includes threats where attackers are impersonating your agency as well as compromised suppliers and third parties.
Supplier Risk can also be used as part of a vendor risk management process when sourcing and choosing new vendors/suppliers. Proofpoint provides visibility into supply chain threats, lookalike detection, and impersonations of your brand with Supplier Risk and Domain Discover. This helps to create the supply chain risk plans that are needed to comply with CMMC.
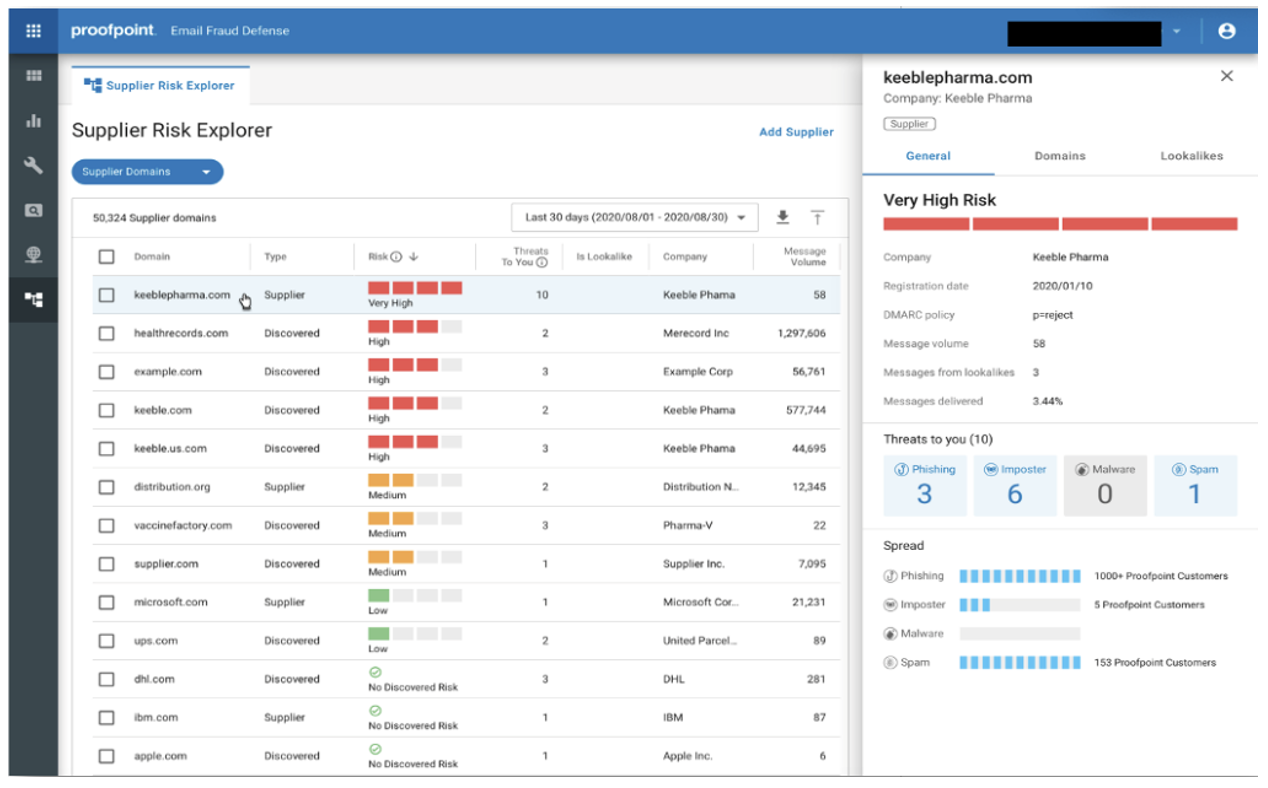
Supplier Risk Explorer identifies supplier domains and shows you which suppliers pose a risk to your organization.
As noted above, Supplier Risk Explorer assesses the risk level of supplier domains by evaluating several dimensions, including:
- Threats sent to your organization
- Threats sent to other Proofpoint customers
- The lookalikes of supplier domains
- Whether a domain was recently registered
- Whether a domain has a DMARC reject policy
By ranking and prioritizing the risk level of your supplier domains, your security team can see and prioritize which suppliers they should pay the most attention to. To learn how to recognize and stop these supplier attacks, see this blog.
Proofpoint Secure Email Relay provides email authentication and email security. You can use it to secure your brand image and reduce the number of suppliers that send emails on your behalf.
How Proofpoint Threat Intelligence meet these needs
Additionally, these threat intelligence solutions tie into this requirement:
- Proofpoint Emerging Threat (ET) Intelligence
- Proofpoint ET PRO®
- Proofpoint Threat Intelligence Services (PTIS)
- Proofpoint Virtual Takedown
These solutions help you to detect threats and proactively defend against threats that are targeting your organization. Proofpoint provides a deep understanding of the ongoing threat landscape and your organization’s place in it. It helps you identify, understand and prioritize threats efficiently. This, in turn, helps your team make better decisions, faster.
CMMC Level 3 – Identification and Authentication (IA) Practice
-
IA.L3-3.5.3E – Block Untrusted Assets
CMMC compliance requirement
Employ automated or manual/procedural mechanisms to prohibit system components from connecting to organizational systems unless the components are known, authenticated, in a properly configured state, or in a trust profile.
How Proofpoint Impersonation Protection meets this need
Proofpoint Secure Email Relay authenticates your email. It allows only trusted senders to send on your behalf—and with security mechanisms in place.
Our secure email gateway integration allows you to enforce DMARC authentication on your inbound email. This helps you to better protect your employees from email fraud by blocking untrusted and compromised senders across your entire email landscape.
Learn more
Federal agencies are under pressure to protect their data, communications and supply chain while enabling employees to carry out their missions. Visit these links to get more details on how Proofpoint helps to protect federal agencies:
Learn how Proofpoint Identity Threat Defense and Proofpoint Insider Threat Management meet our federal customers’ CMMC needs in this white paper and blog.
Find out more about Proofpoint Impersonation Protection in this solution brief.
To learn how other Proofpoint products meet NIST Cybersecurity Framework requirements, download this white paper.

