This is the second blog in a two-part series about data privacy. In our previous post, we discussed how data privacy has become increasingly important. And we covered why data loss protection (DLP) and insider threat management (ITM) tools are critical to ensuring data privacy.
The shift to “work from anywhere” and the increase in cloud adoption have caused a rise in data loss and insider threats. To defend data from careless, malicious and compromised insiders—and the harm that they cause—security teams must implement data security tools like data loss prevention (DLP) and insider threat management (ITM) platforms. These tools monitor and control how employees interact with data. At the same time, companies are collecting more and more data about employees themselves, like protected health information (PHI).
The abundance of all this data—which is being collected and processed in the cloud—creates a critical challenge for security teams. They must protect employee privacy without impeding productivity. In this post, we’ll explore the topic of privacy by design, which aims to strike a balance between these two challenges. We’ll cover why it’s so important. And we’ll discuss how Proofpoint Information Protection can help you build a modern DLP program and comply with data privacy laws.
Why privacy by design matters for DLP and ITM
Privacy by design is a framework that embeds privacy into the design of IT systems, infrastructure and business processes. Privacy is not an afterthought. It is considered right from the start—in the initial design phase. What’s more, it’s a core component that integrates visibility, transparency and user-centricity into its design. In short, privacy by design ensures that everything is built with the user in mind.
Privacy by design is important to DLP and ITM because it helps to:
- Protect employee rights. Personal data is sacred. Employees expect their personal data to be safe and their rights protected. When a company takes a proactive, transparent approach to data privacy, it helps maintain trust with employees.
- Comply with privacy laws. Data privacy laws protect people by requiring businesses to keep their data safe and avoid sharing it unethically with third parties. These laws often require companies to tell users exactly how their data is used and collected, and to notify them in the event of a data breach. Failure to comply can lead to hefty fines and penalties, which can damage a firm’s finances and brand image.
- Prevent bias in investigations. When user data is kept secure and private, it ensures insider threat investigations maintain their integrity and objectivity. If a user is identified, it could influence a security analyst’s response to an incident. User privacy helps take emotion and subjectivity out of the picture.
Ensure data privacy with Proofpoint DLP and ITM
Proofpoint Information Protection includes administration and access controls. These controls can help your business keep data private and meet compliance requirements.
Data residency and storage
Proofpoint uses regional data centers in the U.S., Europe, Australia and Japan to meet data privacy and data residency requirements. You can control exactly where your data is stored at all of these data centers. For example, you can group your endpoints and map each group to a regional data center. This ensures that data on all those endpoints are stored in that regional center. So, a U.S. realm can manage U.S. endpoint data, which is sent to the U.S. data center.
Attribute-based access controls
Attribute-based access controls give you a flexible and easy way to manage access to data. You can use these controls to ensure that security analysts have visibility into data on a need-to-know basis only.
For instance, you can write granular policies and assign access so that a U.S.-based security analyst can only see U.S. data. They cannot see data in Europe or the Asia-Pacific region. And when an analyst needs to access a specific user’s data for an investigation, the systems administrator can “time bound” that access. In other words, they can specify how long the analyst can see that data.
Data masking
Data masking is another way to keep data private. When you use Proofpoint Information Protection, you can mask sensitive data like PHI and personally identifiable information (PII). This makes the data unidentifiable in the user interface. It ensures that only the people who need access to the data can see it in full.
System administrators can configure the data identifiers they want to mask. For example, an admin can decide to show only the last four digits of a credit card number and mask everything else. They can also decide what and how much data users can see based on their role. For instance, they might specify that only authorized analysts can see snippets of sensitive data.
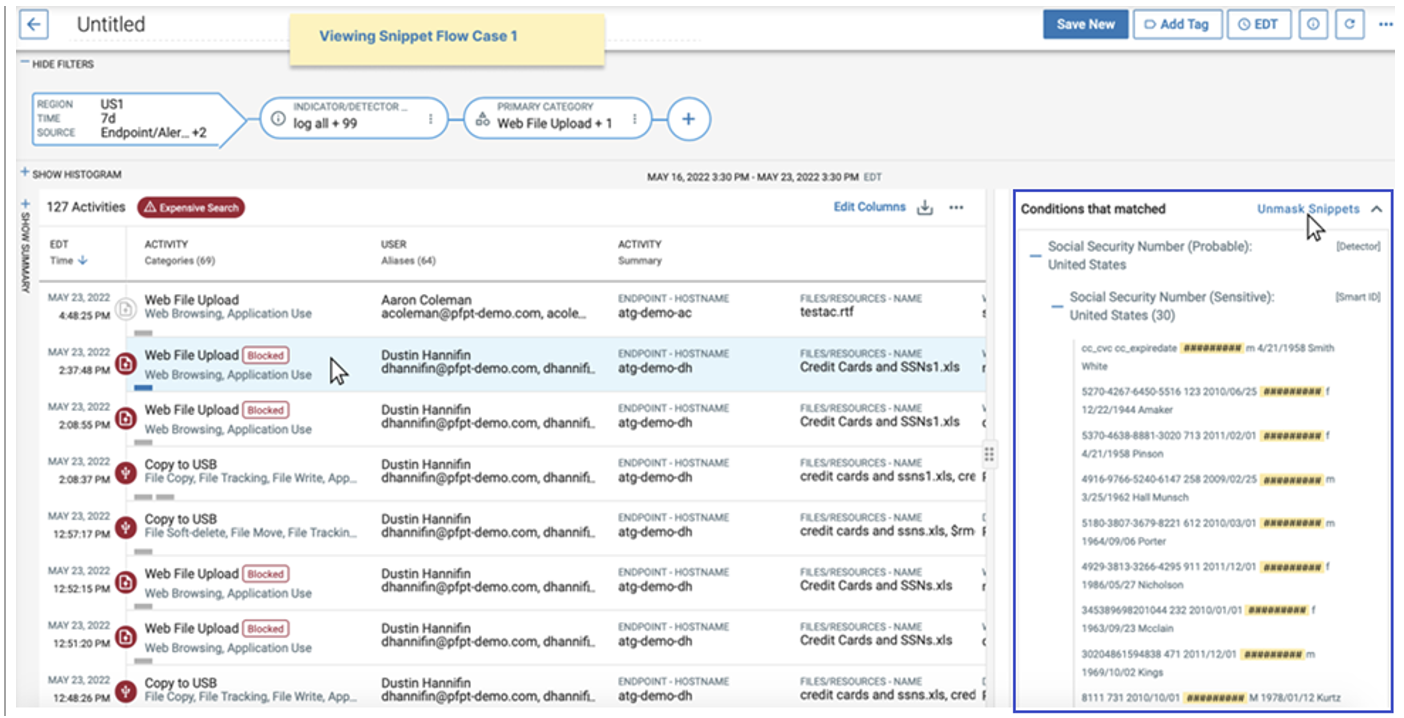
The masking of Social Security numbers in Proofpoint Information Protection.
Anonymization
Anonymization is another way to protect user data. It allows you to hide a user’s identity. You can anonymize the username, host name, IP address, location info and file names.
Anonymization ensures that only authorized security analysts can see the identifying data of monitored users. The process helps eliminate bias in investigations as well. Consider the scenario where a user who just violated corporate policy is a C-level executive. If their identity is known, the incident may be handled differently, or a security analyst may look the other way.
When a user’s identity must be known further downstream in an investigation, the security analyst can request de-anonymization, which an administrator can grant.
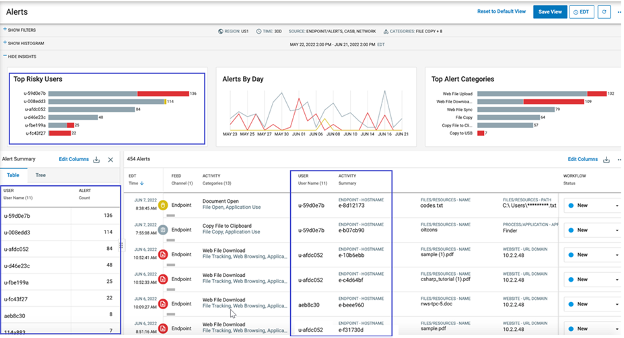
A view of anonymized user data in Proofpoint Information Protection.
Managed services for DLP and ITM
Proofpoint Managed Information Protection can equip your company with the right people and processes to help you optimize your investments. We can help you design and implement a modern program that ensures data privacy and puts flexible controls in place.
Learn more
To find out more about data privacy, read the first blog in this series, The Importance—and Growing Complexity—of Ensuring Data Privacy. You can also watch this on-demand webinar about balancing security and privacy. You’ll get insight into how you can balance security controls and privacy. And if you want to learn more about DLP and ITM from Proofpoint, check out our Proofpoint Information Protection solution brief.
