When strengthening your insider threat security posture, it is crucial that third party access is not over looked. The term "insider" is defined as a current or former employee, contractor, or business partner who has or had authorized access to the organization’s network, systems, or data. An insider threat is when an insider intentionally or unintentionally misuses access to negatively affect the confidentiality, integrity, or availability of the organization’s critical information or system. Research has shown that a massive amount of data breaches are accomplished via remote access to a company’s systems. The most common of these channels are Virtual Private Network (VPN), Remote Desktop Protocol (RDP), Microsoft’s Terminal Services, Citrix XenDesktop and Citrix XenApp Published Applications, and Secure Shell (SSH).
Because the remote accounts used in these breaches are authorized by IT, traditional perimeter defense systems have challenges addressing what users are doing with authorized access.
"I know when users are logging in and I know when users log out. What they are doing when they are in ... I have no idea." - CISO, Fortune 500 Company
To defend against the abuse of these accounts – both by authorized account users and compromised insiders– it is imperative organizations monitor exactly what remote users are doing on critical assets once access is granted. The remote IT Contractor is here to stay. Remote contractors and their employees have become an integral part of day-to-day IT operations in most organizations. Internet-based remote access systems are critical for numerous business function providers, including:
- Outsourced software developers and QA teams
- Outsourced software application configuration/customization consultants
- Outsourced database administrators
- Managed service providers responsible for servers, network equipment (firewalls, routers, switches, etc.) and even entire data centers
- Managed service providers responsible for employee desktops (operating systems, user -permissions, software applications)
- Outsourced employee technical support and help desk services
When an organization’s internal systems are extensively accessible to remote partners, the risk that unauthorized users will exploit their access privileges to find an avenue into company servers, databases, control systems and other sensitive resources increases dramatically. Furthermore, even contractors with the purest of intentions still pose great danger to the organization: mistakes made while deploying code, configuring systems or assigning user permissions have the potential to reduce the performance of business-critical systems, destroy data or open huge security holes. Chances are also much greater for privileged user credentials to be stolen by third-party hackers and data thieves without a contractor’s intent or knowledge. The bottom line is having IT vendors with access to sensitive internal systems is a fact of modern corporate life despite the tremendous danger that this reality imposes on the organization.
How can you leverage the business and economic benefits of remote vendors, while mitigating the associated threats?
Proofpoint can help.
Proofpoint ITM provides the ability to capture user activity across all applications, even applications that do not generate logs, and converts screenshots into user activity logs that make it easy to search, analyze, audit, and act upon alerts for suspicious application users, admins and external vendors who have authorized access to an organization's data. This includes the ability to monitor all activity from Remote Desktop Protocol (RDP), Microsoft’s Terminal Services, Citrix XenDesktop and Citrix XenApp Published Applications, and Secure Shell (SSH).
Proofpoint ITM leverages a massive library of insider threat indicators to detect malicious and accidental actions. These alerts include unauthorized remote access, privilege escalation, use of shared accounts, bypassing security, backdoor creations, configuration mistakes and much more.
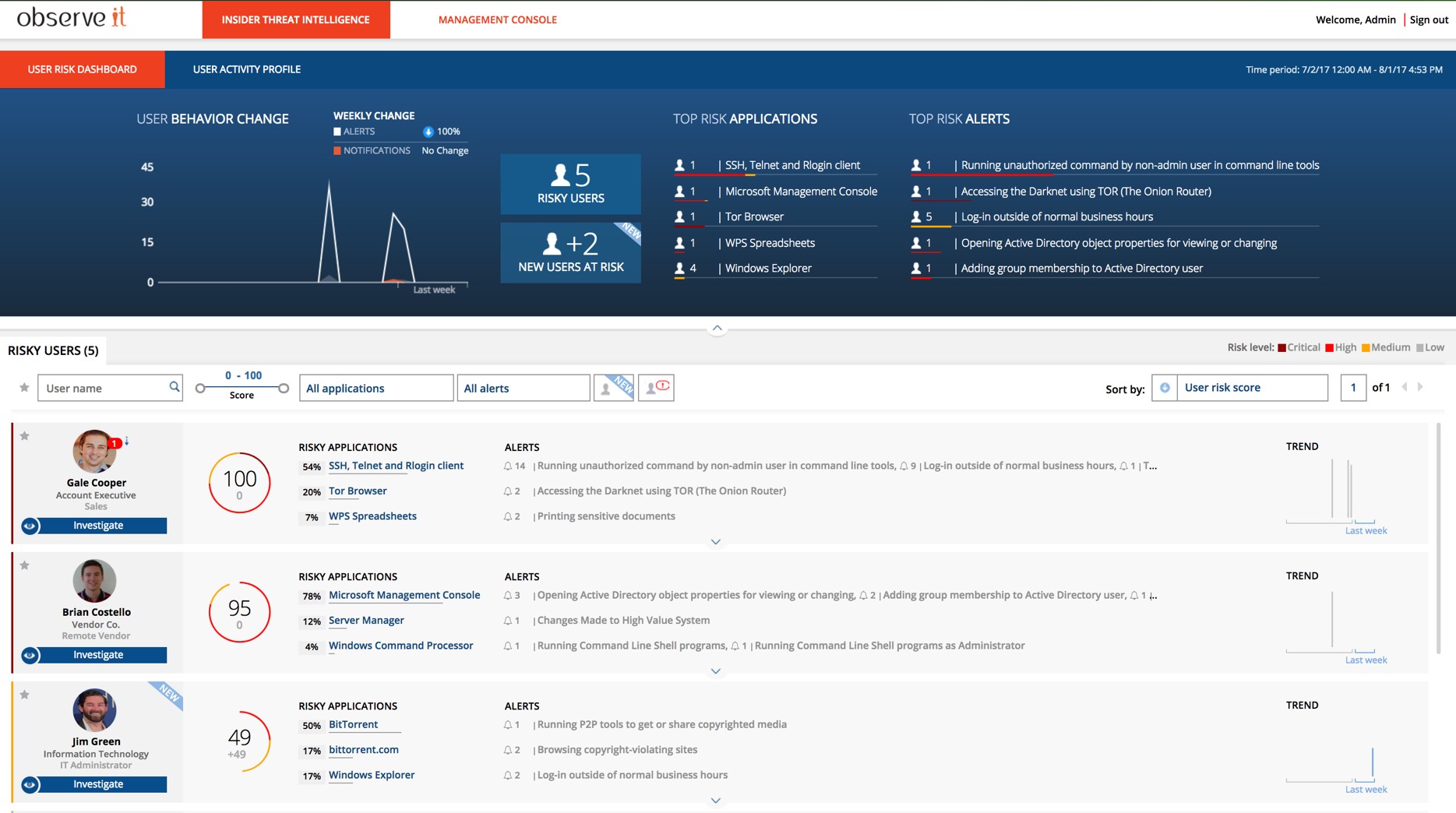
If suspicious activity is detected, Proofpoint ITM provides a full metadata and visual capture of every user action ensuring even the strictest controls are in place:
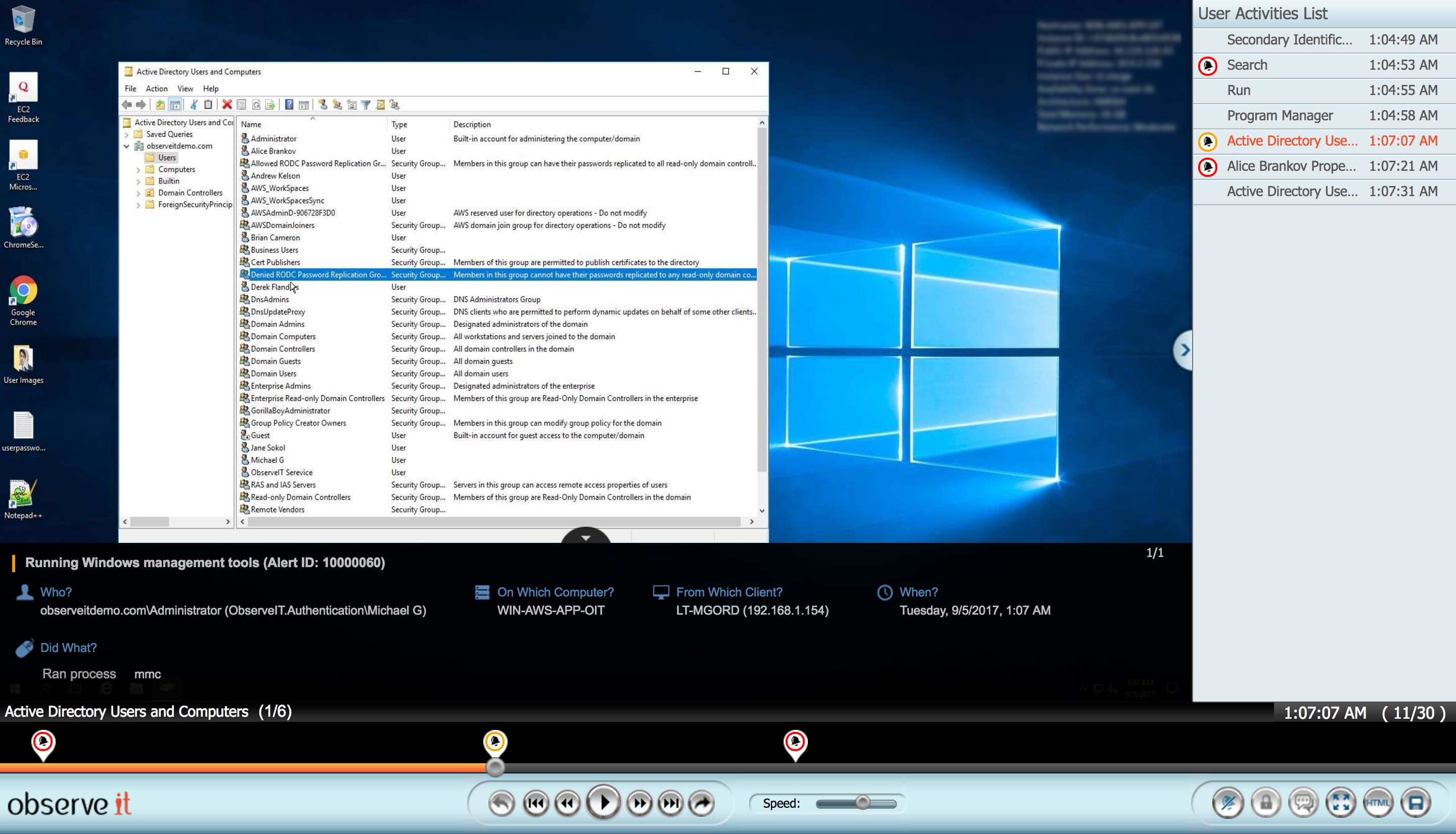
Proofpoint ITM Player
Any third-party or remote access can easily be search and reported on to streamline the audit process:
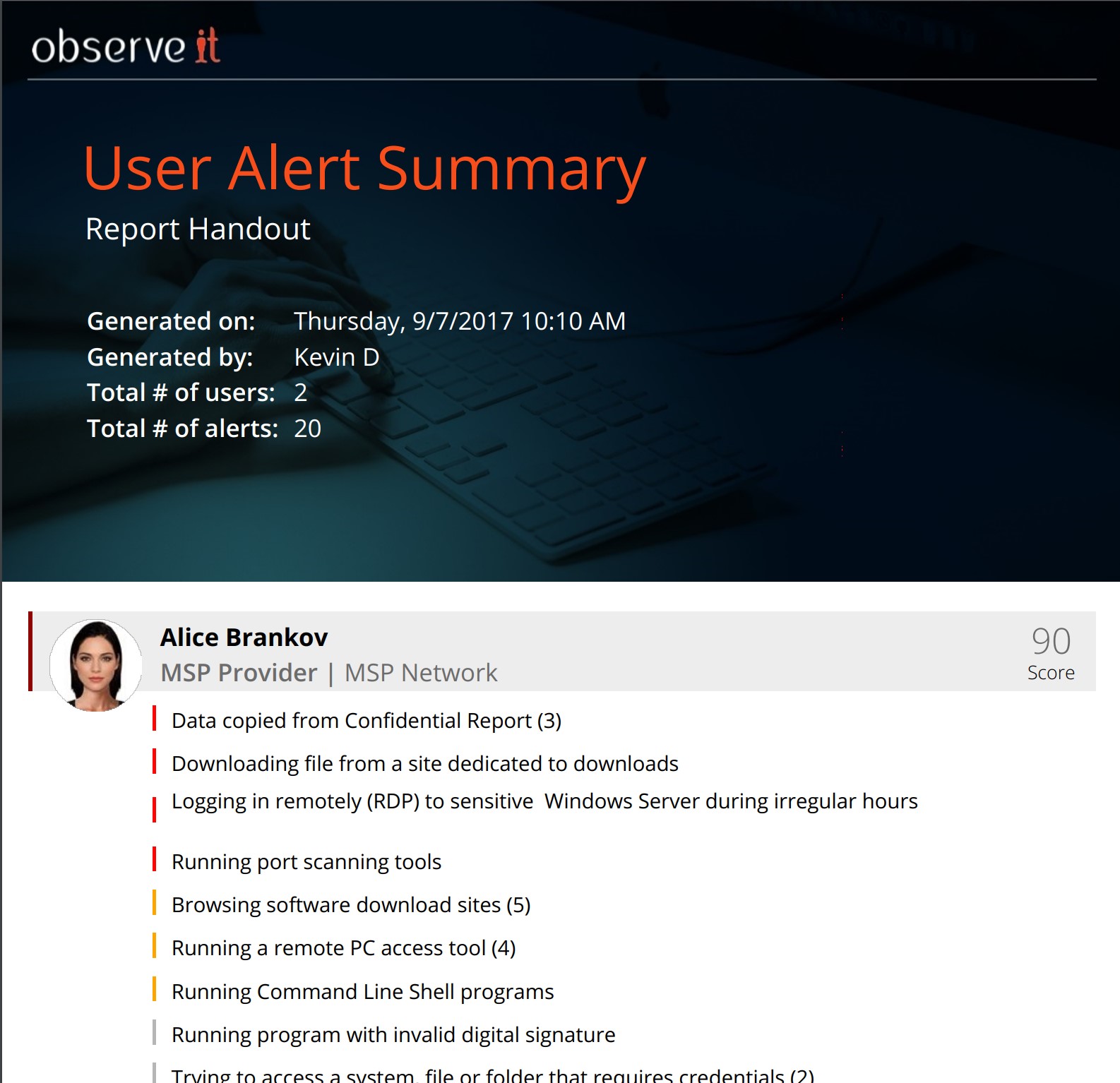
Conclusion
Deploying Insider Threat Monitoring and Prevention makes it easy to quickly detect questionable, dangerous or abusive remote (and internal) user activity, provides a full visual capture and metadata of every user action on any critical asset, and provides the ability to prevent unauthorized and accidental actions. Insider Threat Monitoring and Prevention makes it easier to get compliant and stay compliant with security aspects of government and industry regulations (e.g., GDPR, PCI, HIPAA, NERC, FISMA), while reducing overall security auditing costs. Most auditor requests can now be answered instantly by searching for user actions or watching a portion of a recorded session capture—without the need for complex machine data correlation and analysis.
Learn more about how Proofpoint can help you tell a better security story today.
