I’m a big fan of the Verizon Insider Threat report. It has brought significantly more attention to a previously underestimated business risk: insider threats. It is rich with eye-opening statistics and powerful recommendations. And it serves as validation for the hard work SOC and Insider Threat Analysts have put in for years without much recognition.
The Eleven Recommendations (As Listed in the Verizon Report) Are:
- Integrate security strategies and policies
- Conduct threat-hunting activities
- Perform vulnerability scanning and penetration scanning
- Implement personnel security measures
- Employ physical security measures
- Implement network security solutions
- Employ endpoint security solutions
- Apply data security measures
- Employ identity and access management measures
- Establish incident management capabilities
- Retain digital forensics services
If you’re new to the Verizon Insider Threat Report, I highly recommend checking out the 5 key takeaways from the report written by our Head of Security, Chris Bush. This blog post will dive into building a program based on the Verizon report’s recommendations and our customers’ journeys.
Having said that, I question the order of the recommendations in the report. In my experience, there is a strong potential for failure if a security organization attempted to set up capabilities in the order listed. Proof? For example, most security organizations don’t start with threat hunting first before they are proficient in their vulnerability scanning, personnel security and physical security measures. Threat hunting involves the proactive discovery of adversaries before they execute a full attack, usually reserved for the most advanced threats. It combines security tools, analytics, and threat intelligence with human analysis and instinct. These tools take expertise to use successfully, and the skills are hard (and expensive!) to acquire or rare to already have within a security organization new to this challenge. Why would insiders in an organization take a harder path to exfiltrate data or cause harm when they know basic security measures aren’t yet in place?
New Era of Coordination and Business Integration for Cybersecurity
There are two key areas that make insider threat management significantly more difficult than traditional external adversaries:
- The insiders’ deep knowledge of your systems and data
- The greater sensitivity to acknowledge the existence of potential insider threats within the business
Traditionally, cybersecurity has been focused on network security, external threats and prevention tools. Not anymore. Cybersecurity can no longer solve this problem on its own by investing in technology the way they tackled malware or zero-day vulnerabilities exploited by external hackers.
It is important to note that the Verizon Insider Threat Report’s eleven countermeasures span across people from multiple departments, new processes and across the technology stack.
This level of coordination and business integration is new to most CISOs, security operations directors and incident response managers. Following the journey of our 1,900+ customers as they have tackled the insider threat challenge and built a proactive program, we learned a few common traits and the most successful maturity path. The Verizon report accurately describes many of the core technologies, processes and people involved. However, the priority order of their recommendations would be counterproductive to, potentially drown, less mature security programs. Below are the four steps in which have implemented many of Verizon insider threat report recommendations.
Insider Threat Management Maturity Path Based on Verizon Insider Threat Report:
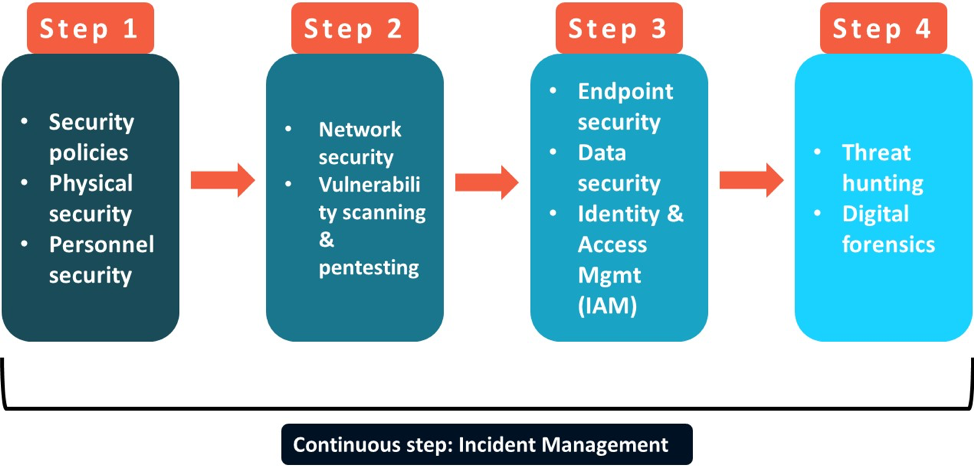 Note: This is a reimagining of the Verizon 11 countermeasures in Proofpoint’s recommended priority order.
Note: This is a reimagining of the Verizon 11 countermeasures in Proofpoint’s recommended priority order.
Our most successful customers usually started with updating their security policies and building more robust personnel security and physical security. As you’ll notice throughout this discussion, the insider threat problem goes beyond technical controls to include people, processes and technology. The second step speaks to basics of cybersecurity with network security and vulnerability management. As customers got more serious about insider threats as a major threat vector to the business and its employees, we saw a greater focus on endpoint security and Identity and Access Management. Even now, only customers with significant budgets or technical resources can afford to invest in threat hunting and digital forensics. One constant irrespective of your budget, size or security focus, Incident Management is a key capability because the number of alerts security operations deals with is still increasing every year. As our customers matured, we also saw insider threat driven incident response (IR) go beyond technical evidence collection to including legal, HR and privacy/compliance teams on an ongoing basis.
Learning From Our Customers’ Journeys
Our earlier customers cohorts had to be visionaries. They grokked the inadequacy of minimizing the risk from insider threats using existing paradigms in most cybersecurity organizations. This before significant market awareness, let alone much of a budget, a semblance of a dedicated team or clear mandate for tackling insider threats within their firm. Instead, they begged, borrowed and stole resources from other departments and cobbled together basic insider threat programs. Over time, we’ve seen more technology, more dedicated resources and more collaboration within companies and across industries.
Insider Threat Management Visionaries
One such visionary was within a global chemical company that reached out to us a few years ago because their Incident Response (IR) team was overwhelmed when dealing with user related security incidents. This team dealt with security and non-security incidents and didn’t have a dedicated budget for insider threats. Through their initial research, the customer realized the need to update their IR and security awareness policies along with buying new technology. Going back to maturity steps, they started their journey with two of the three pillars in the first step: security policies & privileged users under personnel security. Proofpoint ITM was used to monitor privileged users and help measure the effectiveness of the new security policies.
Within the first six to nine months with Proofpoint ITM visibility into user and data activity along with new IR policies, their IR analysts drastically reduced the time wasted on alerts that were red herrings. Each analyst saw a few hundred medium to high priority alerts from their security technology stack. Triaging that many alerts took most of the day, most of which were spent on false positives. Frustrating to say the least. With Proofpoint ITM visibility, we provided them context to any user and endpoint related alert in seconds and in plain English. Perhaps a small win, but one that mattered to the analysts on the frontlines. To paraphrase the Security Operations Centre (SOC) Director: there’s nothing like giving images and a timeline of events in plain English to Legal teams when a bunch of alerts became a full investigation.
Maturing to Data, Endpoint and Collaborative Incident Response Playbooks
The initial success helped them see a need to identify high-risk user and data activity enterprise wide, not just among their privileged users. In terms of the maturity steps, they were onto the next step with enterprise-wide endpoint security against insider threats. A byproduct of our visibility into user and data activity showed them the potential data loss already occurring within the company. This drove the customer to expand their Proofpoint ITM footprint; we became their core monitoring solution at the endpoint and cloud layer serving two user groups: data loss prevention (DLP) analysts and the IR team. The value of one product collecting the telemetry for both teams monitoring and investigations purposes helped them collaborate more on user driven alerts & build common IR playbooks. As we touched upon earlier, building irrefutable evidence in plain English about an incident is trivial with Proofpoint ITM. Along with the new collaborative processes, the customer significantly reduced the time to investigate user driven incidents from months to a week or two with the same headcount. In fact, some of the IR analysts even took on new projects such as proactive threat hunting on top of their daily responsibilities.
Now, a Shining Beacon in Their Industry
Over a period of 3 years, this large enterprise was recognized by peers as having climbed the insider threat management maturity pyramid. Today, the same SOC of 5 analysts and 2 developers are also able to proactively explore new potential threats on top of their existing investigation & governance responsibilities. Just to be clear a mature program still has areas of improvement. Conversely, a mature program doesn’t require every security technology under the sun. This customer has chosen not to invest in three specific technologies listed among the Verizon Insider Threat report countermeasures. It works for them.
The CIO summed up their success with one story of how cybersecurity and HR are now two closely aligned when just two years ago, mid-level managers in the two departments didn’t even know each other. At our recent customer advisory board, this customer presented their CIO level metrics around time, legal and severance cost savings within their SOC. We are delighted to be a major driving force of reducing investigation time by 90% and saving hundreds of thousands in legal and employee costs during security incident investigations in the past 3 years.
There are many such successes among our base, across industries. What stands out among them is the ambition to tackle big business risks and the diligence to stick to a maturity path. The Verizon Insider Threat Report has excellent recommendations but can leave mid-market companies and small cybersecurity teams feeling overwhelmed. Don’t worry, our customers demonstrated a common maturity path in going from ‘Not a Priority’ to proactively protecting their organization without breaking the bank.

