Privacy of consumers has been a white-hot topic in the press particularly among those of us in cybersecurity. That got Proofpoint thinking about a sister topic: trust in the workplace. Vanson Bourne, an independent specialist in market research for the technology sector, recently conducted a survey on this topic with more than 600 IT and cybersecurity decision makers.
Increasingly, to gain competitive advantage, employers are trusting employees to choose and use the most appropriate technology and work style to increase productivity. The result is a workforce with increasing numbers of remote and contract workers. This reality means the firm and cybersecurity teams cannot rely on closed, locked down environments as their primary method of risk mitigation. They must grant access to the data and systems so that users are effective in their roles, trust that they will handle the access with care, and verify with technology the trust is not misused – accidentally or maliciously.
Cybersecurity adapts: personal stories
Two recent stories put this into context. At breakfast with a friend in private equity finance, I was shocked to hear that, even in 2019, his firm struggles with allowing employees to work outside the two corporate offices! They are being forced to confront shadow IT across the firm and the inadequacy of the current, highly restrictive, approach. Multiple employees use Google Gmail to send sensitive corporate documents to each other. Some executives work from coffeeshops on public Wi-Fi without being on the corporate VPN. Depending on the technologies involved, shadow IT blinds the firm from risky user and data activity occurring with corporate assets. Not only is it harder to get work done, the firm’s risk posture is potentially worse off. In fact, one employee supposedly left to work for a competitor due to the strait-jacket IT policies. The workforce demands more trust and freedom from the firm to choose their work style and technologies, and organizations and their cybersecurity policies have to evolve.
Similarly, the construction industry in the U.S. is going through a talent upheaval with difficulty hiring younger workers. A recent NYTimes article featured a few construction companies using virtual reality devices, simulation games and continued online education to attract and train employees and improve employee productivity. New technology is always exciting and who wouldn’t be even slightly jealous of being able to play VR games at work! However, as the vanguard of the organization, cybersecurity needs to educate the workforce on protecting against the data and user security risks opened up by using 3rd party software or allowing personal VR devices to connect to the corporate network. Hence, cybersecurity needs an alarm system when things go wrong - like data exfiltration or privilege abuse.
Now, these two are extreme examples of waking up to the importance of trust in the workplace. The reality is cybersecurity teams are still figuring out appropriate controls in this new world.
No duh, more trust in employees is good
Just as we thought, 90% of firms surveyed by Vanson Bourne permitted significant remote work among the workforce, whether or not IT has written up a corporate policy.
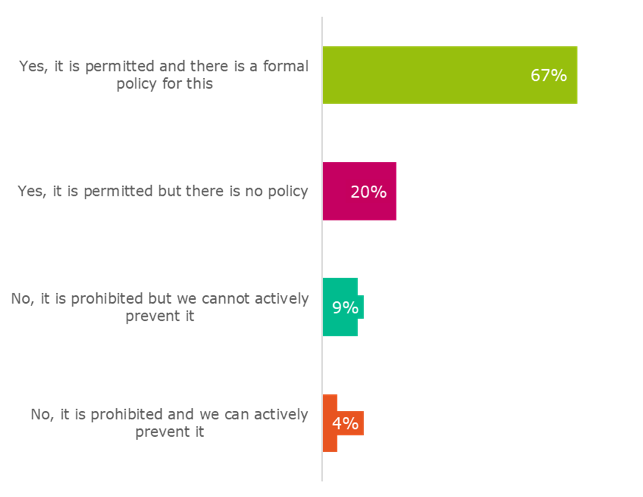
Figure 19: “Is remote work permitted within your organization?” asked to all respondents (600)
There’s no going back on increased trust in this era of talent wars. Personally, I feel more empowered – and as a result, am more productive - when my boss and company, in general, trust me to be productive and give me the flexibility to work in a way that fits my style and location. Honestly, I’m also more available for my teammates given we are spread across continents.
“With great power comes great responsibility”
The predicament of my cybersecurity colleagues reminds me of this famous quote most recently attributed to Spiderman. Employees having more freedom means we can be more productive, but the down side is it also opens up our employers to more potential for harm. We are talking about both poor security awareness and, as a result, poor cybersecurity policy compliance, and, to a much lesser extent, malicious users with increased legitimate access and interaction with critical systems and sensitive data. Thus, cybersecurity and employees themselves have more responsibility to protect themselves, the firm and its customers when using all of this new technology.
Traditionally, cybersecurity has taken a prevention mindset. This involves locking down the network and whitelisting the only software that employees can use and how users are able to move data. Two-thirds of all surveyed confirmed they currently have technology controls to prevent or block user actions.
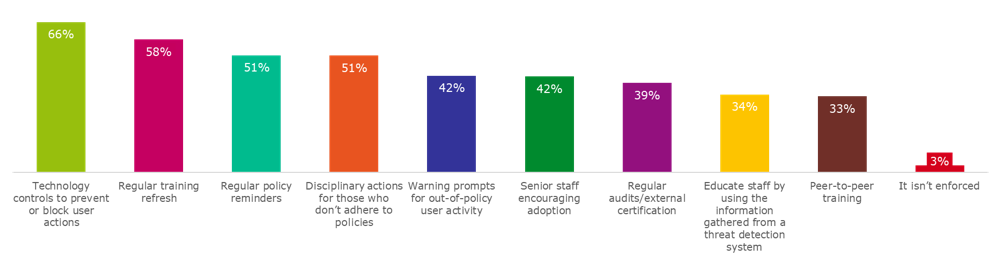
Figure 14: "How does your organization enforce the adoption of cybersecurity best-practices and standards?" asked to all respondents (600)
Detection and response are the present and future
Our customers tell us they cannot define all the rules around data movement given the number of new technologies the business requires to remain competitive and the employee needs. In fact, our own recent survey of customers found that half of the respondents have given up on Data Loss Prevention (DLP) technology due to challenges classifying data, policy creation and maintenance and heavy user endpoint impact of the DLP software. 13 out of 14 customers from our recent survey emphasized they are leaning more heavily on detection and response capabilities to tackle data exfiltration channels that are not effectively protected today with their current security stack. In fact, half of our top customers told us that they’ve completely given up on traditional DLP tools to stop users leaking data, intentionally or in malicious fashion.
The upside of using an endpoint user and data activity-based detection and response approach is that it allows the company to give more freedom to employees while providing the organization with better insider threat security. At the same time, with no gaps in technical visibility across any application, data, or user action on the endpoint, the firm can verify the trust isn’t being misused.
