Web Security
 Information Protection
Information Protection
Protect your people against advanced web threats
Proofpoint Web Security services protect against advanced threats as your users browse the web. It provides you with advanced security on a highly scalable cloud-based architecture. And it delivers threat protection and access control that’s easier to manage and deploy than legacy solutions.
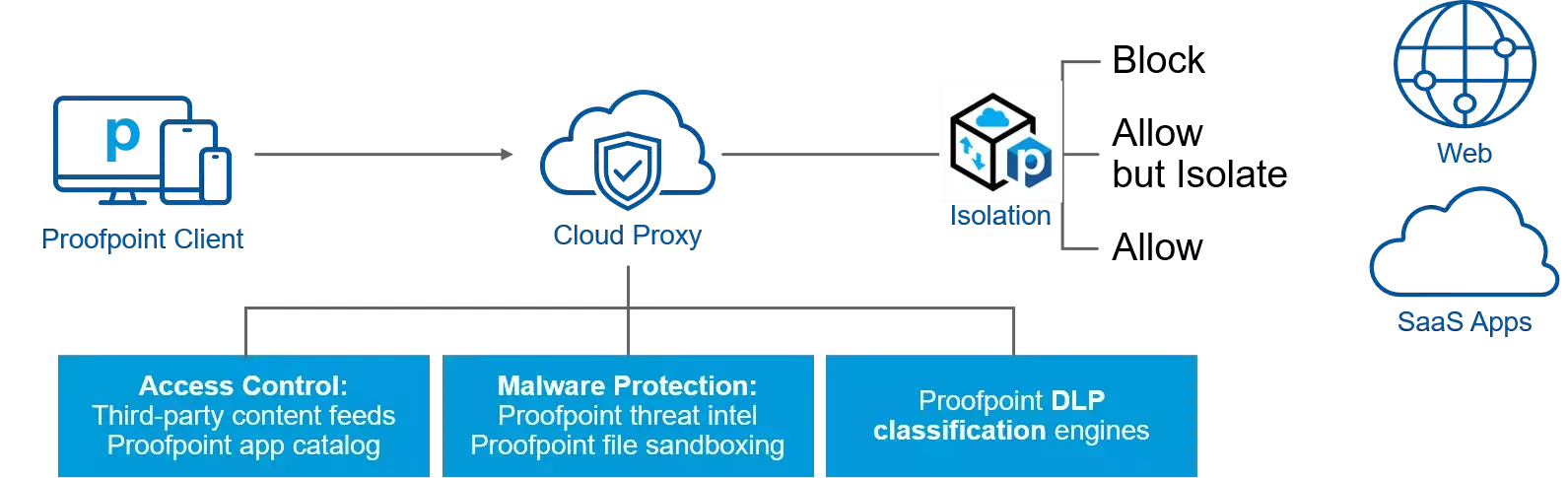
Features
Stay ahead of attackers with adaptive email threat intelligence
Advanced web threat protection
Web Security gives you industry-leading threat detection that’s powered by Proofpoint Threat Intelligence. It’s built on a scalable cloud-based architecture, and it automatically blocks your users from threats as they browse the web. This means they get the same level of security whether they browse from inside your organization or from a remote location. So it keeps your people and your organization safe.
- Block access to known malicious sites automatically
- Experience reputation based cloud web security threat detection and prevention based on Proofpoint industry leading threat intelligence
- Get deeper sandboxing for unknown sites
- Gain deeper visibility in cloud-based threats
- Reduce organizational risk associated with cloud-based threats
- Deploy easily across your organization with simple security rules
People-centric access control
With Proofpoint’s Web Security services, you can address internal and external requirements for user web access from managed devices. This easy-to-use tool helps you streamline access control with a people-centric approach. It also gives you visibility and control for potentially malicious ShadowIT apps. Beyond the traditional block rules, you can also opt to isolate specific web traffic. This allows your users to access sites while reducing risk to your organization.
- Gain domain-, URL- and IP-based access control
- Get inline detection and enforcement of ShadowIT apps
- Enforce access control with integrated isolation or customizable block page
- Get full visibility and control into web traffic with SSL decryption
Data loss prevention
It’s important to ensure that your organization’s confidential data and resources aren’t stolen or lost. That’s why Proofpoint’s web threat protection takes a people-centric approach to protecting data while users are on the web. Web Security integrates with our market-leading data loss prevention (DLP) capabilities to ensure that your organization’s data stays secure, whether your users access it from within or outside the workplace.
- Get inline and integrated DLP for SaaS applications
- Isolate web traffic to prevent uploads/downloads and prevent copy/paste functionality
- Easily apply rules to your entire organization, groups or specific people
- Choose predefined detectors, dictionaries, smart identifiers and exact data matching based on your organization’s needs
Cloud-based management
Web Security is an easy-to-use cloud-based management tool. And we make it a simple process roll the solution out to your entire organization. Web Security is distributed globally, which ensures that your users have a low-latency experience. This also cuts down on frustration. And our management tools are API based to enable remote management. What’s more, it integrates seamlessly with other Proofpoint Cloud Security solutions.
- Get a cloud-based and globally-distributed proxy
- Manage from a cloud-based console
- Experience built-in SSO integration
- Get user provisioning with IdP
- Send logs to your organization’s existing SEIM
Seamless isolation integration
Looking for more than simply allowing or blocking? With seamless integration between Web Security and Proofpoint Browser Isolation, it’s easy. For sites that are unknown, suspicious, or personal use, such as email or banking, you can specify that those pages open in Browser Isolation. This allows your users to browse the web, while you keep them protected against web security threats from those pages that may impact them or their devices.
- Gain near-zero security risk for your corporate assets, so there’s no need to inspect and unknown, suspicious and personal web traffic
- Protect employee privacy
- Monitor what matters without violating compliance standards
- Protect your users from phishing attacks in personal webmail
- Prevent external content, such as JavaScript or Active Content, to execute on corporate devices