Credential phishing remains a popular technique by malware campaigners, with Outlook Web Access credentials joining other webmail accounts as a frequent target. As the use of cloud-based documents becomes more and more widespread, phishing campaigners have also been leveraging this behavior as a lure for their messages, with some benefits for their credibility and effectiveness.
A recent example examined by Proofpoint researchers demonstrates the key ingredients of this kind of attack, as well as a clever innovation attackers have recently added. Google Apps credential phish are among the most common email-borne threats Proofpoint currently detects, and organizations that have adopted Google Apps for regular internal use are particularly susceptible to clicking.
In this example, rather than taking a potential victim straight to a (fake) login page, clicking the link brings up very realistic Google docs shared document landing page.
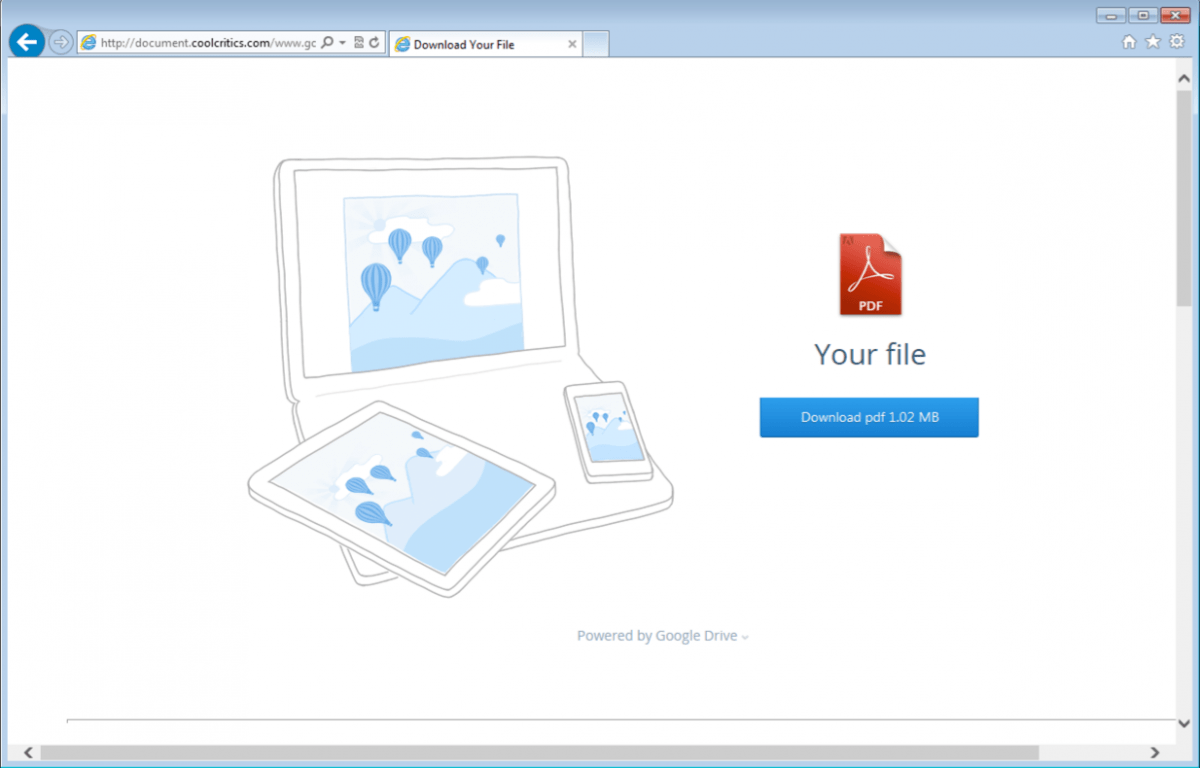
The page is a perfect replica of an authentic Google page, with the exception that it is delivered via HTTP, rather than HTTPS. Failing to notice this warning sign, the recipient clicks the Download button and then sees the Google login page, again almost identical to the authentic equivalent.
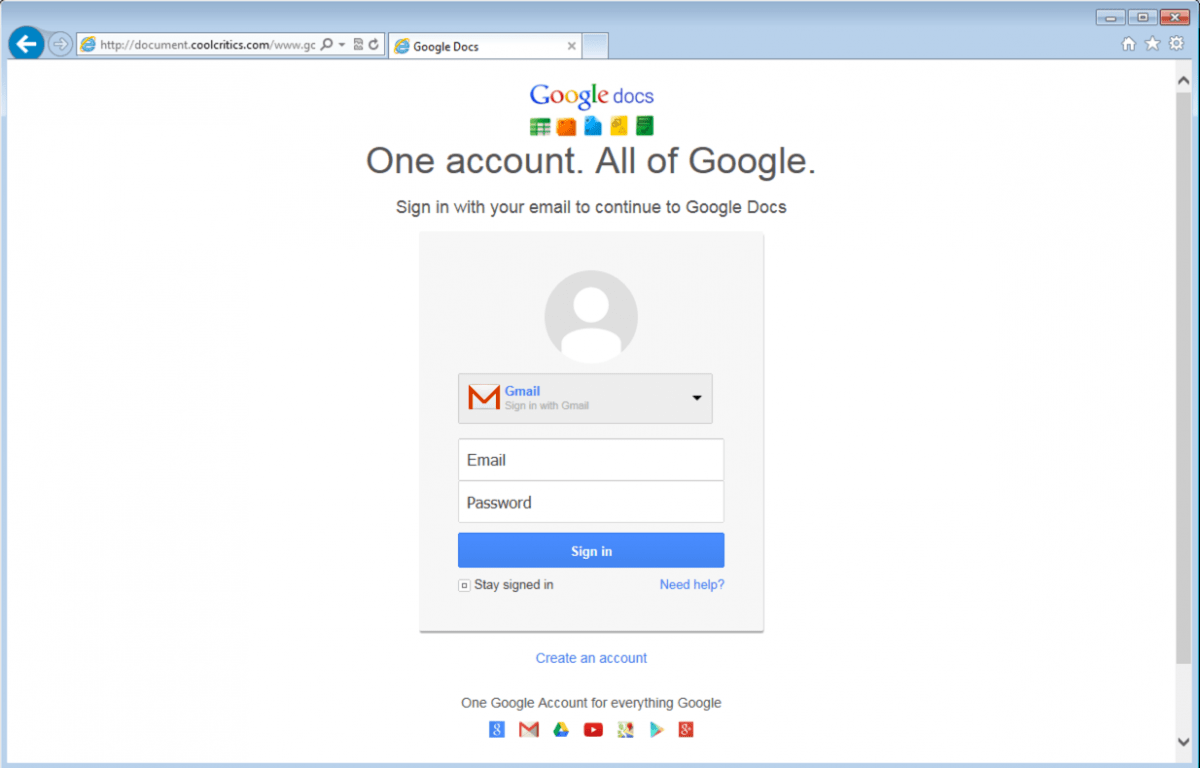
For added flexibility, the malicious document also supports logins for other webmail services, such as Yahoo, Hotmail, AOL, and even an “other” option in which the victim can enter any corporate credentials. This enables the attackers to extend their reach by pulling in and leveraging a wider range of credentials.
Credential phish normally drop their ruse after the victim has submitted their credentials, but in this case the attackers follow through with the ‘login’ by displaying an actual document.

This technique reduces the risk that a user will realize right away that something was amiss and giving the attackers more time to make use of the stolen credentials. Buying even a few hours gives the attackers more than enough time to leverage the victim’s stolen credentials to deliver the next round of messages.
Another advantage of launching credential phishing campaigns from compromised Google accounts is that a relatively minor effort delivers highly believable, targeted phish thanks to the ability to scrape the victim’s Contacts list and use it to populate the list of recipients for the next step of the campaign.
A similar attack technique employs a fake Dropbox document to capture credentials for the cloud-based document-sharing service. Like the Google Apps credential phish, the login page shown to the recipient is perfectly credible:

This example was taken from the cloud-document phishing campaign of an actor that tends to prefer campaigns with more limited scope, often distributing less than three URLs across 30-50 messages per week, often targeting on 10 organizations, but in some cases as many as thirty organizations. Initially targeting organizations in the advertising and hospitality sectors then leveraging these to target businesses in the financial sector, the attacker seems to be shifting strategy of late to be less targeted and much more opportunistic. As if to underscore the relative value of this technique, scraping email addresses from the advertising and hospitality services executive accounts led – intentionally or not – to targeting executives in the financial sector in successive rounds of phishing emails.
Hacking via cloud-based document services and application accounts adds still more options to the value of a hacked email account by creating more opportunities to create campaigns that are at once more targeted, more effective, and more lucrative. Credential phishing with cloud-based documents will continue to grow in popularity as attackers leverage its advantages to stay ahead of defenses that are often still focused on well-known and easily defeated techniques.

