Overview
Proofpoint researchers recently found a previously undocumented ransomware spreading since the end of March through Bedep after infection via the Angler Exploit Kit (EK). Combining our findings with intelligence shared by Frank Ruiz (Fox IT InTELL) lead us to the same conclusion: this project is conducted by the same group that was driving Reveton ransomware operations and is closely tied to Angler/Bedep. Dubbed "CryptXXX", this new ransomware is currently asking a relatively high $500 per computer to unlock encrypted files. Angler is the number one exploit kit by volume, making the potential impact of this new CryptXXX ransomware in the hands of experienced actors with access to this vector quite significant.
CryptXXX Ransomware Analysis
On April 15, 2016, we spotted an Angler EK into Bedep pass pushing both a ransomware payload and Dridex 222.
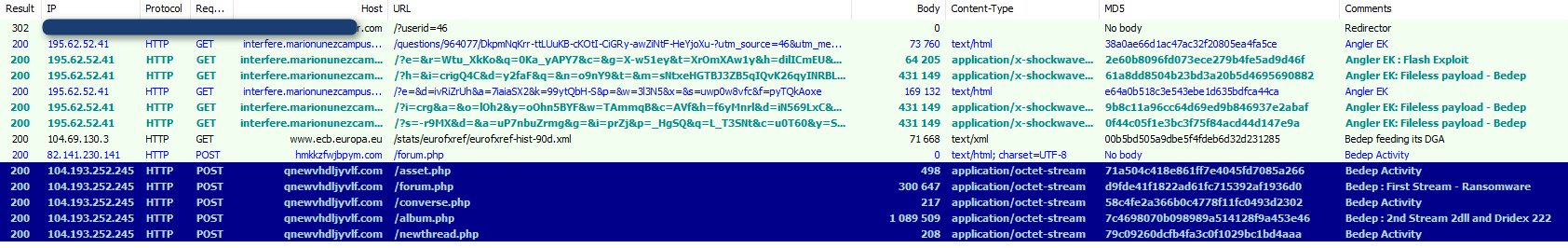 Figure 1: April 15, 2016 - UK - Redirector to Angler loading Bedep spreading a Ransomware and Dridex 222 among other payloads
Figure 1: April 15, 2016 - UK - Redirector to Angler loading Bedep spreading a Ransomware and Dridex 222 among other payloads
To alert the victim that they are infected and their files are encrypted, this ransomware creates three types of files, similar to many other types of ransomware (Locky, Teslacrypt, and Cryptowall):
- de_crypt_readme.bmp
- de_crypt_readme.txt
- de_crypt_readme.html
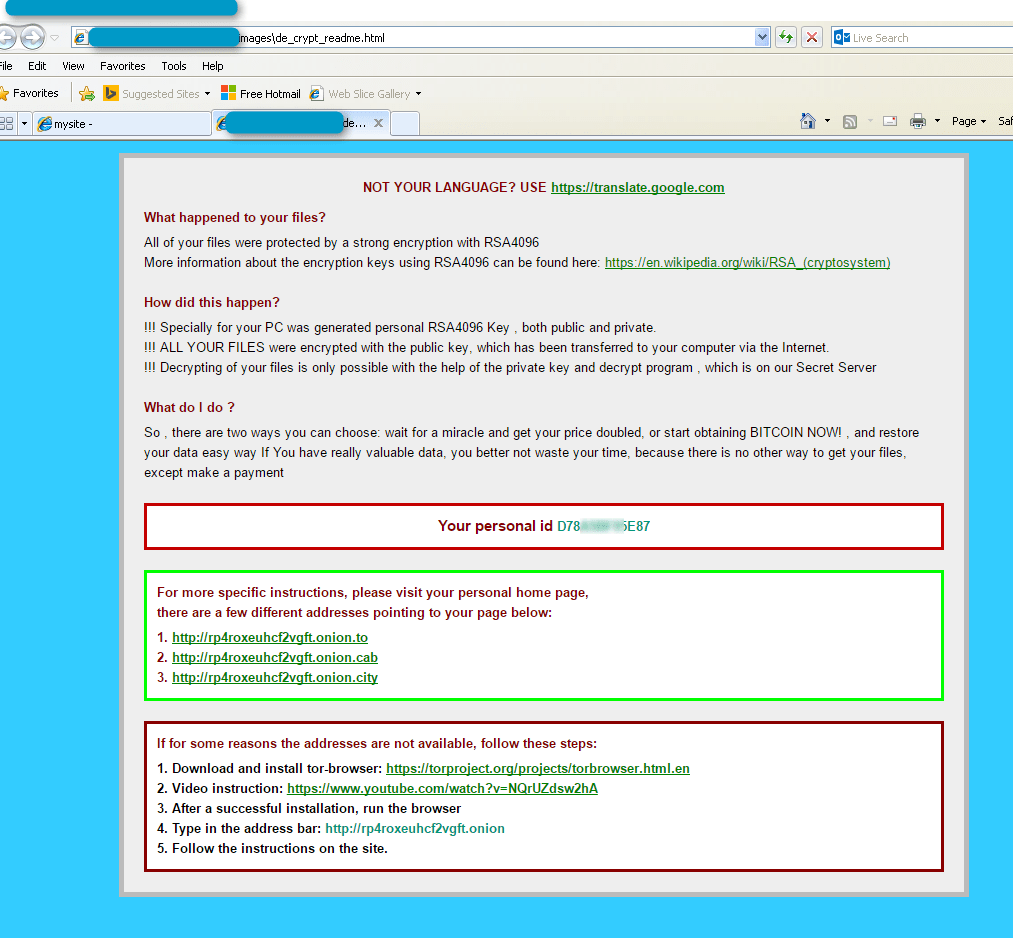
Figure 2: Ransomware user notification page
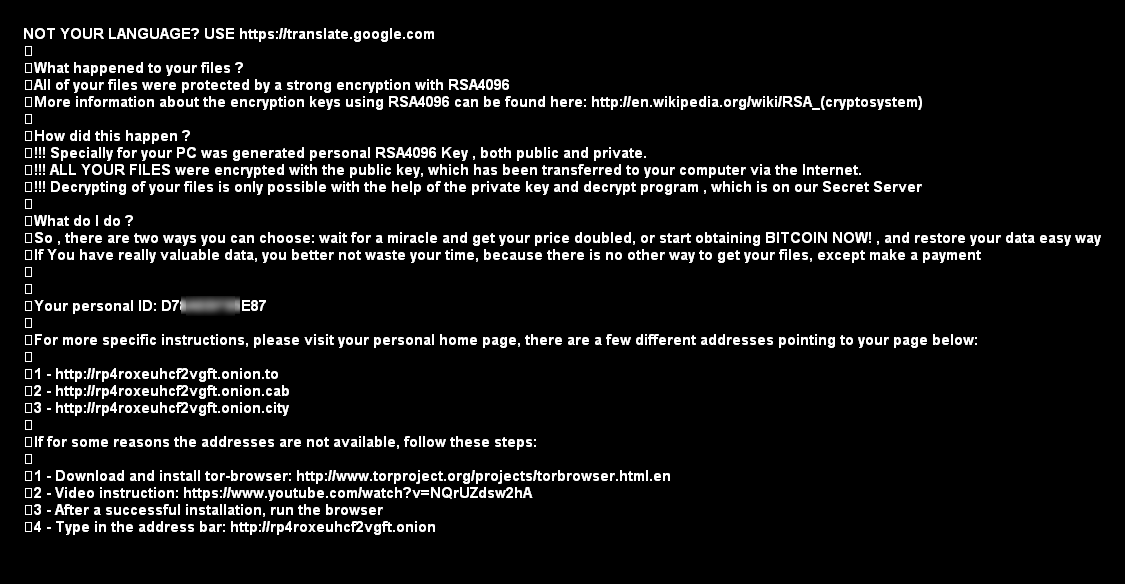
Figure 3: Ransomware black wallpaper
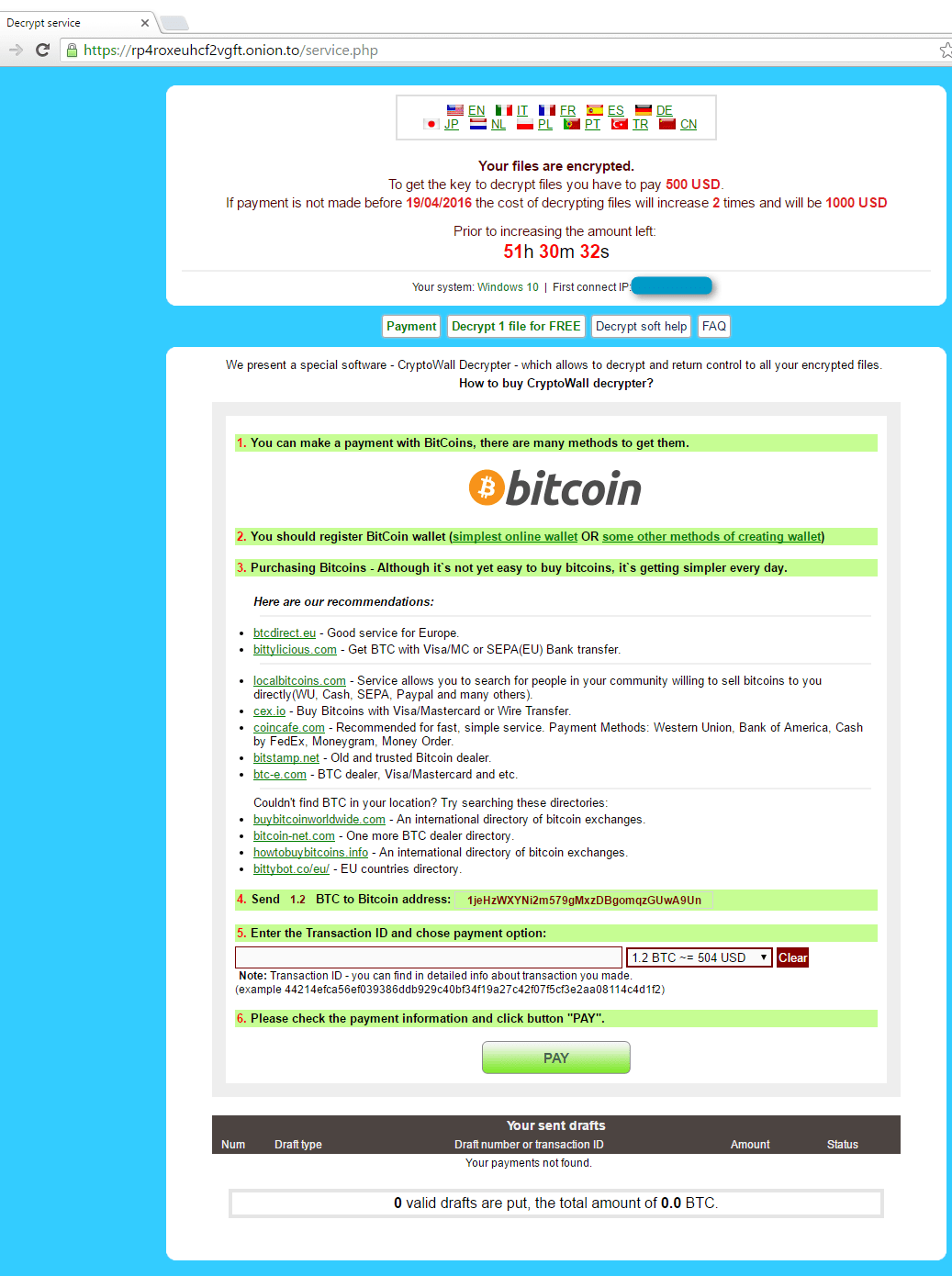
Figure 4: Payment site, with multi-language support (Languages available: EN, IT, FR, ES, DE, JP, NL, PL, PT, TR, CN)
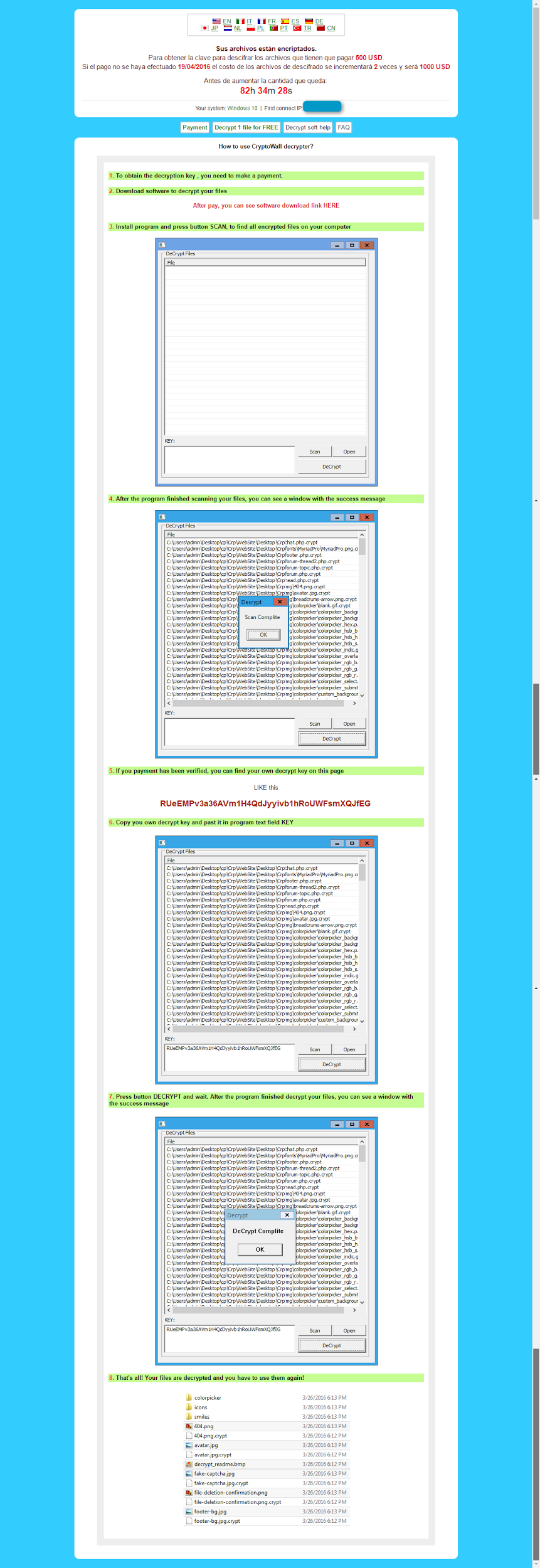
Figure 5: Payment site - Decrypt soft help
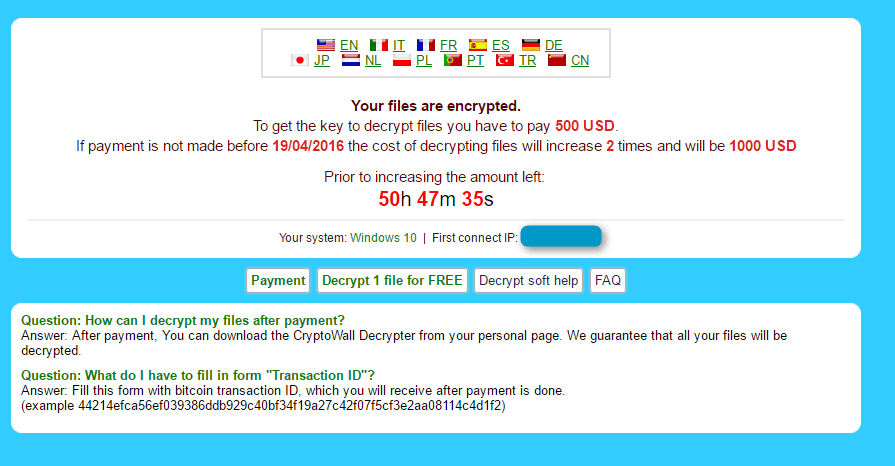
Figure 6: Ransomware payment site FAQ
Initially we could not connect this ransomware to any that we already know, but searching the Internet we found a forum thread [1] where victims first reported infections on the 31st of March. We decided to take a closer look and ran the full chain in a monitored environment:
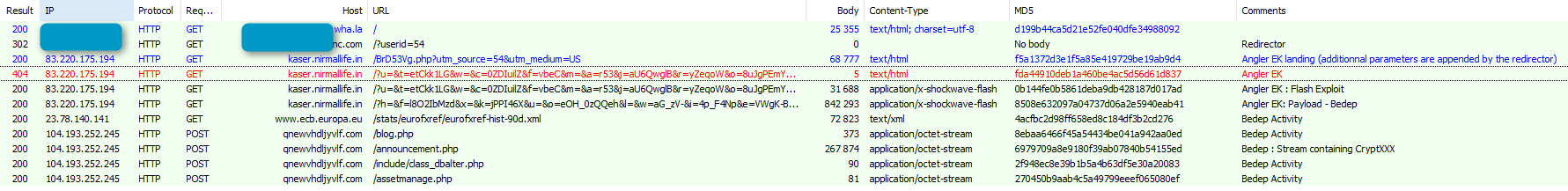
Figure 7: April 16, 2016 - a chain to CryptXXX
The ransomware is being shipped as a DLL dropped by Bedep in folders like those observed below in four separate infections:
-
C:\Users\%Username%\AppData\Local\Temp\{C3F31E62-344D-4056-BF01-BF77B94E0254}\api-ms-win-system-softpub-l1-1-0.dll
-
C:\Users\%Username%\AppData\Local\Temp\{D075E5D0-4442-4108-850E-3AD2874B270C} \api-ms-win-system-provsvc-l1-1-0.dll
-
C:\Users\%Username%\AppData\Local\Temp\{D4A2C643-5399-4F4F-B9BF-ECB1A25644A6}\api-ms-win-system-wer-l1-1-0.dll
-
C:\Users\%Username%\AppData\Local\Temp\{FD68402A-8F8F-4B3D-9808-174323767296}\api-ms-win-system-advpack-l1-1-0.dll
In real-world conditions, the start of this DLL is randomly delayed (for example, we saw 62 minutes):
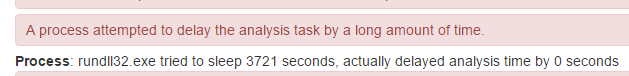
Figure 8: CryptXXX launch delay caught by sandbox analysis
The main advantage of this delay from a threat actor’s perspective is that the victim won’t be able to easily connect it to the infection vector (that is, to the compromised or malvertised website).
We saw the DLL executed in multiple cases with the entry function ‘Working’, but this will likely change in the future:
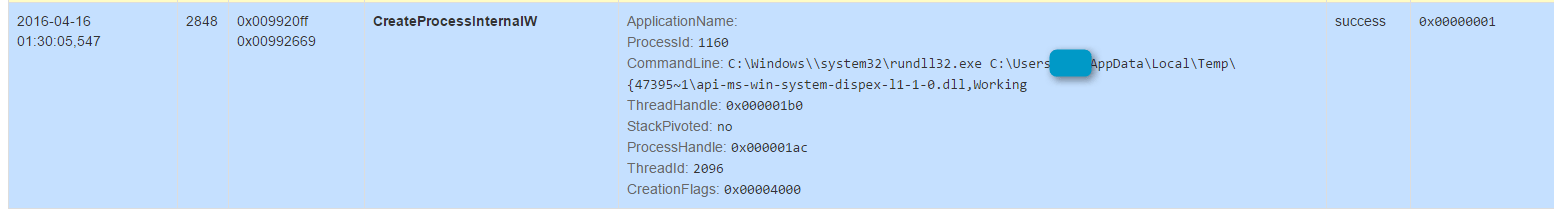
Figure 9: CryptXXX start command line
The ransomware has anti-VM and anti-analysis functions. In particular, CryptXXX:
-
Checks CPU name in the Registry
-
Installs a hook procedure to monitor for mouse events
When the ransomware actually executes, it encrypts files and adds a .crypt extension to the filename.

Figure 10: Sandbox output showing the most visible action to the victim
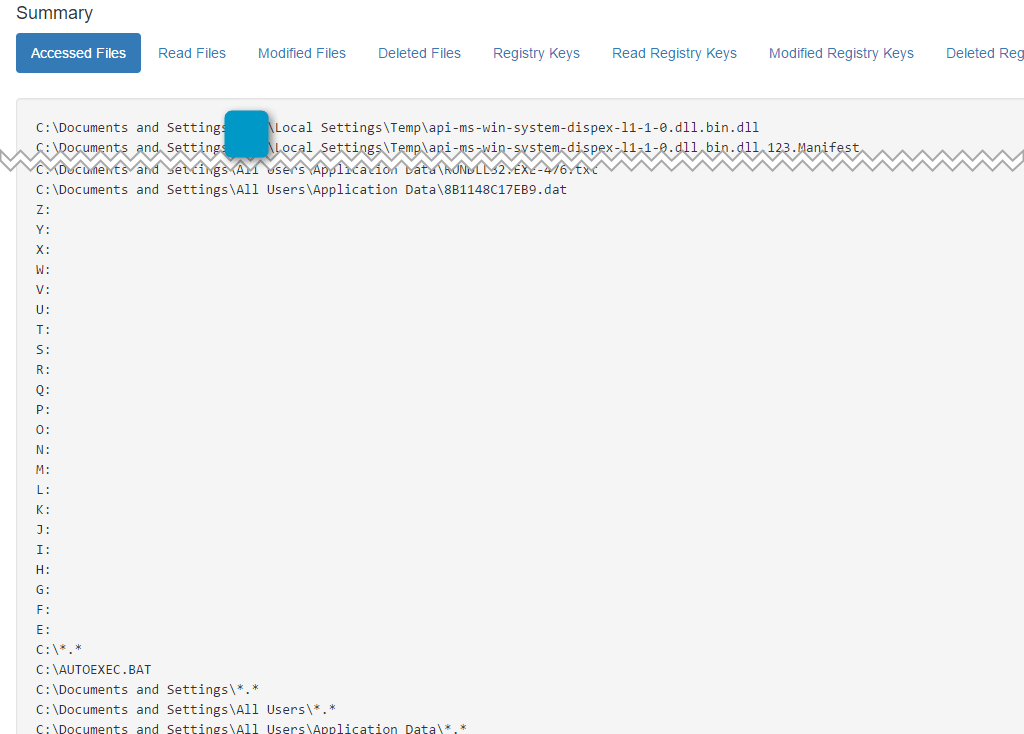
Figure 11: CryptXXX attempting access to all the possible mounted drives
The CryptXXX ransomware is not only encrypting files locally and on all mounted drives; it’s stealing Bitcoins and a large range of other data. We were expecting this because that instance of Bedep has a long history of dropping information stealers in its update stream. Specifically, it dropped Pony from November 2014 until mid-December 2015. It replaced Pony with an undocumented “private stealer” until mid-March 2016. We believe that the information stealing functions in this ransomware are the same as in the “private stealer” distributed by this instance of Bedep.
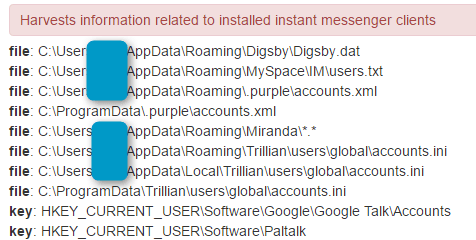
Figure 12: CryptXXX harvesting instant messenger client data
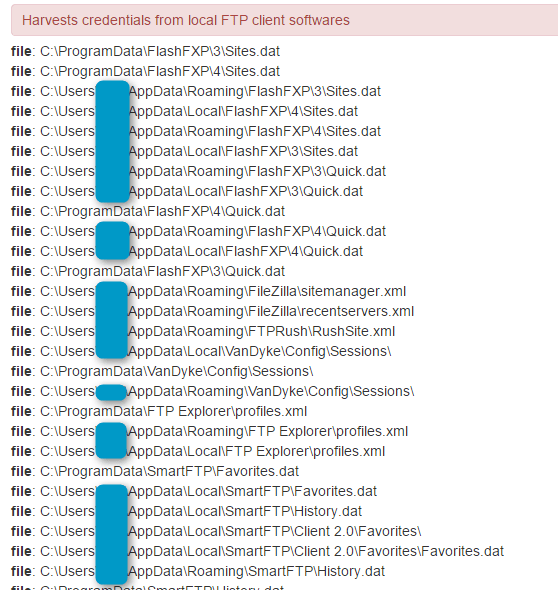
Figure 13: CryptXXX harvesting credentials from local FTP client software
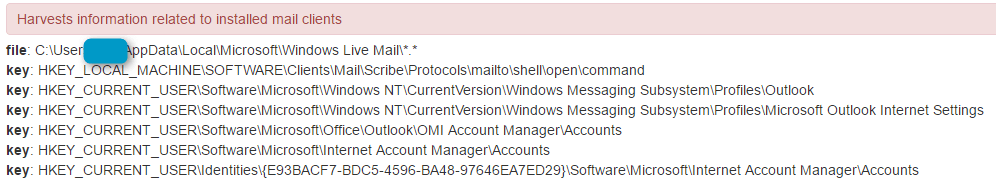
Figure 14: CryptXXX harvesting information related to installed mail clients
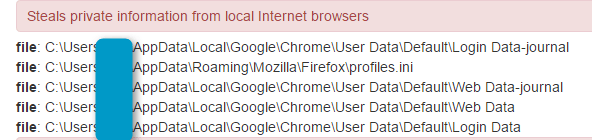
Figure 15: CryptXXX collecting browser data
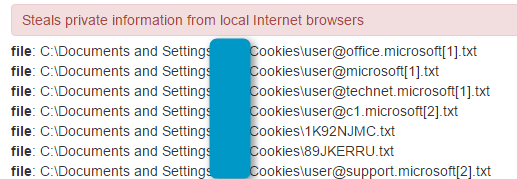
Figure 16: CryptXXX stealing cookie data
Affiliation
Based on the infection vector and its history, we suspected this new CryptXXX was directly connected to the Angler/Bedep team. We based the name of this ransomware on two strings found in the unpacked binary:
Z:\CryptProjectXXX\Loader\InstDecode.pas
Z:\CryptProjectXXX\Loader\DDetours.pas
Note, the real name of Angler EK is also XXX [2]. Additionally, the actor behind Angler EK was also behind Cool EK and Reveton [2][3].
Figure 17: Last known design of the Reveton Ransomware, February 2015 [5]
There are many similarities between Reveton and CryptXXX. Most notably,
-
Delphi programming language
-
Custom C&C protocol on TCP 443
-
Delayed start
-
DLL called with a custom entry function
-
dat file dropped in %AllUsersProfile% (For CryptXXX, it looks like code reuse as the file only contains the letter x)
-
Bitcoin and credential stealing functions

Figure 18: CryptXXX check-in caught by sandbox
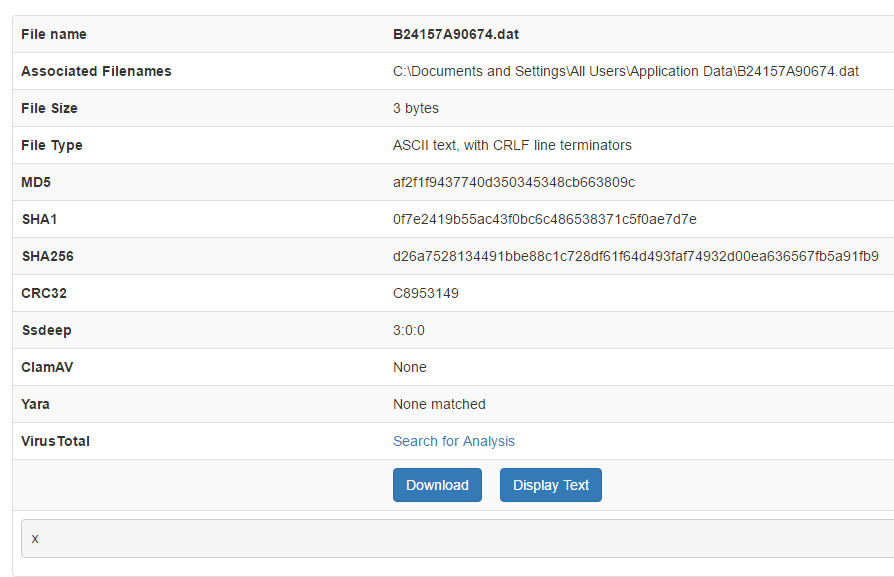
Figure 19: CryptXXX is dropping a .dat file containing only the letter x.
Conclusion
Based on threat intelligence shared by Frank Ruiz (Fox IT InTELL) and telltale signs uncovered in our own analysis, we are confident in the connection between CryptXXX ransomware and the Reveton Team. Given Reveton's long history of successful and large-scale malware distribution, we expect CryptXXX to become widespread. While we have observed many new ransomware instances in recent months, many have been written and/or distributed by less experienced actors and have not gained significant traction. Those associated with more experienced actors, however, (such as Locky) have become widespread quickly. Based on the large number of translations available for the payment page, it appears that the Reveton team shares those expectations.
Acknowledgement
Thanks to Frank Ruiz from Fox IT InTELL [6] for sharing strong clues confirming the relationship between CryptXXX and Reveton.
References
[2] - http://malware.dontneedcoffee.com/2015/12/xxx-is-angler-ek.html
[3] - http://krebsonsecurity.com/2016/04/blackhole-exploit-kit-author-gets-8-years/
[4] - http://malwdontneedcoffee.com/2013/10/paunch-arrestationthe-end-of-era.html
[5] - http://malware.dontneedcoffee.com/2015/02/RevetonWinter2015.html
[6] - https://www.fox-it.com/intell/
Indicators of Compromise (IOC’s)
|
IP/Domain |
Comment |
|
146.0.42.68 |
CryptXXX checkin server |
|
rp4roxeuhcf2vgft.onion.to |
CryptXXX payment site |
|
rp4roxeuhcf2vgft.onion.cab |
CryptXXX payment site |
|
rp4roxeuhcf2vgft.onion.city |
CryptXXX payment site |
|
104.193.252.245 |
Bedep C&C IP |
|
md5 |
sha256 |
Comment |
|
3776ec795ef3aa649ff48fcf83c87713 |
41dbbc60b8921709c5eb187cf03e60701e3b172e6deebdb67dd66c8cb3666b90 |
Zip archive with most of the mentioned content |
|
17697e1829f0d18d2051a67bc2bca134 |
ab7a58b6e50be6b9bcb926c550ff26669601bbd8bfd922a5b32756e663b25a67 |
Bedep 1809 first stream dll CryptXXX |
|
d4439055d2d63e52ffc23c6d24d89194 |
1036c84a003378907560356642bb065caef961f9dbc5c3b2a4954d5cbe7100df |
Bedep 1809 update stream dll1 |
|
3e75e8238a6bbd8817164658696198af |
1036c84a003378907560356642bb065caef961f9dbc5c3b2a4954d5cbe7100df |
Bedep 1809 update stream exe2 - Dridex 222 |
|
de882c049be133a950b6917562bb2313 |
e53610a977b65c01b275e37aefad7884368dfe00b50750e35b6c8c87556a2c06 |
Bedep 1809 update stream dll3 |
|
bfb8f7f6cbe24330a310e5c7cbe99ed4 |
a4e9c151a50595b59e787dd3b361ac53d02dd7f212d6b22639dc01776c886d05 |
CryptXXX |
|
0c3431dbb8cd0478250eb4357257880e |
565dadb36e1d8b0c787d0d5e4cd7ec8c24cac1d6b37637427547ae465ab0fff0 |
CryptXXX |
|
cd2d085998a289134ffaf27fbdcbc8cb |
0b12584302a5a72f467a08046814593ea505fa397785f1012ab973dd961a6c0e |
CryptXXX |
|
d65f155381d26f8ddfa304c83b1ad95a |
eaa857c95fca38ca08411b757f4ad2a841cfb9782deca8abf64aada445923c0d |
Bedep “Private stealer” |
|
b824d94af0f981106ec2a12d0c4cc1c0 |
5bfae47c9fda81243b50b6df53ac4184d90a70000894fa2a516044fa44770cfd |
Bedep “Private stealer” |
|
971c578c9dea43f91bfb44ceac0ee01d |
59ddf36a9e85f4cf82a6511b49cfcdd9e4521b17f7e245f005e18418176ff4aa |
Bedep Pony “news.php” (May 2015) |
|
70a377690917a98e6ee682f7941eb565 |
ad3cc219a818047d6d3c38a8e4662e21dfedc858578cb2bde2c127d66dfeb7de |
Bedep Pony “news.php” (December 2015) |
|
728733095fe2c66f91a19ebde412dd25 |
dff7c0aac326f210705e4f53cd78a57cb277e80ecec7bdffd6f68db3bdda39c3 |
Reveton - 2015-04-14 |
Select ET Signatures that would fire on such traffic:
2819805 || ETPRO TROJAN CryptXXX Ransomware Checkin
2819806 || ETPRO TROJAN CryptXXX Possible Payment Page
2021418 || ET TROJAN Bedep HTTP POST CnC Beacon
2022467 || ET TROJAN Bedep Connectivity Check M2
2811284 || ETPRO CURRENT_EVENTS Angler or Nuclear EK Flash Exploit M2
2815452 || ETPRO CURRENT_EVENTS Angler EK Landing/RIG EK Landing Dec 23 2015 Common Construct
2815888 || ETPRO CURRENT_EVENTS Possible Angler EK Landing Jan 21 M3
2816926 || ETPRO CURRENT_EVENTS Possible Angler EK Landing URI Struct M5 Apr 06
2816932 || ETPRO CURRENT_EVENTS Angler EK Landing with URI Primer Apr 06
2816933 || ETPRO CURRENT_EVENTS Angler EK Apr 07 2016
2816941 || ETPRO CURRENT_EVENTS Angler EK Flash Exploit URI Struct Apr 07 IE
2819646 || ETPRO CURRENT_EVENTS Angler EK Payload Apr 08 2016