Yesterday we learned about two hardware bugs dubbed Meltdown and Spectre that allow normal, low privileged user programs such as database applications or JavaScript in web browsers to access what the kernel memory has been designed to hide. As patches are becoming available, organisations will experience up to a 30% hit to their CPU where Intel chips reside.

A Simple Explanation of the Kernel
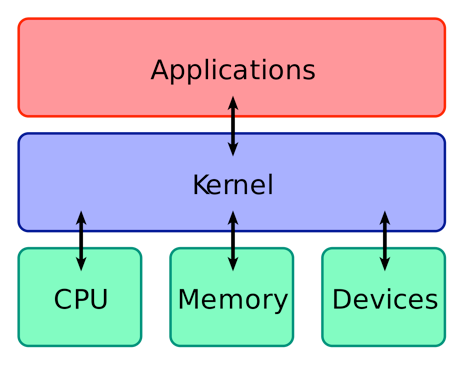
The kernel is the core of your computer’s operating system. It is the layer in your OS that exists between your applications and the CPU and memory itself. It also helps applications reach device drivers, as seen in this simple block diagram below.
Within the process address space, usually, a set of kernel space pages are added and protected from user level access to allow for faster context switches between user space and the kernel space. However, Meltdown and Spectre side-channel attacks can provide access to the content of that memory. The current kernel-level workarounds being implemented separate the user-space and kernel-space page table, but this introduces a large penalty on context switching. Of course, with this overhead comes a massive performance hit on the chip’s performance. AWS and Google report that all systems have already been patched; Linux, Xen and other patches are already available.
What are the Security Implications?
As a security professional, you as always have to measure the impact of agent-based solutions. Access to kernel space has been tricky for security teams long before today’s Meltdown and Spectre news. Once a user gains access to kernel space, he can manipulate just about anything (think DLOGGER.) Talk about the ultimate threat coming from inside your network.
The vulnerability enables the kernel of critical servers and workstations to be exploited easily by installed applications and used as a weapon by insiders – either maliciously or by well-meaning employees who inadvertently install the applications providing access to hackers. A process as simple as hosting an application in a private or public cloud can open the door to both internal and external attackers to unearth stored passwords, encrypted patient or customer information, company IP, or sensitive content.
With the current trend of so many organisations migrating to hosted cloud environments, this is sure to be a concern as the vulnerability affects the three major cloud hosts: AWS, Microsoft Azure, and Google Cloud.
Vulnerability is a concern, but so is the performance hit to the end system. Some tools deployed (but not always designed) with security in mind can wreak havoc on a system (and the sleep patterns of IT security architects). Kernel-level agents such as DLP or EDR are notorious for blue-screens, continuous reboots, heavy hooks into browsers like Chrome, and requirements for browsers to be kept up-to-date. Inevitably, this leads to sparring matches for CPU utilisation which can bring even the most sophisticated company’s machines to their knees. Luckily, like AMD or the wry acronym termed by the Linux kernel team describing an isolation of kernel processes with memory, there are alternatives to the problem: user-level agents.
The User-Mode Agent Advantage
User-mode agents like Proofpoint's Insider Threat Management solution are a game-changer. There is no reboot, no need to hook into applications or web browsers, and an undimmed detection capability into risky behaviour on a machine in real-time. For this reason, security professionals are moving to the truly “lightweight” agent. Agent fatigue is a real issue, so when you’re looking at an agent based vendor that claims to be “light-weight” be sure to ask if the agent is kernel-based, what performance hit the agent will introduce, and how the CPU performance hit affects the agent.
As it relates to the recent vulnerabilities, the Proofpoint agents consist of applications that depend on user space interactions which rarely introduce additional context switches. Patches to fix the Meltdown vulnerability will primarily affect applications that make continuous calls into the kernel because a mandatory page remapping has been added to every kernel system call, increasing processing time.
The endpoint is the new perimeter and should be secured, agent-based security software is the best way to collect meaningful data and act on cyber incidents. However, it can’t be at the cost of day-to-day performance. Hold your security vendors accountable for agent impact.
Put our agent to the test today.
