
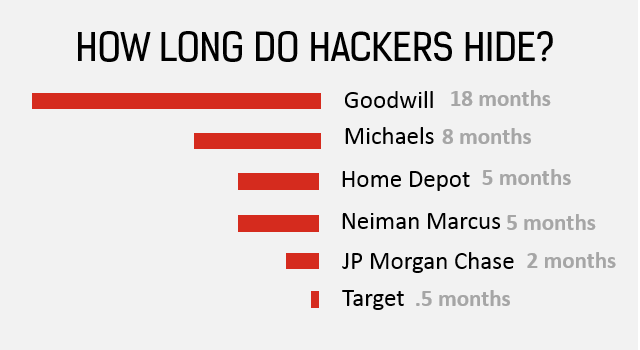
Companies like JPMorgan Chase have hundreds of employees and spend millions of dollars to prevent cyber theft. So how is it possible that hackers gained access to their system for 2 MONTHS before being detected?
In fact, this is actually pretty common. Michaels, the crafts store chain, was breached by hackers for 8 months before noticing. The thrift store, Goodwill, had hackers in their system for a year and a half!
Why so long? Hackers usually won’t find exactly what they are looking for the second they gain access to a system. It may take further searching or they may have to break other levels of security before they find credit card numbers or whatever other information they may be after. Once they do find the information, it may take them awhile to extract it without being detected.
That’s the why. So how do hackers stay undetected for so long?
Too much noise
When hackers were inside the credit card system of clothing retailer Neiman Marcus they set off almost 60,000 security alarms. Unfortunately, the alarms made up less than 1% of the alerts on their daily security logs.
The fact is that most security systems flag so many incidents it is easy for real threats to get lost in all of the noise. The Neiman Marcus hackers named their malicious software something similar to the company’s payment software, making it even less likely that someone would notice them.
Intermediary Computers
In order to raise less suspicion, hackers also route data through intermediary computers. If the security system notices that the system is being accessed by a suspicious computer, such as one in a country where hackers are predominant like Russia, then it may flag that as a security concern. If the system thinks it’s being accessed by a computer in a school or other less assuming location, it is less likely to raise an alarm.
Fixing Security Flaws
In order to cover their tracks, sometimes hackers will fix the security flaw that granted them access to the system. This way, when system administrators are looking for potential weaknesses in the future, there won’t be any concern.
If they were able to find a security flaw, admins could use an activity monitoring tool to see if anyone took advantage of that flaw in the past.
Remote Vendor Access
Allowing 3rd party vendors access to the company’s system is becoming a more common practice. Unfortunately, many companies don’t take the necessary precautions when giving others access. Some companies may see their vendor access the system and not pay attention because they trust that vendor.
In reality, a vendor’s login information could have been compromised by theft or by an inside employee. Monitoring user activity is a necessary practice to make sure your information is safe.
With all of the tricks hackers have to stay undetected in your system, it is even more important to carefully and thoroughly monitor it. After their hack, JPMorgan pledged that it would place a much higher priority on cyber security. By the end of 2014, they will have 1,000 employees and $250 Million a year devoted to cyber security.
The longer a hacker goes undetected in your system the greater the chance that serious data will be leaked and the more chances they’ll have to use that data. Most businesses can learn from these mistakes now so they can detect threats sooner and end them before a small breach becomes a big problem.
To learn more about how to protect your company data when working with contractors, download our latest eBook: Strangers in Your Servers: Making Working with Contractors More Secure
