If you ask the folks at Forrester Research, they’ll probably tell you that most organizations still have a long way to go on the road to implementing zero trust security. Partially, “because they're not sure of the concrete technology purchases and organizational changes needed to do so.”
Which is why Forrester introduced the Zero Trust eXtended (ZTX) framework—to help enterprises perform strategic decisions and map their technology purchases to the implementation of a Zero Trust ecosystem.
As zero-trust pioneers, we’re very enthusiastic about Forrester’s ZTX initiative. We will briefly examine the key pillars of the ZTX framework and outline how the Proofpoint Meta NaaS capabilities map into ZTX.
ZTX Framework Key Pillars
Forrester identifies several key pillars for identifying whether a technology or solution qualifies as a Zero Trust eXtended framework. Following is a brief description of each, but you can read about them in more detail in Forrester’s paper, The Zero Trust eXtended (ZTX) Ecosystem.
- Network: How does the technology enable network isolation, segmentation, and security?
- Data: How does it enable data categorization, schemas, isolation, encryption, and control?
- People: What does the solution do to secure the people using the network and business infrastructure? Does it reduce the threat that users create?
- Workload: Does it secure cloud networks, apps, and other things used to make businesses operate technically?
- Devices: Does it always isolate, secure, and control every device (including mobile devices) accessing enterprise resources?
- Visibility and Analytics: What kinds of useful analytics and data points does it provide?
- Automation and Orchestration: How does it automate Zero Trust principles? How does it provide more control of disparate systems?
Network Isolation
The Proofpoint Meta approach to network isolation and segmentation establishes one-to-one dynamic segments between individual users and applications or resources, according to policy. With Proofpoint Meta, all assets are isolated and hidden unless explicitly revealed by a policy. Once users are authenticated and verified, they are exposed only to the resources they are allowed access to – the ones they truly need -- in order to dramatically reduce attack surface and lateral movement.
Data Security
Proofpoint Meta secures data connections, regardless of user location. When working on non-secure networks like hotels and coffee shops, data is encrypted as it travels to its business destinations. Every packet that traverses the secure Proofpoint Meta NaaS is embedded with a unique ID allowing not only continuous policy enforcement, but also rich data analytics based on user and machine traffic.
People
Rather than positioning the data center as the primary security entity, Proofpoint Meta focuses on the individual user, offering a software-defined perimeter that follows each device regardless of location.
Proofpoint Meta’s distributed cloud network embeds user/device identity at the packet level for continuous verification after initial authentication, plus authorization through integration with next-gen IAM providers. All network activity is monitored and logged for alerting and analytics.
Proofpoint Meta treats device security as an inherent aspect of network access. Posture checks are performed before granting access; if checks fail, access is either denied or restricted according to policy. Policies automatically adapt according to whether users are on- or off-site and working on a managed or personal device.
Workloads Across Data Centers and Cloud
With today’s distributed cloud computing, it’s not uncommon for a remote employee to require simultaneous access to a manufacturing system in the data center, a supply chain app hosted on AWS, and a CRM system hosted on Azure.
Proofpoint Meta creates secure “zones” in data centers and cloud deployments that enable isolating workloads and protecting them individually. Proofpoint Meta NaaS inherently supports multi-app, multi-cloud connectivity. Multi-vendor, cross-cloud workloads are enabled via lightweight SDP connectors, which provide a secure authenticated interface between existing servers and the Proofpoint Meta cloud. Connectors are delivered as a virtual machine (VM) image for deployment in enterprise data centers, local private cloud environments such as VMware, or public cloud environments such as AWS EC2.
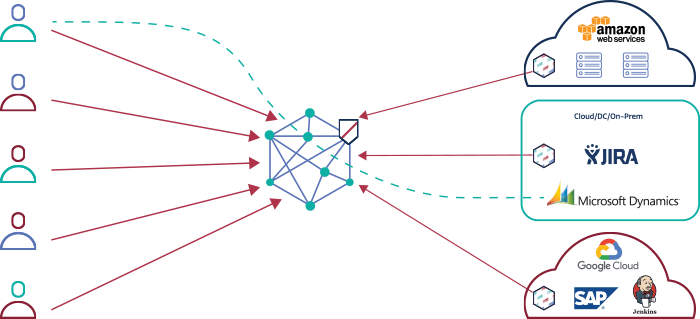
Proofpoint Meta’s lightweight SDP connectors provide a secure interface between existing servers and the Proofpoint Meta cloud to facilitate micro segmented user access to applications. For example, the above architecture shows the Meta Networks cloud with 3 SDP connectors for AWS, Jira and Jenkins.
Securing and Controlling Every Device
Proofpoint Metas’ identity-based, zero-trust approach enforces a custom policy for each user device. At the same time, it offers flexibility for IT managers to define the exact security approach for different devices, access methods and authentication method.
Devices can assigned privilege-based access to any application or network resource allowed by their policy. Access can be implemented using full tunneling to route all traffic through a secure tunnel, or alternatively, using split tunneling to separate enterprise traffic from internet traffic. Resources or applications including web, RDP and SSH often used by external contractors can be allowed access via the browser.
Administrators can choose from a variety of different authentication methods for devices including username/password, two-factor authentication (2FA), or single sign-on (SSO) using an IdP. They can also apply posture checks to ensure the device is compliant with an enterprise policy, such as running a pre-defined AV, or joined to an AD Domain.
Visibility and Analytics
Proofpoint Meta provides alert/log data for custom-defined or recommended policies and risky activity. For example, Proofpoint Meta logs all network traffic and enriches it with the user identity and information to trigger security alerts such as unauthorized attempts to access network resources, change access policies, or failed logins. Integration with SIEM systems is available for additional analysis, audit, anomaly detection and additional UEBA.
Automation and Orchestration
From an IT perspective, Proofpoint Meta makes it easy to centrally manage all access to enterprise applications and data, regardless of physical location or use of modern or legacy technology. There are no appliances to install/configure/sync, and the network is inherently zero-trust, meaning all resources are isolated and hidden unless access is explicitly granted (i.e. no manual network segmentation).
All control and visibility features of Proofpoint Meta NaaS are accessible through our 100% API first approach, so integration to third party RESTful-enabled systems can be used to automate any aspect of enterprise security and networking.
Learn More
The Zero Trust Framework is an effective paradigm for enterprise security that addresses the way organizations do business today. Learn more about how Proofpoint ZTNA can support your Zero-Trust Strategy here.
