Phishing is nothing new. In fact, 2016 marks the 20-year anniversary of the first time the term was used online, although it took several more years for the term to hit the mainstream. With early roots in AOL account abuse, Nigerian advance fee fraud, and other scams, phishing is alive and well.
Phishing, however, has evolved dramatically as the technology has improved and our reliance on online services has increased to the point of ubiquity. Now phishers use sophisticated malware in documents attached to emails and links to malicious websites to collect credentials and personal and business information. We outline this trend in our report The Human Factor 2016:
"URLs linking to credential phishing pages were almost three times more common than links to pages hosting malware. Our researchers found that on average, 74% of URLs used in email-based attacks linked to credential phishing pages, rather than to sites hosting malware...In effect, the victim does the work of keyloggers, info stealers, and other automated malware that would have been used to steal this information in past campaigns."
It isn't just the technology behind phishing that has gotten more sophisticated, though. Cyber criminals continue to refine and differentiate their approaches and techniques.
Phishing is a bit like ice cream: plain vanilla is a classic standby with countless adherents, but you don't have to look too far to find just the right flavor for everyone. Targeted phishing schemes require more work on the part of attackers but tend to be much more effective at nabbing victims. Your users might not take notice of a vanilla cone, but a salted caramel gelato will likely grab someone's attention.
Plain vanilla phishing relies on high volume. If attackers send enough messages, someone will click through and divulge personal information—or more likely, credentials for a corporate network, database, cloud service, or banking site.
But many of these messages are no longer as effective as they once were. That’s why attackers are turning to lures with higher click rates. Click-through rates from lures related to Google Drive and Dropbox, for example, were four to five times higher than those for PayPal or Apple Pay, according to The Human Factor 2016 report.
More effective lures in large-scale campaigns are just the beginning of improved targeting and social engineering, though. But phishing isn't just about stealing credentials. As Verizon explained in its 2015 Data Breach Investigations Report,
"Phishing campaigns have evolved in recent years to incorporate installation of malware as the second stage of the attack...phishing [is] a favorite tactic of state-sponsored threat actors and criminal organizations, all with the intent to gain an initial foothold into a network….for two years running, more than two-thirds of incidents that comprise the Cyber-Espionage pattern have featured phishing."
This week, Proofpoint published research on an advanced persistent threats (APTs) targeting Indian diplomatic interests in Saudi Arabia and Kazakhstan. A key component of these was a set of targeted emails to Indian Embassies in these countries. Palo Alto Networks also published research on a carefully crafted and spoofed email targeting the Indian Ambassador to Afghanistan, "commending the Ambassador on his contributions and success." Documents attached to these emails could drop remote access tools (RATs) on vulnerable machines.
While these sorts of attacks may feel distant to the average business user, they are just two examples of the broader trend towards "impostor email threats." Last year, the FBI warned about "business email compromise" (BEC), also known as CEO fraud. In one well-publicized example, an accountant with a large supply chain and logistics company wired $480,000 to an account in China at the apparent behest of his CEO. The lure email played on the known close relationship between the CEO and the accountant and, in typical BEC fashion, asked the accountant to correspond only with the sender via email and not discuss the details with anyone else ("to avoid violating SEC rules").
Impostor email threats were launched into the news with Snapchat's announcement that its human resources department had turned over payroll information on current and former employees after attackers spoofed an email from CEO Evan Spiegel.
Proofpoint itself received a similar set of emails, also targeted at people in human resources, with spoofed senders including our CEO and internal HR staff:
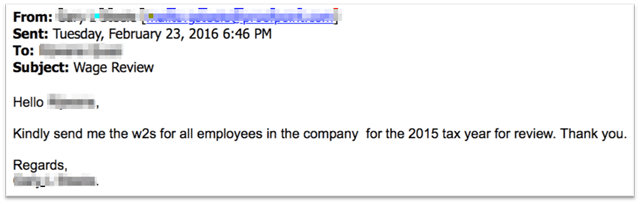
Fortunately, both our systems and savvy end users identified the emails for what they were. But this kind of targeting and spoofing is highly effective in convincing users to take action. These kinds of campaigns can be especially challenging for email gateways to detect as well since they rarely contain malicious documents or URLs that have been traditional hallmarks of spam and phishing. Imposter email threats often make use of LinkedIn to mine internal contacts and executive information to target specific departments such as HR and finance.
And there's the rub. We continue to see high volumes of phishing emails (both "vanilla" and targeted) because they work and cyber criminals follow the money. At the same time, though, both approaches to phishing and the underlying technology are evolving quickly to make attackers more effective and go after bigger payoffs.
Learn more about email phishing and business email compromise with Enterprise Email Protection.