The Cybersecurity Stop of the Month blog series explores the ever-evolving tactics of today’s cybercriminals. It also examines how Proofpoint helps businesses to fortify their email defenses to protect people against today’s emerging threats.
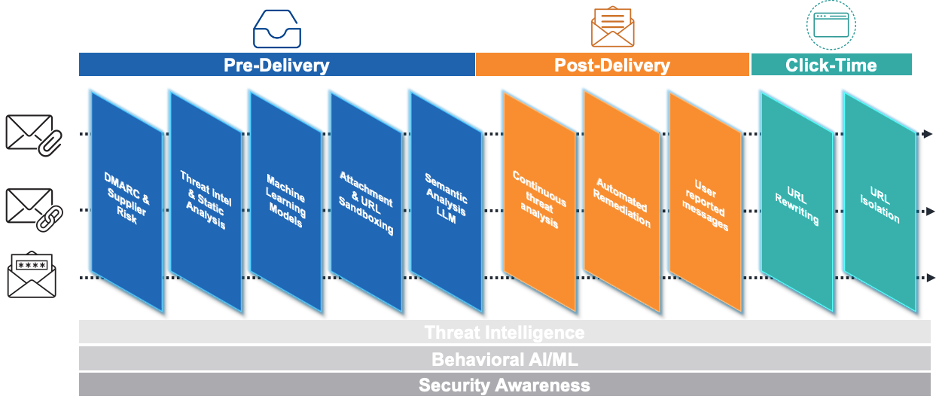
Proofpoint people protection: end-to-end, complete and continuous
So far in this series, we have examined these types of attacks:
- Uncovering BEC and supply chain attacks (June 2023)
- Defending against EvilProxy phishing and cloud account takeover (July 2023)
- Detecting and analysing a SocGholish Attack (August 2023)
- Preventing eSignature phishing (September 2023)
- QR code scams and phishing (October 2023)
- Telephone-oriented attack delivery sequence (November 2023)
- Using behavioural AI to squash payroll diversion (December 2023)
- Multifactor authentication manipulation (January 2024)
- Preventing supply chain compromise (February 2024)
- Detecting multilayered malicious QR code attacks (March 2024)
- Defeating malicious application creation attacks (April 2024)
- Stopping supply chain impersonation attacks (May 2024)
- CEO impersonation attacks (June 2024)
Background
Last year, the number of malware attacks worldwide reached 6.08 billion. That’s a 10% increase compared with 2022. Why are cybercriminals developing so much malware? Because it is a vital tool to help them infiltrate businesses, networks or specific computers to steal or destroy sensitive data. or destroy sensitive data.
There are many types of malware infections. Here are just three examples.
- SocGholish (compromised websites known to lead to ransomware)
- Rhadamanthys (information stealer)
- DarkGate (multifunctional malware)
DarkGate is a notable example. It’s a sophisticated and adaptive piece of malware that’s designed to perform various malicious activities. This includes data theft, unauthorised access and system compromise. What makes DarkGate unique are its key characteristics:
- Multifunctionality. This malware can execute a range of malicious functions, like keylogging, data exfiltration, remote access and more.
- Evasion techniques. To help avoid detection, it uses advanced evasion techniques, like code obfuscation, encryption and anti-debugging measures.
- Distribution methods. Bad actors can distribute DarkGate in a variety of ways to trick users into installing it. These methods include phishing emails, malicious attachments, compromised websites and social engineering tactics.
- Command and control. DarkGate has automatic connectivity to remote control servers. This allows it to receive instructions and exfiltrate data.
Its adaptive flexibility is why DarkGate is favored by so many cybercriminals.
The scenario
In a recent attack, a threat actor (TA571) used DarkGate to try to infiltrate over 1,000 organisations worldwide. The attack spanned across 14,000 campaigns and contained more than 1,300 different malware variants.
DarkGate acted as an initial access broker (IAB). The intent was to gain unauthorised access to an organisation’s networks, systems and users’ credentials to exfiltrate data or deploy ransomware. Once they gain remote access, threat actors have been observed selling this access to other bad actors who can then commit further attacks.
In this scenario, the threat actor TA571 targeted a resort city on the U.S. East Coast known for its sandy beaches and 10 million tourist visitors annually.
The threat: How did the attack happen?
Here is how the recent attack unfolded.
1. The deceptive message. Attackers crafted a message that looked like a legitimate email from a known supplier. It detailed the purchase of health and safety supplies for the city's office. Instead of including an attachment, the threat actors added embedded URLs to avoid raising suspicion in an attempt to bypass the incumbent email security tool.
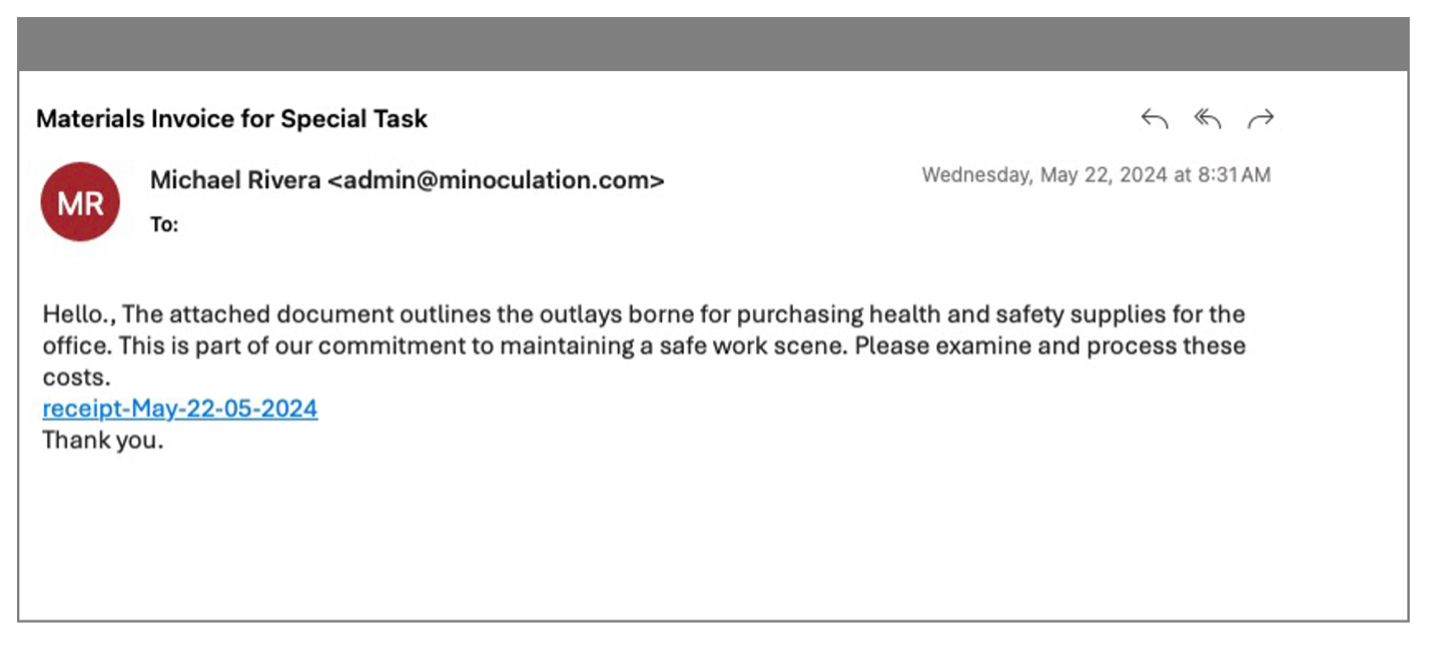
Malicious email detected by Proofpoint that was delivered by the incumbent security tool.
2. The malware attack sequence. To evade detection, the attackers used a series of URL redirects that they facilitated through a compromised traffic distribution system (TDS).
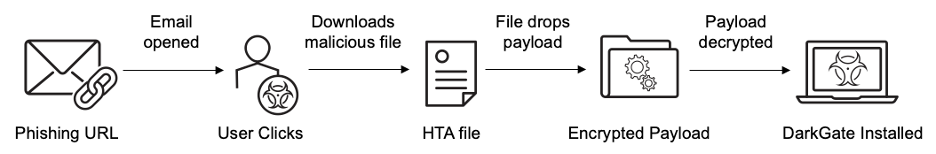
The original URL appears to point innocuously to Google. However, by compromising the TDS mechanism, the bad actors target specific user conditions. This ensures that only users who meet certain criteria—like having a particular set of cookies in their browser—are redirected to a malicious URL. It’s this URL that prompts the user to download malware.
Once the user downloads and executes the file, the malware activates. That’s when it begins its work in the background by downloading additional components. These may include keyloggers, data exfiltration tools or ransomware.
Detection: How did Proofpoint detect the attack?
DarkGate is stealthy, sophisticated and a challenge to detect. Proofpoint employs an advanced blend of signals and layers of analysis to distinguish between weaponised or benign emails, attachments, and URLs. In this case, we analysed and profiled:
- The sender
- The sender’s previous sending patterns
- The relationship of the sender and recipient based on their past messages
- Email payloads (files and embedded URLs)
These indicators helped us to identify the suspicious sender and determine whether they were acting in a way that was different from how they’d behaved in the past. In this example, we had never seen this sender communicate with this coastal resort city or recipient before. As a result, we proactively identified this as a new threat.
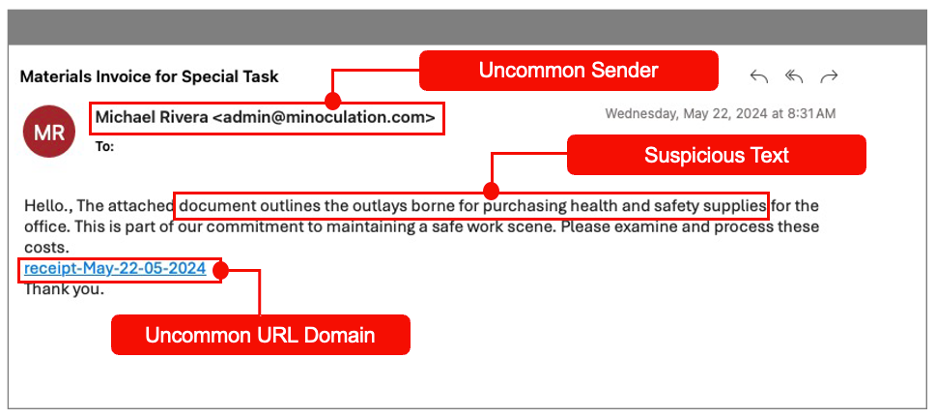
The signals that Proofpoint used to condemn the message as a threat.
If you condemn a message based on uncommon sender patterns alone, it can lead to falsely classifying a benign message as bad. This often happens with email security tools that don’t have sophisticated threat intelligence-derived engines.
To reduce the number of false-positives, Proofpoint combines many signals to extract the thematic nature and intent of the message content. We analyse the sender’s email history. We also conduct a linguistic and semantic analysis of the email body. This approach allows us to identify language that reveals whether an email asks the recipient to take an action. In this example, the attackers wanted to prompt the recipient to click on an embedded malicious URL.
Besides behavioural and language analysis, Proofpoint used machine learning (ML), behavioural AI, and the Proofpoint Threat Research team to detect this threat. But we didn’t stop there—we went deeper.
Our enhanced predelivery protection for URL-based threats capability allows us to hold suspicious messages with URLs for sandbox analysis. This minimises the risk of a user engaging with a malicious URL.
We use behavioural signals and threat intelligence to determine if a message should be held for a more thorough inspection. Our sandbox technology exhaustively inspects the URL using both static and dynamic analysis. Our detection identifies and blocks URL-based attacks before they land in users' inboxes. This, in turn, eliminates the chance that a user might activate them.
Finally, keep in mind that URLs are not always malicious when they are delivered. They can become weaponised post-delivery. As such, emails that contain links require constant scrutiny to help protect people and the business against advanced threats. That is why continuous analysis from pre-delivery through to click-time is so important to stop URL-based attacks.
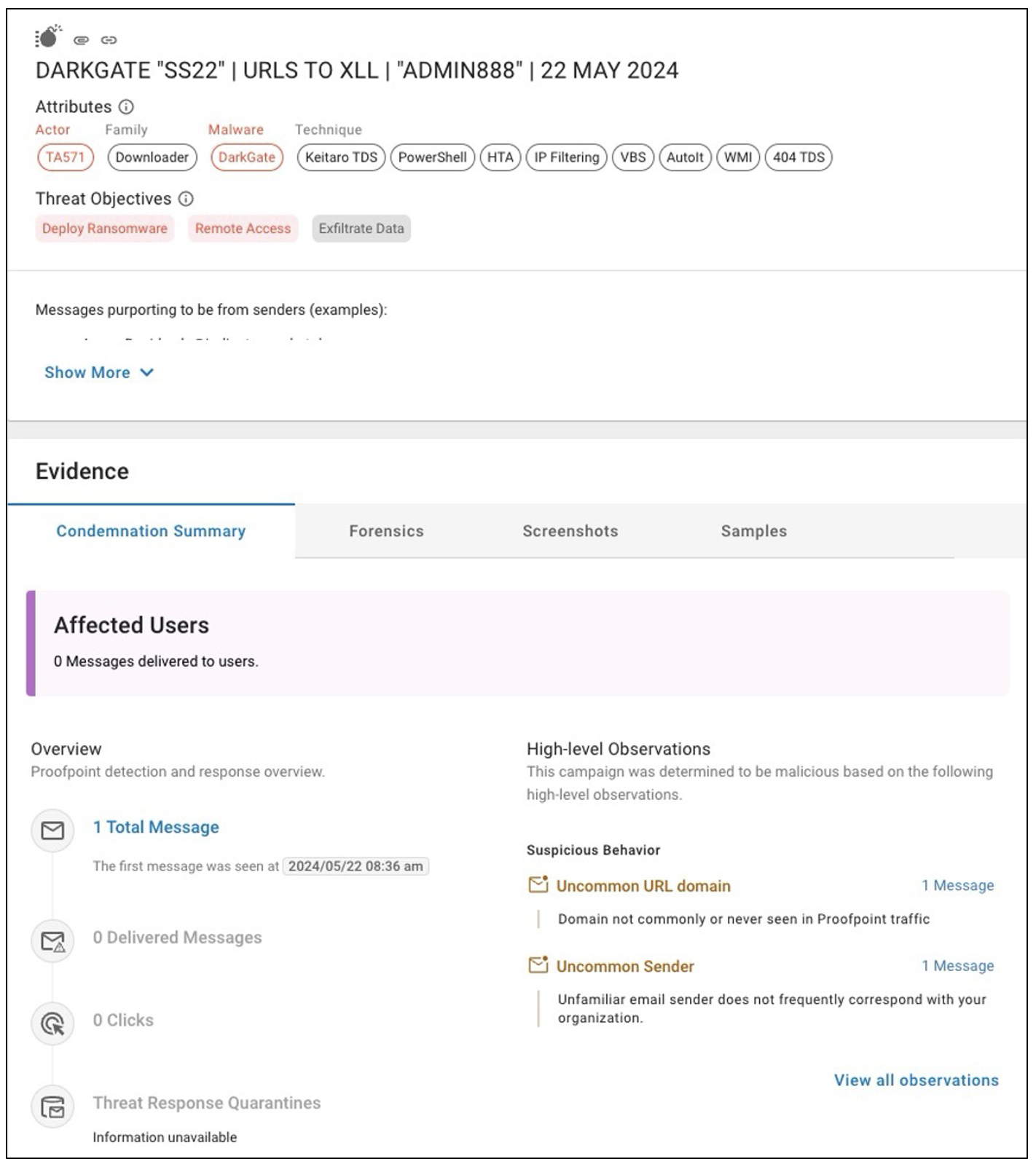
A condemnation summary that outlines the signals Proofpoint detected to block this threat.
Remediation: What are the lessons learned?
To help safeguard against DarkGate phishing and malware attacks, we recommend that businesses take the following actions.
- Implement pre-delivery threat protection. Our research shows that 1 in 7 users will click on an email within one minute. The only way to keep your users safe is to block malicious messages before they are delivered. Look for a tool that combines AI-driven ML algorithms and advanced threat intelligence to identify and block threats.
- Educate your users. Your employees and customers are your first line of defense. To play this crucial role, they need to have security awareness education that teaches them about all types of phishing attacks. Be sure that your training covers topics like deceptive emails and fake login pages. This can help to reduce the chances that your users will become victims.
- Use post-delivery threat detection and remediation. DarkGate’s flexible deployment and deception techniques help convince users to click on weaponised URLs in the post-delivery phase. That’s why you need an email security solution that continuously monitors delivered messages for links that may change over time. And if they turn malicious, it should automatically remediate them in real time.
Proofpoint delivers human-centric security
In today’s world of sophisticated cyberthreats, you must be vigilant and proactive if you want to succeed at protecting your people and business. Bad actors continue to find new and creative methods to get around security tools. DarkGate’s various deception techniques and deployment methods are just the latest reminder of the critical need for multilayered and robust email security measures.
A comprehensive approach to security is a must. Proofpoint provides continuous detection and analysis (predelivery to post-delivery to click-time) throughout the email delivery lifecycle. This allows our customers to achieve end-to-end protection against modern email threats. We deliver the most accurate detection and a 99.99% efficacy rate. Our combination of behavioural AI, threat intelligence and sandboxing techniques can help you stay ahead of threat actors.
To learn more about how you can protect your people and business against threats like DarkGate, read the Proofpoint Threat Protection solution brief.

