Another RSA Conference has arrived, and with it comes the gold standard report for our industry, the Verizon DBIR. And for yet another year, it concludes the same thing: the human element is central to the vast majority of breaches (76% this year), especially the ones that matter, from ransomware to BEC to data loss.
The very first word of the 2024 DBIR is also not new; it’s “phishing”. Email security has always been central to human risk: it’s the #1 way users encounter threats, the #1 way users make mistakes, and the #1 way attackers get what they want, from credentials to wire transfers to malware infections.
Proofpoint has a long history of stopping more human-targeted threats than anyone else. Our long history of firsts includes the first ML models to stop unwanted messages, the first rewriting of URLs for click-time protection, and the first connection of a malware sandbox to email. But attackers have continued to innovate and so have we – starting now, we’re setting a new standard for protection across the entire email delivery chain.
Building an Unmatched Detection Ensemble
What organisations need in email security is simple to describe but hard to do: a single solution to protect against every type of threat, every time, every way a user may encounter it, using every form of detection. Our detection ensemble was already the industry’s most effective, including threat intelligence, static analysis, sandboxing, click-time protection, and our unique set of Nexus AI models. I’m thrilled to announce that we have now added the industry’s first ever pre-delivery protections to stop social engineering and malicious URLs, as well as our newly integrated post-delivery behavioural AI, Proofpoint Adaptive Email Security.
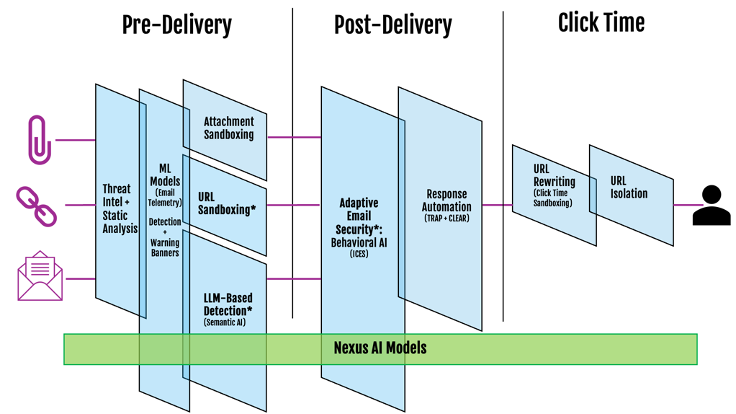
* New capability
According to our data across more than 500,000 organisations, including 87 of the Fortune 100, attackers rely on two techniques more frequently than any others: text-based social engineering and malicious URLs. While we already detect both these threat types at the highest rates in the industry, we wanted to push the envelope – not just detecting them, but detecting them as early as possible.
To make this a reality, we optimized the performance of our Nexus AI LLM-based detection model by 10X, enabling us to use semantic analysis to interpret a malicious message’s intent (such as invoicing fraud), regardless of the words they use or even the language they write in. In parallel, we built the capability for our gateway to hold messages with suspicious URLs until they are sandboxed.
The result is the most formidable set of defense in-depth measures available for organisations to prevent attacks from reaching their targets.
Continuous End-to-End Detection with Proofpoint Adaptive Email Security
Joining our pre-delivery enhancements is Proofpoint Adaptive Email Security, our API-based email security offering that integrates with Microsoft 365 and applies our broad detection ensemble to stop advanced threats, including BEC, social engineering and lateral phishing messages. Once deployed, Adaptive Email Security enriches all detections with easy-to-understand explanations about behavioural anomalies observed. Additionally, it automatically quarantines high confidence threats, while delivering real-time coaching using contextual warning banners to alert users to the risks in social engineering and BEC-type emails that don’t contain an obvious malicious payload.
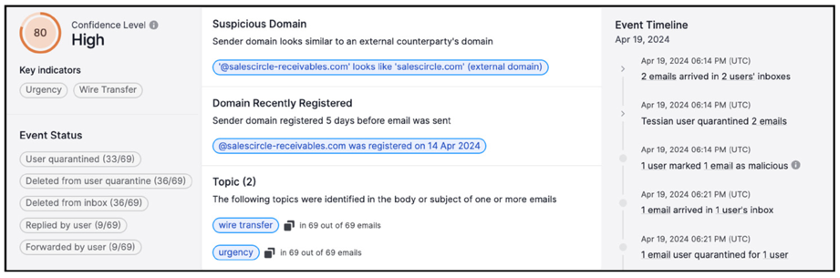
Insight into a malicious message generated by Adaptive Email Security
The Next Level
While we’re thrilled for you all to experience our latest set of innovations, we know we can still do more to help you protect your people. That takes two main forms: continuing to lead with Nexus AI, and deepening and strengthening our ecosystem partnerships.
Nexus AI: The value of our proprietary data is enhanced by contextual insights and in-depth classification from our leading team of threat researchers and data scientists, who track adversaries, analyse evolving attacker tradecraft, profile data exfiltration patterns, and help train our systems to improve. Across Nexus AI, our models have taken our efficacy to the next level by adding semantic understanding, new classifiers, computer vision, anomaly detection, and campaign clustering capabilities. Complementary to our detection efforts, our generative AI models now deliver elegant threat summaries and end user warnings.
While our data scientists are world class, they would be the first to tell you that there’s no magic in the models – the magic is in the training data. Our data set is not only wide but deep, as we analyse 22 trillion potential payloads annually to extract intelligence and continue to improve our models. When you’re a Proofpoint customer, you benefit from this tremendous network effect.
Ecosystem integration: The other network effect that can provide an unfair advantage over attackers is the network of leading cybersecurity vendors and our combined capabilities. We partner with the ecosystem of market-leading cyber security vendors—including Palo Alto Networks, CrowdStrike, Microsoft, CyberArk, Okta and many more—to enhance outcomes for our joint customers.
With the rise of SASE, XDR, and modern security architectures, our controls for protecting networks, endpoints, and infrastructure have evolved, becoming more comprehensive, adaptive, and effective. With over 90% of breaches involving the human element, Proofpoint’s human-centric security platform does the same for people, and integrates with the key leaders across the other 5 components of the modern security stack.

Getting the Best Protection for Your People
Not only have our new email security capabilities set the bar for both comprehensive and effective protection, they are available to all Proofpoint email security customers. Our new pre-delivery defenses for both social engineering and URLs go live on a rolling basis this quarter. Adaptive Email Security is now available in early access at no additional cost for Proofpoint customers, and can be applied to the riskiest users identified by Proofpoint’s Targeted Attack Protection, an organisation’s VIPs, or any other risky cohort of users, which can be informed by Proofpoint’s unique human risk scoring.
If your organisation has a greater risk tolerance or smaller security function and is looking for a simple add-on to Microsoft 365, Adaptive Email Security deployed as a post-delivery only solution may meet your needs. Later this year, we intend to make Nexus AI capabilities available via Adaptive Email Security’s rapid integration with your existing Microsoft gateway.
This is the first of a series of blogs that will lay out the core elements of the future of human-centric security. In the next post, we’ll cover how human-centric security fits into the new world of SASE, XDR, and the rest of the modern cybersecurity architecture.
Additional resources:
- Read the Press Release: Proofpoint Sets New Industry Standard in Email Security with Adaptive Threat Protection Capabilities Across the Entire Email Delivery Chain
- Read our blog on “GenAI Is Powering the Latest Surge in Modern Email Threats”
- Read our blog on “Malicious Links: Stop URL-Based Attacks Before They Start”
- For more information on all our award-winning email security solutions, visit: https://www.proofpoint.com/us/products/threat-defense

