

Identity Protection
Detect, investigate, and respond to account takeovers
Stop account takeovers from causing major security incidents
Without timely detection and clear visibility, account takeovers are difficult to find and fix
Most organisations regularly experience compromises of their users’ Microsoft 365 and Google Cloud accounts. While using is an important security defence, it can easily be bypassed. Without specialised defences against account takeovers attacker dwell times extend, investigative processes grind forward slowly, and related email and account data resources get abused.
Detect and remediate cloud account takeovers immediately
TAP Account Takeover applies threat intelligence, sophisticated behaviour and machine learning-based analytics, and automation to quickly detect, investigate, and remediate . TAP Account Takeover leverages Proofpoint Targeted Attack Protection (TAP) to correlate between email and cloud threats to detect the most current threats.
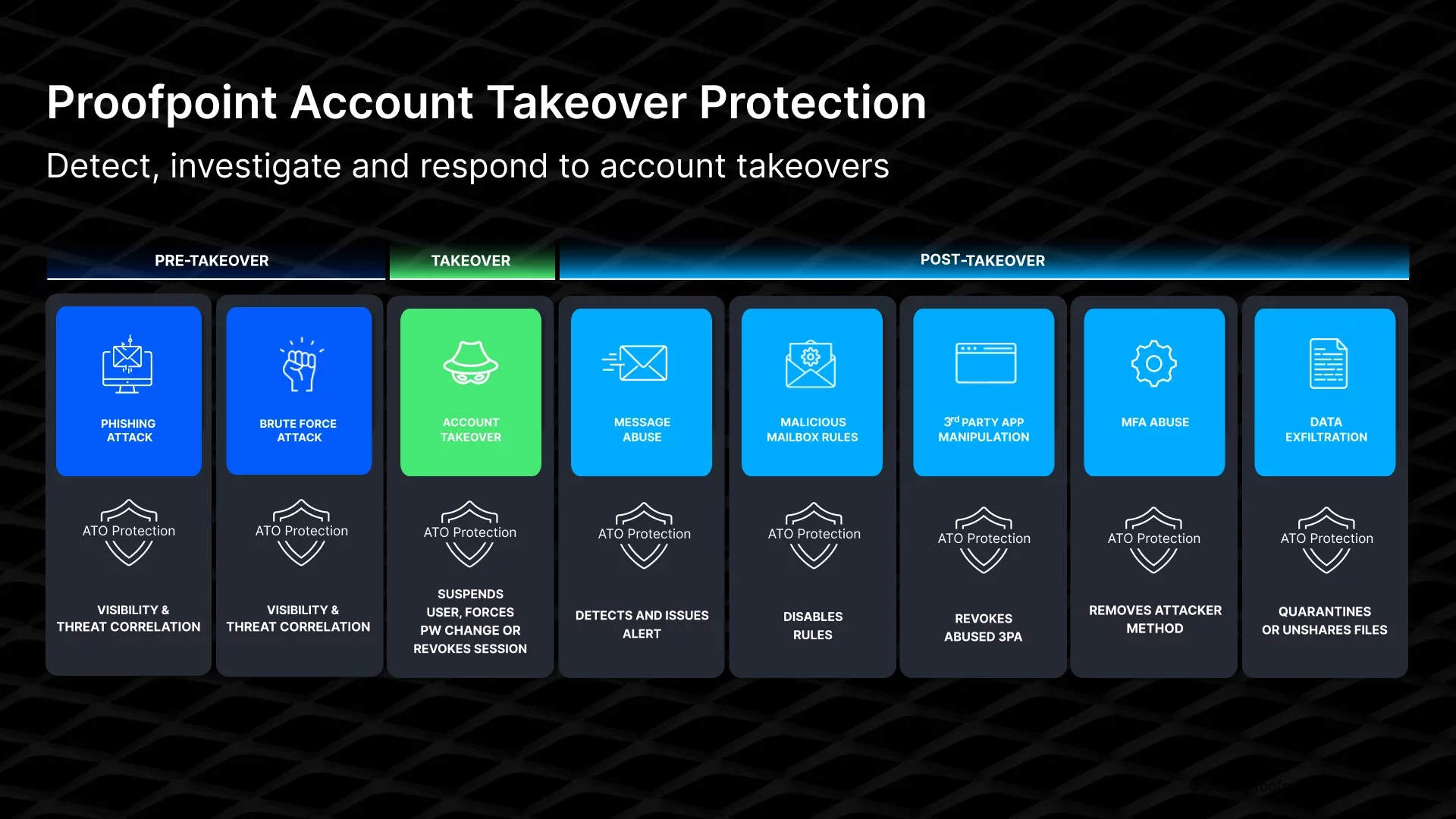
TAP ATO protects over 50M users at nearly 5000 organisations and detects hundreds of thousands malicious login and subsequent resource abuse incidents.
Key Benefits
Provides high-fidelity account takeover detection
Detective alerts that turn out to be false positives are almost as bad as missing real active threats. Incident investigative time that is wasted cannot be claimed back. Excessive false positives lead to distrust and ignoring the alert source. TAP Account Takeover’s continuously curated threat detection techniques deliver high-fidelity detection verdicts.

Accelerates investigations to shorten dwell times
Slow incident investigations allow attackers to extend their undetected dwell times. Excessive attacker dwell times dramatically increases the probability that significant business impacting breaches will result. Proofpoint TAP Account Takeover enables security analysts to quickly see and understand mailbox rule, file, MFA, and 3rd-party application changes so that immediate remediation steps can be taken.

Automates the remediation of malicious actions
Without automation the cleanup of security incidents can often take as long as the detection and investigation stages. TAP Account Takeover applies automation to the remediation steps required to bring the compromised accounts back under the control of the legitimate user and to reverse the malicious, post-compromise changes, such as MFA settings, conducted by the threat actor.
Provides continuous visibility of the cloud accounts
All detection and response effectiveness begins with visibility. Through extensive API-based integrations with cloud services, TAP Account Takeover can monitor and analyse what is occurring in your organisation’s Microsoft 365, Google Cloud, and Okta accounts.
Key features
Provides comprehensive visibility
TAP Account Takeover surfaces compromised accounts and suspicious post-access activity in the organisation’s cloud environments. Security analysts can see whose account has been compromised and how. It can show investigators how attackers accessed the accounts as well as what they did after logging in via the attack sequence timeline. All as a natural extension of Proofpoint TAP.
Correlates threat intelligence with AI/ML and behavioural analytics
Proofpoint Account Takeover leverages extensive threat intelligence, behavioural and machine learning analytics, and cloud monitoring to provide low false-positive detections of account takeovers and of specific malicious actions. TAP Account Takeover issues automated alerts in the TAP dashboard when an account is compromised, enabling comprehensive visibility.
Displays the full attack sequence
TAP Account Takeover’s attack sequence timeline displays an overview of account takeover activity. It also shows impacted accounts and malicious activities pre- and post-takeover. It can show security analysts how attackers accessed the account as well as what they did after taking control. It can show the investigator the threat actor’s file activities and flags changed mailbox rules, mail-sending activities, MFA settings, and when application trust relationships are established with malicious third-party apps.

Extends Proofpoint TAP’s investigative processes
With TAP Account Takeover security analysts can quickly understand what has happened and how to immediately limit risk. Information about account takeovers is integrated with the Proofpoint TAP investigation system. The investigator can see if the user is a Very Attacked Person (VAP) and can learn about other users who have been hit by similar threats.

Resets malicious mailbox rules, revokes 3rd-party apps, reverses attacker-controlled MFA changes, and quarantines malicious files
TAP Account Takeover automatically detects and remediates when attackers make changes to mailbox rules. Attackers often change these rules to hide their existence before they stage a BEC or phishing attack. TAP Account Takeover also detects and revokes malicious third-party apps that can help attackers control an account without being detected. And incident responders can automatically or manually delete malicious files that attackers have inserted into the environment.
The latest developments in Identity Protection

Identity Protection
Read More
Account Takeover – Bypassing Multifactor Authentication

Proofpoint Account Takeover Protection

