The email threat landscape is rapidly evolving. Today, infrastructure is being targeted less while people are being targeted more. And the rise of social engineering means that attackers can quickly identify and target specific people within organizations.
Making matters worse is that with generative AI threat actors can attack people relentlessly with personalized email-borne threats. Given these trends, it makes sense that all of today’s top cybersecurity risks are people centric. Just look at these statistics:
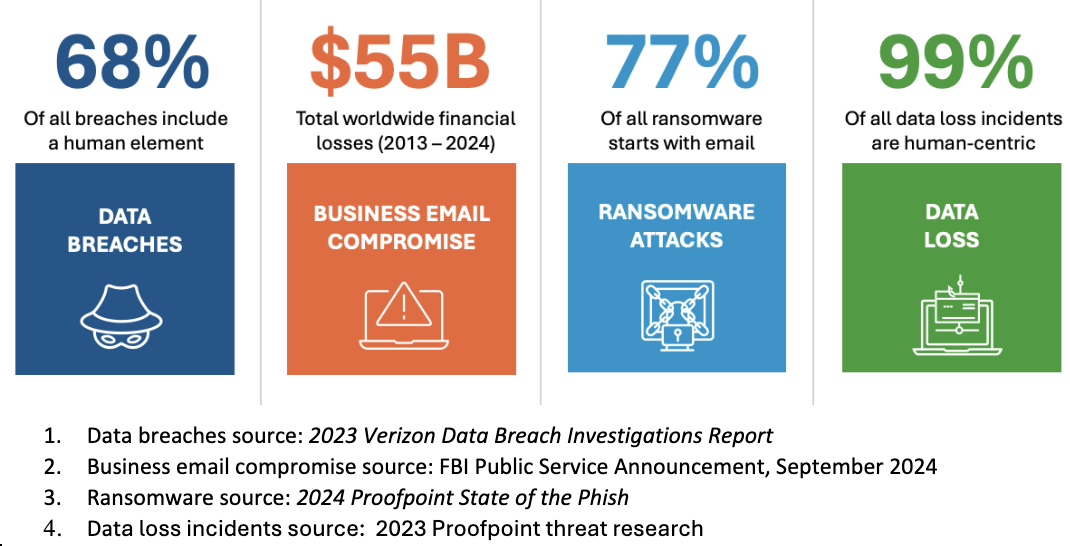
Top people-centric cybersecurity risks.
Threat actors prefer people-centric attacks because they don’t want to break into your network, they want to login. The quickest way to compromise your people is through email—more specifically, through your porous Microsoft 365 email security defenses.
In this blog post, we’ll do a deep dive into why Microsoft 365 email security is not enough. And we’ll cover some best practices for strengthening your email defenses.
Business is built on Microsoft
There’s no denying that Microsoft productivity and collaboration tools are the industry gold standard. Microsoft 365 has an 88.1% productivity software market share and more than 400 million licensed users. And it continues to grow globally.
Because Microsoft 365 is spreading across the globe, its underlying email security platform is too. This means that more and more organizations rely on Microsoft’s built-in, native security capabilities. And whenever a single platform prevails, risk gets more concentrated. Essentially, attackers know that if they can break through Microsoft security, then they can get the keys to the kingdom to thousands of organizations at the same time.
Microsoft makes an especially good target for attackers. That’s not only because it has so many products, but because those products extend across the entire attack chain. For example, Microsoft Exchange Online Protection (EOP) can act as an entry point. Then, Microsoft Entra ID (formerly Azure AD) can be used to compromise identities and escalate privileges. Meanwhile Microsoft cloud services—like Microsoft Dynamics 365, Microsoft Office 365 and Microsoft Teams—can be compromised or used to host and launch attacks.
All this makes Microsoft not just an attack surface, but an ideal launching pad for new types of attacks.
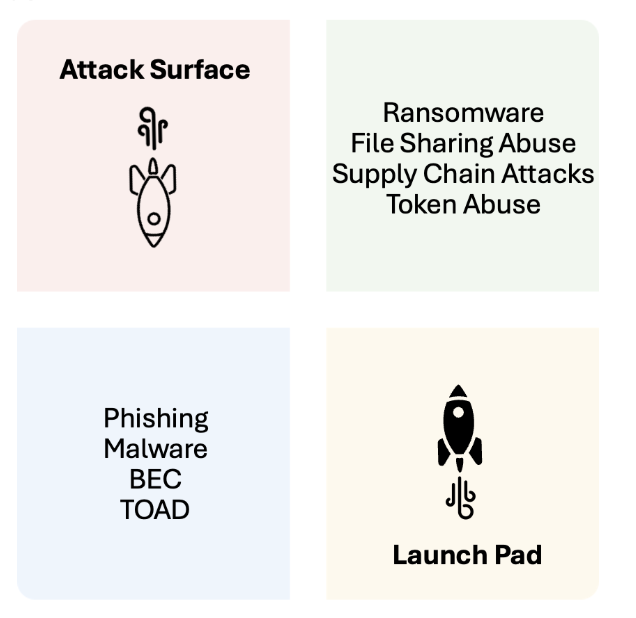
Microsoft is both an attack surface and launch pad for cyberattacks.
Bad actors exploit Microsoft’s success
As Microsoft 365 adoption increases, it’s a more attractive target for cybercriminals. And they use Microsoft’s gargantuan customer footprint to for their attacks. In 2023, Microsoft was the most abused brand in the world. According to Proofpoint threat research, attackers sent more than 68 million malicious emails last year. Those emails abused products like Office 365, SharePoint and OneNote, as well as the Microsoft brand. Their goal: to trick unsuspecting users into handing over their credentials.
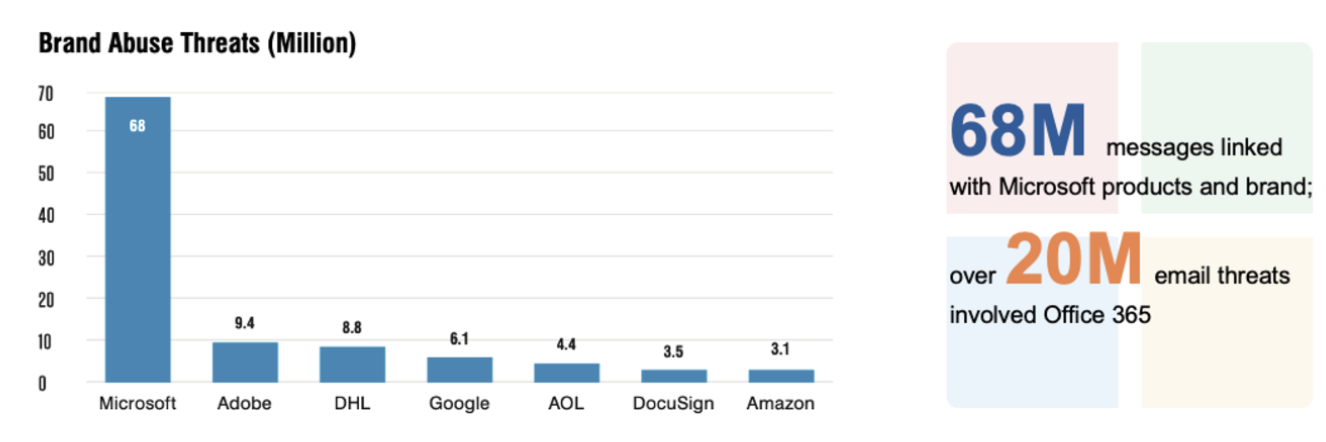
By the numbers: Microsoft as the most abused brand in the world.
Where to strengthen your Microsoft 365 security
Threat actors are strategic and are always looking to get the most bang for their buck. This is why they have homed in on attacks against Microsoft that they know are going to be easy to implement and highly successful.
As a result, the types of attacks we see most often are focused on Microsoft detection gaps. Here are the biggest gaps:
- Business email compromise (BEC). Also known as email account compromise (EAC) or targeted phishing, BEC is a type of cybercrime that uses email to trick people into sharing sensitive information or sending money. In these attacks, a threat actor impersonates a trusted person, such as a vendor or executive, and sends an email that appears to be legitimate. The email may ask the recipient to pay a fake invoice, hand over sensitive data or send an urgent wire transfer. The goal is to get the victim to perform an action.
- Advanced phishing. This is a sophisticated attack where threat actors use social engineering to trick people into sharing sensitive data. They might try to steal login credentials, multifactor authentication (MFA) codes or credit card numbers. Once they’ve achieved that goal, they take over their victims' accounts on legitimate websites.
- Account takeover (ATO). This is a type of cybercrime or identity theft that occurs when an unauthorized user gains access to a legitimate user's online account. Their goal is to steal data, commit fraud or access privileged information. ATO attacks can affect a variety of accounts, including email addresses, bank accounts and social media profiles.
- Impersonation abuse. In these attacks, a threat actor creates a fake online presence to trick people into giving away sensitive data or visiting malicious websites. These fake presences can be websites, social media profiles or email addresses.
- Accidental data loss. This is when digital data is destroyed or compromised by mistake. It can happen in variety of ways. People might accidentally delete or misplace a file, enter data incorrectly or fail to save their work. They also inadvertently compromise sensitive data when they open malicious email attachments, use weak passwords and install unauthorized software.
While Microsoft provides native email security through Microsoft EOP and Microsoft Defender for Office 365 (for an additional cost), advanced email threats continue to easily bypass its defenses. That’s why you need to protect your Microsoft investment and strengthen your email security with Proofpoint. It’s the only way to detect and stop threats from getting past your email defenses.
So, what can you do to better protect your organization?
5 Best practices: a defense-in-depth approach
To protect your people and business from a constantly evolving threat landscape, you need to add more layers of security. This means adding security to your Microsoft native email security as well as any other additional layers that you’ve purchased. This is where Proofpoint can help.
1: Use pre-delivery protection to stop threats faster
With Proofpoint, you can take a defense-in-depth approach to protecting your users. We ensure that your emails are protected pre-delivery to help you stop sophisticated threats at the front door—not after they’re delivered. This includes threats like advanced credential phishing, BEC, QR codes and malicious URL-based attacks. All this means that we help you to strengthen your Microsoft 365 email security with a 99.99% detection efficacy rate.
2: Harness AI-driven, multilayered detection for threat accuracy
Our multilayered detection stack Proofpoint Nexus® is powered by threat intelligence, machine learning (ML), behavioral AI, sandbox detection and semantic analysis. It has a high-fidelity detection efficacy rate. And it can stop many different types of modern threats with fewer false negatives and false positives. In other words, we stop more malicious messages without blocking the good ones. That way, we don’t impede your business.
3: Get comprehensive visibility into people risk and threats
Proofpoint gives you unique insights into your very attacked people (VAPs) and the threats that are targeting them. Our data helps you to better understand how attacked and vulnerable your people really are. This information enables you to implement targeted adaptive controls—like browser isolation, security awareness training and multifactor authentication—for the people who need them the most.
4: Automate post-delivery remediation
Proofpoint streamlines the email incident response process for your security teams. When an email is delivered to a user's inbox and it is deemed to be malicious, all instances of it are removed automatically post-delivery. By aggregating and correlating our industry-leading threat intelligence data, we automatically build behavioral relationship associations between recipients and user identities. With these insights, we can take automated actions based on targeted users, groups or departments to remove and quarantine any delivered or forwarded malicious messages.
5: Get proactive click-time protection
Proofpoint helps your organization to protect users from malicious URLs in suspicious messages. We provide a multilayered approach to click-time protection with URL rewriting, real-time threat analysis (pre- and post-delivery), browser isolation and URL sandboxing. When a user clicks on a URL link, our real-time analysis can determine if it is malicious or not. If it is, then we block access to the malicious website.
Our click-time protection secures users the moment a URL link is clicked on, not after the email is delivered. Even if a URL link appears safe when the email arrives—but becomes malicious later—we automatically block it.
More secure together: Microsoft and Proofpoint
As Microsoft 365 adoption continues to grow, attacks that target Microsoft will continue to increase. That’s why fortifying native Microsoft email security should be a top priority for security teams.
Email security needs to cover both inbound and outbound email communications. It must also provide a modern defense against advanced email threats. The only way to keep your users completely safe is to detect and block malicious messages pre-delivery, post-delivery and at click-time. To do this, you need to adopt a defense in-depth approach. Case in point, a California university recently augmented their Microsoft 365 email security with Proofpoint. As a result, they can better protect their people from even the most sophisticated email threats.
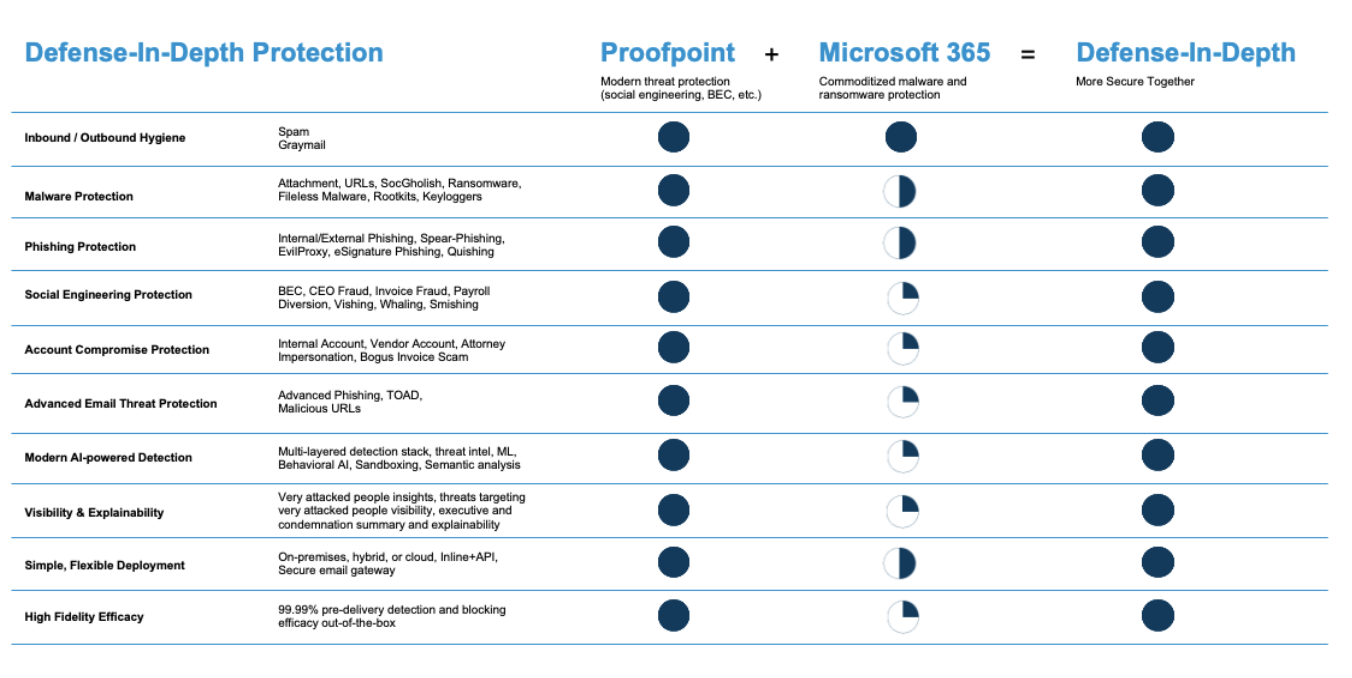
Proofpoint and Microsoft together—a comprehensive defense-in-depth approach.
Proofpoint provides comprehensive and continuous security across the email delivery lifecycle to give you end-to-end protection. By analyzing more than 3.5 billion emails a day across our ecosystem of more than 510,000 customers, partners and providers, our Proofpoint Nexus detection stack delivers a 99.99% efficacy rate. When you complement native Microsoft 365 email capabilities with Proofpoint, your organization can better protect users and defend against evolving cyberthreats.
To learn more, download the Microsoft and Proofpoint: More Secure Together solution brief.

