One of the things I like about being in cybersecurity is knowing my company helps protect others from criminals looking to exploit them. At every customer-facing event that I go to, customers tell me how many times our solutions have made them look good with their executives. But many of these same people may be doing something that has the potential to make them look very bad. You may be in a similar situation and not even know it. So that is what I’ll cover today – steps you can take to reduce the chances that your transactional emails impact your user-generated messages.
In this blog post, we are going to assume that you are already familiar with what we mean by transactional email. However, if you would like to better understand this topic – including where transactional emails are generated and why they are so important – read our blog “Transactional Emails: Best Practices and Background”.
3 Methods for relaying transactional email
Let’s start by exploring the three different methods for relaying transactional email.
1: On-premises mail transfer agent (MTA)
Microsoft Exchange is an example of an on-premises solution that can be used to relay transactional email. There are several challenges with using this type of solution. For starters, it can be costly to maintain physical servers and pay for licensing. Also, when the solution hits end-of-life, support becomes an issue. Moreover, this method typically doesn’t align with a company’s desire to move these types of functions to the cloud. And since authentication is not required to submit messages via the host name, it can be abused by bad actors.
2: Email service provider (ESP)
ESPs are third parties that can relay transactional email on a company’s behalf. This method is often popular because it’s inexpensive. Unfortunately, these are the same reasons why it’s frequently targeted. Bad actors can easily register accounts to launch attacks or compromise existing accounts. If bad actors compromise your authorised ESP infrastructure (or app-owner accounts) “upstream”, then they can send malicious email on your behalf. What’s worse is that it will likely be delivered because it will pass email authentication.
3: Sending transactional email through your user-generated sending IPs
This is the riskiest method. Frequently, the risks far outweigh the convenience and potential cost savings. Email is one of the most critical forms of business communications that we use today. Any issues that are caused by an application or third-party sending email on your behalf could jeopardise these sending IPs. In fact, this method is so risky that many email providers are now precluding companies from using this method in their terms of use.
Key issues with this method:
- Transactional emails are typically sent in much higher volumes. This can impact performance, resulting in delays of business-critical emails (“did you get it yet?”).
- Messages sent via an “open relay” can result in blocklisting. When you allow third parties to send on your behalf, you could be creating an “open relay”. If exploited, this can result in your main sending IP addresses being blocklisted.
- Blocklisted addresses can grind business to a halt. Whether high volumes of traffic is the result of compromise or just a rogue app, any blocklisting of your addresses can bring down your company’s entire business operations.
That last bullet is the scariest one to face. You don’t want to put yourself in a position where all your email is blocked due to something that occurs with your transactional email. Believe me, it can happen. And when it does, any thoughts about your cost savings will be overshadowed by the urgency to get your email flowing again quickly.
What is the best method?
By far, sending transactional email from a dedicated email environment is the best method.
With this method, you use a dedicated gateway environment that is specifically designed for relaying transactional email. This way, you get centralised control over all application generated email – whether they are created internally or by third-party partners sending messages on your behalf. This separation safeguards the IP addresses you use for sending user-generated email.
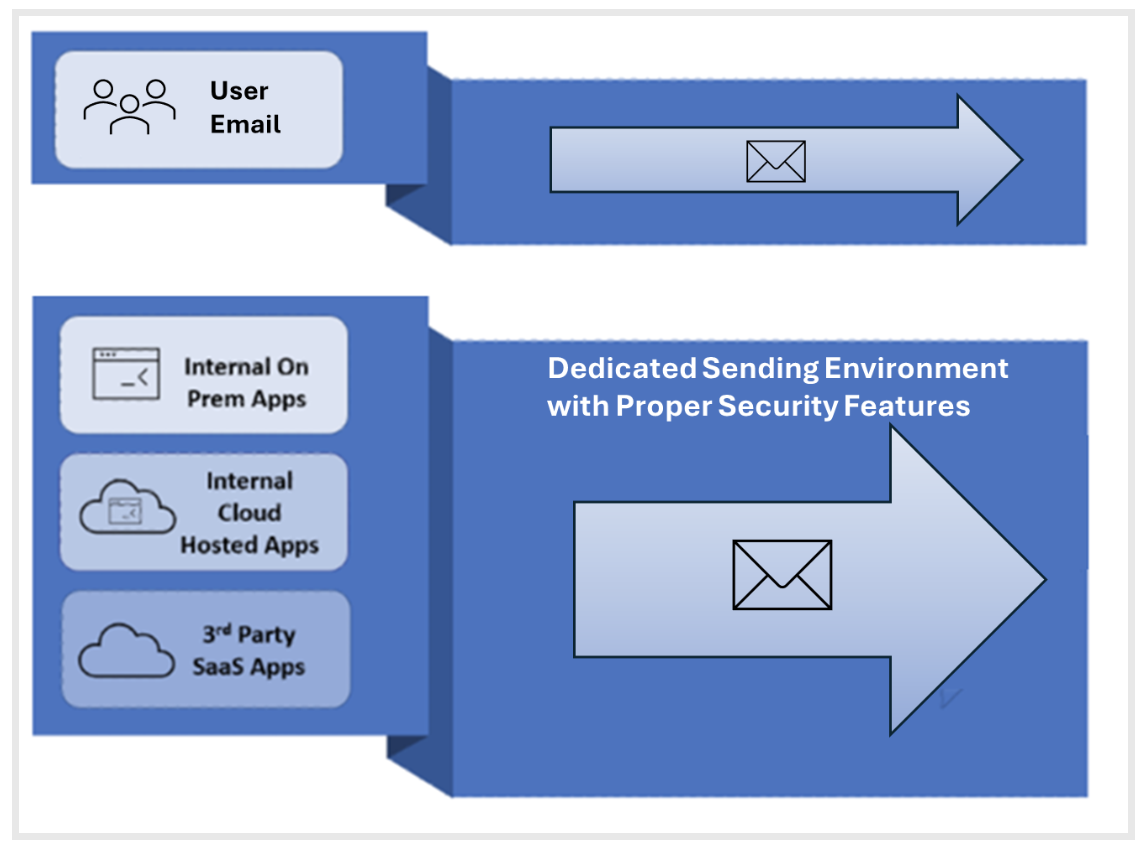
Separating user-generated email from transactional email is a best practice.
Need help creating your transactional email sending environment?
Not all solutions offer the same level of security. Proofpoint is one of the industry leaders when it comes to email and email security. We have the resources, the technology and the skills to help you separate and protect your transactional emails. As a result, we can help you create a protective layer between your application email and email recipients, without sacrificing security. And with our cloud-based Secure Email Relay (SER) solution the process is quicker and more cost-effective than you might expect.
The Proofpoint SER solution allows authenticated sources to submit emails for relaying. At that point, all messages are scanned for malicious content and viruses to ensure that they’re clean before they’re sent out. In addition to antivirus and anti-spam scanning, messages also get a DKIM signature to protect against impersonation, support DMARC initiatives and help increase their deliverability.
As a bonus, SER can help manage your unsubscribe lists and even inject an unsubscribe link in your email header to meet the new “one-click unsubscribe” requirements from Google/Yahoo and Apple. Add-ons for DLP and encryption are also available to restrict users from sending sensitive content and add another layer of security to messages before sending.
Get the benefits of Proofpoint SER
With Proofpoint SER, your organisation gets a centralised solution to better manage all the applications and third-party SaaS partners that are sending email from your domain. And if one of these sources is compromised, you have the control to shut them off immediately. This is especially important for third-party applications that were historically outside your control but could cause significant damage to your email identity and brand.
Whether you want to separate your transactional email, retire your on-premises relays, get DKIM or increase your control over the email that’s being sent from applications, Proofpoint Secure Email Relay may be the solution that you’ve been waiting for. For a quick overview of how it works, watch our video: “What is Secure Email Relay?”

