As modern global supply chains expand, food processors, manufacturers, and agriculture service providers are faced with an impossible security task. Not only are they responsible for feeding families worldwide, but they must also be hyper-vigilant about cyber threats that increasingly target them. And they must do all this despite shrinking budgets and higher constraints on their resources.
For these reasons, the success of their security strategy often depends on their ability to:
- Continuously detect threats that target their people
- Ease the growing burden on their IT teams
- Decrease their reliance on ineffective native security tools
We learned this from one of our customers in the food manufacturing industry who recently compared Proofpoint Threat Protection to Abnormal Security’s point product. We have anonymised their story in order to share their experiences and lessons learned. The following blog offers insights into how the food industry can build a better people-centric defence.
A slow descent into message madness
Spurred by progressively deceptive attacks from threat actors, the manufacturer had seen a gradual decline in the threat efficacy of its email security built on Microsoft. Microsoft’s native security has historically struggled against the types of advanced email attacks the customer observed.
The security team saw an influx of employee-reported malicious messages which primarily used impersonation and social engineering techniques. These attacks included:
- Invoicing fraud and CEO spoofing through business email compromise (BEC)
- Malware from compromised supplier accounts
- Telephone-oriented attack delivery (TOAD)
The backlog in their abuse mailbox that contained user-reported emails grew by the day. The team needed to manually investigate and remediate each of these threats while trying to control the inflow of new ones. This put their already stretched thin security team under unsustainable pressure. The company worried about jeopardising their place in the international food chain and their mission to feed communities.
After a near miss with an email containing ransomware, the manufacturer decided it was time for a change. Enter Proofpoint and Abnormal Security.
Comparing Proofpoint and Abnormal side-by-side
The food manufacturer ran concurrent evaluations with Proofpoint and Abnormal Security to find the best solution to protect their more than 7,000 employees, countless customers, suppliers and third-party partners. This comparison process revealed the differences between the two offerings.
Each company has a different approach. Proofpoint provides a comprehensive platform. It detects threats continuously to protect people throughout the entire email delivery life cycle. In contrast, Abnormal focuses on limited post-delivery detection and remediation.
The team began its selection process with very clear decision criteria. It was determined to find the right partner to augment the company’s native Microsoft email security and defend its 100-year-old heritage brand. Below are the key areas where the customer compared Proofpoint and Abnormal.
End-to-end detection capabilities – Proofpoint wins
Abnormal’s restrictive structure only allows malicious messages to be detected after they are delivered to a user’s inbox. It has a 0% pre-delivery efficacy rate, meaning all email attacks must be retracted from users’ inboxes. This puts users at undue risk. Proofpoint threat research found that 1-in-7 clicks on malicious links occur within 60 seconds of a message’s delivery. And one-third of replies to BEC messages happen in less than five minutes.
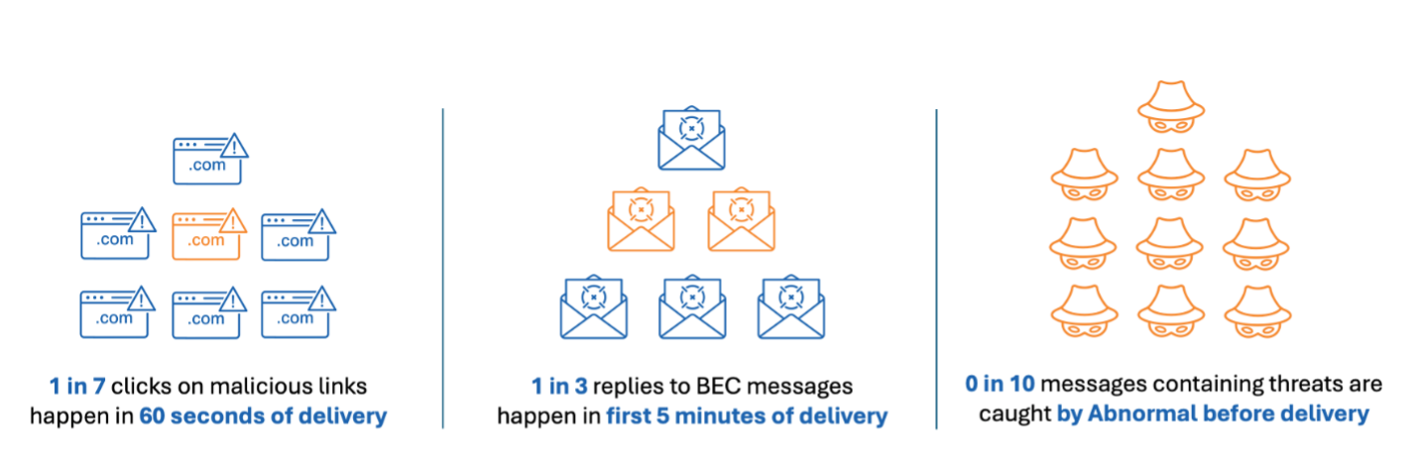
Proofpoint Threat Research results.
The customer recalled that Abnormal relies too heavily on behavioural AI and lacks sandboxing capabilities. They shared concerns that this would expose their company to never-before-seen links and attachments.
Abnormal claims that Microsoft’s built-in sandboxing can catch these kinds of attacks. But our 2023 threat research found that Microsoft misses about 30% of the advanced attacks that Proofpoint detects. Sixty-three percent of those threats involve credential phishing from unknown websites. Often, attackers conduct this activity through embedded URLs, which Microsoft’s sandboxing capabilities overlook.
Unlike Abnormal, Proofpoint features end-to-end detection to stop the widest variety of threats across the email lifecycle. Our multi-layered, pre-delivery analysis uses AI-driven detection which helps us identify threats that get past other tools. For example, our newest semantic analysis engine understands message context and intent to stop highly targeted BEC threats better than other vendors.
Proofpoint has used AI and machine learning for more than 20 years. But our detection capabilities don’t end there. Recently, we introduced the industry’s first predelivery URL hold and sandboxing to capture more malicious links and hazardous payloads at the front door of an organisation. And Proofpoint protection continues post-delivery. We use predictive analytics that trigger automated remediation for messages detected in user inboxes. Those same users are protected at the time-of-click by adaptive controls like email warning tags and isolated web browsing.
The food manufacturer concluded that relying on post-delivery detection alone puts its people, business and customers under unacceptable risk. They agreed that the complete pre-delivery, post-delivery and click-time protection efficacy that Proofpoint provides can’t be beaten when compared with Abnormal.
Operational ease and efficiency – Proofpoint wins
Not only did the customer call Abnormal’s efficacy into question, but they also challenged their accuracy. They noted that Abnormal had reported a significant number of false positives – benign messages being captured and marked as malicious. This disrupted business, which was painful for both end users and security teams. End users began frequently reaching out to analysts about missing messages. And analysts had to manually release the affected emails. Though straightforward, this process was time consuming and frustrating for the team.
Arguably worse were the many false negatives. These dangerous messages made their way through Abnormal’s behavioural AI, leaving administrators to identify and remove them manually before they were activated. The customer already struggled securing resources to handle day-to-day support requests. They soon recognised that the level of daily upkeep and long-term maintenance that would be required to manage Abnormal was not feasible.
“Abnormal might have been OK if we had the resources, time and money to manage it. But we simply don’t.”
– Security operations manager, heritage food manufacturer
Proofpoint eliminates these types of disruptions. According to our 2023 threat research, we have an unmatched false-positive rate of one in every 19.7 million messages. Our solution accurately catches more threats, faster. The result reduces the burden on downstream security teams.
The manufacturer has also recognised other benefits from using Proofpoint to complement Microsoft’s native email security capabilities. One of those benefits comes from our full-circle threat intelligence, which informs the automatic analysis and removal of threats across the entire business. This includes messages that users report and forward. For example, our automated remediation of delivered malicious messages occurs in less than 10 seconds, on average. This can reduce a company’s time spent on remediating emails by more than 90%.
Reducing dependency on Microsoft – Proofpoint wins
Microsoft dominates the productivity space. This has led to a widespread concentration of risk within their native security tools. Though Microsoft may be making gradual improvements, they consistently fall short of attacker’s relentless advancements. Because of this, our customer was hesitant to rely too heavily on Microsoft. And their opinion only grew as they continued to evaluate Abnormal.
Due to the nature of their architecture, Abnormal’s overall effectiveness is tied directly to Microsoft. Abnormal’s dependence on Microsoft’s APIs introduces multiple additional failure points into an organisation’s security stack. Should Abnormal or Microsoft APIs experience an outage, emails would be delivered with only base-level analysis completed. Also, email management must be handled between the two vendor’s consoles. This creates unnecessary administrative overhead.
Abnormal’s solution to access all the features the food manufacturer needed was to upgrade to a Microsoft E5 license. This would excessively increase the customer’s total cost of ownership – a fact that they could not overlook.
Proofpoint is the natural partner to augment Microsoft and act as an independent failsafe. We offer cohesive protection for a company’s people and their Microsoft security investment. We integrate closely with Microsoft and at the same time we separately innovate against new and emerging threat tactics. This is why 83 out of the 87 Fortune 100 companies that use Proofpoint trust us to supplement and protect their Microsoft environments.
The results – Proofpoint detects thousands of missed threats
In the end, the benchmarks outlined by the food manufacturer made their decision easy. Proofpoint was the obvious choice given their:
- Desire to lessen their risk from reliance on Microsoft
- Need for easier daily operations through higher detection accuracy
- Focus on pre-delivery, post-delivery and click-time protection for user-targeted attacks
During the evaluation, Proofpoint identified the equivalent of thousands of spam, malware, phishing, and BEC messages per year after annualising the data. These threats were missed by the manufacturer’s existing email security tool, which was anchored on Microsoft.
Our averaged data across evaluations against Abnormal in the second half of 2023 suggest this customer is not alone in their conclusion. The combined detection efforts of Microsoft and Abnormal still miss about 13.5% of all threats that Proofpoint identifies. This can mean hundreds of thousands of missed messages annually, depending on the traffic volume.
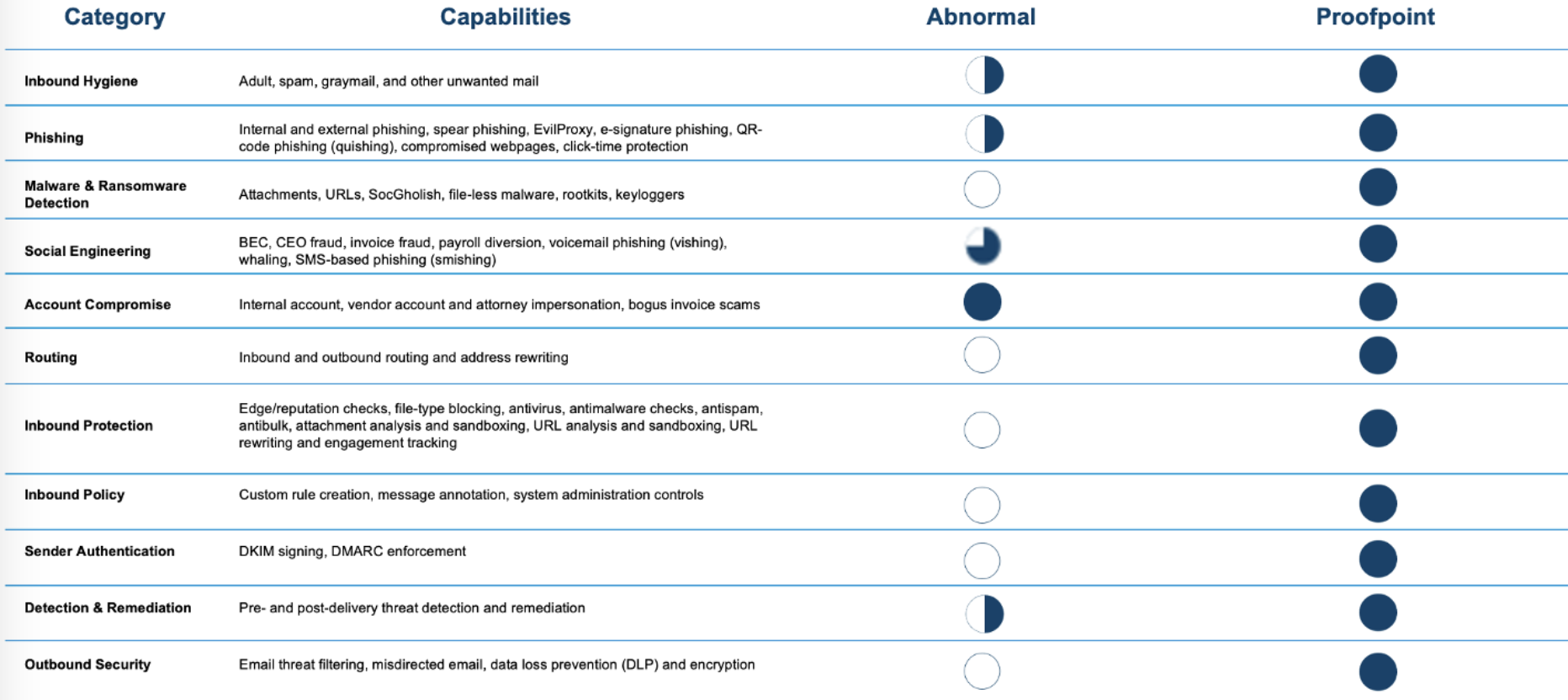
Comparing Proofpoint and Abnormal Security.
Proofpoint – the better choice for protecting Microsoft
You need more than basic security measures and patchwork API tools to defend your business against today’s advanced threats.
Proofpoint is the global leader in email security. We see where bad actors exploit Microsoft better than anyone else. Our solution provides effective, end-to-end protection, which means that it vastly reduces risks compared to API-only point products. It uses multiple layers of detection to continuously analyse threats. These detection layers work across an email’s lifecycle, through pre-delivery, post-delivery and at the time-of-click.
We define the defence-in-depth approach to supplement Microsoft’s native email security where it is most vulnerable. Our threat intelligence offers unparalleled insight into the widest variety of threats, accurately stopping more attacks and improving the efficiency of your business operations.
Take the next step to protect your people and business from human-centric cyberattacks. Learn more about how to safeguard Microsoft with Proofpoint in our solution brief, Microsoft and Proofpoint: More Secure Together.

