The Cybersecurity Stop of the Month blog series explores the ever-evolving tactics of today’s cybercriminals. It also examines how Proofpoint helps businesses to fortify their email defences to protect people against today’s emerging threats.
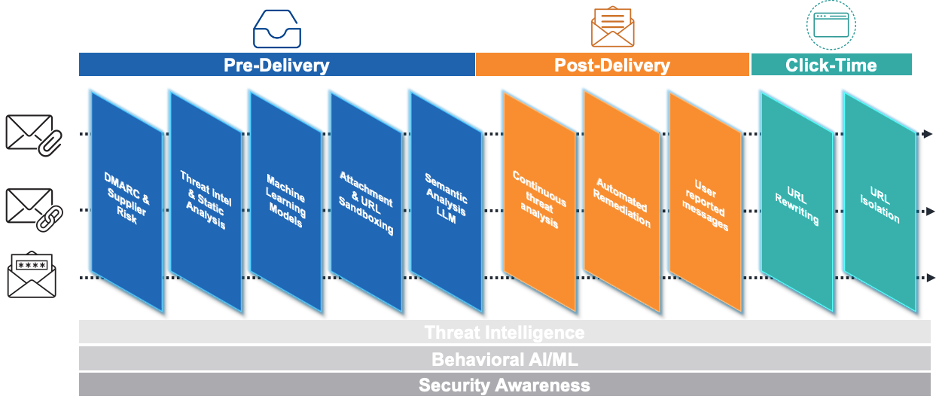
Proofpoint people protection – end-to-end, complete and continuous.
So far in this series, we have examined these types of attacks:
- Uncovering BEC and supply chain attacks (June 2023)
- Defending against EvilProxy phishing and cloud account takeover (July 2023)
- Detecting and analysing a SocGholish Attack (August 2023)
- Preventing eSignature phishing (September 2023)
- QR code scams and phishing (October 2023)
- Telephone-oriented attack delivery sequence (November 2023)
- Using behavioural AI to squash payroll diversion (December 2023)
- Multifactor authentication manipulation (January 2024)
- Preventing supply chain compromise (February 2024)
- Detecting multilayered malicious QR code attacks (March 2024)
- Defeating malicious application creation attacks (April 2024)
- Stopping supply chain impersonation attacks (May 2024)
- CEO impersonation attacks (June 2024)
- DarkGate malware (July 2024)
In this blog post, we look at how threat actors use QR codes in phishing emails to gain access to employee credentials.
Background
Many threat actors have adopted advanced credential phishing techniques to compromise employee credentials. One tactic on the rise involves is the use of QR codes. Recorded Future’s Cyber Threat Analysis Report notes that there has been a 433% increase in references to QR code phishing and a 1,265% rise in phishing attacks potentially linked to AI tools like ChatGPT.
Malicious QR codes embedded in phishing emails are designed to lead recipients to fake websites that mimic trusted services. There, users are prompted to enter their login credentials, financial information or other sensitive data. Threat actors will often try to create a sense of urgency in a phishing attack – for example, claiming account issues or security concerns.
The use of QR codes in a phishing attack helps to provide a sense of familiarity for the recipient, as their email address is pre-filled as a URL parameter. When they scan the malicious QR codes, it can open the door to credential theft and data breaches.
The scenario
Employees of a global developer of a well-known software application were sent a phishing email, which appeared to be sent from the company’s human resources team. The email included an attachment and a call to action to scan a QR code, which led to a malicious site.
A key target of the attack was the vice president of finance. Had the attack been successful, threat actors could have accessed the company’s finances as well as the login credentials, credit card information, and location data for the apps’ millions of monthly active users.
The threat: How did the attack happen?
The phishing email sent by the attacker asked employees to review a document in an email attachment that was advertised as “a new company policy added to our Employee Handbook”.
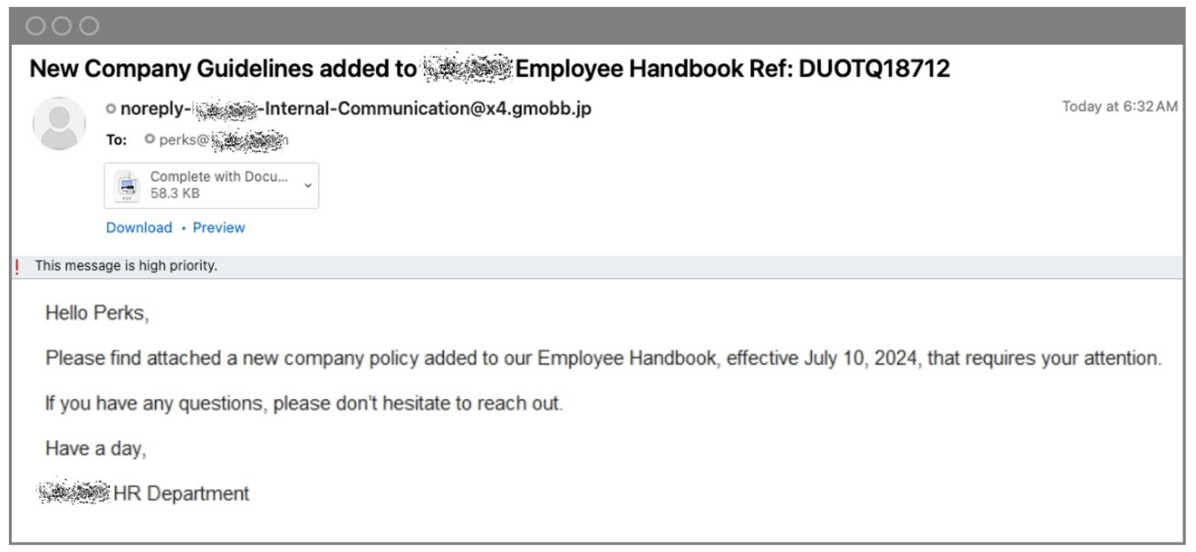
Email sent from an uncommon sender to a division of the location sharing app’s company.
The attachment contained a call to action: “Scan barcode to review document.”
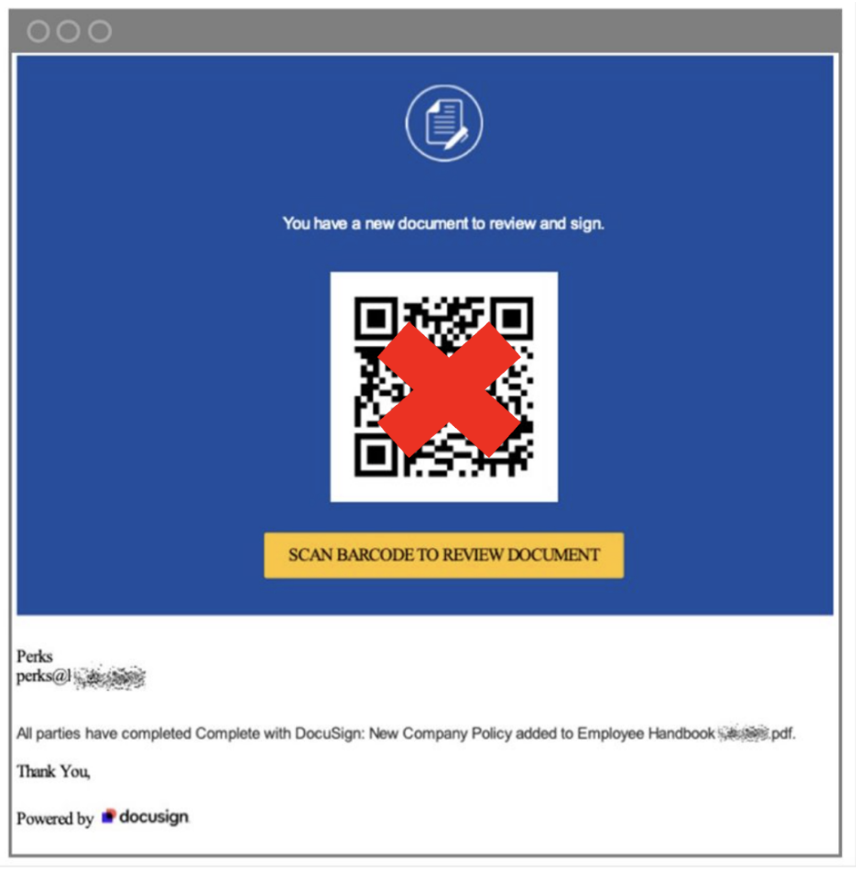
The file type labelled “Barcode” resembling a QR code.
The “barcode” was a QR code that led to a phishing site. The site was made to look like the company’s corporate website. It also appeared to be a legitimate site because it was protected by human verification technology, which can make it nearly impossible for other email security solutions to detect. The technology uses challenges (like CAPTCHAs) to prove that a clicker is a human and not a programmatic sandboxing solution.
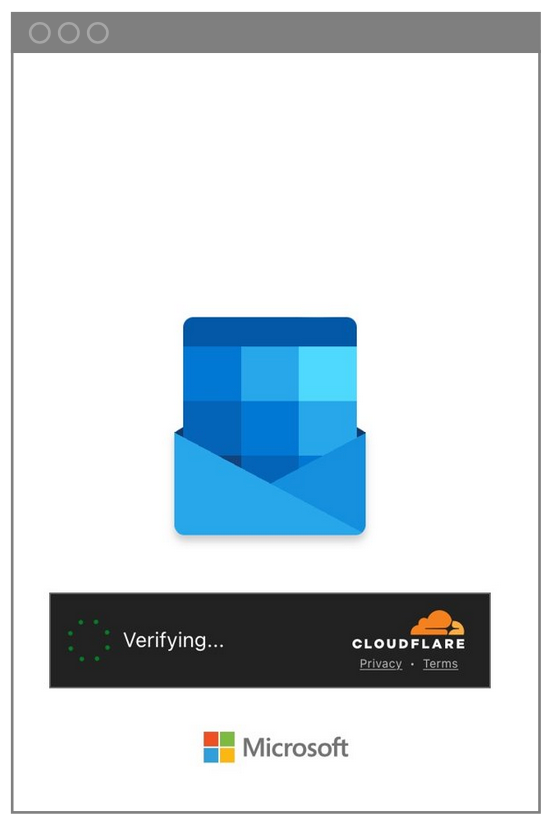
Human verification request.
After the threat actors asked for human verification, employees were prompted to log into the impostor site. This is the point where the attackers could steal their Microsoft credentials.
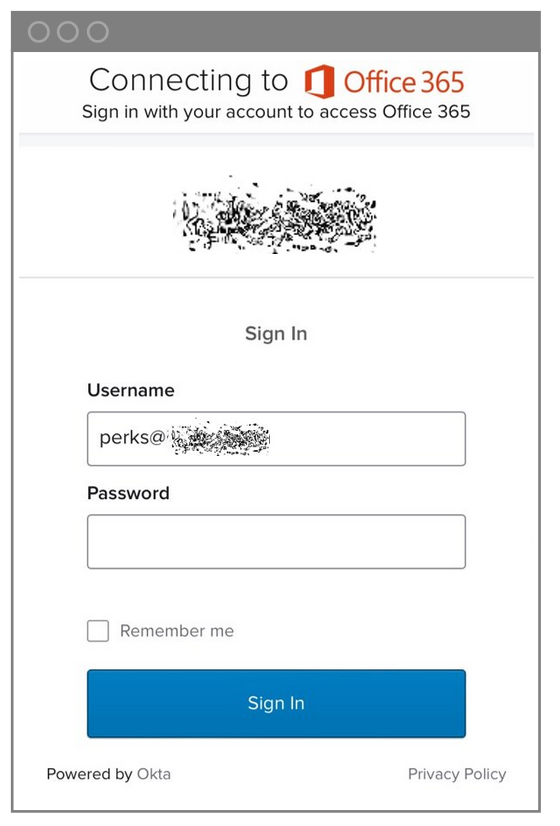
Microsoft Office 365 login credentials screen.
Detection: How did Proofpoint prevent this attack?
Continuous detection and analysis from Proofpoint covers pre-delivery to post-delivery to click-time, ensuring end-to-end protection against modern email threats like:
- Business email compromise
- Advanced phishing
- Other socially engineered attacks
- Malware
In the scenario described above, Proofpoint used several detection indicators to determine that an attack was being attempted.
- Uncommon sender detection. Proofpoint identified unusual or suspicious sender behaviour by analysing sender attributes. For example, we looked at domain reputation, email patterns and deviations from typical communication.
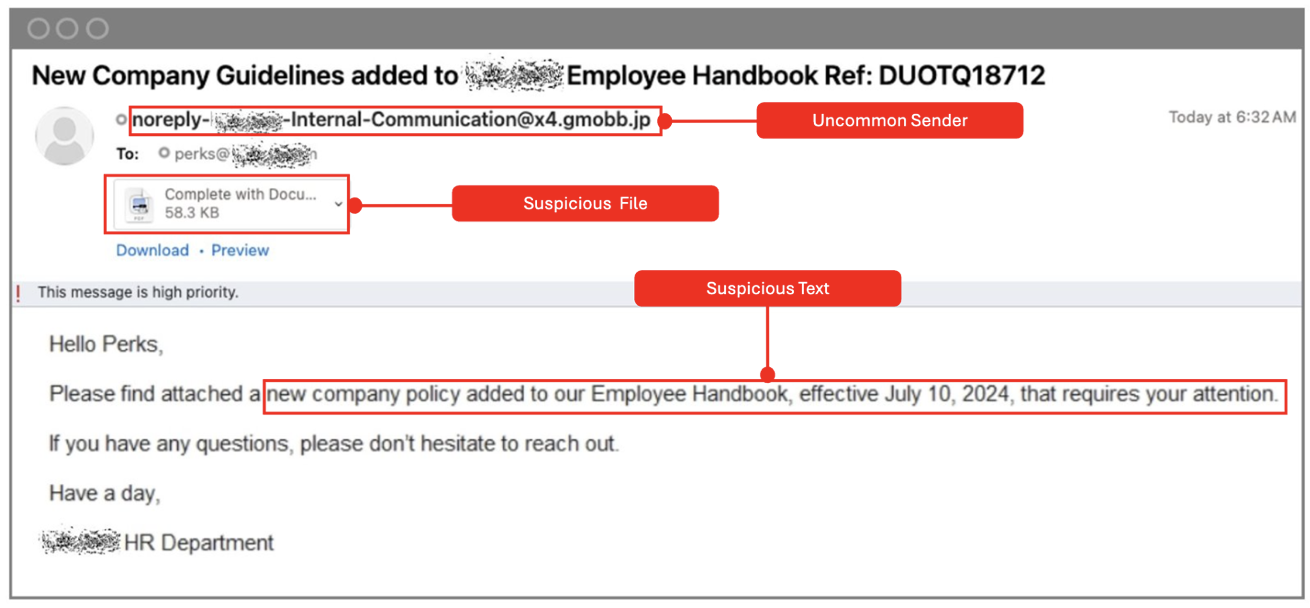
The original email that the threat actor sent to the company’s Perks department.
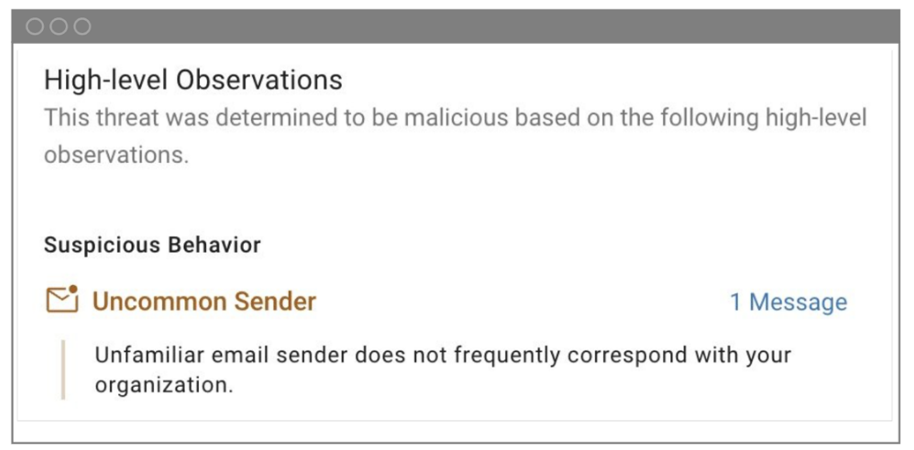
The detection of an uncommon sender by Proofpoint.
- Image detection. Proofpoint scanned the content of the email for embedded images. Malicious images can contain hidden payloads or links to phishing sites.
- QR code decoding. Proofpoint decodes QR codes in phishing emails before recipients can scan them. This reveals the actual URL destination and allows for an assessment of its legitimacy.
- Human verification evasion. Threat actors will sometimes use human verification to obscure malicious domains. Proofpoint looks for patterns that indicate evasion techniques to help ensure better detection.
- URL-to-URL tracking. Proofpoint traced the URLs used in the malicious emails. Suspicious redirections or chains of URLs can indicate phishing attempts.
- Phish kit impersonation. Proofpoint identifies phish kits – fraudulent sites that mimic legitimate services. In this case, the phish kit impersonated a Microsoft login. It even featured a company logo.
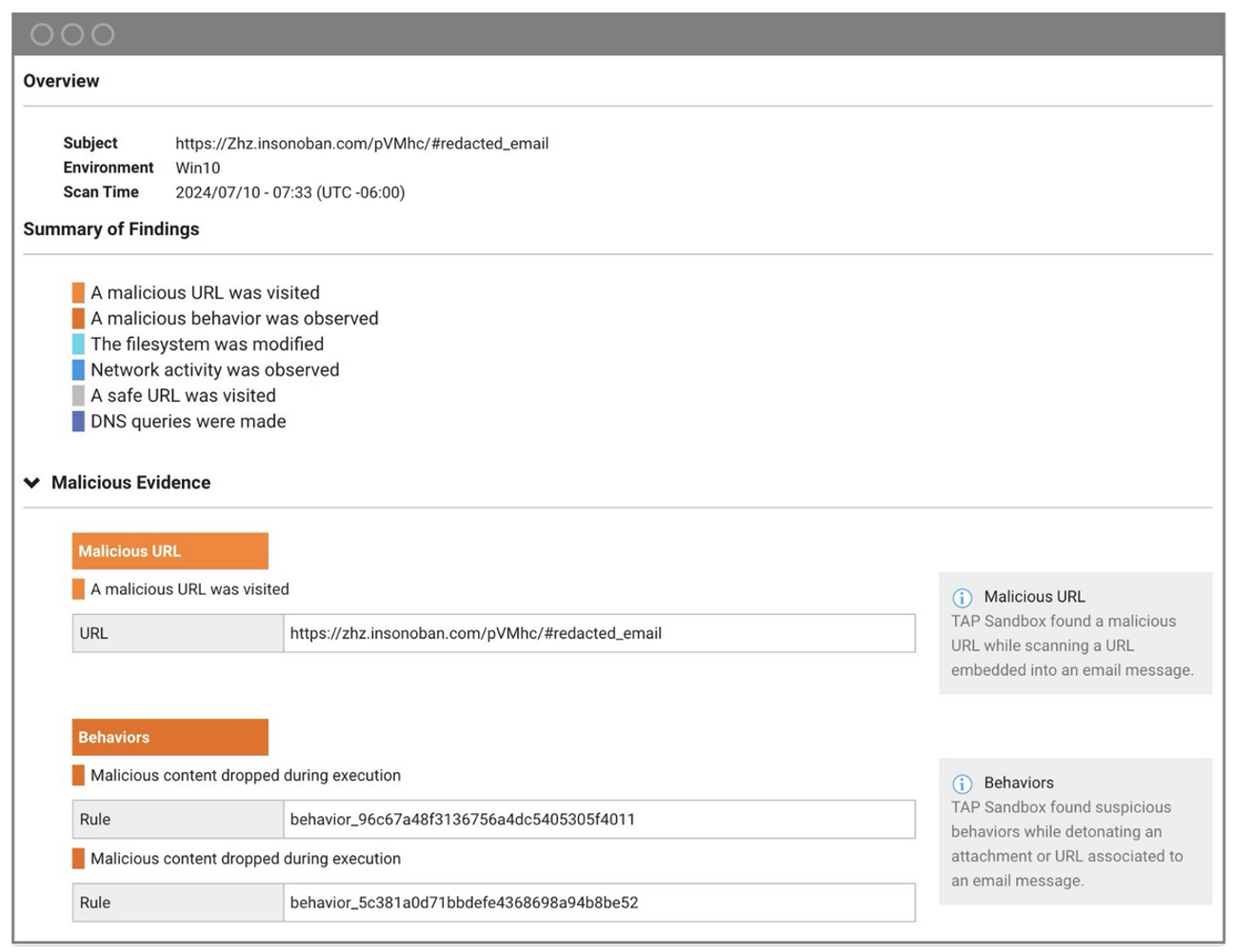
Indicators of compromise and forensics from the threat shown in the Proofpoint TAP Dashboard noting a malicious URL and malicious behaviour.
Remediation: What are the lessons learned?
To help safeguard against credential phishing attacks like the one described in this post, we recommend that businesses take the following actions.
- Stay on the lookout for uncommon senders. Be vigilant about unusual communication patterns, domain anomalies or deviations from typical messages. Provide awareness training so that your users can recognise these red flags, too.
- Help employees learn to identify suspicious file types. Educate your users to beware of files that resemble QR codes.
- Employ URL security measures. Treat QR codes embedded in emails as potential risks and take the following steps:
- Decode URLs before scanning them
- Scrutinise URLs leading pages that seem to be protected by human verification technology
- Implement anti-phishing measures, including regular security awareness training and multi-factor authentication (MFA)
- Verify URLs – especially when there is a prompt to log in – to prevent domain spoofing
Proofpoint delivers human-centric protection
QR code phishing attacks are on the rise. Bad actors are using QR codes to improve their chances of compromising employee credentials. So, it is critical to take steps to protect your business and users against this growing threat.
Proofpoint offers continuous detection and analysis across the entire email delivery lifecycle – from pre-delivery to post-delivery to click-time. Our approach ensures end-to-end protection against modern email threats and boasts a 99.99% efficacy rate. Our behavioural AI, threat intelligence and sandboxing techniques can help you stay ahead of threat actors, even in the face of emerging threats like those that use generative AI to their advantage.
Register for one of our Proofpoint Protect 2024 events in New York, London, Austin or Chicago to learn more about how you can protect people and defend your data in today’s complex threat landscape.

