The leading solution for insider threat and compliance just got better.
Proofpoint helps you manage the most fickle security variable: people. We provide configurable smart alerts and irrefutable video logs of vendors, privileged users, or high risk users who breach security policies and put your organisation at risk.
Version 6.7 further enhances monitoring and investigation capabilities and ensures your organisation will continue to comply worldwide standards.
- Enhanced insider threat library with 180 out-of-the-box smart alerts
- Detection of data exfiltration attempts via print jobs
- User identity anonymisation for enhanced privacy
- Complete monitoring of user activity on Mac endpoints
- Enhanced Integration capabilities with Splunk, QRadar, ArcSight and LogRhythm
You can download the new version 6.7 here. For further assistance, please reference this upgrade guide, product documentation, or as always contact our support team.
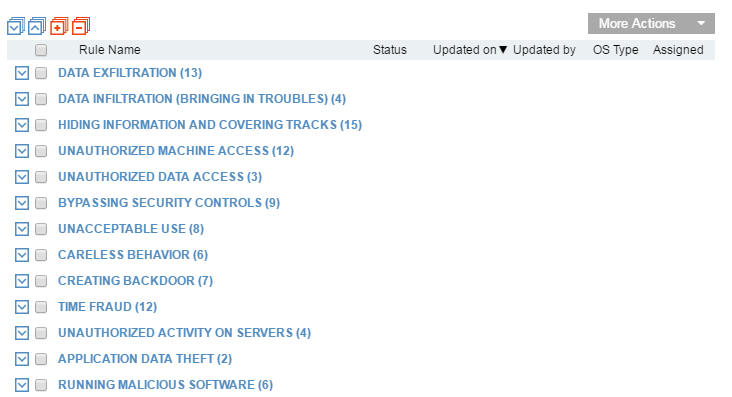
Insider Threat Smart Alerts
180 tuned, categorised and pre-assigned smart rules for out-of-the-box security and insights.
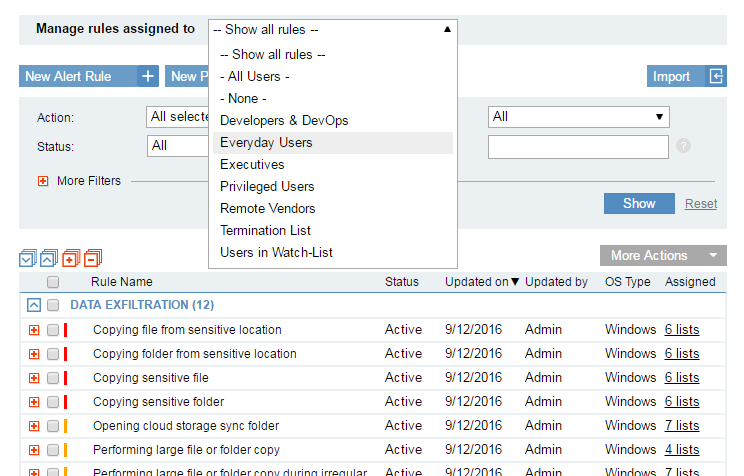
The new library of Insider Threat Smart Alerts significantly increases out-of-the-box value by providing greater visibility to user intent, with virtually no setup time. Alerts are now more accurate, leveraging newly-collected metadata such as website categories and file print detection, and are triggered only for the relevant group of users - whether administrators, everyday users, remote vendors, or terminated employees. Proofpoint ITM 6.7 enables you to efficiently manage large sets of smart alert rules, integrate data from your HR systems, and better protect employee privacy by anonymising personal user information in the Proofpoint ITM console.
Protect User Privacy
Proofpoint ITM 6.7 addresses new privacy laws in Europe, helping you to comply with privacy regulations and concerns worldwide, by configuring Proofpoint ITM to work in Anonymisation mode.
In Anonymisation mode, all personal user information in the Dashboard and the Web Console is encoded – system administrators cannot see the name of the user, role or department, or personal photos. In addition, computers that are accessed and login accounts being used are anonymised.
Security analysts or investigators can view risky users’ alerts and activity, but not the users’ personal identity.
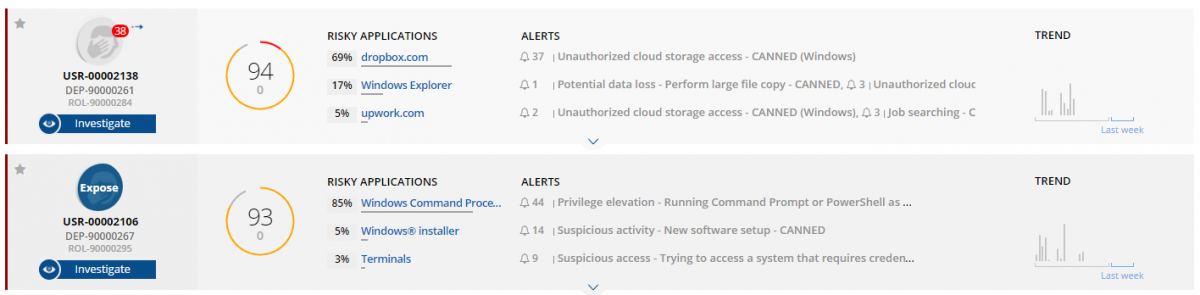
If there is a need to expose user details during the investigation process, an Exposure Request is submitted, and the request is reviewed and approved (or rejected) by an authorised administrator acting as the Privacy Officer.
Proofpoint ITM supports the full process of submitting exposure requests, approving or rejecting them - including notification emails sent to the requester or the approver correspondingly. The Privacy Officer can review all historical requests, and cancel active requests if needed.
In addition, exposure requests have an expiration date; once expired, the user becomes anonymised again.
Mac Support
To complete our enterprise coverage for endpoint monitoring, Proofpoint ITM 6.7 introduces a new agent for Mac with full recording capabilities, including:
- Video and metadata recording
- Configurable recording policies (include/exclude users, applications, or URLs)
- Record when agent is offline
- Recording notification message
- Out-of-policy notifications (warning and blocking messages
- Health monitoring – know if the agent is offline or has been tampered with
All the metadata that is collected from the Mac is searchable, reportable, can be alerted on, and can be exported to your favorite SIEM.
Risky activity that is performed on the Mac is consolidated with other risky activities from the same user, providing a unified risk score for the user and a user-centric view in the User Risk Dashboard.
Additionally, v6.7 expands support for existing platforms with Ubuntu 16.04, RHEL 7.2, and Windows 10 (including Edge Browser) compatibility.
User Risk Trends
A new graph in the User Risk Dashboard allows you to track your overall risk and behaviour trends over a period of time. You can quickly tell whether the risk has increased or decreased over time, compare to last week's average, and see how policy notifications reduce the overall risk.
Similar to all other data in the Dashboard, the information presented in the graph is restricted to what the specific console user is permitted to see.
Job Print Monitoring
Printing documents is a common way to exfiltrate company data. Proofpoint ITM 6.7 can monitor any print job that is sent to the printer, by providing the following information:
- Details about the user/computer who printed the file
- Name of the document being sent to the printer
- Printer name, including manufacturer’s name
- Number of pages sent to the printer
- Whether a large number of pages (10 or more) were sent to the printer
Both local and network printers are supported.
Similar to any other user activity in Proofpoint ITM, you can search for printing activity, create alerts and reports, and export print job activities to your favorite SIEM.
You can download version 6.7 here. For further assistance, please reference this upgrade guide, product documentation, or as always contact our support team.
