Share with your network!
There will always be bad guys who try to circumvent even the best security systems in order to steal data or cause damage. As a critical component of the IT ecosystem in the organisation, Proofpoint's User Activity Monitoring software is a prime target. Let’s take a quick look at some ways that Proofpoint ITM protects itself from being defeated.
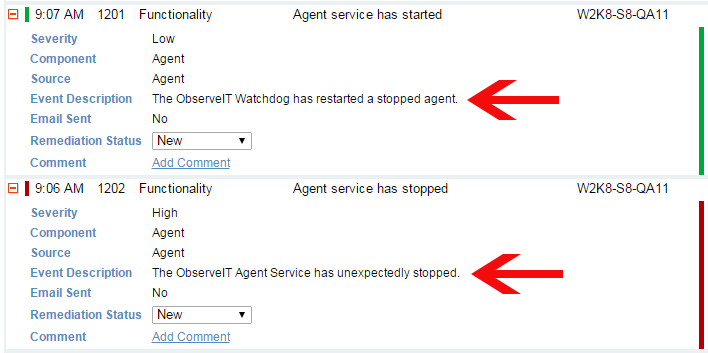
- User kills the Agent process – Proofpoint ITM has a “watchdog” mechanism that continuously monitors the recording Agent. In the event that the Agent process is unexpectedly stopped, the watchdog immediately restarts it and reports the incident to the Application Server. If so configured, the event will also be reported to a SIEM system and/or an email address. On Unix/Linux machines, killing the agent process will report the incident and terminate the shell process.
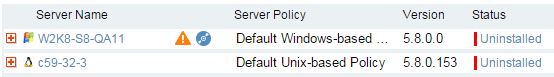
- User tries to uninstall an Agent – Uninstalling an Agent requires an administrator-level password, preventing most users from doing so. Any time an Agent is uninstalled using a password, the uninstall event is reported to, and logged, by the Management Console.
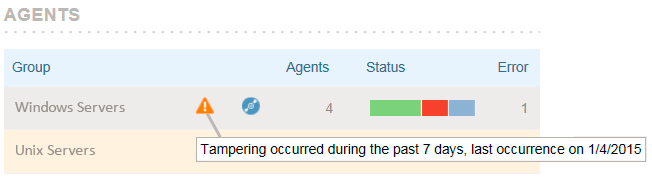
- User tampers with Agent installation files – Proofpoint ITM detects any tampering with its program and configuration files and generates an event which can be seen in the Management Console and Administrator Dashboard. These events can also optionally be sent to an email address and/or to an integrated SIEM system.
- User disconnects computer from the network – If Agent-Server data communication is blocked in any manner, the Agent will go into ‘offline’ mode, caching all captured data locally. When communication is reestablished, the Agent transmits the cached data to the Application Server.
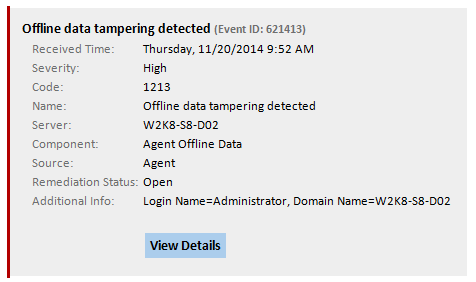
- User tampers with offline Agent data – Accessing Proofpoint ITM data requires administrator access rights, which protects the data from being accessed by most users. However, in the event that a privileged administrator tampers with the data, Proofpoint will detect this tampering and will report such incidents to administrators via email, SIEM integration and the Administrator Dashboard.
- User tampers with the server-side activity data – A privileged administrator might attempt to delete or alter user activity data stored by Proofpoint. To this end, Proofpoint ITM detects if any stored data has been deleted or tampered with, and displays a visual indication on sessions that have been tampered with.
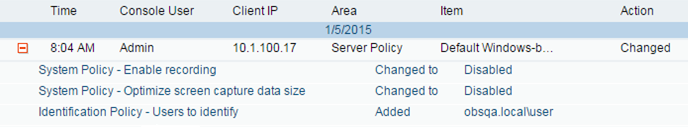
- User changes Proofpoint configuration – A privileged administrator has the ability to alter recording policies; for example, he could exclude himself (or a particular computer) from being recorded temporarily, in order to perform some malicious action. Or he could disable a user activity alert, or change the email recipients of an alert. To mitigate this risk, Proofpoint ITM includes detailed configuration change auditing which will indicate the person responsible for all changes, discouraging such actions.
Of course, no system is foolproof. However, as described here, Proofpoint ITM has implemented a comprehensive set of security mechanisms to protect its User Activity Monitoring system as much as possible. If you have any other ideas or suggestions for improving the system’s protection mechanisms, leave a reply below.
