Business email compromise (BEC) and email account compromise (EAC) are complex, multi-faceted problems. Our “Combating BEC and EAC” blog series dives into how you can stop these threats at your organisation. Each post focuses on one of seven key steps, the first of which we tackle today: blocking imposter threats before they enter.
According to our researchers, nearly 90% of organisations faced BEC and spear phishing attacks in 2019. This $26B problem requires a multi-layered solution—and the journey starts with blocking impostor threats at the gateway. Here’s why imposter threats are so pervasive, and how Proofpoint can help you stop them before the inbox.
The Nature of Impostor Threats
BEC starts with email, where an attacker poses as someone the victim trusts. Unlike traditional email threats that carry a malicious payload, impostor emails have no malicious URL or attachment. Attackers use social engineering to trick or to threaten their victims into making a fraudulent wire transfer or financial payment. Because impostor threats prey on human nature and are narrowly targeted at a few people, they are much harder to detect.
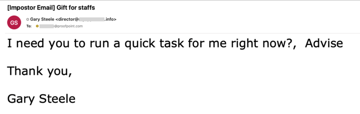
Attacker impersonating Gary Steele, using Display Name spoofing, in a gift card attack
Common BEC attack tactics include:
- Domain spoofing, in which attackers hijack a company’s trusted domains to send fraudulent emails, spoofing the company brand to steal money or data.
- Display name spoofing, where attackers use the name of the spoofed executives, spoofed partners/suppliers, or anyone you trust in the “From” field.
- Lookalike domains, where attackers register a domain that looks very similar to the target company’s trusted domain.
Stopping impostor threats requires a new approach. Solutions that only rely on malware detection, static rules match, or even sandboxing, fail to detect these new types of email threats because attackers forgo malware in favour of a malware-free approach. Here’s how Proofpoint products integrate to offer you better protection.
Advanced Email Security Detects All Malicious Email
Proofpoint’s advanced email security solution uses Impostor Classifier, our unique machine-learning technology, to dynamically analyse a wide range of message attributes, including sender/receiver relationship, header information, message body/content and domain age. It detects malware-less threats, such as phishing and imposter emails, which are common tactics in BEC attacks/scams.
We assess the reputation of the sender by analysing multiple message attributes across billions of messages. We then create a baseline by learning a specific organisation’s normal mail flow and by aggregating information from hundreds of thousands of other Proofpoint deployments. This shared intelligence across the Proofpoint community allows us to quickly identify emails that fall outside of the norm. Rather than depending on static policies and manual tuning, our Impostor Classifier learns in real-time and immediately reacts to the constantly changing threat landscape and attack tactics.
Enforcing Email Authentication
Another effective way of preventing domain-spoofed emails from entering organisations is to enforce Domain-based Message Authentication Reporting and Conformance (DMARC) on third party domains. Proofpoint’s advanced email security solution lets organisations enforce email authentication policies, such as Sender Policy Framework (SPF), Domain Keys Identified Mail (DKIM) and DMARC, on inbound email at the gateway. Some organisations hesitate to enforce DMARC on third party domains because they are concerned that it may interrupt mail flow or block legitimate emails from a trusted source. Some have no idea what policy to create.
To address these challenges, Proofpoint introduced the Verified DMARC feature earlier this year. It provides insights and DMARC reputation services to enforce DMARC on inbound messages. If the sender has a good reputation in implementing DMARC, the gateway will then enforce the DMARC policy of that domain. With this feature, organisations can better protect against inbound impostor threats by taking advantage of DMARC authentication without worrying it may interrupt their mail flow.
Email Warning Tag
When it comes to non-malware threats like phishing and impostor emails, users are a critical line of defence. Email warning tags enable users to make more informed decisions on messages that fall into the grey area between clean and suspicious.

Email warning tag provides visual cues, so end users take extra precautions
Some emails seem normal but may contain characteristics of a suspicious message. In those cases, our email warning tag feature surfaces a short description of the risk for a particular email and reduces the risk of potential compromise by alerting users to be more cautious of the message. Proofpoint’s email warning tag feature supports various use cases, including messages from new or external senders, newly registered domains, that have failed DMARC authentication, and more. By raising awareness of potential impostor email, organisations can mitigate BEC risks and potential compromise.
To find out if your organisation is protected against BEC and EAC attacks, take our assessment here.
