Whether you are the IT manager of a growing startup company or a midsize enterprise, you have probably already faced the increasing demand by end users to remotely access organisational resources.
Naturally, an end user’s main concern is how easy it is to access the services he or she needs, with a user-friendly interface that doesn’t require any technical skills or hands-on configuration. As an IT manager, you are concerned with security; but you’re also concerned about the hard work and the hours of configuration needed to set up and maintain secure remote access for mobile users.
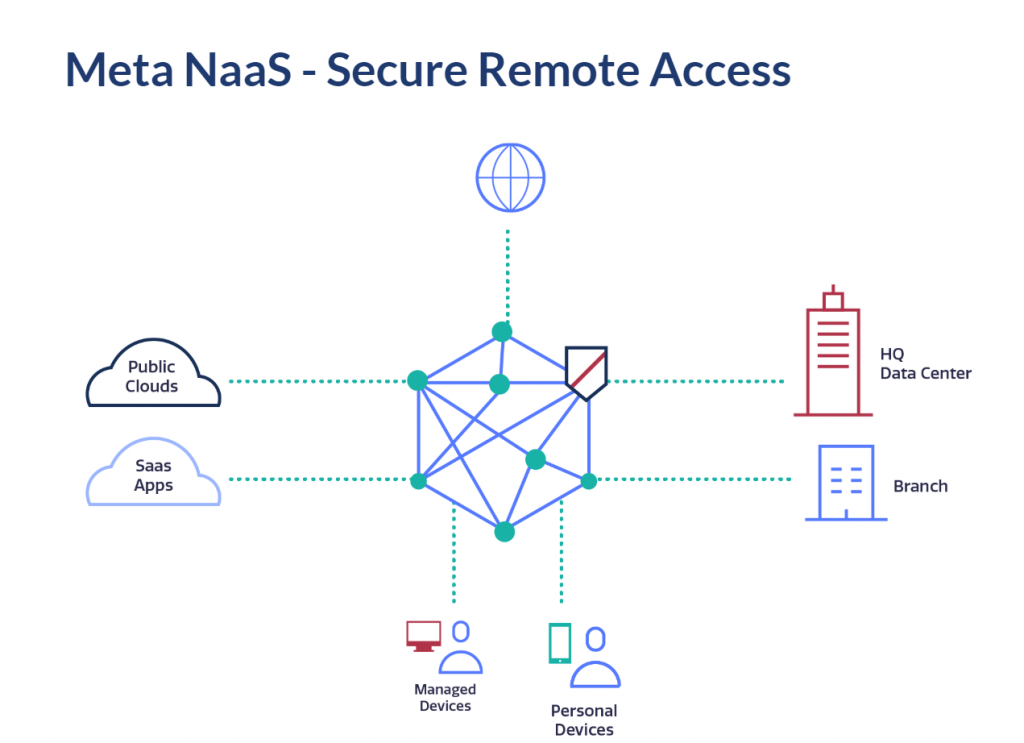
Meta Networks’ Software-Defined Perimeter (SDP) checks all the boxes - on the one hand, it provides end users with multiple connectivity methods and requires no technical skills. On the other hand, it takes the burden off IT in terms of implementation and management, and allows secure remote user access from anywhere to anywhere within the enterprise network.
User Management and Authentication
We all know that IdP providers like Okta, OneLogin or Azure AD have become very common for a reason - they provide greater flexibility for user management and authentication. Some organisations have even replaced their on-premise Active Directory with an external IdP.
Meta’s user management and authentication are fully integrated and interoperable with third-party IdP providers supporting SAML 2.0:
- User Management and Provisioning: Meta supports SCIM, which enables you to provision, synchronise and de-provision users and groups through their existing IdP. All registered user records in the IdP can be automatically created in the Meta NaaS during the user onboarding process. They can then be automatically assigned to relevant groups and policies as needed. In addition, Meta Networks integrates with the old but reliable Active Directory for managing users and groups.
- User Authentication: Any user trying to access resources through the Meta NaaS has to be authenticated using one or more factors. Although Meta NaaS provides its own authentication mechanism (including MFA), authentication can be configured to work via your IdP provider. The user just needs to click ‘SSO Authentication’ on the login page and authentication will be redirected.
2. Self-Service Device Onboarding
When replacing the existing VPN with a new solution, you also want to reduce the burden of onboarding each and every device.
Agent Onboarding
The Meta Networks agent launches a simple self-service onboarding process on each user device. When integrating with an IdP like Okta, OneLogin, or Azure AD, the onboarding process is even easier and shorter. The agent can be set to ‘Always-on,’ so whenever the user logs in, the agent will automatically connect to Meta NaaS for a seamless experience. Once authenticated, the user gains access to the relevant services and applications according to the pre-defined policies.
Browser-Based Access
There are cases where it is not possible to install an agent on an end-user device. This is common for BYOD, as well as with partners and subcontractors who need access to internal corporate resources. This is why Meta Networks developed a clientless, browser-based solution - MetaConnect.
MetaConnect allows users to access corporate resources from any browser with protocols like RDP, VNC, SSH, and any web-based application. The user simply browses to the MetaConnect URL, authenticates and receives a list of available links according to his or her policies.
3. Onboarding Network Resources
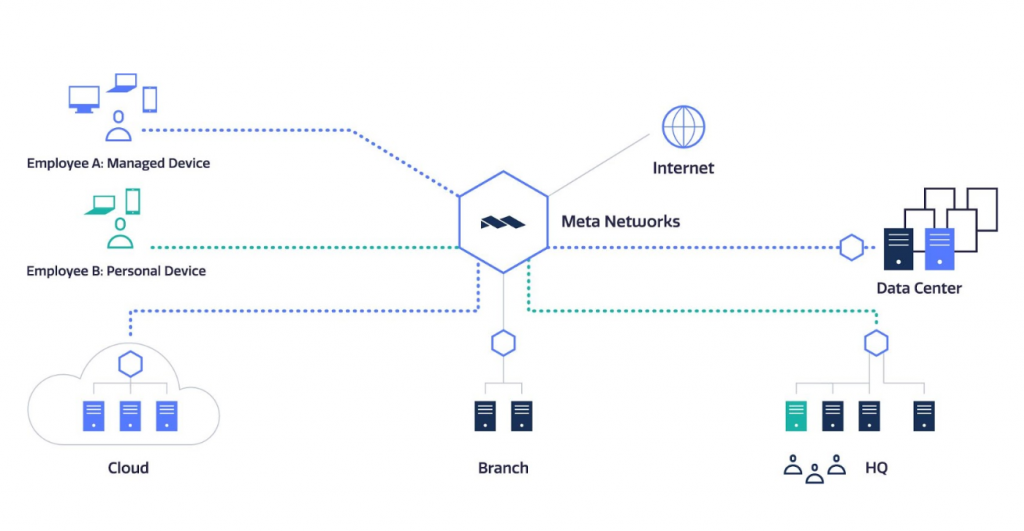
User onboarding and provisioning is only one side of the equation. Users need to access enterprise network services like applications and servers. Most organisations and enterprises host resources on-premises, in private data centers and cloud providers like AWS, Azure, GCP, and OCI. So it’s entirely possible for a midsize enterprise to have services on AWS in Europe, Azure in North America, a data center in India and an office in London.
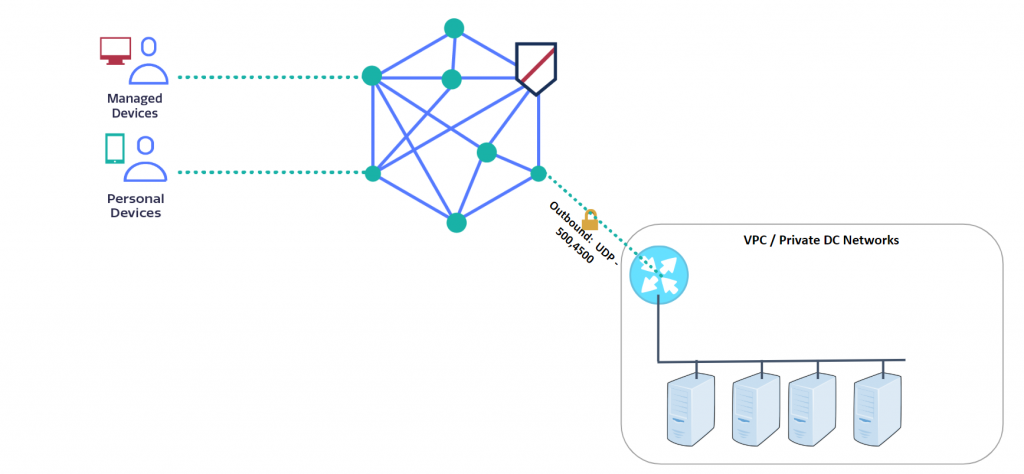
You can onboard resources to the Meta NaaS quickly and simply. This is done using a virtual appliance called a MetaPort, which acts as a gateway for Meta NaaS, establishing an outbound IPSec connection to the nearest Meta PoP. Because the MetaPort initiates the IPSec connection with Meta NaaS, only outbound ports need to be opened in the data center or cloud firewall, which limits exposure to threats.
Setting up a MetaPort takes just a few minutes; it is easy to deploy, scalable, highly available, and requires no maintenance. Meta Networks provides an image for any cloud environment as well as an OVA for in-house VMs.
4. Micro-segmented Access to Network Resources
Most VPN solutions allow access to the entire subnet, requiring IT to manually segment the network in order to reduce the attack surface. But with Meta Networks, micro-segmentation is enforced out of the box.
You can set it up so only the relevant CIDR blocks are exposed through the MetaPort (protecting the rest of your resources from possible attacks) and hiding applications, services and networks from the Internet to control exposure depending on the user and device identity.
5. Policy-Based Access
Once a network resource is onboarded to Meta NaaS, that does not mean that users can access it. The opposite is true - all access is denied, and every network resource is hidden, unless you explicitly expose it as part of the user policy.
The Meta Platform is identity-based, making it easier to manage the access policies and providing granularity at the port and protocol level. Defining policies is as easy as selecting users and groups, and choosing the target, such as a subnet or a specific service with a defined port and protocol.
6. Automating Security with the API
The use of APIs has become very common, and is actually a must on any system.
Meta NaaS includes a rich API, allowing you to easily set up automated workflows, and integrate Meta NaaS capabilities with any service. For example, you can set up an API flow to automatically trigger alerts to your email or Slack channel about events that interest you.
Additionally, automation can be achieved by using the Meta API to automatically implement and auto-configure a full Meta Networks environment with the click of a button, or to build custom-tailored user interfaces.
Summary
At the end of the day, a big part of IT is providing access to services, allowing users to work from anywhere, and securing enterprise assets from threats. That’s not an easy task, however, there are tools to help make it easier to manage, control, deploy and monitor, without overloading your team.
With Meta Networks, you can onboard several applications and hundreds of users in less than a day.
But don't just take my word for it...schedule a demo and see for yourself!
