“The Hacker Way is an approach to building that involves continuous improvement and iteration. Hackers believe that something can always be better, and that nothing is ever complete.”–Mark Zuckerberg
Constantly questioning the tools protecting your organisation’s sensitive data is the responsibility of all CISO/IT Security Directors. Hackers never trust that something is complete, neither should you. Adopting a hacker state of mind, as stated by Mark Zuckerberg, and continuously testing your security will help you tighten your organisation’s threat protection. Using the data provided by risk assessments is a critical step to continuous testing.
Keep on edge with risk assessment
In the State CIO Priorities for 2015 compiled by NASCIO (National Association of State Chief Information Officers), security has emerged as the #1 priority with ‘risk assessment’ identified at the top of the initiative list. NIST (National Institute of Standards and Technology) backs risk assessments in its Cybersecurity Framework published in February 2014. The writing’s on the wall–risk assessments are critical to good security hygiene.
As email is still the number one way for bad actors to penetrate your organisation, it is critical to identify your vulnerabilities and reexamine your current solution against others. Taking this pragmatic approach allows you to determine if your current solution is meeting your organisation’s requirements as well as identifying other solutions that may be a better fit for your organisation’s needs.
Email security risk assessment results from Proofpoint
Proofpoint will collect data by placing Proofpoint Enterprise Protection behind the incumbent email security solution of an organisation. We monitor the email traffic that passes through the incumbent solution, marking those that we consider unsafe. As the data below demonstrates, Proofpoint catches threats that slip through the net of other solutions.
In this table you can see real-life results of three different audits, in three different organisations, each one using a different vendor.
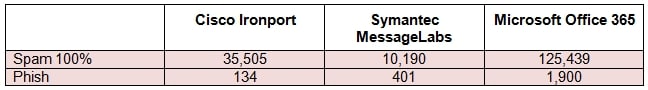
Data was collected from actual organisation risk assessments. For more data details, contact us.
The highlight from this data is the fact that threats that have high potential damage, such as spam and phishing, managed to make it through. (For additional on email threats, consult our article Looking Back at 2014: A Little Good, A Lot of Bad.) As a security professional, focusing on continuous testing and improvement ensures that the information gathered during such a risk assessment is exactly what you need to have in hand to protect your organisation.
