Targeted Attack Protection
 Email Security and Threat Protection
Email Security and Threat Protection
More than 90% of targeted attacks start with email—and these threats are always evolving. Proofpoint Targeted Attack Protection (TAP) helps you stay ahead of attackers with an innovative approach that detects, analyses and blocks advanced threats before they reach your inbox. This includes ransomware and other advanced email threats delivered through malicious attachments and URLs. And zero-day threats, polymorphic malware, weaponised documents and phishing attacks. Proofpoint TAP provides adaptive controls to isolate the riskiest URL clicks. Proofpoint TAP also detects threats and risks in cloud apps, connecting email attacks related to credential theft or other attacks.
Defend Against URL-, Attachment- and Cloud-Based Threats
Proofpoint Targeted Attack Protection (TAP) is built on our next-generation email security and cloud platforms. This gives you a unique architectural advantage. Proofpoint TAP uses static and dynamic techniques to continually adapt and detect new cyber-attack patterns. We analyse potential threats using multiple approaches to examine behaviour, code and protocol. This enables us to detect threats early in the attack chain. This includes cyber-attacks that use malicious attachments and URLs to install malware or trick your users into sharing passwords and sensitive information. This sandboxing and analysis take place in virtual environments, bare-metal hardware, and they leverage analyst-assisted execution to maximise detection and intelligence extraction. Proofpoint TAP also detects threats and risks in cloud apps and connects email attacks related to credential theft or other attacks. Our technology doesn't just detect threats and ransomware—it also applies machine learning to observe the patterns, behaviours, and techniques used in each attack. Armed with that insight, Proofpoint TAP learns and adapts. This makes the next attack easier to catch.
Proofpoint ranked #1 in G2’s Summer 2023 Email Security Reports
|
|
|
|
|
TAP URL Defense
- Protection against URL-based email threats including malware-based threats and credential phishing
- Predictive analysis that preemptively identifies and sandboxes suspicious URLs based on email traffic pattern
- URLs are rewritten to protect users on any device or network as well as provide real-time sandboxing on every click
TAP Attachment Defense
- Protection against known malicious documents
- Unknown attachments are analysed and sandboxed
- Includes sandboxing and analyses of numerous file types, password protect documents, attachments with embedded URLs and zip files
Advanced BEC Defense
- Protection against business email compromise (BEC) and supplier account compromise threats
- Analysis of every detail within a message, from header forensics, originated IP address, sender and recipient relation, and reputation analysis to deep content analysis
- Gain visibility into techniques, observations and message samples for in-depth analysis
TAP SaaS Defense
- Surface suspicious log-in activity
- Gain visibility into broad file sharing
- Detect critical and high severity third-party applications
TAP URL Isolation for VAPs
- Provides adaptive security controls for your Very Attacked People™ (VAPs) based on risk profile
- Enables your users to access unknown or risky websites while still protecting your organisation against URL or web-based attacks
- Provides enhanced visibility and protection for permitted clicks
Proofpoint Supplier Threat Protection
- Proactive monitoring of third-party and supplier domains that interact with your company to detect activity synonymous with an account being compromised
- Streamlined evidence gathering with prioritisation of high-risk compromised accounts
- Early alerting if any vendor you have email interactions with has a compromised account observed anywhere in the Proofpoint ecosystem, even if your company has not yet been targeted
Proofpoint Supplier Threat Protection is an optional add-on to Proofpoint TAP (additional licensing required).
Supply Chain Attack
TAP Account Takeover
- Protect against email account takeover across the attack chain
- Gain visibility and investigate how attackers access accounts and their malicious activities post-account access
- Remediate compromised accounts, malicious mailbox rule changes, abused third-party apps and data exfiltration in email and cloud environments
Proofpoint TAP Account Takeover is an optional add-on to TAP (additional licensing required). It replaces Cloud Account Defense, providing greater post-compromise functionality.
TAP Account Takeover
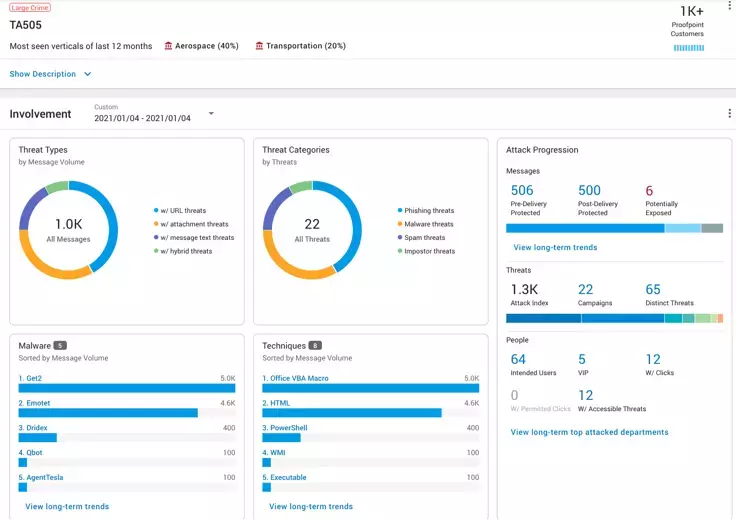
Gain Deep Insight into the Threats Targeting and Attacking Your People
Only Proofpoint provides threat intelligence that spans email, cloud, network, mobile and social media. Our threat graph of community-based intelligence contains more than a trillion data points that correlate cyber-attack campaigns across diverse industries and geographies. You can easily leverage this insight through the Proofpoint Targeted Attack Protection (TAP) Threat Dashboard as well as other unique insights at the organisation and user level.
Advanced BEC Defense
Proofpoint Advanced BEC Defense powered by NexusAI is designed to stop a wide variety of email fraud. This includes payment redirect and supplier invoicing fraud from compromised accounts. For these types of threats, you need a more sophisticated detection technique, since there’s often no malicious payload to detect.
With Advanced BEC Defense, you get a detection engine that’s powered by AI and machine learning. And it’s specifically designed to find and stop BEC attacks. It analyses multiple message attributes, such as:
- Message header data
- Sender’s IP address (x-originating IP and reputation)
- Message body for urgency and words/phrases, and more
It then determines whether that message is a BEC threat. And it detects various attacker tactics, such as reply-to pivots, use of malicious IPs, and use of impersonated supplier domains.
Advanced BEC Defense also gives you granular visibility into BEC threat details. It provides the BEC theme (e.g., supplier invoicing, gift card, payroll redirect), observations about why the message was suspicious, and message samples. These key details help your security team better understand and communicate about the attack.
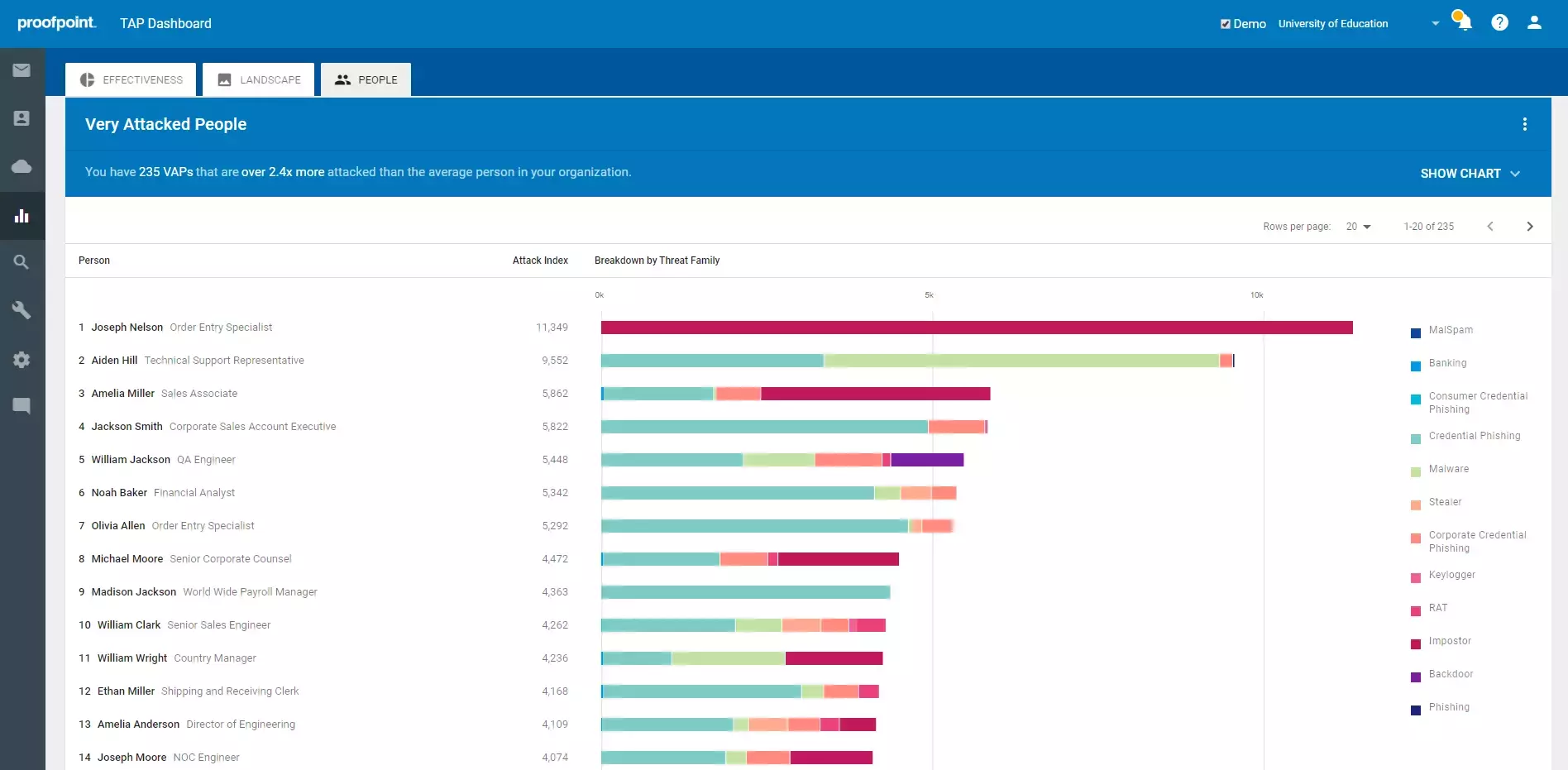
Very Attacked People™ (VAPs)
- Your security teams need to know who your most attacked people, or VAPs, are in order to protect them against the threats and ransomware that target them. The Proofpoint Attack Index helps identify these VAPs. This index is a weighted composite score of all threats sent to an individual in your organisation. It scores threats on a scale of 0-1000 based on four factors: threat actor sophistication, spread and focus of attack targeting, type of attack, overall attack volume. By better understanding your VAPs, you can then prioritise the most effective ways to resolve threats.
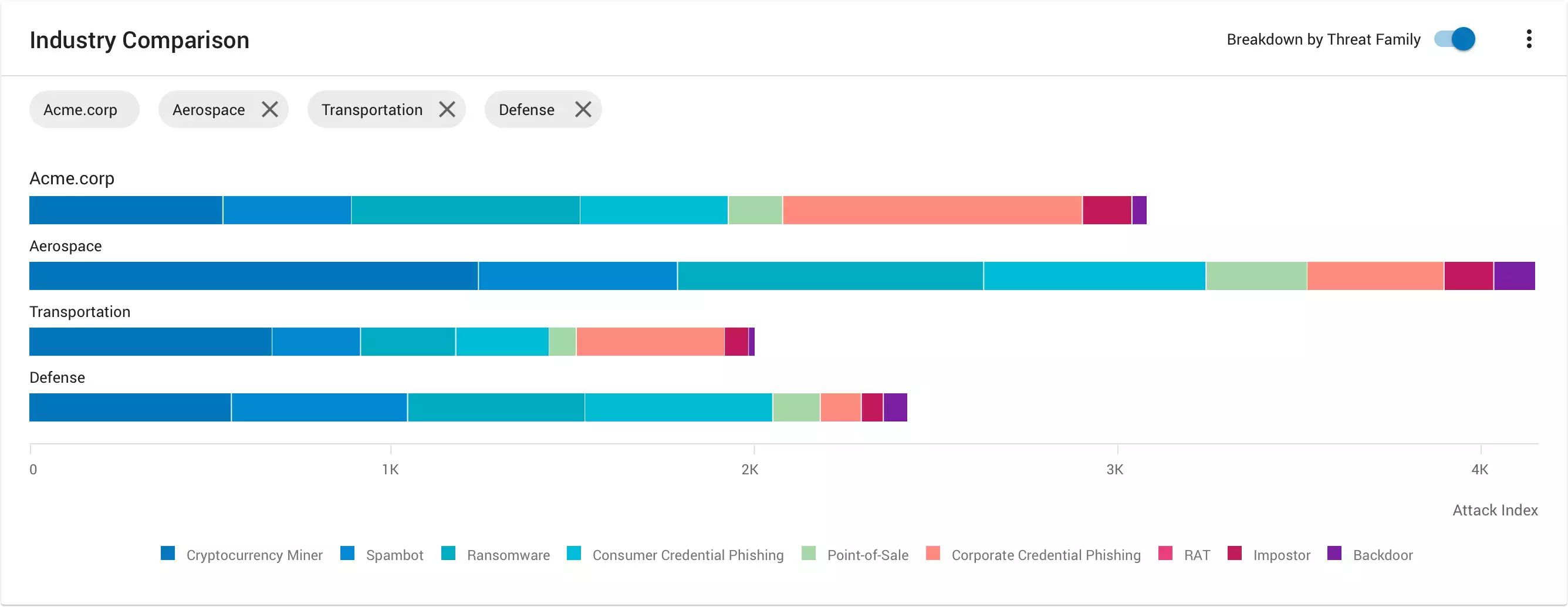
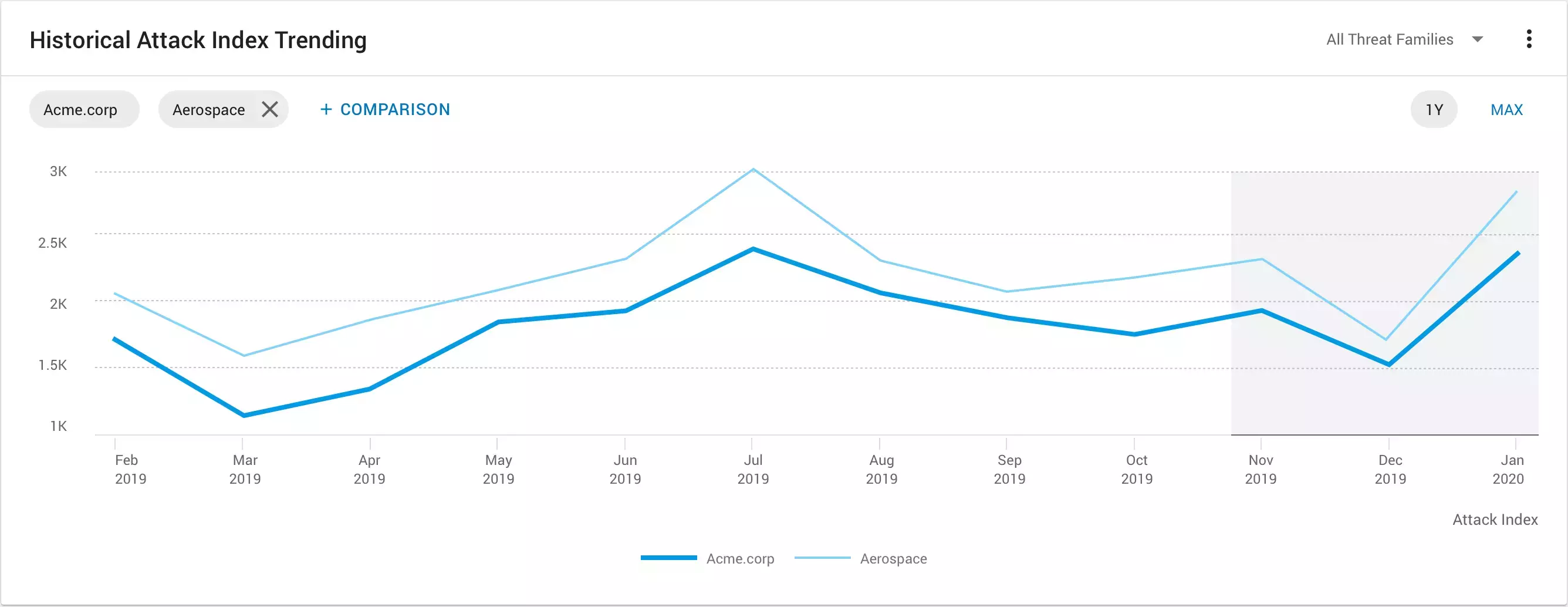
Company-Level Attack Index
- The Company-Level Attack Index includes two reports. They are the Industry Comparison report and the Historical Attack Index Trending report. These are both executive-level reports that can help you understand and communicate company-level risk based on the severity of the threats attacking your organisation. You also get visibility into how your monthly Company Attack Index changes over time. This allows you to surface tactical insights on how the threat landscape has been shifting. You can also leverage our proprietary Proofpoint data. With it, you can compare your Company Attack Index to your peer group (by industry, for example). This enhances and extends your visibility into the threat landscape.
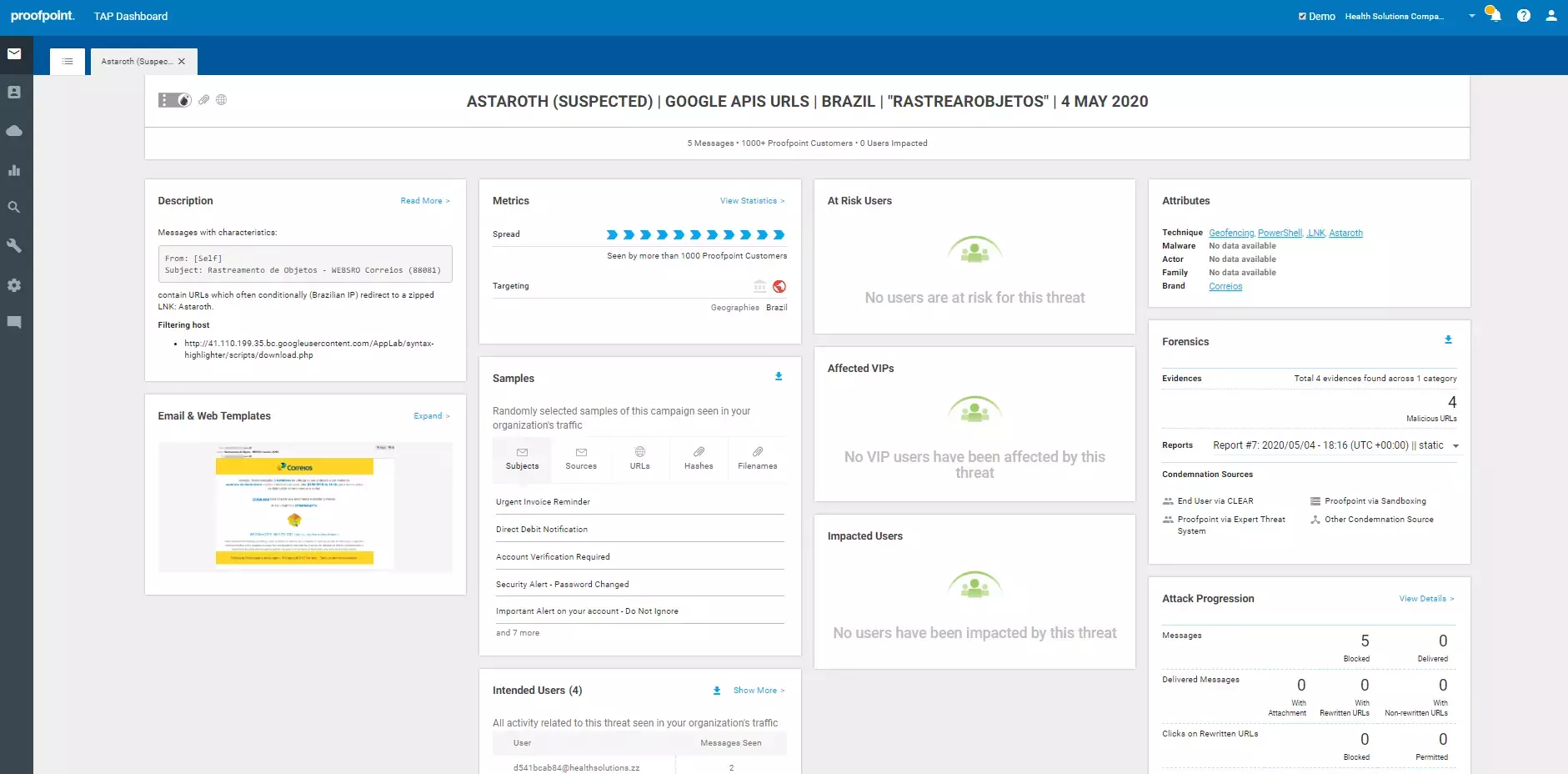
Threat Insight Dashboard
- The TAP Threat Insight Dashboard provides detailed information on threats and campaigns in real time. You gain visibility into both widespread and targeted attacks. It gives you details around the threat itself from impacted users, attack screenshots, and very in-depth forensics.
Superior Intel and Visibility
Only Proofpoint provides threat intelligence that spans email, cloud, network, mobile apps and social media. Our threat graph of community-based intelligence contains more than 600 billion data points that correlate attack campaigns across diverse industries and geographies. You can easily leverage this insight through the TAP Threat Dashboard. The TAP Threat Dashboard:
- Can be accessed through a web browser. Get visibility into the threats entering your organisation. See who is attacking, how they're attacking and what they're after.
- Provides ransomware protection data at organisation, threat and user level. This helps you prioritise alerts and act on them.
- Highlights broad attack campaigns and targeted ransomware threats. You can see attacks directed at your executive leadership and other high-value employees.
- Surfaces account compromises connected to email attacks.
- Highlights brute-force attacks and suspicious user behaviour.
- Provides detailed forensic information on threats and campaigns in real time. You get downloadable reports and can integrate with other tools through application programming interfaces (APIs).
Protection Beyond the Network
To protect your people, your defences must work where they do—at the pace they do. With TAP, you can:
- Protect users on any network, on any device and in any location where they check their email. TAP works on internal or external networks (both public and private) on mobile devices, desktop PCs and the web.
- Deploy quickly and derive value immediately. You can protect hundreds of thousands of users in days—not weeks or months. TAP can be easily configured as an add-on module to the Proofpoint Protection Server, which can be deployed as a virtual appliance, hardware appliance or cloud service.
- Surface file-based threats in your SaaS file stores and detect account compromise.
- Stay ahead of attackers with frequent, daily updates to our cloud analysis services.
- Enhance the security of any email platform—even for Microsoft Office 365 or hybrid Exchange environments.
Learn More About our Office 365 Solutions
Threat Actor Insight
- As people are the continued target, it becomes more and more critical for your organisation to have a holistic picture of attackers. Our threat researchers have been curating data around attackers for many years, and this intelligence is available to you in the TAP dashboard. You can see which attackers are targeting your people, who is being targeted, the tactics and techniques that are being used—including any attack trends that form over time. This helps you prioritise the additional security and remediation controls you need. And it helps you better protect your people from the attackers who target them.
Detection of Compromised Supplier Accounts
Proofpoint Supplier Threat Protection provides an added layer of protection against compromised supplier and third-party email accounts. It detects, prioritises, and provides you with actionable insights on compromised accounts observed anywhere in the Proofpoint ecosystem.
- Identifies, prioritises, and helps block activity from compromised supplier and known third-party accounts
- Provides actionable insights on compromised supplier account traffic observed throughout the Proofpoint ecosystem or in a customer’s incoming traffic
- Streamlines investigation of compromised third-party accounts
Proofpoint Supplier Threat Protection is an optional add-on to Proofpoint TAP (additional licensing required).
Defend Against Supplier Account Compromise
Cross-Vector Threat Intelligence
TAP uses threat intelligence from the Proofpoint Nexus Threat Graph. This graph collects, analyses and correlates trillions of real-time data points across email, the cloud, networks and social media. It powers our industry-leading technology platform and works across our solutions portfolio. There’s nothing extra for you to install, deploy or manage.
Because TAP uses the intelligence from the Nexus Threat Graph, it gives you unmatched insight into cross-vector threats to keep you ahead of today’s threats. For example, this includes emails with links to unsafe OAuth-enabled cloud apps to trick users into granting broad access to their cloud accounts. These attacks often use familiar websites and OAuth services. And stopping them requires a solution that spans multiple vectors, such as cloud and email.
- Real-time community threat intelligence from more than 115,000 customers
- Multi-vector visibility from email, cloud, network and social media
- More than 100 threat actors tracked for insight into attackers’ motives and tactics
