The Cybersecurity Stop of the Month blog series explores the ever-evolving tactics of today’s cybercriminals and how Proofpoint helps organizations better fortify their email defenses to protect people against today’s emerging threats.
Phishing remains the No. 1 tactic that cybercriminals use to target your people and steal valuable data and funds. According to Verizon, phishing is the top method that attackers use to gain unauthorized access, and it continues to evolve in both frequency and sophistication. This trend is not just alarming—it’s costly. IBM estimates the average data breach that originates with phishing causes a staggering $4.88 million in damages.
In this post, we’ll analyze a new and complex e-signature phishing threat. In it, attackers combine several novel tactics to get around native Microsoft email security.
Background
In an e-signature phishing attack, bad actors will spoof a trusted brand and send malicious content through legitimate digital channels. Often, they use advanced methods like adversary-in-the-middle (AitM) to bypass multifactor authentication (MFA) in an effort to further extend their access. And when bad actors use combined tactics, such as Adversary-in-the-Middle plus geofencing, they can be extremely successful in evading detection.
Let’s look at e-signature phishing attacks in more depth:
Impersonating trusted brands
Threat actors leverage brands and services of trusted electronic signature services, such as DocuSign or Adobe Sign. They use them to trick recipients into directly downloading malicious documents or visiting fake websites where they enter their login credentials. Of the billions of phishing emails that Proofpoint sees each year, our 2024 State of the Phish report shows that 3.5M malicious messages abused DocuSign branding.
Bypassing MFA
Attackers that use e-signature phishing lures frequently seek more than just credentials. They also aim to intercept MFA codes or steal session cookies. Adversary-in-the-middle (AitM) tactics use proxy sites to capture login details and MFA codes in real-time. This grants attackers access to the victim’s account and any active session cookies which can, in turn, unlock other websites.
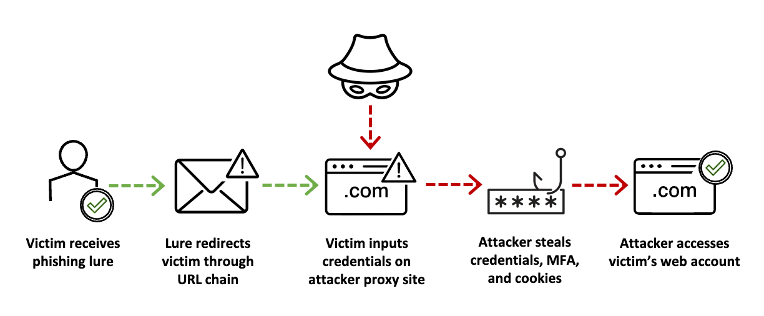
Steps in the adversary-in-the-middle threat technique.
Geofencing access
Threat actors use geofencing techniques to limit from where their targets can access their phishing sites or malicious content. By restricting access to specific geographic locations, such as the target’s region or country, they reduce the likelihood of detection by IT teams and automated security scanning tools based in other regions.
Deploying just one of these tactics can be enough to convince your people to take action. But what happens when a savvy scammer uses all three?
The scenario
Our recent example shows how combining the methods above enabled a threat actor to successfully target a global electric company.
The threat actor’s intended victim supplies power to one of the world’s largest cities and employs more than 15K people. In this attack, the offending message was delivered to the mailbox of a C-suite executive. It bypassed Microsoft security tools as well as additional detection meant to stop such multi-stage campaigns. Thankfully, Proofpoint caught this threat and helped secure the company from a possible cyberattack or data breach.
The named threat actor launching this threat was first observed by Proofpoint in 2021. They are known for using delivery mechanisms like multistep redirection chains, advanced filtering and highly customized lures. Frequent targets include the manufacturing, technology and energy industries. While they often spoof brands like Microsoft OneDrive and LinkedIn, in this e-signature-based phishing attack they chose popular digital transaction management platform, DocuSign.
The threat: How did the attack happen?
Here’s how the attack unfolded:
1. Setting a lure. The attack started with an email that spoofed DocuSign’s brand to appear as a legitimate follow up notice. It offered the recipient a physical copy of supposedly completed forms. The message itself was highly personalized. It included both the recipient’s name and company in the subject line and body. But the sender of the message was unknown to the executive and used a newly registered email domain to launch their lure.
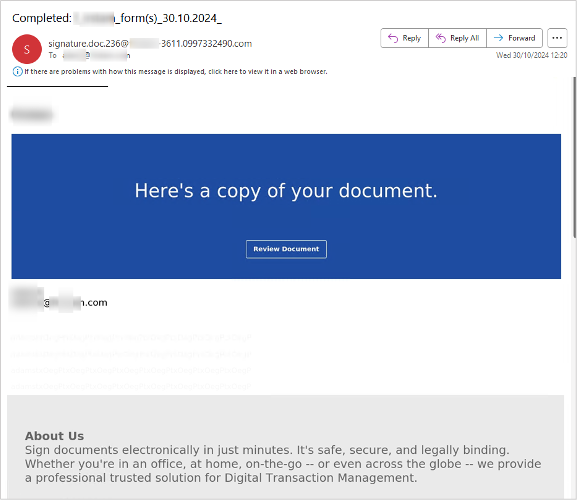
Spoofed DocuSign message received by the user.
2. Following the chain. The URL link in the message leads to a long string of URLs hosted on Google infrastructure. Redirecting through a multi-step chain of well-known and safe domains makes it more difficult for email security tools to determine the attacker’s path.
3. Landing on a proxy site. Once the redirection is complete, the target user arrives on what appears to be a legitimate DocuSign login portal. However, this page is a proxy site which routes the user's requests and responses through a third-party proxy server that acts as the “middleman.” As an additional deceptive measure, the attacker used geofencing to allow only users in the victim’s geographic region to access the proxy site.
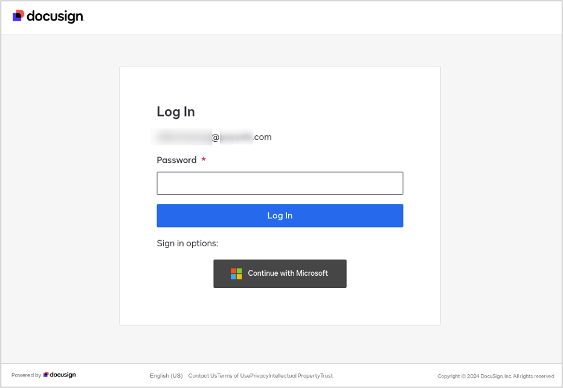
Fake DocuSign login portal on proxy website.
4. Gaining unauthorized access. Through the proxy site, the attacker can see every move made by the user. In this case, they scraped the DocuSign credentials and MFA codes as well as the active session cookies tied to the user’s browser. These session cookies can unlock an untold number of professional and personal web accounts—a virtual treasure trove for the threat actor. These are classic AitM techniques. As a gesture of convenience, the scammer allows the user to login with their Microsoft credentials hoping to extend their ill-gotten access further.
Detection: How did Proofpoint identify this attack?
Even though the electric company used built-in email security which claims to detect advanced phishing threats, this attack successfully reached the intended user’s inbox.
Microsoft’s email threat detection missed the attack for several reasons. First, it only opens URLs if they lead to a direct payload like malware. Even then, sandboxing only happens after a user clicks on the malicious link. Its sandboxing has demonstrated significant gaps in detecting threats that use complex evasion techniques and has struggled to follow second, third or fourth-level URL chains.
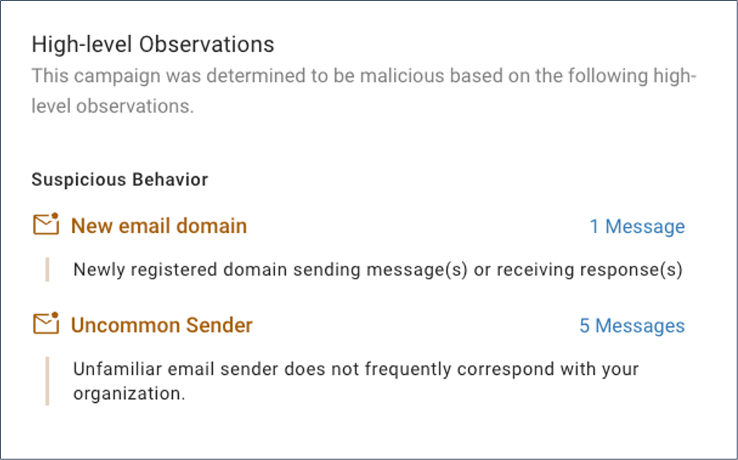
Condemnation summary of signals Proofpoint used to detect the threat.
Proofpoint easily identified this message through a combination of threat analysis sandboxing and our end-to-end Proofpoint Nexus AI platform. E-signature threats are difficult to stop because you need both to make a conclusive condemnation.
- Behavioral AI signals. Proofpoint behavioral AI analyzes user behavior to look for abnormal activity. It alerts organizations to potential threats with over 99.99% accuracy. In this case, we analyzed behavior patterns and found that the sender had never interacted with the targeted user. What’s more, they had recently registered a new email domain to send their message.
- URL sandboxing. Proofpoint uses the industry’s only URL sandboxing technology that works before, during and after email is delivered to identify and block malicious links. Our advanced URL-to-URL (U2U) analysis traces relationships between URLs. As a result, it can map complex and extended attack chains. Additionally, Proofpoint supports multiple global threat analysis centers that can bypass geofencing tactics. This ensures threats that target specific regions are detected and quickly neutralized.
Our detection stack’s accuracy is unmatched. It identifies less than one false positive reported in every 19 million messages. What’s more, we make details about these threats visible and easily accessible by security and IT teams. Threat actors’ tactics are automatically aligned to the MITRE ATT&CK framework (see below). This enables your analysts to map our visibility against your own methodologies. Consequently, they can better understand the nature of each threat and respond accordingly.
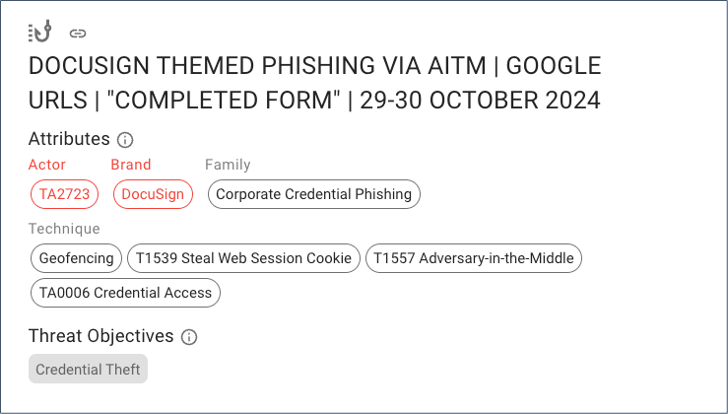
Attributions Proofpoint assigned to the condemned message.
Armed with this threat visibility, we were able to notify the energy company’s security team and remove the impending attack.
Remediation: What are the lessons learned?
Here’s what we recommend to help protect against e-signature phishing threats:
- Get comprehensive URL analysis. Look for a tool that can uncover hidden threats in complex redirect chains. It should also be able to detect malicious content that’s hosted on reputable domains. And it should be able to bypass geofencing tactics that limit visibility. Without these capabilities, organizations can miss sophisticated attacks that are designed to exploit gaps in traditional email defenses.
- Track behavioral anomalies with AI. When evaluating tools that use AI, make sure that they include behavioral analysis. This can help identify when users interact with unfamiliar senders or domains, revealing phishing attempts. Also, users should receive security training to recognize these red flags, too.
- Invest in global threat visibility. Organizations need to see and understand threats to prioritize the most relevant risks and remediate them in a timely way. Ultimately, better visibility leads to a stronger threat detection, response, and overall security posture.
Proofpoint delivers human-centric protection
E-signature phishing threats provide a grim example of how email attacks are becoming more sophisticated. They exploit gaps in native security measures and target organizations where they’re most vulnerable—their people. To combat them, you need more than basic email security tools. You need complete human-centric security with both advanced threat intelligence and AI-driven detection capabilities.
Proofpoint provides end-to-end protection that detects threats at every stage, from pre- and post-delivery scanning to click-time defenses. By combining behavioral analysis with advanced URL sandboxing, we protect against even the most complex phishing attempts.
Protect your people and business from the widest variety of cutting-edge phishing attacks. Download our Threat Protection solution brief to learn how.
Read our Cybersecurity Stop of the Month series
To learn more about how Proofpoint stops advanced attacks, check out our previous blogs in this series:
- Uncovering BEC and supply chain attacks (June 2023)
- Defending against EvilProxy phishing and cloud account takeover (July 2023)
- Detecting and analyzing a SocGholish Attack (August 2023)
- Preventing eSignature phishing (September 2023)
- QR code scams and phishing (October 2023)
- Telephone-oriented attack delivery sequence (November 2023)
- Using behavioral AI to squash payroll diversion (December 2023)
- Multifactor authentication manipulation (January 2024)
- Preventing supply chain compromise (February 2024)
- Detecting multilayered malicious QR code attacks (March 2024)
- Defeating malicious application creation attacks (April 2024)
- Stopping supply chain impersonation attacks (May 2024)
- CEO impersonation attacks (June 2024)
- DarkGate malware (July 2024)
- Credential Phishing Attack Targeting User Location Data (August 2024)
- Preventing Vendor Impersonation Scams (September 2024)
- SocGholish Haunts the Healthcare Industry (October 2024)
- Preventing Vendor Email Compromise in the Public Sector (November 2024)
- How Proofpoint Stopped a Dropbox Phishing Scam (December 2024)

