QR codes are a part of our everyday lives. They appear in everything from restaurant menus to payment portals. We can use them to quickly access information or perform tasks with a simple scan from our smartphones. However, the ubiquity and convenience of QR codes have also made them an attractive tool for attackers. These seemingly innocuous squares have become a Trojan horse for phishing schemes.
In December 2023, Proofpoint launched new in-line threat detection capabilities to stop QR code-based threats. We did this for several reasons. First, we recognized that these attacks are highly deceptive, and existing technologies could not analyze embedded URLs with accuracy. We also understood it was highly likely that users would fall victim to these attacks, as external survey data indicated over 80% of users believe that QR codes are safe.
Additionally, our own research showed that QR code attacks had already hit the mainstream. Now, we see daily QR code attack spikes reaching into the tens of thousands. So, our customers must stay vigilant about this threat.
To help in that effort, Proofpoint now offers QR code phishing simulations through Proofpoint Security Awareness. You can use them to help your users learn how to recognize and proactively report real QR code phishing attempts.
In this post, we will cover the basics of our simulations, and how they serve as a key pillar of our human-centric security strategy. But first, let’s examine how QR code phishing works.
The sequence of events in a QR code attack
In QR code phishing, an attacker will disguise malicious URLs within a QR code and embed the QR code into an email. The email is socially engineered to convince the victim to scan the code. After the code is scanned, the victim is redirected to a fraudulent website that is designed to steal sensitive data like login credentials, credit card numbers or personal data.
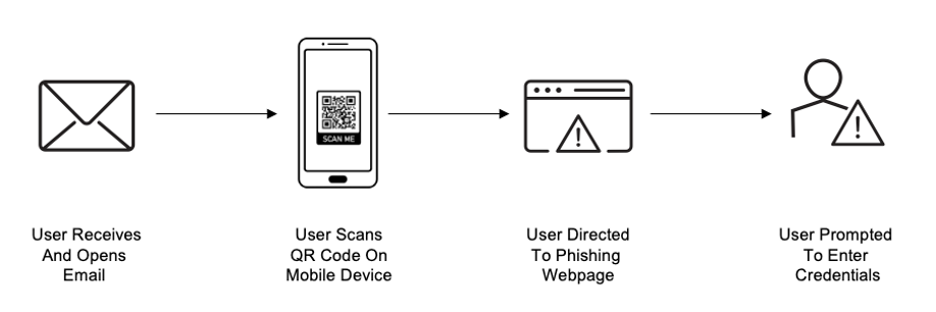
Overview of a QR code attack sequence.
What makes malicious QR codes so hard to detect is that attackers are intentionally combining evasion tactics with malicious QR codes to evade email gateways. For example, in a recent QR code attack, threat actors hid malicious QR codes within a PDF attachment. Further, the redirected URL used evasion tactics like adding a Cloudflare CAPTCHA to appear legitimate. Threat actors know that if successfully delivered to their victim it can lead to a successful compromise and they are motivated to continue investing in evasion.
The solution: QR code phishing simulation
The risk of user exposure to a QR code phishing attack is high, which is why it’s so important to educate your users about this threat. Here is where our QR code phishing simulation can help.
At its core, the simulation works by using email templates that are derived from real-world attacks. Administrators can use the prebuilt templates to launch simulation campaigns that test how employees might react to a QR code attack.
These simulations give users firsthand experience in how to identify, avoid and report these threats. This exercise also helps administrators understand their users’ vulnerabilities so that they can develop tailored educational plans.
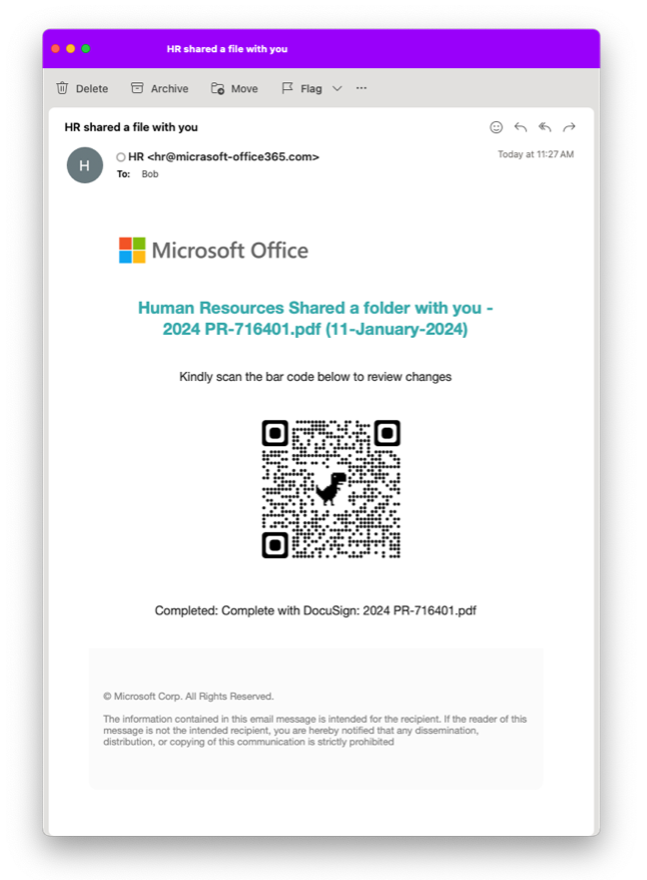
A sample of a QR Code Phishing Simulation template from Proofpoint.
To help hone a user’s knowledge and skills, the prebuilt templates are automatically categorized based on their difficulty level using our Leveled Phishing capability. Proofpoint is the first and only security awareness provider to combine machine learning and NIST Phish Scale research to automatically categorize the level of difficulty of our phishing simulation templates.
Leveled Phishing ensures that administrators can objectively challenge a user’s understanding of the threat. As a user’s knowledge improves with each simulation, the administrator can continue to challenge that user by launching more, and more difficult, simulations.
If the user fails a simulation, “Teachable Moments” provides them with educational tips on why the simulation was a threat, and how they can avoid the threat in the future.
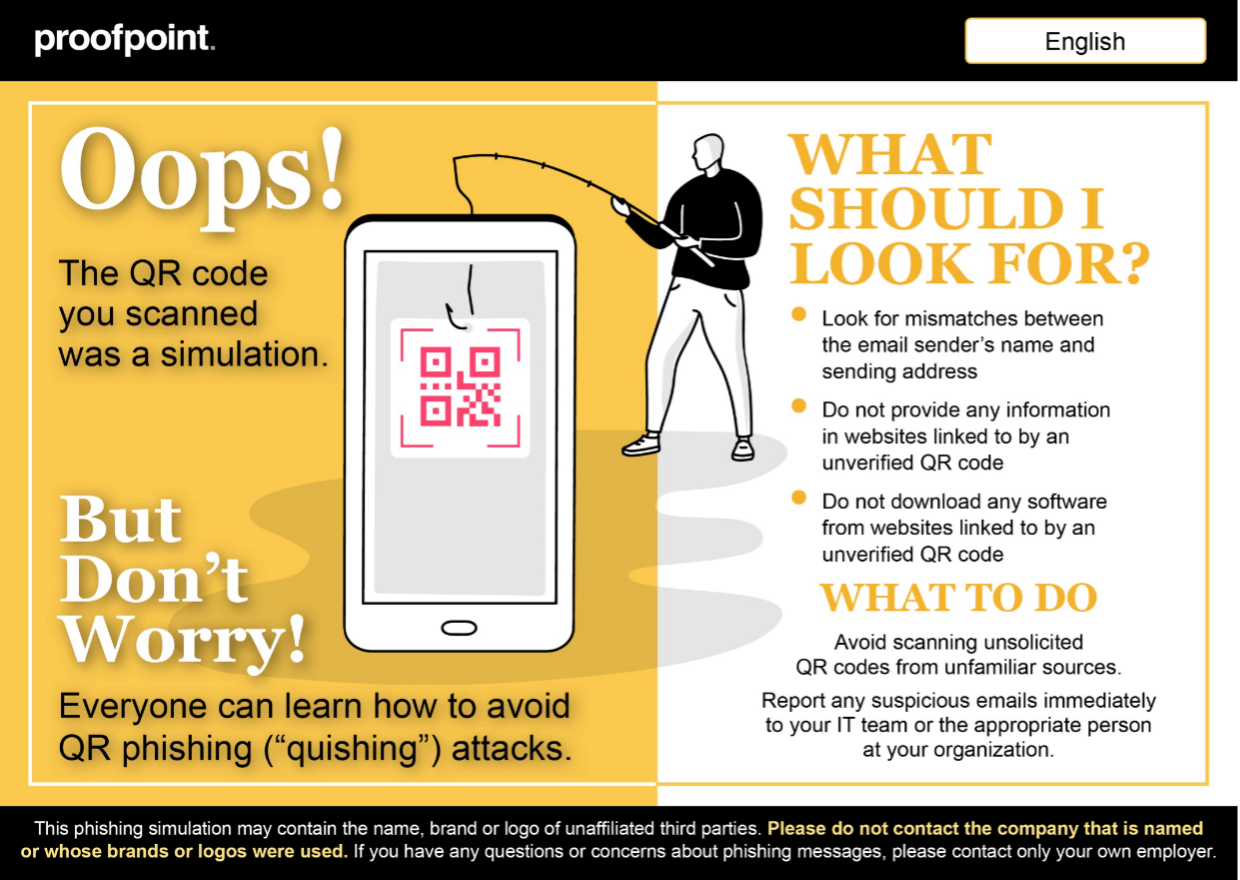
Sample of a “Teachable Moment” from Proofpoint.
The combination of QR Code simulations with just-in-time education can help to:
- Improve user comprehension
- Maximize user engagement
- Drive a positive change in user behavior
How these simulations complement our human-centric security strategy
The risk of QR code phishing attacks is constant. To protect your people, you must take a multilayered approach that combines user education with threat protection.
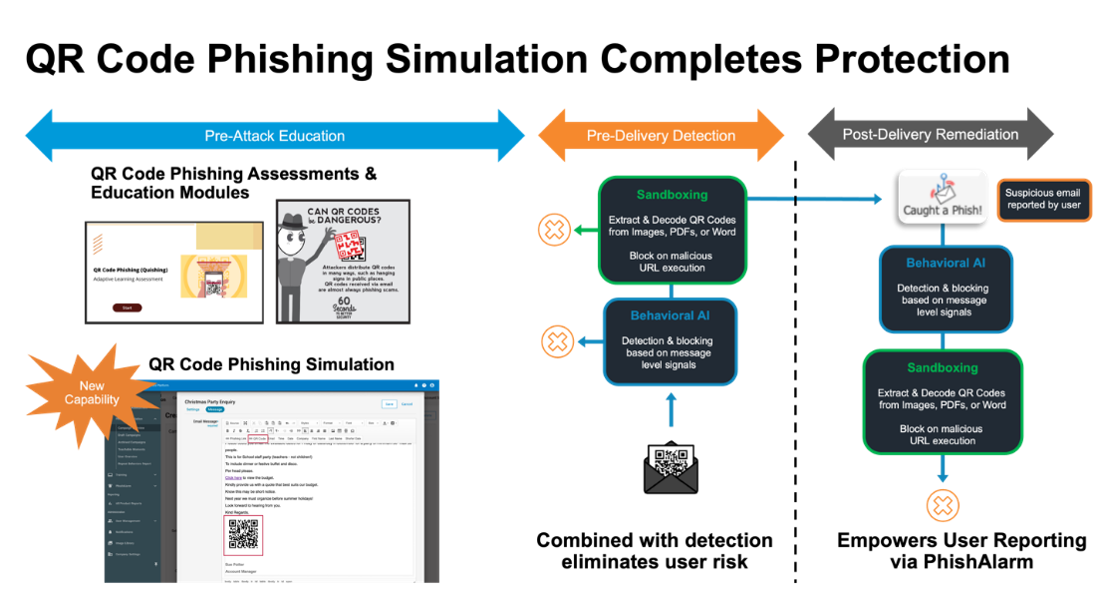
Proofpoint offers complete protection against QR code phishing.
Pre-attack education
If users are to avoid falling for an attack, they must receive training before an attack happens. The curriculum must include engaging content, knowledge assessments and phishing simulations.
Traditional security awareness programs often focus on video-based training that only discusses theoretical concepts. However, the Proofpoint QR code phishing simulation takes this a step further. It provides practical, hands-on training experiences based on QR code threats active in the wild.
Along with QR code-specific educational modules and assessments, our comprehensive approach can reinforce key concepts and teach your users how to recognize and proactively respond to QR code phishing attempts.
Predelivery detection
Security education is critical to building awareness of threats and user resilience. However, user error is always a risk. So, it is equally important to have a threat protection solution that can prevent an attack from ever reaching a user’s inbox.
Enter predelivery QR code detection capabilities from Proofpoint, which combine behavioral artificial intelligence and sandboxing technologies. By scanning QR codes at the point of entry, you can identify and block malicious URLs before your users can access them. As you eliminate QR code phishing attacks, you can reduce user exposure. Your users need only worry about the one or two malicious emails that might find their way to their inbox.
Post-delivery detection and remediation
If you equip your people with the right knowledge, you will empower them to become cybersecurity heroes for your company. In cases where QR code threats may get through, the training that you have provided will spur your users to move fast to report malicious messages.
When they use a tool like PhishAlarm to report a suspicious message, post-delivery remediation capabilities from Proofpoint will automatically analyze the message. As with our predelivery capabilities, we can scan and parse QR codes in attached PDFs and Word documents, as well as images from within the email using technologies like optical character recognition (OCR). If an email is found to be malicious, we can automatically condemn and remove it from all users’ inboxes across your business.
Get human-centric security with Proofpoint
QR code phishing is a significant and evolving threat to businesses of all sizes. And as the use of QR codes continues to spread, cybercriminals are likely to keep using them as tools to conduct phishing attacks. However, if your business adopts a comprehensive security strategy that integrates security education and threat protection, you can mitigate the risks associated with QR code phishing—and make your users more resilient against these attacks.
To learn more about our human-centric security approach to preventing QR code phishing, reach out to Proofpoint today.

