The days of a one-size fits all security awareness program are over. The State of the Phish report from Proofpoint notes that over 98% of businesses have a security awareness program. Yet a staggering 68% of users say they take risky actions despite knowing the risks.
These statistics underscore the frustrations that we hear from prospective clients every day. They tell us that while they run a continuous educational program, they struggle to achieve the desired behavior improvements among their users. Some of the key challenges they face are:
- Not knowing who represents the greatest risk to the organization
- Not knowing what policies, threats and vulnerabilities to educate users about at any given moment
- Not being able to keep a program agile without exhausting resources, constantly updating user groups or continually tailoring curriculums
These issues highlight the critical need to go beyond traditional security awareness and think holistically to build a human risk management program.
A good place to start is focusing on highly targeted user groups. It’s these users who are often the ones responsible for most of the security issues within a business. When you can tailor education to the specific needs of these users, you can mitigate individual vulnerabilities. You can also fortify your entire defense against potential attacks.
A new workflow from Proofpoint focuses on these users to produce exponentially positive results in helping you reduce overall risk. In this blog, we’ll explore why focusing on human risk management is so important. And we’ll explain how Proofpoint can help you do just that.
What is human risk management?
Human risk management builds on existing security best practices to automate cyberattack prevention and response. What makes it different is that it places people at the center. Fundamental to a human risk management solution is an ability to ingest user event and identity activity across multiple security tools within a given environment. The solution will track:
- Attack risk. The likelihood a user will be attacked
- Vulnerability risk. The likelihood that the attack may be successful
- Privilege risk. The damage that a successful attack may cause the organization
Then it quantifies an overall risk score for each individual. With this insight, companies and their security teams can:
- Gain visibility into which individuals or groups are prime targets and prioritize strategies to best protect them
- Intervene with technical controls to immediately prevent a risky action or provide contextual nudges that advise users about their risks and how to avoid them
- Automatically enroll risky users into tailored education curriculums, which empowers them to protect themselves and the company against future cyberattacks
- Easily track improvements in user behaviors and foster a positive security culture
These are the issues that the new Adaptive Threat and User-Risk Response Workflow within Proofpoint Security Awareness is designed to address. In short, this new workflow lets you take advantage of everything that is great about Proofpoint.
Our Adaptive Threat and User-Risk Response Workflow
The new workflow integrates three core capabilities. It enables you to:
- Dynamically create and manage user groups based on the user risk profiles and groups derived from Proofpoint Nexus People Risk Explorer (NPRE) and Proofpoint Targeted Attack Protection (TAP) using Adaptive Groups
- Create a threat-driven educational curriculum based on the defined Threat Families tracked by our own Threat Research and reported via TAP
- Build an Adaptive Assignment to auto-enroll new users into the curriculum whenever a new user qualifies for the previously created Adaptive Group
This adaptive learning approach prioritizes education for highly targeted groups. It helps to drive maximum user engagement, too, by enabling administrators to tailor the curriculum to the threats and risks that are most relevant to those users.
It does all of this by quantifying threat and user risks—and giving you granular visibility into them. You can use these insights to tailor education for your highly targeted groups. Here’s how.
Quantifying threat and user risk
Our user risk groups and profiles are at the heart of the new workflow. They include the Imminent Target and Very Attacked People™ groups that are available through NPRE and TAP.
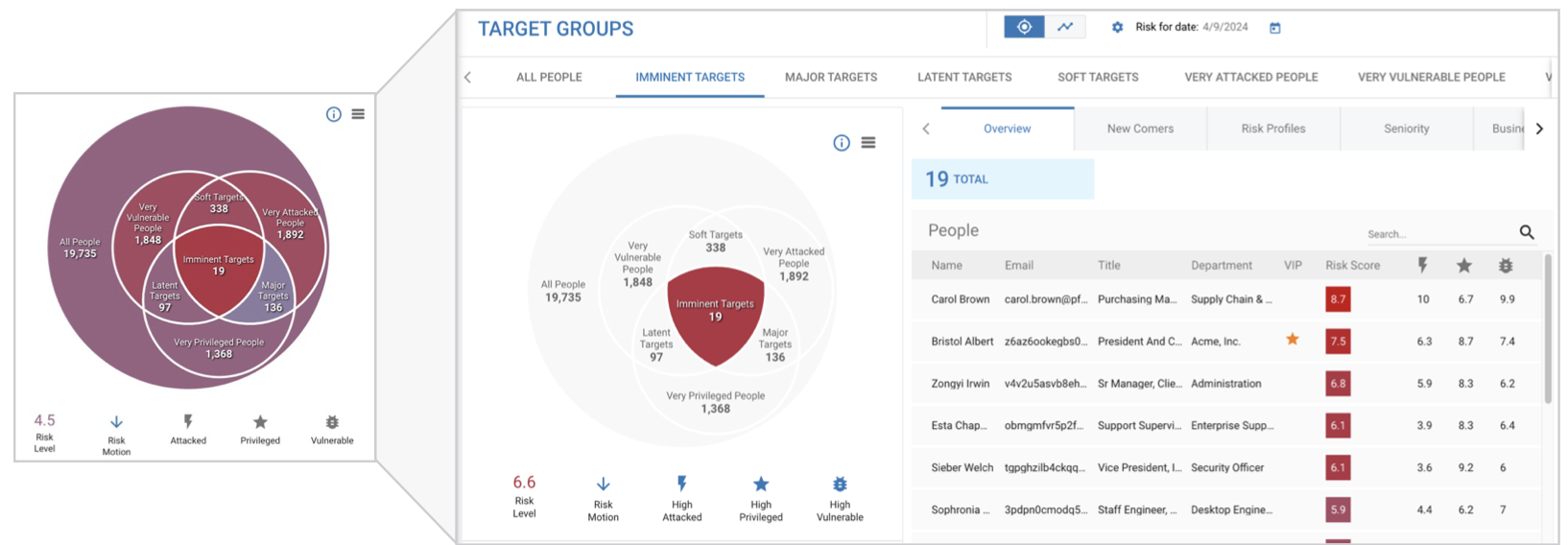
NPRE User Risk Groups example.
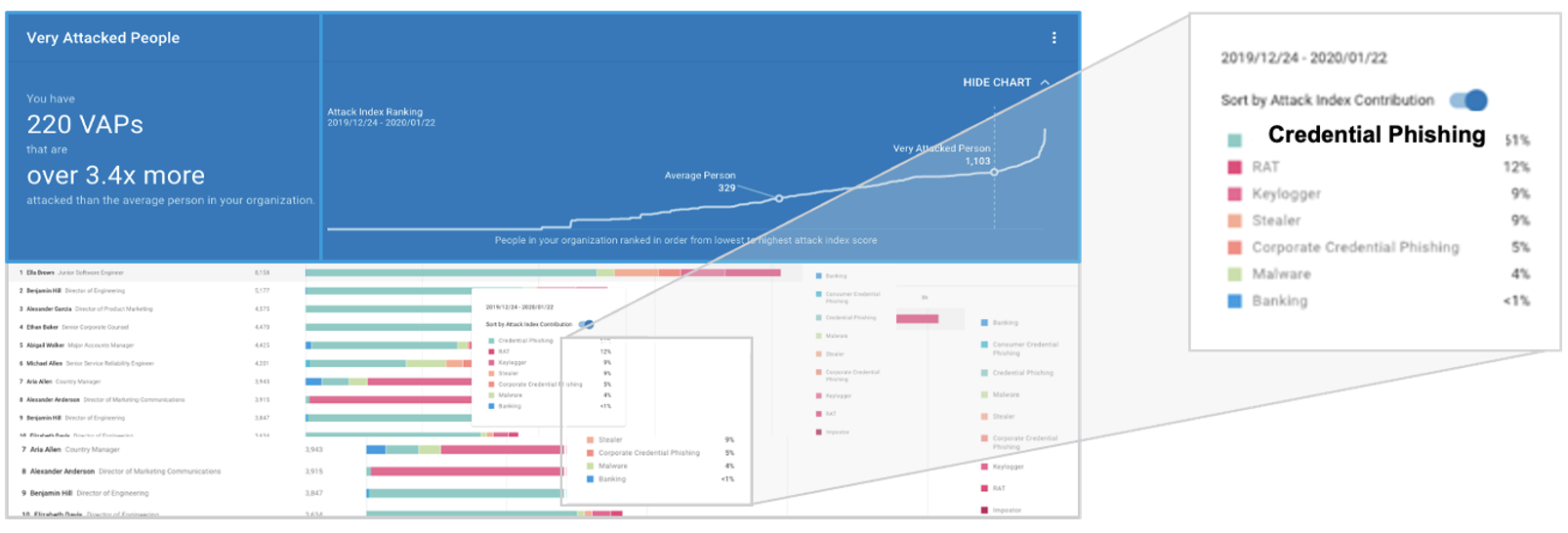
Very Attacked People™ with Threat Family example.
NPRE and TAP integrate multiple factors, like the following.
Attack Risk and Attack Index
These metrics assess the probability that a user group will be targeted by a cyberattack. The factors that contribute to the risk profile include but are not limited to:
- Message attack volume
- Type of attack
- Threat actor sophistication
- Attack diversity
- Spread and focus of attack targeting
Vulnerability Risk
This metric is used to evaluate the likelihood that an attack on a user would be successful. It considers the following information about the user and group:
- Security education participation
- Phishing tests performance
- Third-party app authentication requests
- Shadow IT usage
- User location inconsistencies
- URL click behavior
- Distribution list member attributes
- Compromised cloud account
- Insider risk alerts
- Risky handling of data
Privilege Risk
This metric assesses the potential damage that a successful attack could inflict. It considers user characteristics such as the following.
- User directory department/group/individual identity privilege
- Customer-defined privilege groups
- Privileged Identities (like domain administrators)
- Users with high-risk attack paths to tier zero entitlements (“crown jewel” assets)
By analyzing these factors, companies can prioritize their educational and security control strategies toward the individuals and groups that represent the highest risk.
Tailoring education for high-risk groups
The visibility that NPRE and TAP provide allows administrators to tailor education for a target group. Admins can provide a curriculum that is dedicated to the vulnerabilities or threats that the group is most susceptible to.
For example, one high-risk group that you can tailor education for is the “Top Clicker” risk group. Within that group, admins have visibility into the most common threats that are used to target the group such as “Ad-Fraud” or “Banking Trojans.”
Using this information and the Proofpoint Security Awareness integration, administrators can:
1. Build an Adaptive Group within Proofpoint Security Awareness. This group directly connects with the user risk group “Top Clicker” and the top threats that users are being targeted with, like "Ad-Fraud,” “Banking” and “Backdoor.”
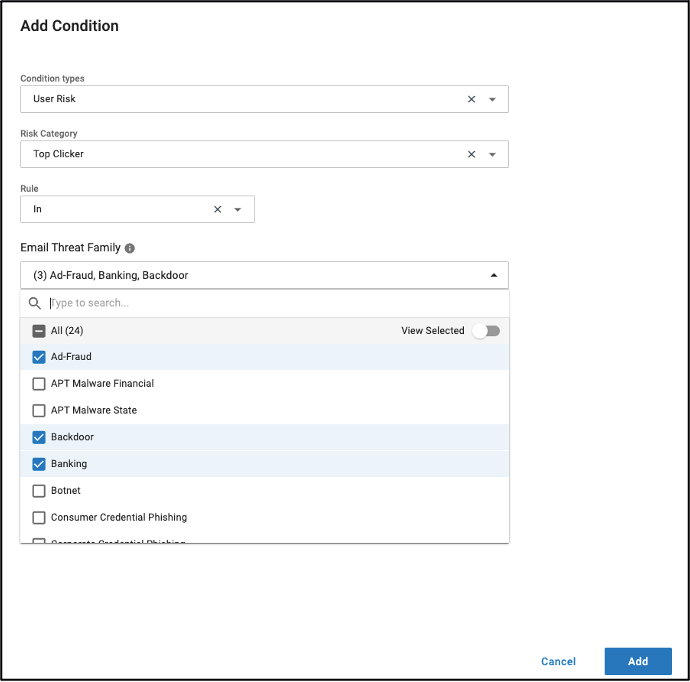
The configuration of the Adaptive Group with “User Risk” and “Threat Family” conditions.
2. Easily discover content. The Content Library includes a prebuilt search filter that is based on the Threat Families that TAP tracks.
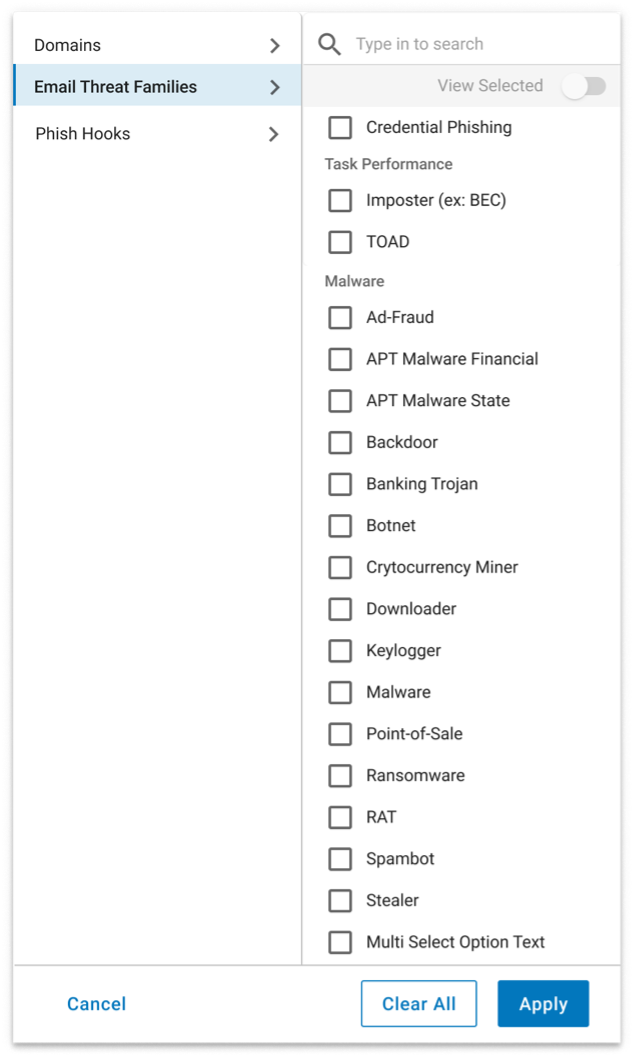
An example of the Content Library search filter for “Threat Families.”
3. Quickly create an Assignment. With the click of the button, you can align specific educational modules and assessments associated with these threats.
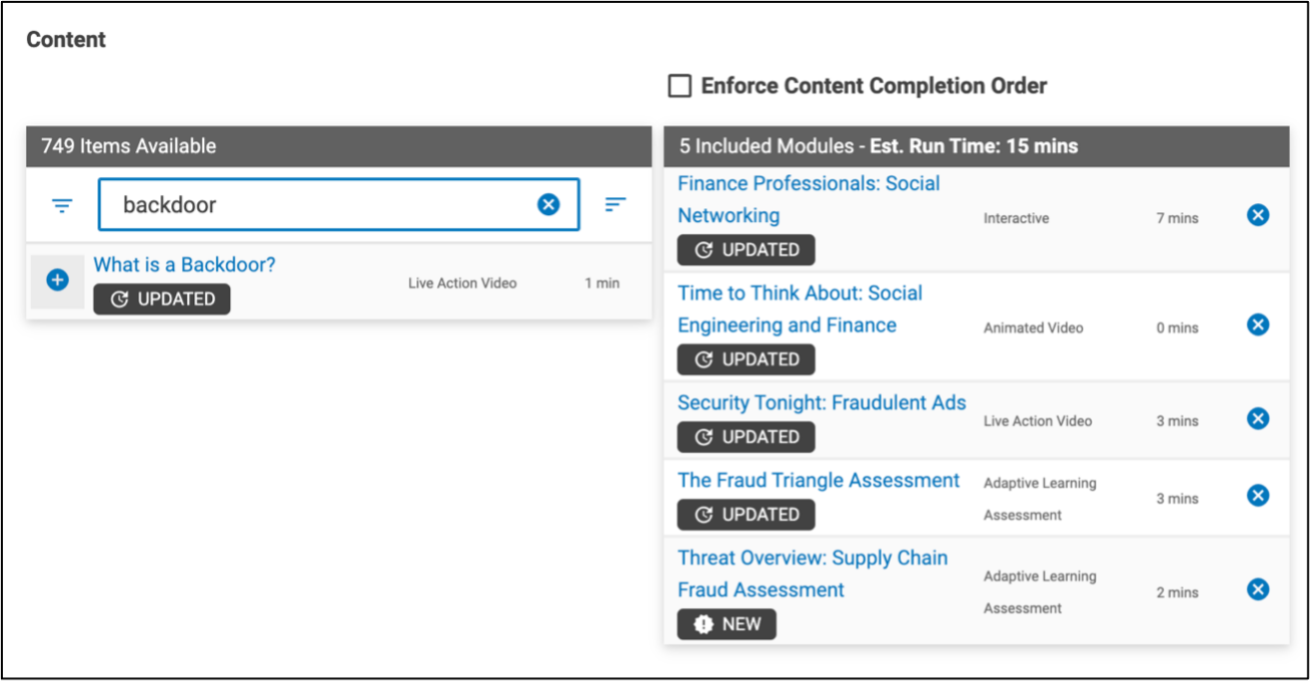
An overview of building an assignment.
4. Enforce auto-enrollment for new group members. That means anyone who becomes a “Top Clicker” and has been targeted by “Ad-Fraud,” “Banking” and “Backdoor” threats is automatically enrolled into the Assignment that was created previously.
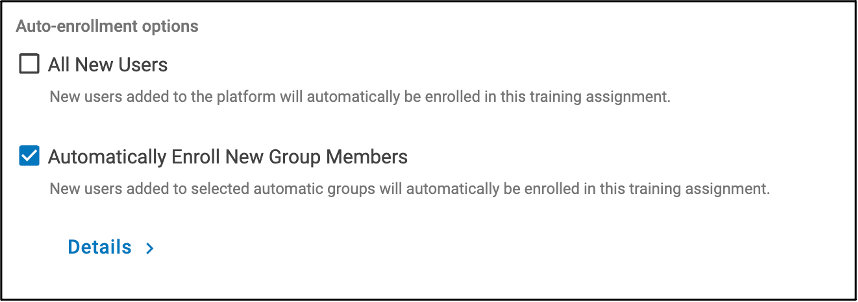
The option to auto-enroll new users into the Assignment.
Benefits of this targeted approach
The Adaptive Threat and User-Risk Response Workflow is a game changer. It allows you to:
- Prioritize resources. You can allocate your training resources more effectively when you focus on the most vulnerable groups first.
- Maximize engagement and competency. Users who receive the most relevant education are more knowledgeable and competent when it comes to identifying threats.
- Promote a proactive defense mindset. When your users are empowered with education, they’re more likely to report suspicious emails and activities rather than just ignore them.
- Achieve quantifiable risk reduction. By targeting high-risk groups, your business will greatly reduce the likelihood of successful attacks.
A significant advancement in the fight against human risk
With Proofpoint Security Awareness Adaptive Threat and User-Risk Response Workflow, you get detailed visibility into your company’s highly targeted user groups. Plus, you can deliver tailored education to them based on comprehensive their risk scores as well as the types of threat that are targeting them. This gives you the opportunity to break through the one-size-fits-all security awareness model—and build a human risk management program that works.
Proofpoint Security Awareness can help you stay ahead of threats and fortify your human firewall. Contact us today to learn more about our solutions.
