Over the past weeks, Proofpoint researchers have been monitoring an ongoing cloud account takeover campaign impacting dozens of Microsoft Azure environments and compromising hundreds of user accounts, including senior executives. This post serves as a community warning regarding the attack and offers suggestions that affected organizations can implement to protect themselves from it.
What are we seeing?
In late November 2023, Proofpoint researchers detected a new malicious campaign, integrating credential phishing and cloud account takeover (ATO) techniques. As part of this campaign, which is still active, threat actors target users with individualized phishing lures within shared documents. For example, some weaponized documents include embedded links to “View document” which, in turn, redirect users to a malicious phishing webpage upon clicking the URL.
Threat actors seemingly direct their focus toward a wide range of individuals holding diverse titles across different organizations, impacting hundreds of users globally. The affected user base encompasses a wide spectrum of positions, with frequent targets including Sales Directors, Account Managers, and Finance Managers. Individuals holding executive positions such as “Vice President, Operations”, "Chief Financial Officer & Treasurer" and "President & CEO" were also among those targeted. The varied selection of targeted roles indicates a practical strategy by threat actors, aiming to compromise accounts with various levels of access to valuable resources and responsibilities across organizational functions.
Following the attack’s behavioral patterns and techniques, our threat analysts identified specific indicators of compromise (IOCs) associated with this campaign. Namely, the use of a specific Linux user-agent utilized by attackers during the access phase of the attack chain:
Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Attackers predominantly utilize this user-agent to access the 'OfficeHome' sign-in application along with unauthorized access to additional native Microsoft365 apps, such as:
- ‘Office365 Shell WCSS-Client’ (indicative of browser access to Office365 applications)
- ‘Office 365 Exchange Online’ (indicative of post-compromise mailbox abuse, data exfiltration and email threats proliferation)
- ‘My Signins’ (used by attackers for MFA manipulation; for more info about this technique, see our recent Cybersecurity Stop of the Month blog)
- ‘My Apps’
- ‘My Profile’
Post compromise risks
Successful initial access often leads to a sequence of unauthorized post-compromise activities, including:
-
MFA manipulation. Attackers register their own MFA methods to maintain persistent access. We have observed attackers choosing different authentication methods, including the registration of alternative phone numbers for authentication via SMS or phone call. However, in most MFA manipulation instances, attackers preferred to add an authenticator app with notification and code.
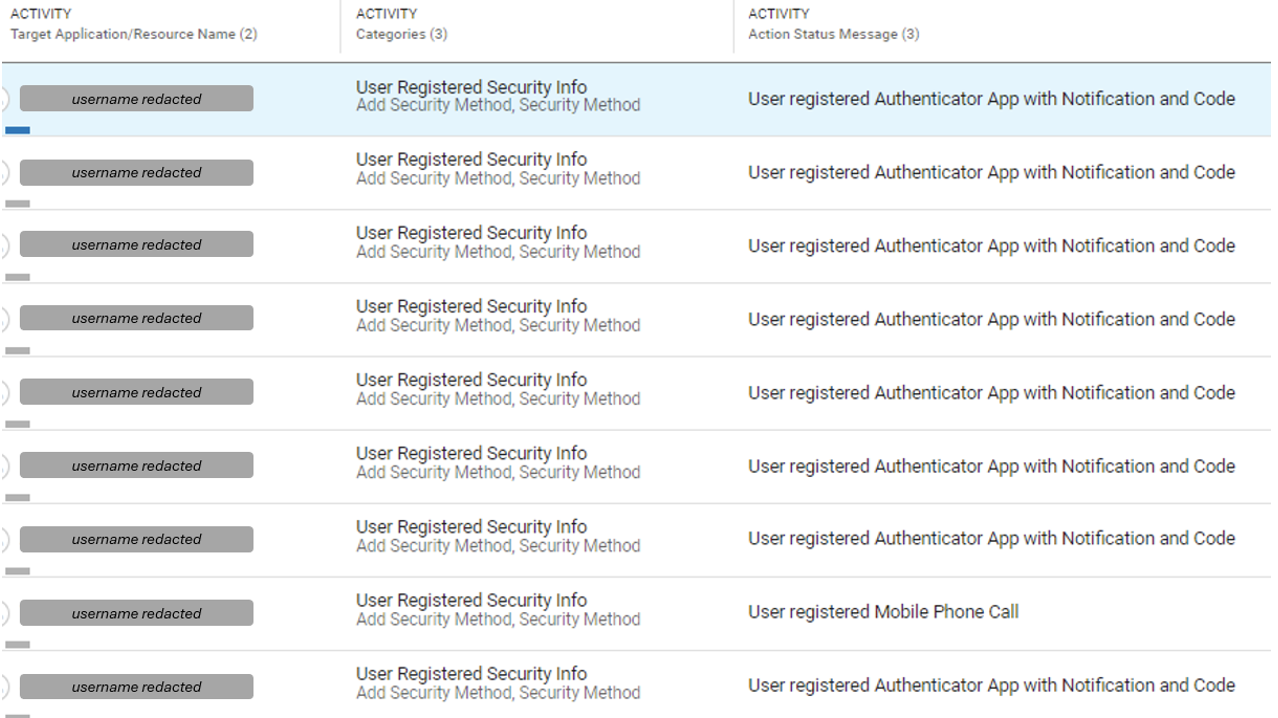
Examples of MFA manipulation events, executed by attackers in a compromised cloud tenant.
- Data exfiltration. Attackers access and download sensitive files, including financial assets, internal security protocols, and user credentials.
- Internal and external phishing. Mailbox access is leveraged to conduct lateral movement within impacted organizations and to target specific user accounts with personalized phishing threats.
- Financial fraud. In an effort to perpetrate financial fraud, internal email messages are dispatched to target Human Resources and Financial departments within affected organizations.
- Mailbox rules. Attackers create dedicated obfuscation rules, intended to cover their tracks and erase all evidence of malicious activity from victims’ mailboxes.
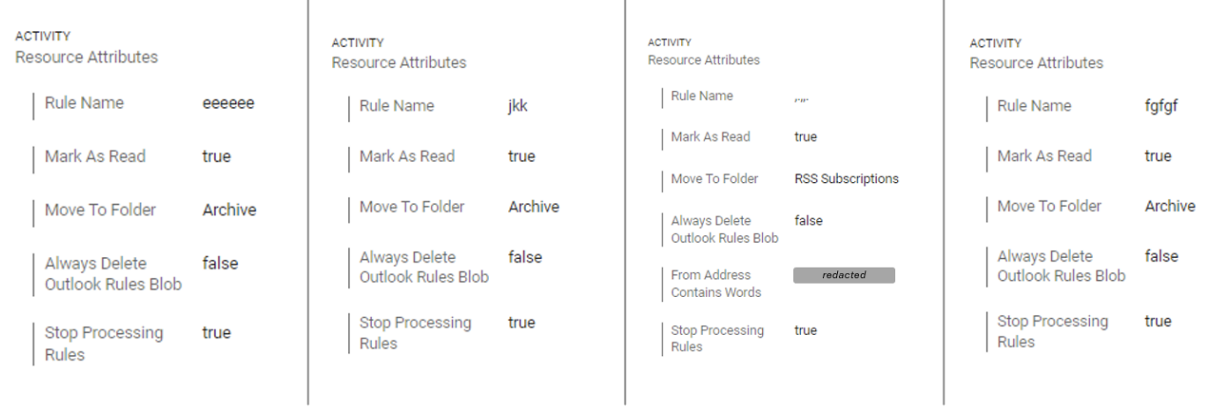
Examples of obfuscation mailbox rules created by attackers following successful account takeover.
Operational infrastructure
Our forensic analysis of the attack has surfaced several proxies, data hosting services and hijacked domains, constituting the attackers’ operational infrastructure. Attackers were observed employing proxy services to align the apparent geographical origin of unauthorized activities with that of targeted victims, evading geo-fencing policies. In addition, the usage of frequently alternating proxy services allows threat actors to mask their true location and creates an additional challenge for defenders seeking to block malicious activity.
Beyond the use of proxy services, we have seen attackers utilize certain local fixed-line ISPs, potentially exposing their geographical locations. Notable among these non-proxy sources are the Russia-based 'Selena Telecom LLC', and Nigerian providers 'Airtel Networks Limited' and 'MTN Nigeria Communication Limited.'
While Proofpoint has not currently attributed this campaign to any known threat actor, there is a possibility that Russian and Nigerian attackers may be involved, drawing parallels to previous cloud attacks.
Indicators of compromise
|
Indicator |
Type |
Description |
|
Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 |
User Agent |
User Agent involved in attack’s access phase |
|
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 |
User Agent |
User Agent involved in attack’s access and post-access phases |
|
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 |
User Agent |
User Agent involved in attack’s access and post-access phases |
|
sachacel[.]ru |
Domain |
Domain used for targeted phishing threats |
|
lobnya[.]com |
Domain |
Source domain used as malicious infrastructure |
|
makeapp[.]today |
Domain |
Source domain used as malicious infrastructure |
|
alexhost[.]com |
Domain |
Source domain used as malicious infrastructure |
|
mol[.]ru |
Domain |
Source domain used as malicious infrastructure |
|
smartape[.]net |
Domain |
Source domain used as malicious infrastructure |
|
acedatacenter[.]com |
Domain |
Source domain used as malicious infrastructure |
|
Sokolov Dmitry Nikolaevich |
ISP |
Source ISP used as malicious infrastructure |
|
Dom Tehniki Ltd |
ISP |
Source ISP used as malicious infrastructure |
|
Selena Telecom LLC |
ISP |
Source ISP used as malicious infrastructure |
Proofpoint’s Cloud Security Response Team continues to monitor this threat. Additional IOCs may be added based on subsequent discoveries.
Analyst note: The IOCs within this report were updated on Thursday 28th March 2024. Updates included the removal of the following domains: mtnonline.com and airtel.com, and therefore we do not advise any outright blocking of traffic or connections from these specific domains.
Recommendations
To bolster your organization's defense against this attack, consider the following measures:
- Monitor for the specific user agent string and source domains in your organization’s logs to detect and mitigate potential threats.
- Enforce immediate change of credentials for compromised and targeted users, and enforce periodic password change for all users.
- Identify account takeover (ATO) and potential unauthorized access to sensitive resources in your cloud environment. Security solutions should provide accurate and timely detection for both initial account compromise and post-compromise activities, including visibility into abused services and applications.
- Identify initial threat vectors, including email threats (e.g. phishing, malware, impersonation, etc.), brute-force attacks, and password spraying attempts.
- Employ auto-remediation policies to reduce attackers’ dwell time and minimize potential damages.
How Proofpoint can help
Proofpoint’s Targeted Attack Prevention Account Takeover (TAP ATO) solution provides robust detection and remediation capabilities for cloud account takeover and BEC incidents. Leveraging advanced threat intelligence, dynamic monitoring and adaptive AI, TAP ATO provides organizations with the tools to swiftly detect and respond to suspicious activities, thwart unauthorized access attempts, and proactively secure user-accounts within cloud environments. With its comprehensive features and user-centric approach, Proofpoint’s TAP ATO protects both users and data from a variety of cyber threats.
For further information, visit https://www.proofpoint.com/us/solutions/combat-email-and-cloud-threats or contact us.

