Introduction
In today's interconnected world, cloud computing has become the backbone of countless businesses. However, with this rise in cloud adoption, malicious actors have adapted their strategies to compromise sensitive data stored in cloud environments and propagate threats throughout supply chains. One prevalent method is the use of tools specifically designed to automate attacks against cloud accounts, resulting in account takeover (ATO) and business email compromise (BEC) incidents.
Keeping up with a tradition of trying to understand the attackers’ perspective, Proofpoint cloud threat researchers have obtained and analyzed various hacking tools used by threat actors. In this blog series, we'll showcase a few examples and explore the largely uncovered world of these tools, while examining their functionalities, the risks they pose, and how organizations can defend against them.
Understanding toolsets: basic concepts and terminology
Attack toolsets are purposefully crafted to enable, automate, and streamline cyber-attacks en masse. These toolsets exploit diverse weaknesses, from frequent misconfigurations to old authentication mechanisms, in order to gain access to selected resources.
Often, attack toolsets are designed with specific aims in mind. In recent years, cloud accounts have become prime targets. But getting your hands on effective tools is not so trivial. Some toolsets are only sold or circulated within restricted channels, such as closed Darknet hacking forums, while others (especially older versions) are publicly available online.
With a rising demand for hacking capabilities, hacking-as-a-service (HaaS) has become a prominent business model in today’s cyber threat landscape, providing convenient access to advanced hacking capabilities in exchange for financial gain. As such, it lowers entry barriers for cybercriminals, allowing them to execute attacks with minimal effort.
Regardless of their complexity, every attack tool aiming to compromise cloud accounts must utilize an initial threat vector to gain unauthorized access. Proofpoint's ongoing monitoring of the cloud threat landscape has led its researchers to categorize the majority of observed attacks into two primary threat vectors: brute-force attacks and precision attacks.
In terms of sheer volume, brute-force attacks, encompassing techniques such as password guessing and various other methods, continue to maintain their status as the most prevalent threat vector. Despite the statistical nature of these attacks and their reliance on a "spray and pray" approach, they remain a significant threat. According to our research, roughly 20% of all organizations targeted by brute-force attacks in 2023 experienced at least one successful account compromise instance.
The surprising effectiveness of brute-force methods, combined with their relative simplicity, makes this vector appealing not only to common cybercriminals, but also to sophisticated actors. In January 2024, Microsoft disclosed that it had fallen victim to a nation-state attack attributed to the Russian state-sponsored group APT29 (also known as TA421 and Midnight Blizzard).
According to Microsoft's announcement, the attackers employed password spraying to compromise a legacy, non-production test tenant account that lacked multifactor authentication (MFA). After gaining access, attackers were able to quickly leverage it and hijack additional assets, ultimately exfiltrating sensitive data from various resources. This incident emphasizes the potential risk that brute-force and password spraying attacks pose to inadequately protected cloud environments.
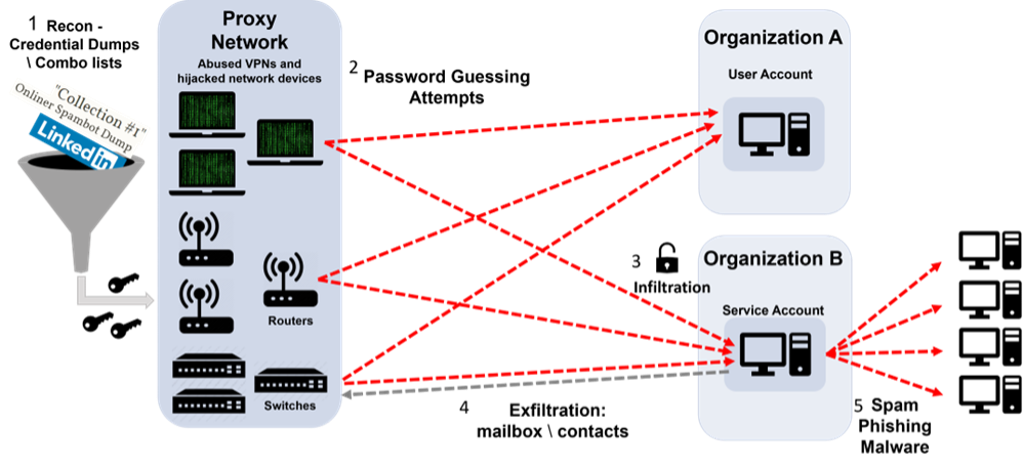
A brute-force attack kill chain, targeting cloud environments using leaked credentials and proxy networks.
Combo lists, proxy lists and basic authentication
Combo lists play a crucial role in facilitating systematic and targeted credential stuffing attacks. These lists, comprised of curated email address and password pairs, serve as the basic ammunition for most tools. Attackers leverage combo lists to automate the process of trying different combinations until a valid entry point is identified within a cloud environment.
In tandem with combo lists, proxy lists add to the stealth and anonymity of malicious sign-in attempts targeting cloud environments and user-accounts. Proxy lists enable threat actors to conceal their identity by routing traffic through a series of intermediary servers. This obfuscation makes it challenging to trace the origin of the attack, adding a layer of complexity to the detection process.
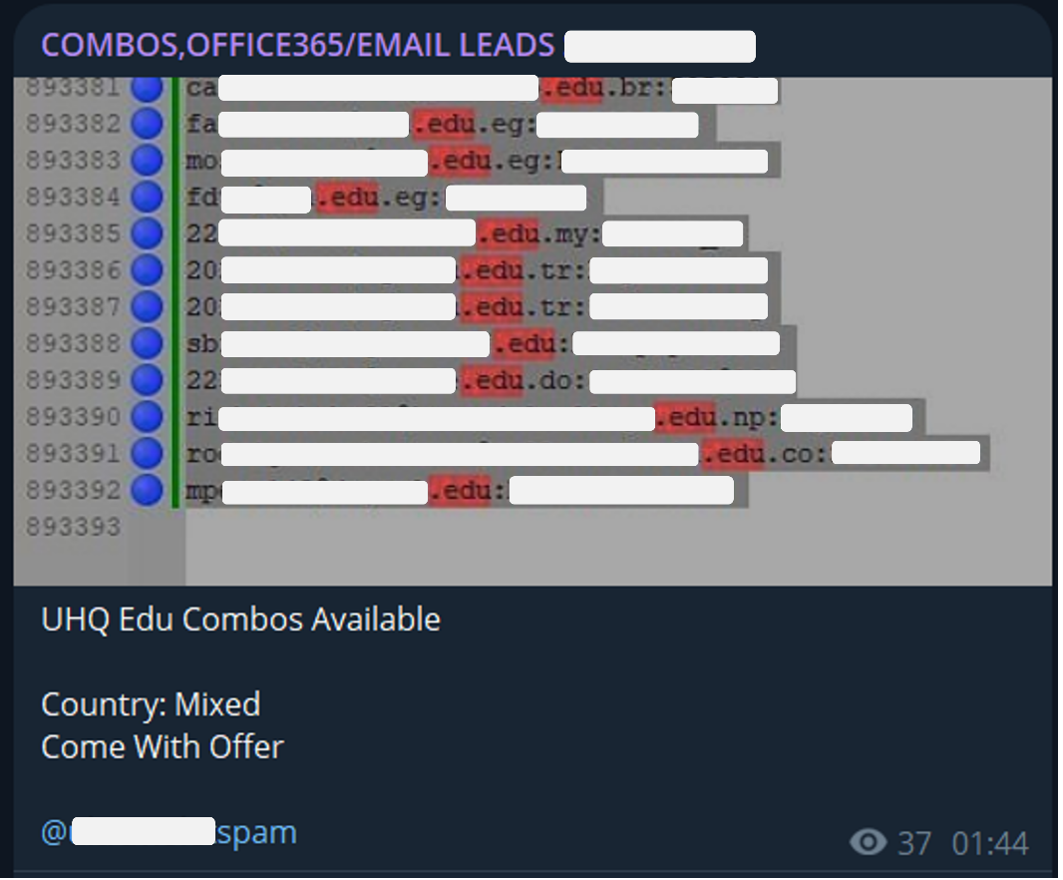
Educational institutions’ emails and credentials combinations, offered for sale on Telegram
Legacy authentication protocols (LAPs) or legacy email protocols (LEPs) refer to outdated communication protocols, such as IMAP or SMTP AUTH, used for retrieving emails from servers. These protocols lack advanced security features, making them highly susceptible to brute-force attacks.
Despite recent efforts to phase out basic authentication in favor of modern authentication methods, many organizations, including Microsoft, apparently still allow both active and dormant user-accounts, as well as service accounts, to authenticate using a simple username and password combination. This creates a significant attack surface that threat actors are quick to exploit. According to Proofpoint’s analysis, most brute-force attacks (namely password spraying and credential stuffing) continue to rely on basic authentication and legacy authentication protocols. Alternatively, users with modern authentication but lacking MFA deployment, can still be impacted by this vector.
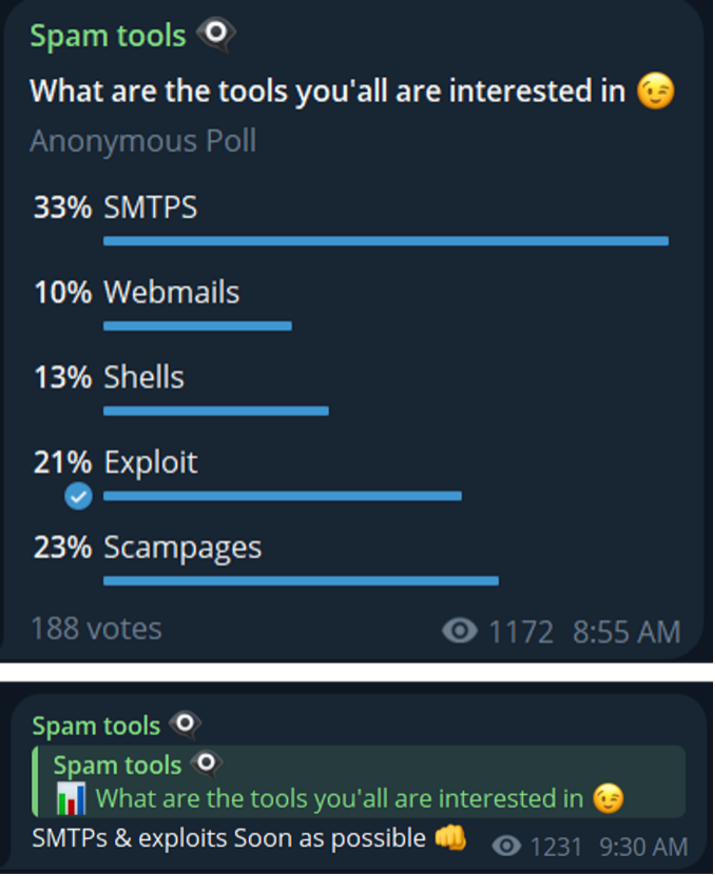
A recent poll conducted on a Telegram hacking channel, showing the popularity of SMTP-based tools.
Toolsets used to target cloud accounts
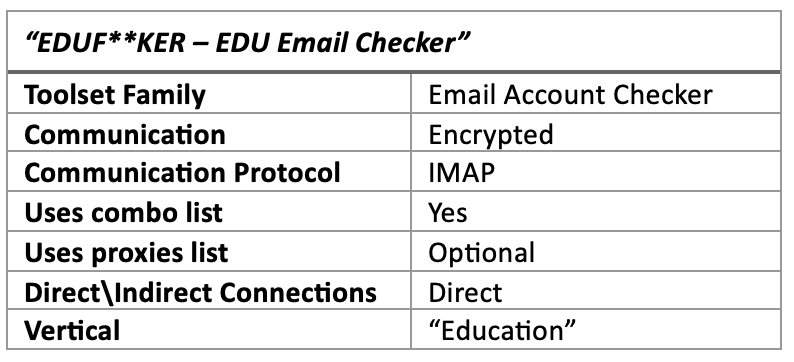
1. EduF**ker – EDU Email Checker
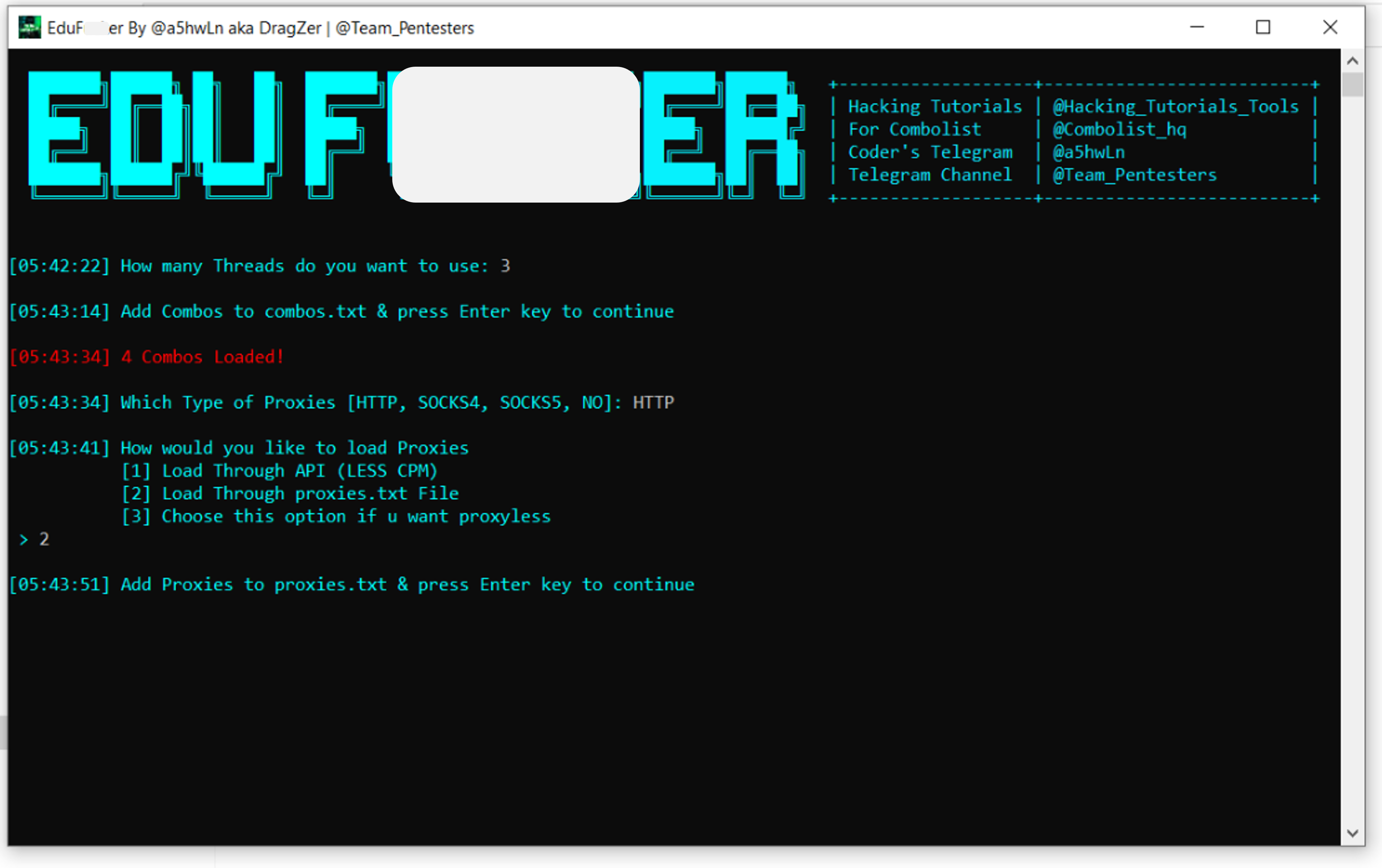
EduF**ker: main dashboard view.
In recent years, the education sector has emerged as one of the most susceptible verticals to cloud threats, drawing the attention of malicious actors, who frequently target educational institutions. According to Proofpoint’s data, approximately 80% of educational organizations suffered at least one successful account takeover in 2023. Out of all the attacked educational institutions, nearly 50% were compromised by various password-spraying campaigns and brute-force attacks.
Attackers have been observed targeting a broad spectrum of individuals, including students (from school children to college attendees and alumni), educators (e.g. teachers and professors), and professional staff members. Upon successfully compromising accounts, threat actors tend to utilize these hijacked accounts as launchpads for external attacks, predominantly spam and phishing campaigns.
Among the arsenal of tools aimed at breaching user-accounts, EduF**ker has emerged as a particularly interesting case.
Based on the tool’s obscene name, one might think that it is only capable of targeting educational institutions. However, this is only a marketing strategy, as the software enables attackers to target accounts across various sectors and industries indiscriminately.
Main features:
- Legacy email protocols. EduF**ker takes advantage of the widespread usage of basic authentication in the education sector. This tool uses IMAP-over-SSL (using TLS 1.2 and port 993) for its connection attempts.
- Combo list. EduF**ker requires a file including a “combo list” consisting of email addresses and credentials, which are needed to gain unauthorized access to email accounts.
- Proxies list. Attackers can choose to provide a list of proxies to be used by the tool. The inclusion of proxies enhances its stealth and anonymity, making it challenging to trace the origins of the attack.
The "EduF**ker - Edu Email Checker" tool demonstrates a level of sophistication that extends beyond its core functionalities. Some versions of this tool employ mechanisms meant to detect and hinder analysis attempts, particularly when executed within a virtual machine (VM).
The real concern lies not only in unauthorized access to vulnerable accounts, but in the subsequent use of hijacked users’ mailboxes to spread email-borne threats (such as phishing, malware and spam), or the exfiltration of sensitive data.
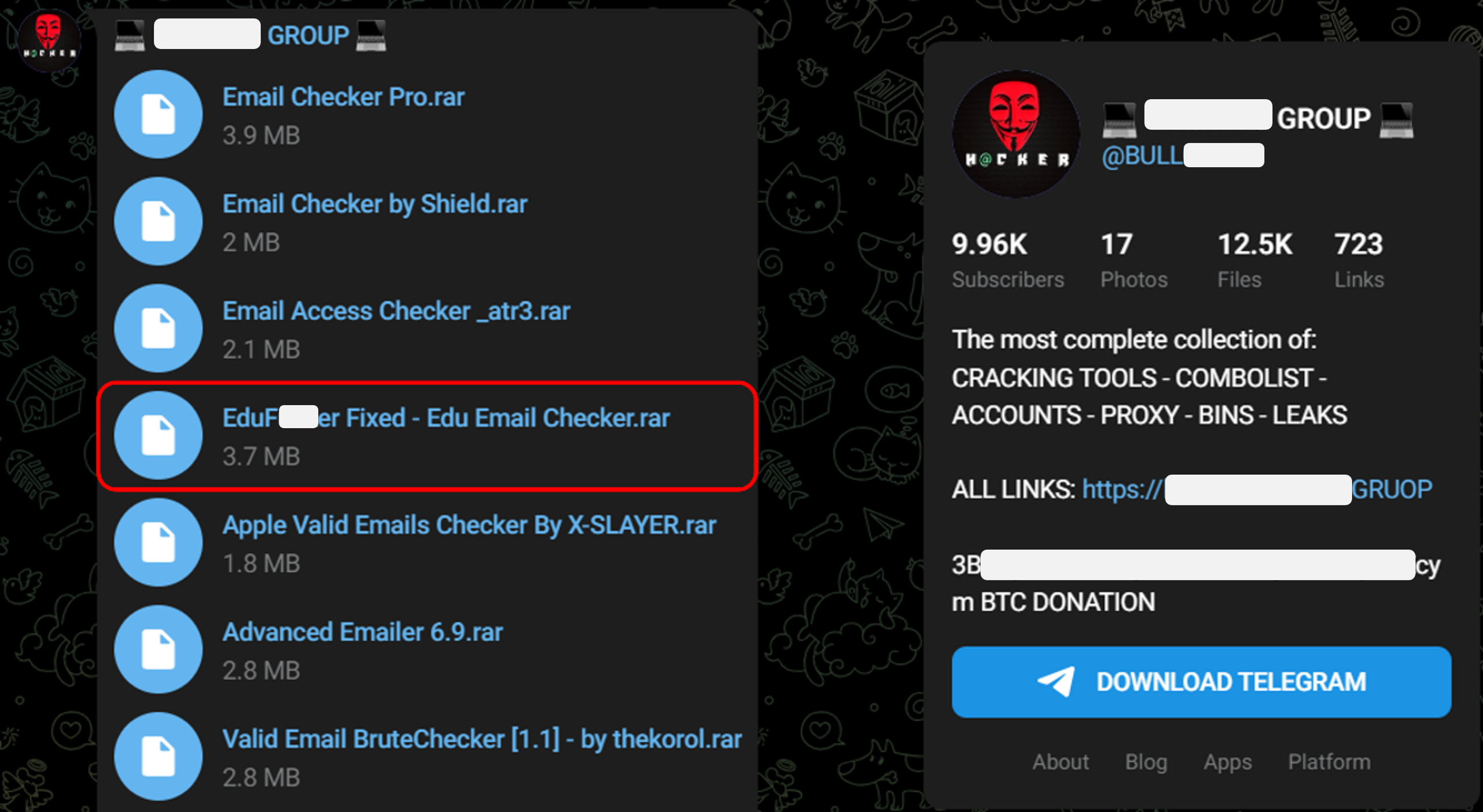
EduF**ker variant sold on a Telegram hacking channel.
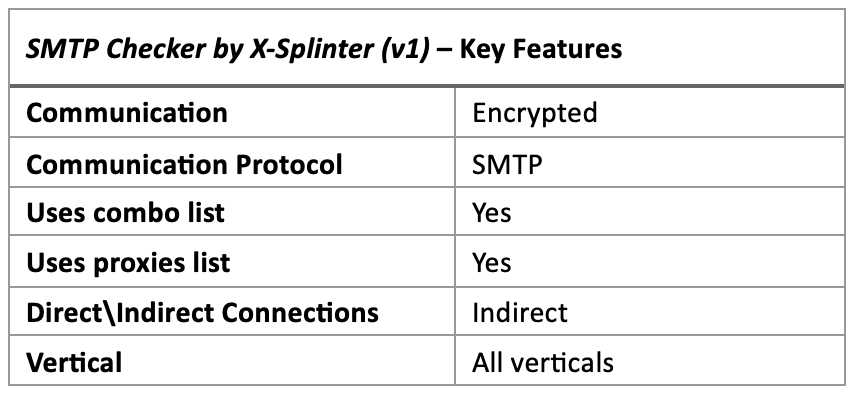
2. Smtp Checker by X-Splinter v1
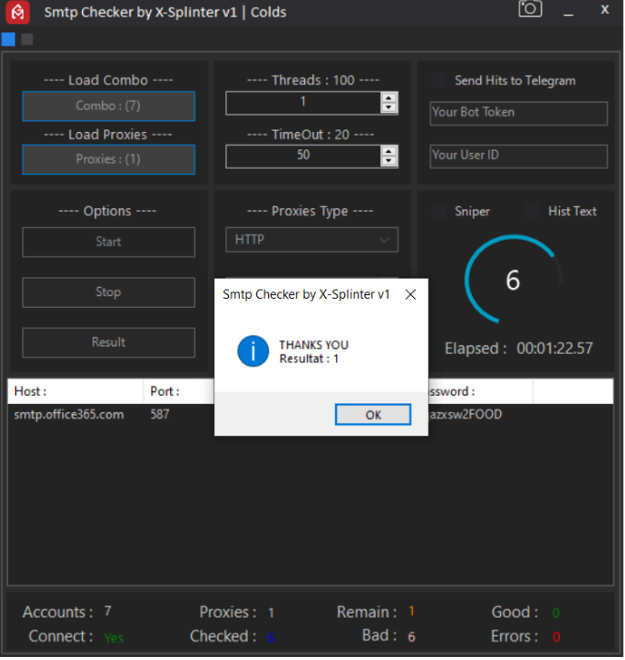
'Smtp Checker by X-Splinter v1’ run screen showing a successful authentication attempt.
The term “SMTP Checker” is used for various reconnaissance tools, benign or malicious. Bad actors commonly utilize these tools for reconnaissance, employing them to validate the authenticity of stolen or harvested credentials, before initiating the primary stage of an attack sequence.
One such tool, attributed to an actor named “X-Splinter”, stands out as quite popular amongst hackers. It is designed primarily for the purpose of accessing email accounts via the SMTP protocol. Utilizing TLS for secure encrypted communication, the tool’s ultimate output is a list of successfully cracked user-accounts.
Key features:
- Uses SMTP. The choice of using the SMTP protocol, as opposed to other legacy protocols (such as IMAP or POP3) suggests that this tool was designed to deal with the ongoing deprecation of old email protocols. In doing so, attackers essentially pivoted to a more stable protocol, guaranteeing operational continuity.
- GMass integration. Smtp Checker by X-Splinter v1 redirects connection request through GMass’s SMTP test tool. This free-to-use product allows users to easily validate access to any email account or SMTP server.
- Traffic is routed via GMass and results are presented to the attacker in the tool’s console.
- As can be seen after deployment, this SMTP Checker tool even uses the GMass logo as its icon, adding an extra layer of brand recognition.
- Alternating user-agents (UAs). SMTP Checker by X-Splinter v1 employs an effective obfuscation method. It uses a diverse range of user-agents (operating system and browser combinations), to decrease its chances of being blocked by static security solutions.
- Proofpoint researchers have discovered a pattern consisting primarily of Windows XP or Windows 10 systems combined with Chrome 41 or Chrome 94 (and their respective sub-versions).
- When targeting Microsoft365 user-accounts, this tool will create login events that appear under the 'Authenticated SMTP' client app, with the user-agent field displaying 'BAV2ROPC' (Basic Authentication Version 2 Resource Owner Password Credential). The displayed UA further conceals the original user-agents generated by the tool itself.
Like many other attack tools, Smtp Checker by X-Splinter v1 utilizes a 'combos.txt' file that includes a list of potential email and password pairs. However, unlike basic tool, it necessitates a proxy list to establish connections.
Overall, this specific ‘SMTP Checker' tool serves as a good example of an elevated level of adaptability and sophistication among attackers, distinguishing itself from Eduf**ker.
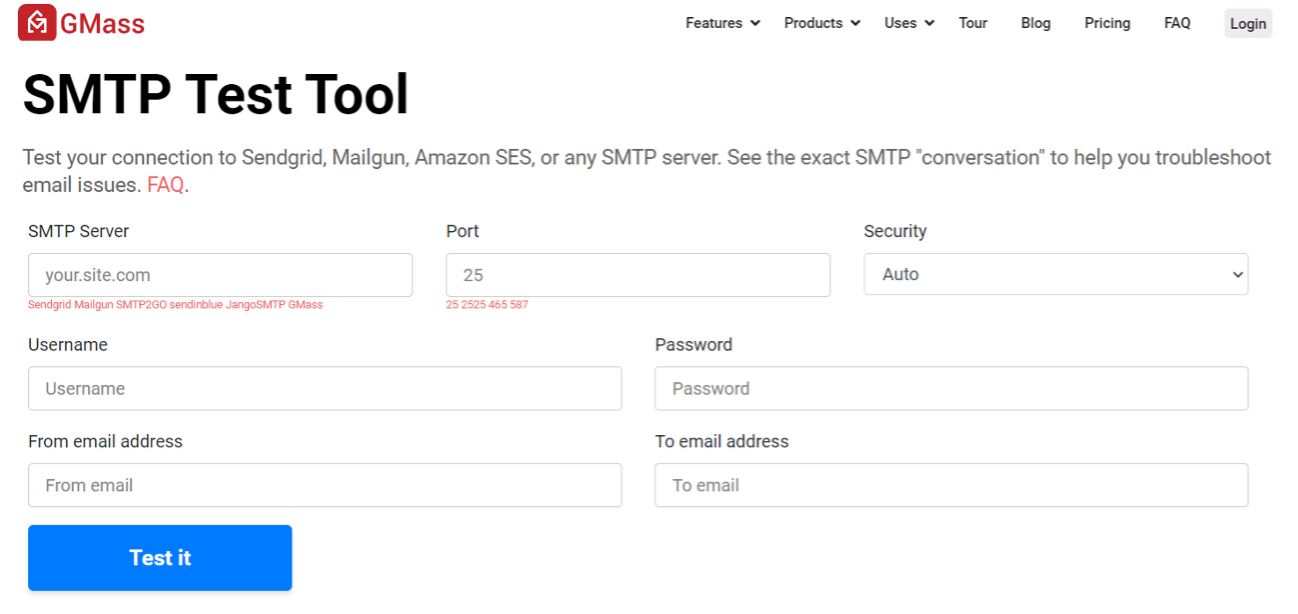
GMass's free SMTP Test Tool, used as a component in SMTP Checker tools.
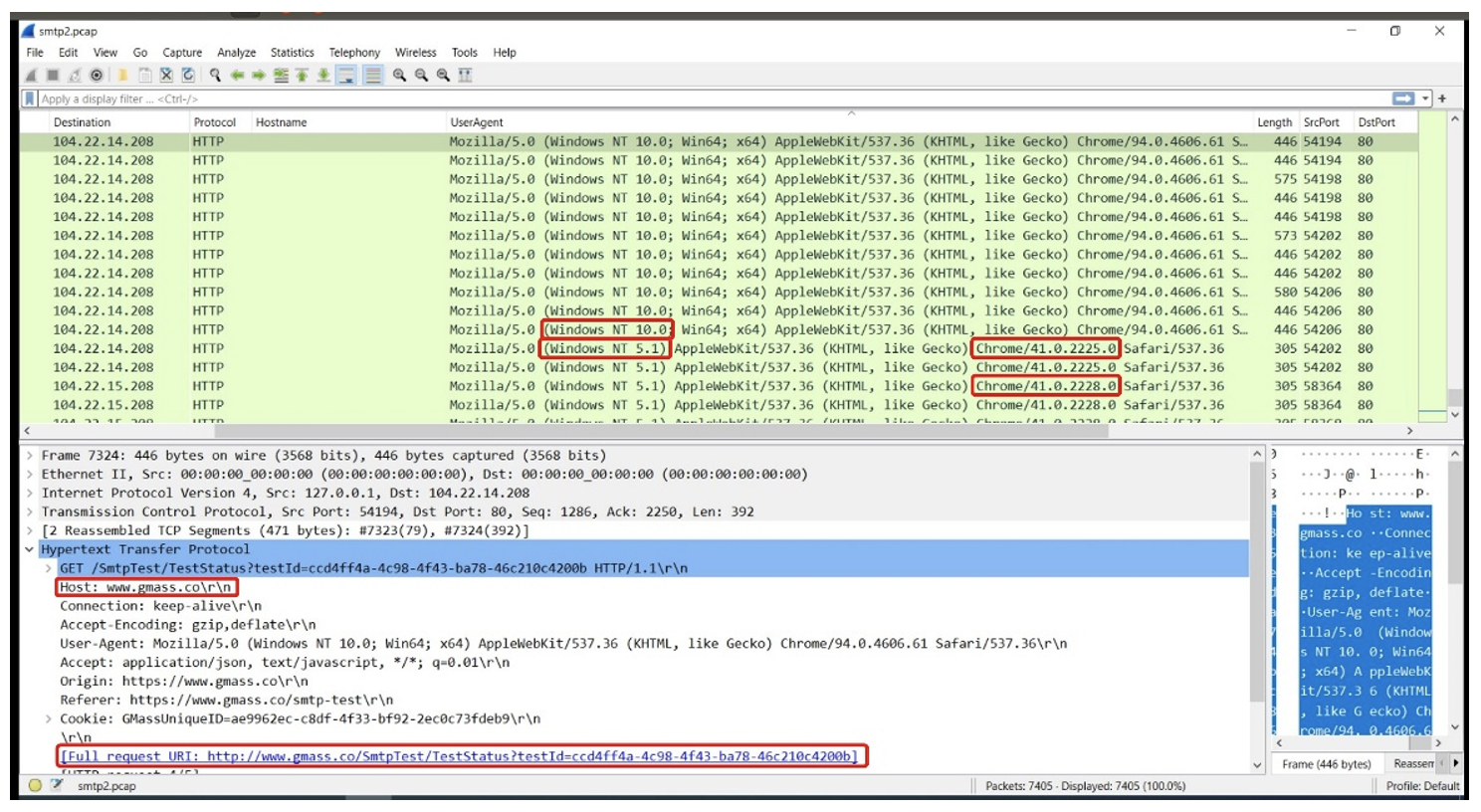
Recorded decrypted traffic from Smtp Checker by X-Splinter v1, showing alternating user-agents and usage of gmass.co.
Conclusion
As we showed in this blog installment, attackers demonstrate ingenuity by exploiting misconfigurations and capitalizing on the continued usage of basic authentication by organizations. The tools discussed in this chapter are representative examples of similar attack tools prevalent in the threat landscape. They were chosen to illustrate the broader trend of attackers leveraging such tools to target and compromise cloud accounts. While these tools may not necessarily be the most cutting-edge from a technical standpoint, they reflect common strategies and methodologies consistently employed by threat actors today.
It is evident that the increased proliferation of offensive toolsets poses a significant challenge to defenders, while democratizing hacking and lowering the entry level for new threat actors. Widespread SMTP-based attacks, in particular, present an ongoing threat to organizations, including security vendors and leading technology firms, which can inadvertently become new vectors for supply chain attacks or advanced persistent threats.
While this chapter has shed some light on toolsets and techniques used by threat actors, there are many more yet to be explored. In future installments of this series, we will continue to shed light on previously uncovered attack tools and nefarious Tools, Techniques and Procedures (TTPs).
Recommendations
It's essential to stress the importance of implementing multi-layered security measures and staying ahead of common threats. By staying informed and leveraging human-centric security technologies, organizations can effectively defend against emerging threats and minimize risks to cloud-based assets and sensitive data.
Implement proactive measures to mitigate the risks of account takeover and cloud-based threats.
Here are some key strategies to prioritize:
- Invest in comprehensive account takeover detection solutions. Stop human targeted attacks and enhance your security arsenal with robust detection mechanisms designed to detect and thwart modern attacks, such as:
- BEC and ATO detection
- Anomaly discovery
- Behavior analytics
- Opt for tools that offer actionable alerts, contextual threat intelligence, and adhere to MITRE ATT&CK® standards, ensuring comprehensive protection against evolving threats.
- Implement robust identity and access management (IAM) practices. Mitigate the risks associated with shared credentials, stored credentials, and shared secrets. Ensure a thorough understanding of access activities within your organization's environment to effectively manage and monitor them.
- Take proactive steps to address password security concerns by securely storing credentials outside of the environments where they are used.
- Recognize the prevalence of identity attacks originating from password dumps or data breaches and prioritize safeguarding against password spraying across corporate accounts.
- Focus on cybersecurity hygiene and enhance visibility into your environment to better detect and remediate vulnerable identities. Leverage solutions like Proofpoint Spotlight and Proofpoint Shadow to address both hygiene and threat detection aspects of identity attacks.
- Empower your users. Recognize the pivotal role your users play in your defense strategy. Conduct regular training sessions to educate them on identifying various threats. By fostering a security-conscious culture among your users, you can strengthen your organization's defense posture.
- Streamline incident response procedures. Establish clear protocols for investigating and mitigating specific threats and scenarios within your organization. Develop response procedures tailored to address incidents such as account takeover detections. Regularly test these processes through simulated exercises to ensure their effectiveness and readiness.
By implementing these prevention and remediation strategies, your organization can significantly bolster its resilience against cloud attacks and other threats, safeguarding critical assets and maintaining a robust security posture.

