Eighty-five percent of breaches involve human error, according to the 2021 Verizon Data Breach Investigations Report. Email remains the number one threat vector for people-centric attacks. And ransomware and business email compromise (BEC), or email fraud scams costing organizations millions.
So, what’s the best way to protect against these rapidly advancing and dangerous threats? That’s what Gartner explores in its recently published 2021 Market Guide for Email Security report. In this guide, Gartner provides a comprehensive list of capabilities that security leaders should look for in an email security solution.
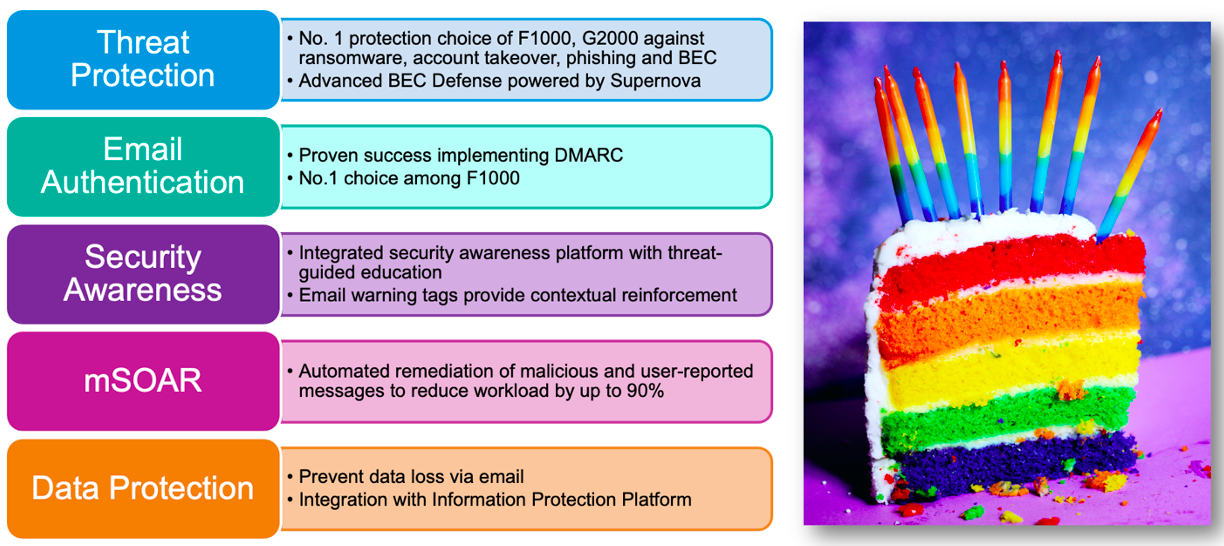
Here’s how email security from Proofpoint lets customers have their cake—and eat it, too.
We’re confident that we can address capabilities by Gartner.
Email security should be layered, like a cake
Figure 1. Five key requirements outlined in latest Gartner Market Guide for Email Security
The first and most important aspect of email security is that it requires layers to be effective. The days of hoping that one layer or one product will solve for the current threat landscape are over. Here’s what Gartner had to say about the current market definition for email security:
“Email security spans gateways, email systems, user behavior, content security, and various supporting processes, services and adjacent security architecture. Effective email security requires not only the selection of the correct products, with the required capabilities and configurations, but also having the right operational procedures in place.”
We agree, which is why Proofpoint has been building an integrated, layered approach to improve operational outcomes, reduce risk and provide our customers unmatched visibility into people-centric threats.
Let’s dive into Gartner Market Guide requirements for email security and show you how Proofpoint delivers on its recommendations.
First: Advanced protection against BEC and traditional threats
BEC attacks have surged in popularity because they’re easy to carry out and generally more difficult to detect as they don’t carry malicious payloads. Every month Proofpoint prevents millions of BEC attacks from ever reaching our customers.
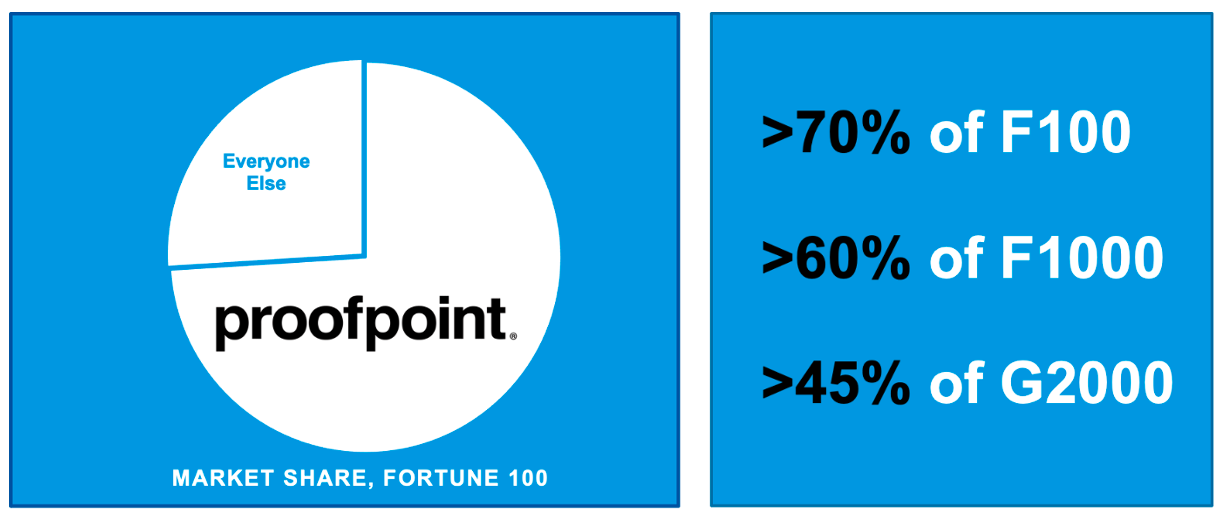
Figure 2. Proofpoint is the most trusted vendor in email security—and the market leader trusted by more organizations in the F100, F1000 and Global 2000
There’s a reason more organizations in the Fortune 100, Fortune 1000 and Global 2000 trust Proofpoint with advanced threat protection for their email security. Our Nexus Threat Graph, which combines over a trillion data points from email, cloud, network, domains, social media, users and a threat intelligence team that more than 100 people strong, drives our proven efficacy and ability to adapt to new threats quickly.
According to Gartner, organizations should:
“Look for email security solutions that use ML- and AI-based anti-phishing technology for BEC protection to analyze conversation history to detect anomalies, as well as computer vision to analyze suspect links within emails.”
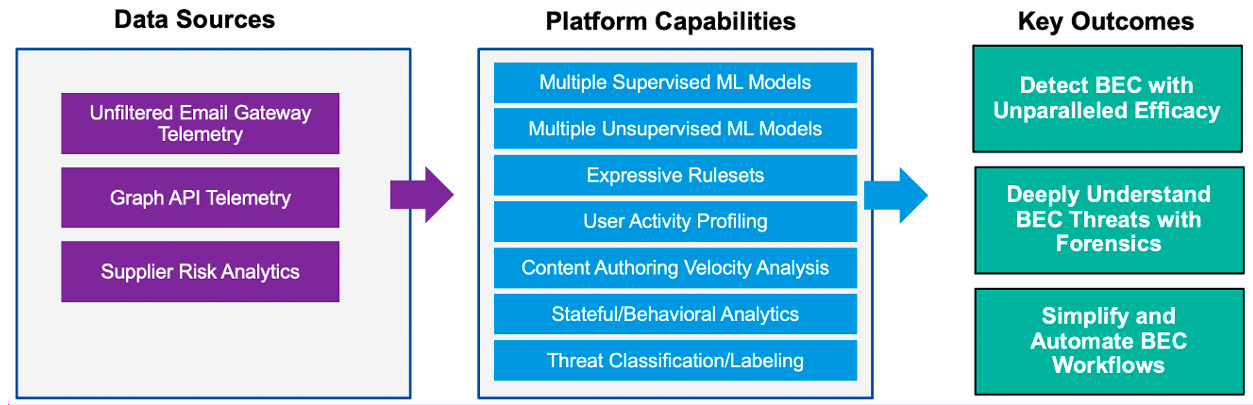
Figure 3. Proofpoint platform capabilities that help stop BEC attacks
Proofpoint has been refining our machine learning (ML) algorithms for more than 20 years as part of our larger NexusAI detection engines. Earlier this year, we launched an Advanced BEC Defense capability, powered by a completely new detection platform that we call Supernova. Using inbound and outbound gateway telemetry, supply chain risk analytics, and API data from cloud productivity platforms like Office 365 and Google Workspace, it accurately uncovers even the most sophisticated email fraud attacks—and it’s included with all Proofpoint advanced email security licenses.
While machine learning and artificial intelligence (AI) are popular buzzwords in the industry, effective outcomes are more important than marketing jargon. Proofpoint’s unmatched insights as the market leader in email security means more data for better efficacy. Unlike many email security solutions, Proofpoint delivers an extremely low false positive rate for detecting BEC, stopping teams from unnecessarily spending time sifting through messages to determine if they are, in fact, malicious.
But BEC isn’t the only type of attack Proofpoint prevents. We employ advanced sandboxing to inspect unknown attachments and URLs. Because we’ve observed a rise in legitimate file-sharing abuse, where attackers use well-known services to evade detection, we predictively sandbox all file-sharing URLs. Our research found more than half of malicious URLs delivered were from Microsoft (for example, OneDrive and SharePoint).
We also inspect attachments, including the URLs in attachments and even password-protected attachments. And we provide URL rewriting and time-of-click analysis to protect your users on any network and device. This helps reduce the risk of content activated as malicious post-delivery.
Second: DMARC authentication trusted by more organizations worldwide
An important layer of defense is authentication, which can help prevent BEC attacks, protect your organization’s reputation, and provide you with insights to prevent lookalike domains and other attacks.
Organizations should, according to Gartner: “Implement DMARC for protection against domain spoofing attacks.” Gartner also noted that:
“DMARC prevents exact name domain spoofing aimed at employees, partners and customers, but can be complicated depending on the size and number of domains in an organization. Professional services are often needed to assist with implementation and ongoing monitoring of DMARC.”
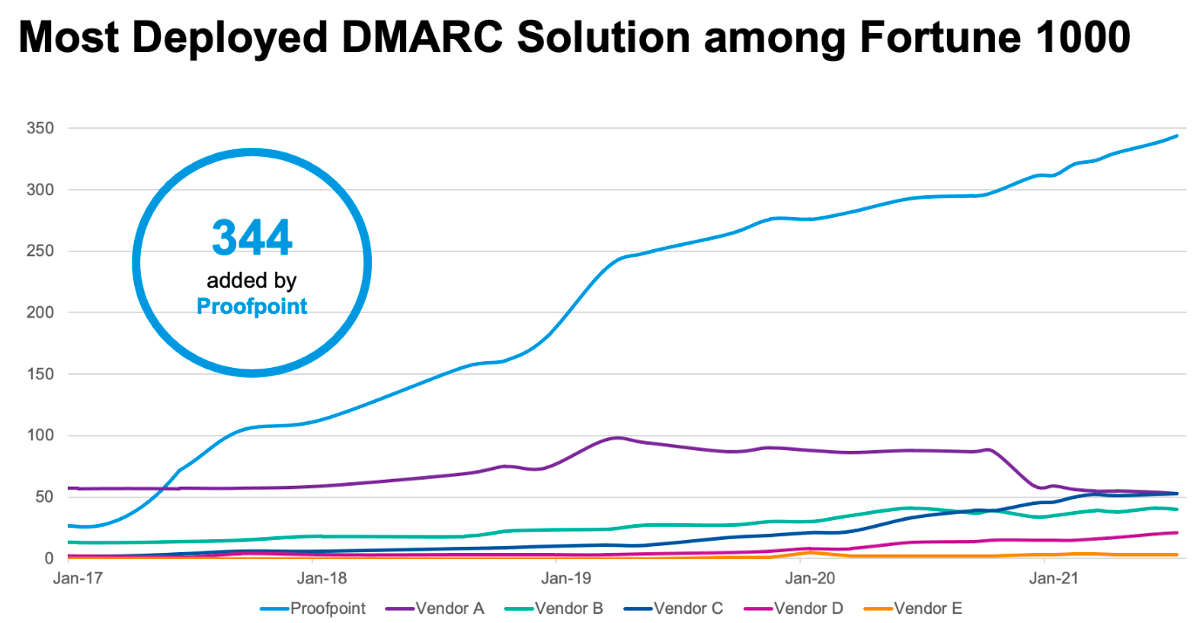
Figure 4. Chart showing DMARC implementations by different vendors
Proofpoint has implemented DMARC with more organizations in the Fortune 1000 than any other. We have the expertise needed for advanced configurations.
But it isn’t just a one-and-done event for organizations with DMARC. As part of our Email Fraud Defense solution, Proofpoint offers significant, ongoing value for customers to prevent fraud attacks such as comprehensive brand protection across senders, mitigation of lookalike domain abuse and visibility into supplier risk.
Third: Integrated security awareness training
Gartner also discusses the concept of integrated security awareness training in its Market Guide:
“Consider products that also include context-aware banners to help reinforce security awareness training. Invest in user education and implement standard operating procedures for handling financial and sensitive data transactions commonly targeted by impersonation attacks.”
Proofpoint is at the leading edge of how to educate users against targeted attacks. Our email security solution is tied closely to our Security Awareness Training offering for more targeted and effective education:
- Users who are Very Attacked People™ or engaging with real malicious email can be auto-enrolled into relevant education with our Targeted Attack Protection (TAP) Guided Training Integration.
- Our content is driven by Proofpoint threat intelligence, with trending lures, attacks and full campaigns for standard operating procedures in our extensive content library.
- Our Security Awareness Training solution uses the Nexus Threat Graph and the Proofpoint threat detection stack to score user-reported messages and provide insights into user reporting accuracy.
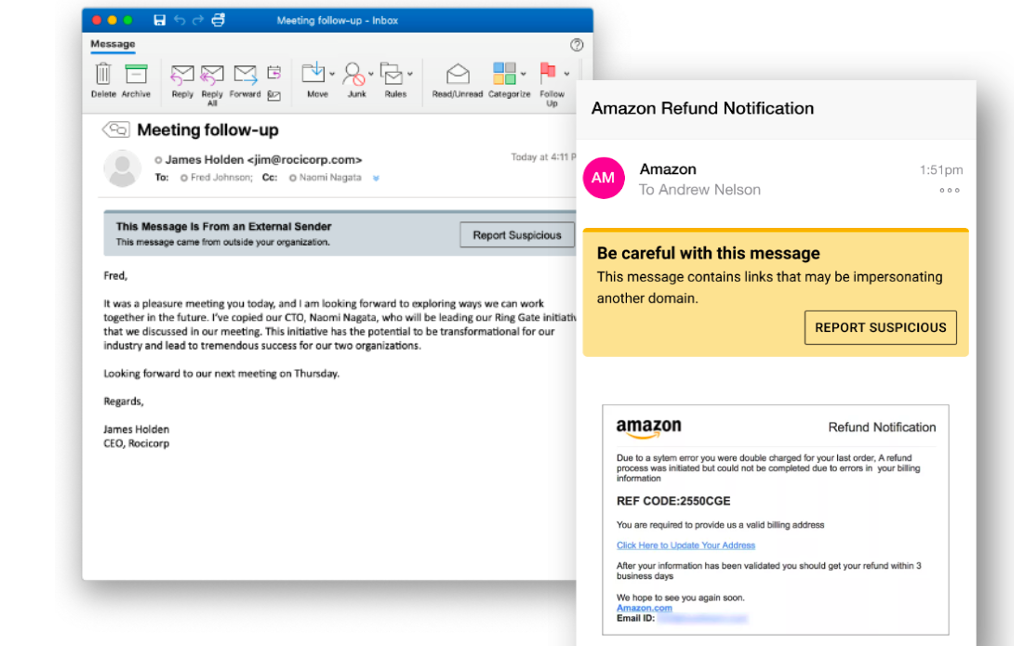
Figure 5. HTML-based Email Warning Tags with Report Suspicious from Proofpoint help organizations reinforce awareness and improve email security posture
Proofpoint also includes our contextual HTML-based Email Warning Tags with Report Suspicious for all email security customers, meaning users can get context about a potentially dangerous email and easily report it regardless of device. And when they do report messages, we offer powerful email security orchestration and response to reduce the operational impact on teams, while providing users feedback to “close the loop” and let them know what kind of message they reported.
Fourth: mSOAR with powerful automation for operational impact
There are two key use cases for the Proofpoint mSOAR solution, Threat Response Auto-Pull (TRAP):
- Automatically removing emails identified or weaponized post-delivery
- Remediating user-reported messages
In its Market Guide, Gartner said the following about mSOAR tools:
“Emails reported by the user can then be processed by MSOAR tools to assist in the automatic reclassification of emails and removing them from inboxes. Although this simplifies the processing of reported emails, it (remediation) can still put a burden on overstretched IT security teams.”
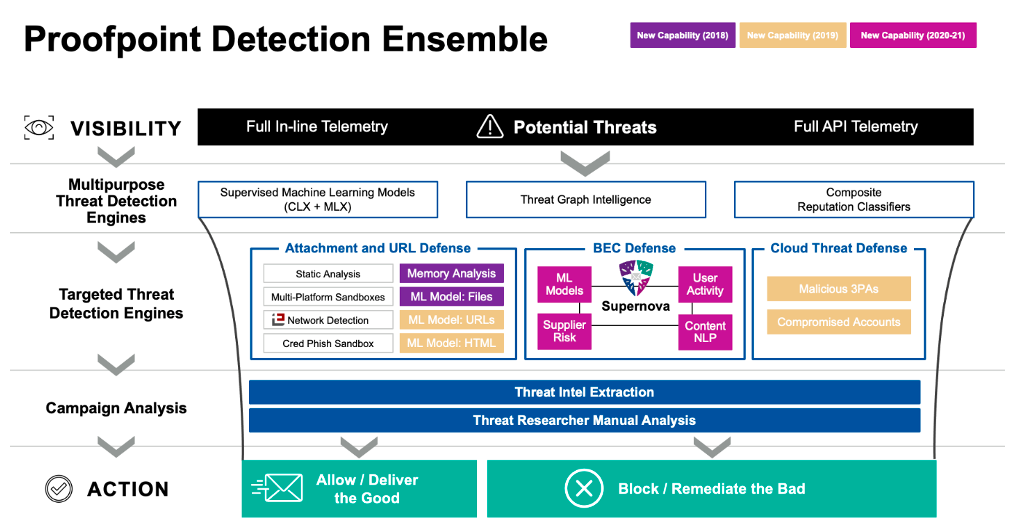
Figure 6. An overview of the detection ensemble for email security from Proofpoint, which drastically cuts incident response time
To reduce the burden on IT security teams, Proofpoint uses our leading corpus of data in the Nexus Threat Graph and our advanced detection stack to reduce workload by up to 90% in the use cases noted above.
After messages have gone through the entire detection ensemble, subsequent actions such as quarantine (including forwards or similar messages), case close, or integrated workflows with technology partners like Okta, SailPoint, CrowdStrike, Palo Alto Networks, VMware Carbon Black and others can be activated to streamline operations.
This automation can lead to thousands of dollars in reduced costs for internal resources, as was the case with the healthcare organization featured in this white paper.
Fifth: Email DLP as part of the Proofpoint Information Protection Platform
As we like to say at Proofpoint, “Data doesn’t lose itself.” The email data protection component can’t be underscored enough as a crucial element of email security and information protection.
And today, email data protection is more important than ever. As Gartner states in the Market Guide:
“The ability to secure, track and potentially redact sensitive data shared in email with partners, clients and/or customers becomes important, especially in light of continued regulations and privacy laws … Email also continues to be the most common cause of data breach, especially accidental data loss.”
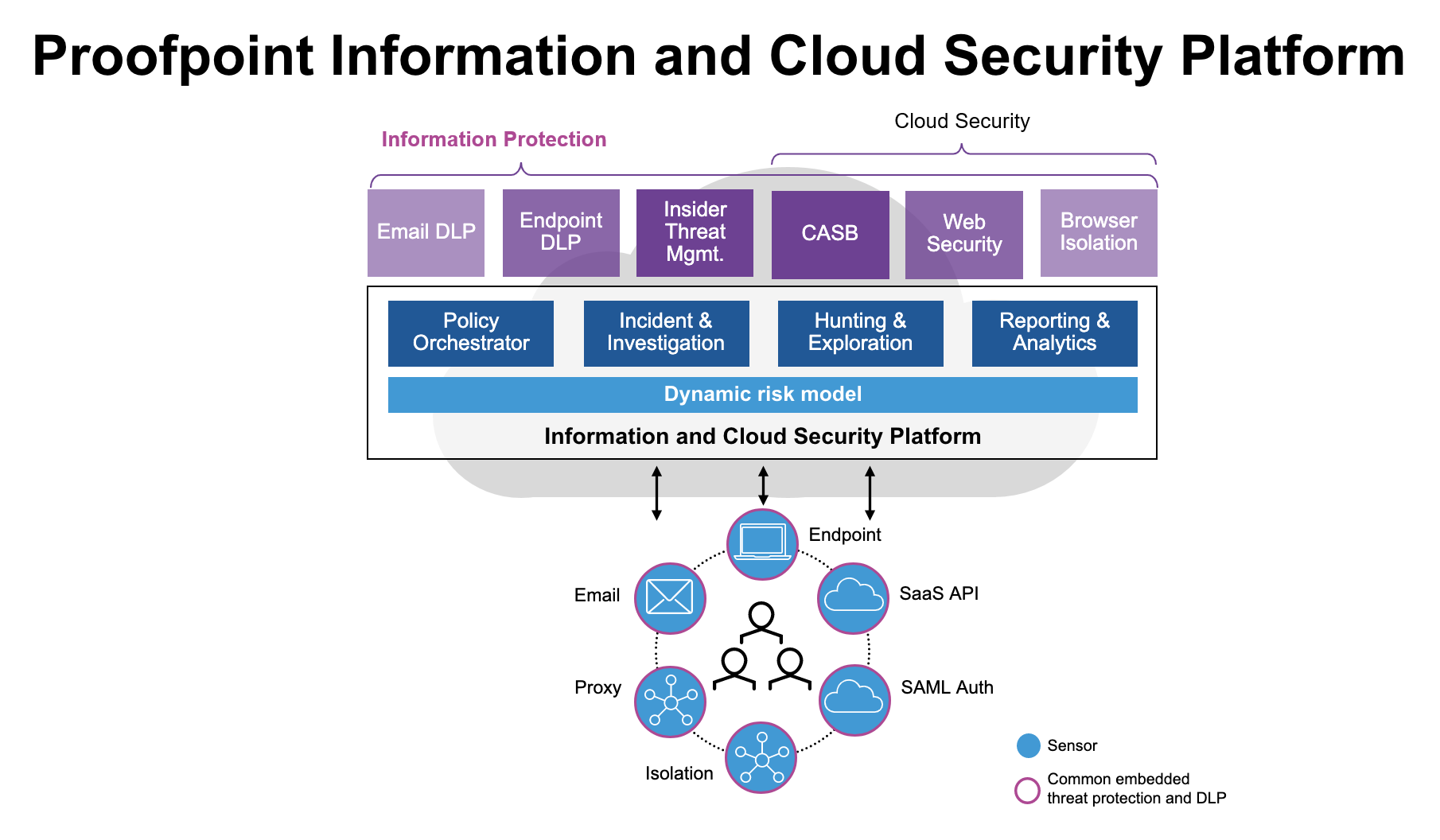 Figure 7. The full Information and Cloud Security Platform from Proofpoint provides powerful capabilities to reduce organization’s people-centric risk
Figure 7. The full Information and Cloud Security Platform from Proofpoint provides powerful capabilities to reduce organization’s people-centric risk
With Proofpoint’s full information security platform, our Email Data Loss Prevention (DLP) and Encryption solution becomes extremely beneficial as a key use case and starting point for greater information protection. With Proofpoint you can:
- Manage and enforce email DLP and encryption centrally with our email security platform.
- Take it a step further by integrating into the full Proofpoint Information Protection Platform to address insider threats, cloud security, content inspection and more to get contextual, people-centric visibility with a modern architecture.
Now that we’ve covered the five key use cases, let’s quickly cover how your team can manage this vital component of your security posture.
Eat your cake, too, with Managed Services for Email Security from Proofpoint
Information security departments around the globe are challenged by staff shortages and retention issues. With Managed Services for Email Security from Proofpoint, you can get optimized defensive systems, prioritized support, and proof of success with best-of-breed services aligned with our email security solution.
Our ongoing involvement will provide your organization with unmatched visibility and reduced risk, freeing your staff to focus on the most pertinent threats and other important projects.
Download Gartner report today to learn more about what to look for in an email security solution.
Gartner, Market Guide for Email Security, Mark Harris, Peter Firstbrook, 7 October 2021
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Please add the following disclaimer: GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.