Cybercriminals are constantly innovating so that they can infiltrate your systems and steal your valuable data. They do this through a complex multi-stage method commonly known as the attack chain. During the initial compromise, attackers use advanced email threats like phishing scams, malware attachments, business email compromise (BEC) and QR code threats to get a foothold in your systems. That’s why email security tools typically focus on stopping these threats.
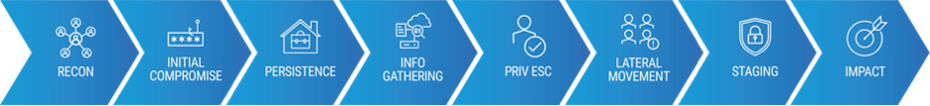
Steps in the attack chain.
But no technology is foolproof. Inevitably, some emails will get through. To keep your company safe, you need an email security solution that can detect, analyze and remediate email threats post-delivery. That’s where Proofpoint can help.
Proofpoint Cloud Threat Response is the cloud-based alternative to TRAP (Threat Response Auto-Pull), known for its effective post-delivery remediation capabilities. Not only is this solution easy to use, but it also automates post-detection incident response and remediation tasks that slow down security teams.
In this blog post, we’ll highlight some of its capabilities and benefits.
Overview of Cloud Threat Response capabilities
Proofpoint Cloud Threat Response keeps you safer by remediating threats post-delivery. Plus, it helps security teams prioritize and execute response actions three different ways:
- Automatically by Proofpoint. Cloud Threat Response automatically analyzes emails post-delivery. It identifies and quarantines malicious emails within user inboxes. Doing so reduces the risk that users will interact with them, helping to prevent your business from being compromised.
- Manually by the SOC team. Your security team gains instant access to detailed email analysis, historical data and risk scoring through an integration with Proofpoint Smart Search. This integration makes it easier for you to delve into specific emails and swiftly identify and remove any lurking threats.
- With the assistance of end users. Users can report messages that look suspicious thanks to a simple button directly integrated into their mailboxes. Reported emails are automatically investigated and are neutralized if determined to be a threat.
Proofpoint Cloud Threat Response benefits
At many companies, security incident response is a slow and labor-intensive process. Responding to security incidents may take days or weeks depending on the size of your security team. Time-intensive tasks can turn into painful bottlenecks.
Compare that to Proofpoint Cloud Threat Response, which automates and simplifies threat response tasks. Here’s what you can expect:
- Enjoy a simplified management interface. Our centralized, modern interface simplifies how you manage email security. From this dashboard, you can manage a range of tasks, including threat reporting, threat analysis and user administration.
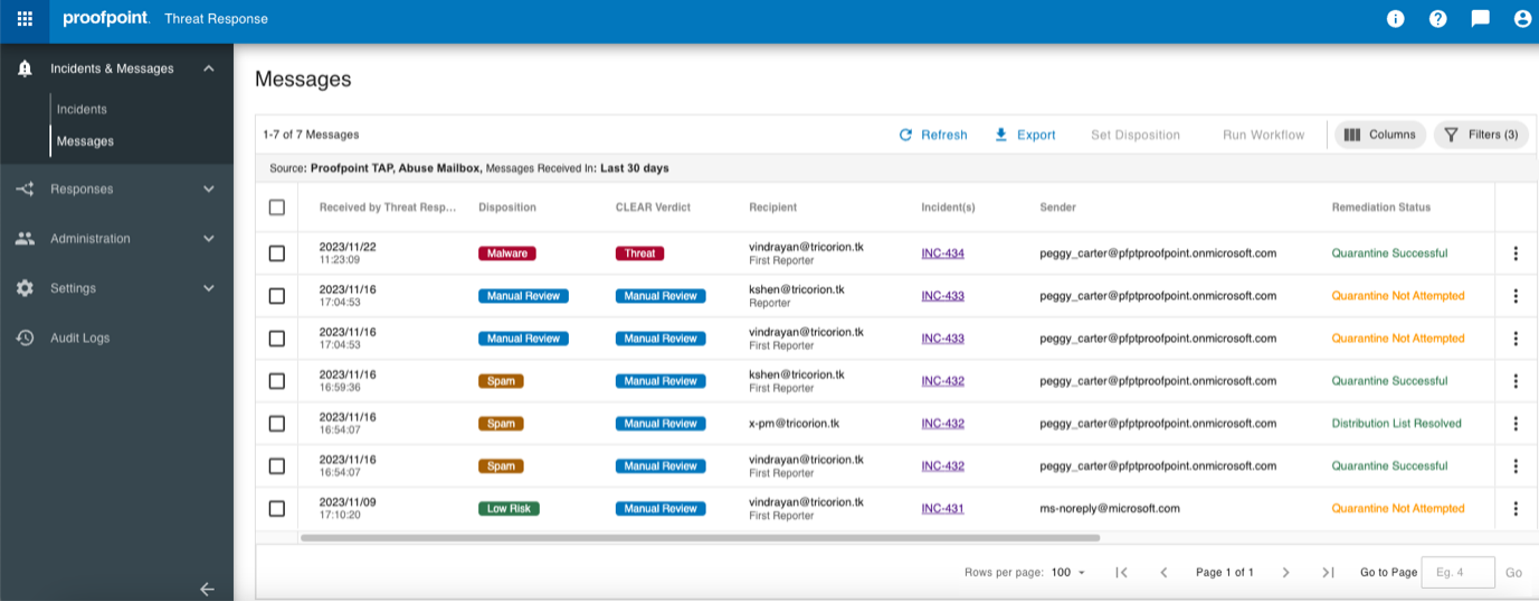
The simplified, modern interface of Proofpoint Cloud Threat Response.
- Respond to incidents faster. Proofpoint Cloud Threat Response acts on intelligence from our Supernova detection engine, which improves threat detection and reduces the mean time to respond (MTTR).
- Spend less time on deployment and maintenance. Because it’s cloud native, our platform is not only easy to deploy but it eliminates the need for on-premises infrastructure. Plus, your investment is future-proof, and it comes with automated maintenance and security updates.
- Streamline security operations. Use Single Sign-On (SSO) to seamlessly navigate between Cloud Threat Response and other Proofpoint apps such as Targeted Attack Protection, Email Fraud Defense and Email Protection. This helps to boost analyst efficiency and response times.
- See more threats. It automatically shares a threat’s remediation status across your other Proofpoint platforms. This increases threat visibility and helps you to identify and neutralize threats faster.
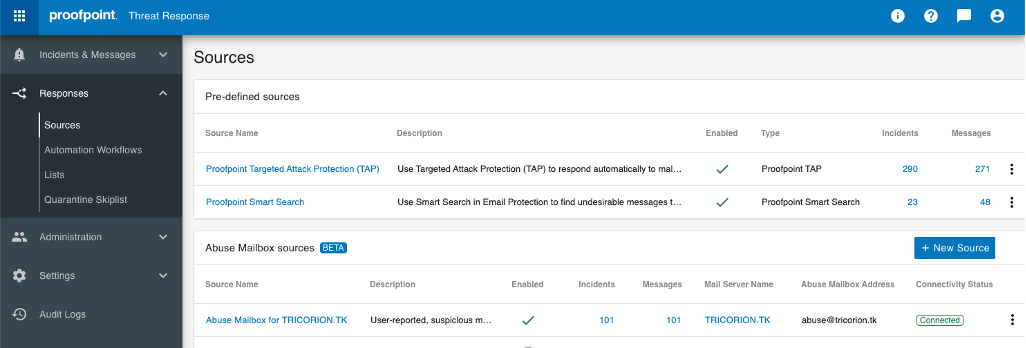
Proofpoint Cloud Threat Response is integrated with Proofpoint threat intelligence and abuse mailbox sources.
- Contain threats quickly. Malicious emails are automatically quarantined, deleted or labeled. This helps to ensure that users don’t interact with the threat.
- Automate your notifications. Whenever there’s a threat incident, you need to keep stakeholders informed. That’s why Proofpoint Cloud Threat Response includes templates. These messages are sent out whenever there’s a quarantined or reported email.
- Reduce busy work. Manual tasks like email removal are automated. This means that security teams have more time to focus on more important tasks and strategic initiatives.
Break the attack chain
Some threats can bypass traditional email defenses. Proofpoint Cloud Threat Response can help protect you from those threats. Our solution acts like a safety net by stopping malicious messages automatically—before they can reach users.
Proofpoint Cloud Threat Response also features tools that empower security teams. Not only do these tools help security teams quickly analyze and respond to suspicious emails, but they also speed up investigations. And employees are empowered, too. Built-in reporting gives them a way to directly flag suspicious emails for follow-up. This adds another layer of defense and helps to create a culture of proactive security within your company.
Next Steps
Learn more about Proofpoint Threat Response solutions here. If you’re an existing Proofpoint customer, you can log into Level Up and watch our training videos on this topic: “Cloud Threat Response Deployment” and “CLEAR Deployment for Cloud Threat Response.”

