Understanding your organization’s human attack surface is not just a good idea in today’s threat landscape; it’s essential. Why? Because it can make all the difference in your efforts to allocate your limited resources efficiently.
Let’s face it—in the world of cybersecurity, one size does not fit all. It is not feasible to adopt a uniform approach to secure your business. And while most of your users may pose a minimal risk, there are smaller, high-risk groups that attract the lion’s share of attention from cyberthreat actors. Identifying these groups and understanding what makes these users so enticing to attackers is key to creating an effective defense.
At Proofpoint, we recognize the importance of understanding the human attack surface. Our approach to cybersecurity revolves around a human-centric defense strategy. And email serves as a valuable window into the most vulnerable parts of your business. We analyze inbound threats directed at email addresses and enrich them with directory information. This is a Proofpoint Targeted Attack Protection (TAP) feature that’s available to all customers. As a result, we provide valuable insights into the job roles and departments that are prime targets for attackers.
In this blog, we’ll go through some of our most recent insights for the healthcare industry—and the job roles that attracted the most interest from attackers.
2023 research overview
For our research in 2023, we created a healthcare peer group of over 50 similar hospital systems to track within the Proofpoint TAP platform. We meticulously analyzed “people data” from these systems to identify trends in attack patterns. We tracked:
- Attack index
- Click rates
- Malicious message volume
- Total clicks across various departments
More specifically, we looked for outlier clusters that exhibited movement beyond the average. What follows are a few of our insights.
Threat actors target roles related to finance and the revenue cycle back-end
As it turns out, attackers have a penchant for people in finance-related jobs and those who are involved in transactions. These users were consistently attacked more than others.
When we drill down further on our findings, we see that departments involved in the supply chain and facilities management exhibit similar deviations from the average. The reason? These roles often require people to be involved in transactions, making them attractive targets for attackers.
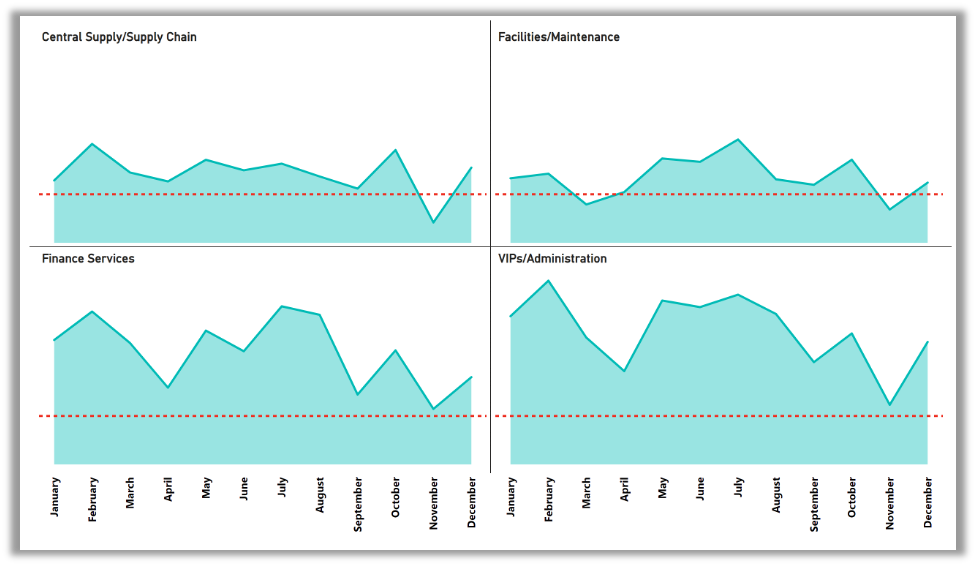
2023 department-level average attack index: Finance and transactional job roles averaged a significantly higher attack index per month per user.
Money is a bigger draw than data
But here is where it gets interesting. When we compare job roles and departments based on access to transactions versus access to health information, the difference is stark. It seems that attackers are more determined to interdict financial transactions than to gain access to users with large amounts of health data.
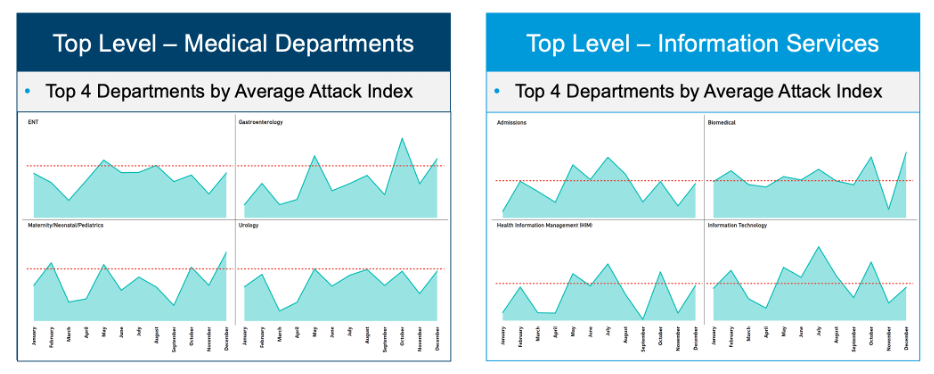
2023 department-level average attack index; medical and information services departments averaged a significantly lower attack index per month per user than financial and transactional job roles.
Threat actors go after roles that deal with patient service revenue
Going a step further, we wanted to understand the impact of threats on people in administrative and clinical roles who help capture, manage and collect patient service revenue. We examined the revenue cycle by categorizing job roles and departments in the following ways.
- Front-end (admin and pre-visit)
- Middle (visit, claim submission)
- Back-end (inbound processing, payer, patient)
The disparity between groups with access to transactions and those with access to health data is evident. The revenue cycle back-end category exhibits the highest average attack index among revenue cycle labeled data, which we attribute to finance job roles associated with billing.
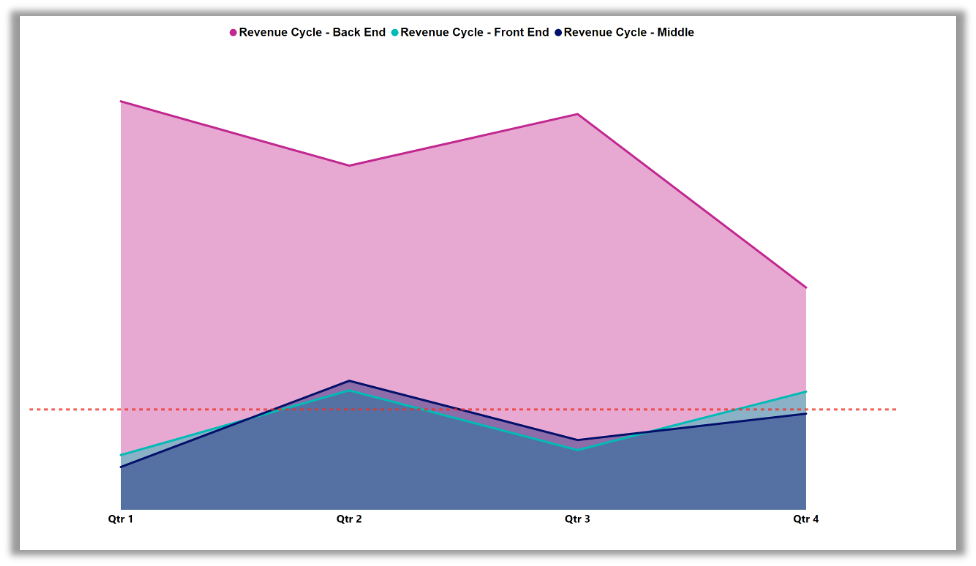
2023 average of attack index trends; revenue cycle quarterly comparison.
The interest of attackers in finance-related job roles comes as no surprise. Confirming this theory with extensive data over a year provides a foundational understanding.
Finance roles are more attractive than those in data and research
From the 2023 dataset, we analyzed attacked users based on keywords in their job titles into three risk areas outlined below.
- Finance keywords associated with risks related to transactions or financial loss
- Data keywords linked to risks of personal data exposure
- Research keywords that indicate risks to intellectual capital
Each category has a threat profile that includes the average attack index, total clicks and volume of malicious messages. We track this profile against all departments.
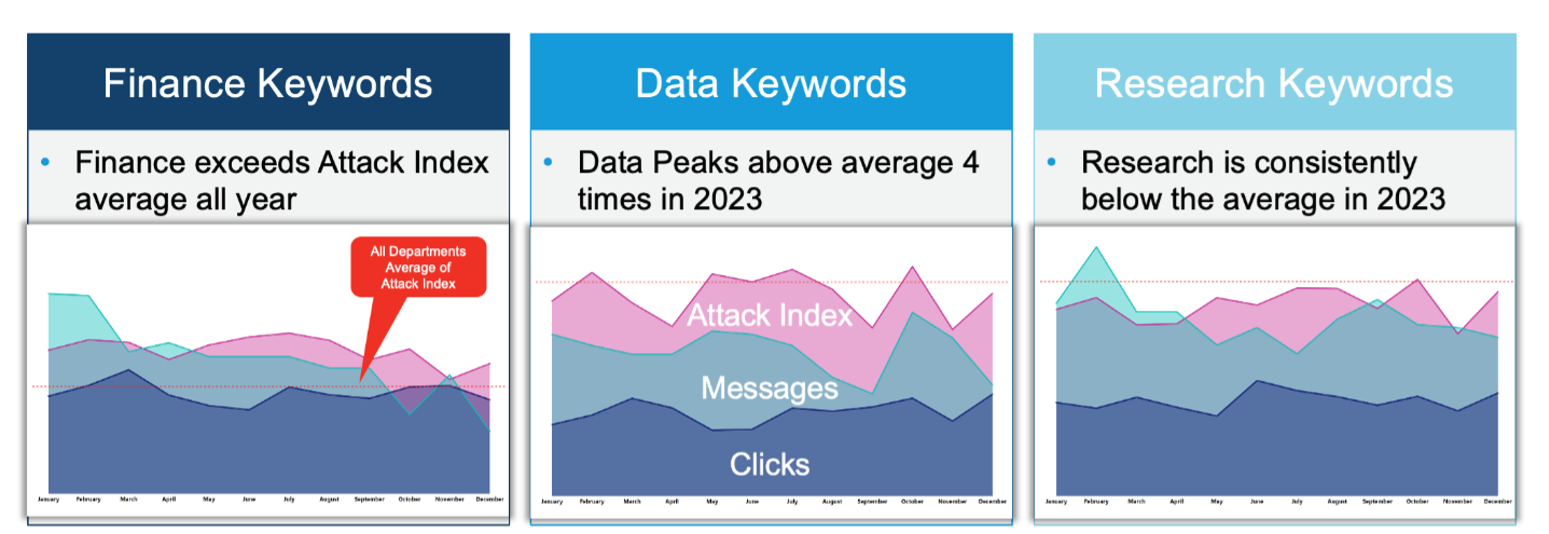
A comparison of job title keyword threat profiles.
Last year, the finance target group consistently exhibited a threat profile that surpassed the averages. This threat profile serves as our baseline. In the future, significant shifts in paradigms can be observed when a threat profile deviates from this baseline.
Valuable insights help you use your resources more effectively
So, what does all of this mean for defenders like you? It means that what you think is most at risk at your organization may not be what attackers are actually targeting.
When you know where attackers are likely to focus their efforts, you can deploy your limited resources more effectively. And you can effectively communicate your organization’s needs to nontechnical leadership.
The human attack surface area is the key to protecting your business from threats. When you have this data, you can minimize risk and enhance manageability—even if you have a limited budget—because you can focus on the areas that matter most. This helps you stay one step ahead of cyberthreats and keep both your organization and your users more secure.
Learn more about human-centric cybersecurity solutions for healthcare from Proofpoint.

