Threat actors no longer operate in silos. Today, they use multiple channels such as SMS, email, fake web pages, and compromised cloud accounts. They use these various channels to establish persistence and compromise identities so that they can elevate privileges and move laterally.
Proofpoint Threat Research recently observed campaigns in which threat actors used multichannel attacks to target the retail industry. The attack chain and timeline show how the threat actors (TA) move from one targeted organization to the next. Each time their unauthorized access is revoked or exhausted, the attackers move on to the next target.

The multichannel attack chain that targets global retailers.
In our research, these campaigns begin with a smishing attack. A smishing attack, also known as SMS phishing, uses SMS text messages to trick recipients into doing what the attacker wants them to do. This might be providing their personal or financial information, clicking on malicious links or downloading harmful software applications. The smishing messages use short support ticket themes to lure victims to the threat actor’s phishing sites.
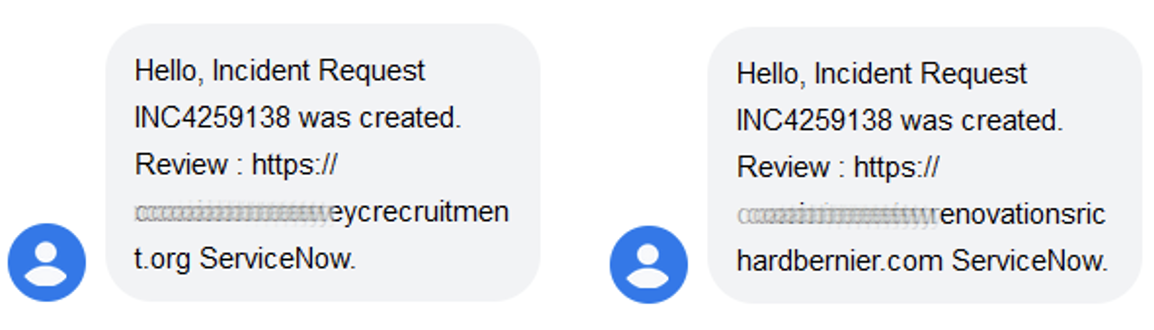
Examples of SMS phishing messages with support ticket themes.
In the campaign we observed, the TA used a customized Microsoft phishing page that included the targeted organization's branding. This page led users through the MFA authorization flow to collect their credentials.
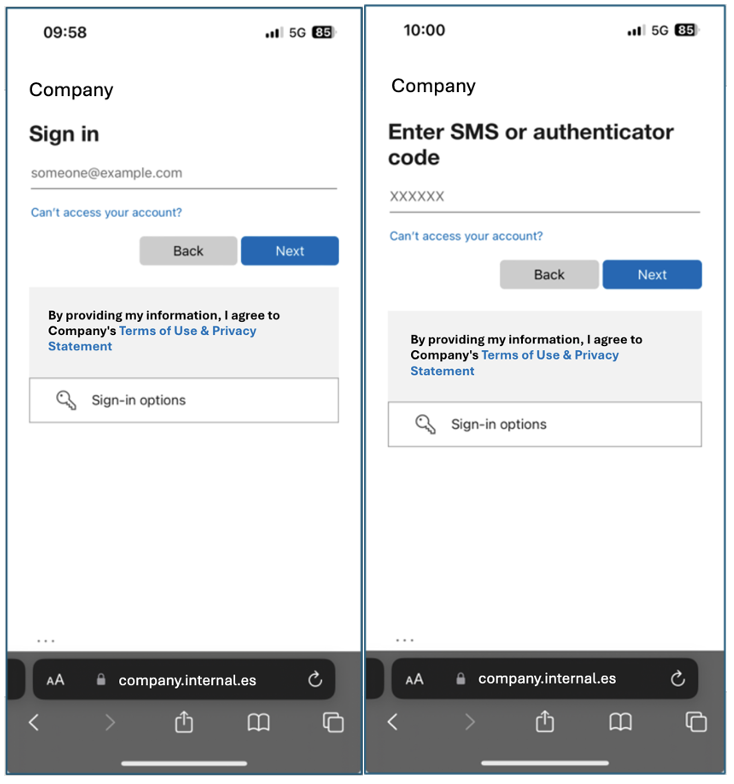
Example of customized Microsoft phish page with the target organization’s branding.
Once the TA captured credentials, they compromised user accounts. Post-account takeover (ATO), the attackers used several methods to maintain persistent access and hide their unauthorized activities. These include:
- MFA manipulation. The attackers used hijacked accounts to register their own MFA methods.
- Enrollment of new devices via native Microsoft apps (such as Intune Enrollment). This helped the attackers hide their unauthorized activities and gain access to certain resources.
- Malicious use of corporate VPN. The TA used the victim’s VPN and ZTNA products and several of their own VPN clients to access resources such as security products and production environments.
The attackers gained access to the organization’s single sign-on (SSO) portal, which in turn provided access to numerous other internal services and third-party applications (3PA). The attackers enumerated all apps connected to the IDP and tried to find API connections that they could abuse. Then they went into a specific business application to create counterfeit gift cards.
Attribution
The threat actor in this attack has potential areas of overlap with the actor whom Microsoft tracks as Storm-0539. This threat actor is, “known to target retail organizations for gift card fraud and theft using highly sophisticated email and SMS phishing during the holiday shopping season.” Although these attacks did not originate in email, their overlap in TTPs (tactics, techniques, and procedures) leads us to believe that the activity set may align with the threat actor we track as TA4901. This TA has been targeting companies in the telecommunications and retail sectors since at least 2018.
The power of end-to-end insights
What makes Proofpoint stand out from other security providers is that we have end-to-end insights into these attacks, including SMS threats. This is thanks to our Cloudmark group, which works with mobile operators to protect mobile messaging. We combine this capability with threat actor tracking and cloud threat insights to identify shifts in attack patterns quickly which gives us a significant advantage over our competitors.
We protect more than 9,000 enterprise customers and roughly 500,000 SMBs. That means we can see threats across multiple industries. This visibility allows us to readily identify and protect frequently targeted sectors.
Tips to protect your organization
Threat actors constantly evolve their tactics, so our defenses must evolve with them. Here are a few ways to protect your organization:
- Train users on multichannel attacks. It’s no longer enough for users to learn about email-based threats. They should also learn about attacks like SMS-based threats.
- Deploy systems to flag threats. When an account has been compromised, your teams need to know as soon as possible. Make sure have systems in place that can notify them when an account has been compromised. They should also be notified about any potentially malicious post-compromise actions, like adding MFA factors and enumerating applications.
- Limit access from unmanaged devices. Wherever possible, it’s a good idea to limit VPN access to managed and authenticated devices only.
Organizations must stay one step ahead in the constantly evolving threat landscape. At Proofpoint, we are committed to providing the insights and tools you need to protect your assets in this challenging environment.
Indicators of compromise
|
Indicator |
Type |
Description |
|
216.151.180.15 |
Source IP address |
Observed operational infrastructure used by attackers for account takeover and unauthorized activities |
|
216.151.180.16 |
Source IP address |
Observed operational infrastructure used by attackers for account takeover and unauthorized activities |
|
216.131.72.131 |
Source IP address |
Observed operational infrastructure used by attackers for account takeover and unauthorized activities |
|
216.131.84.178 |
Source IP address |
Observed operational infrastructure used by attackers for account takeover and unauthorized activities |
|
216.131.84.179 |
Source IP address |
Observed operational infrastructure used by attackers for account takeover and unauthorized activities |
|
216.151.191.110 |
Source IP address |
Observed operational infrastructure used by attackers for account takeover and unauthorized activities |
|
64.145.79.135 |
Source IP address |
Observed operational infrastructure used by attackers for account takeover and unauthorized activities |
|
64.145.79.136 |
Source IP address |
Observed operational infrastructure used by attackers for account takeover and unauthorized activities |
|
209.222.97.47 |
Source IP address |
Observed operational infrastructure used by attackers for account takeover and unauthorized activities |
|
192.200.148.241 |
Source IP address |
Observed operational infrastructure used by attackers for account takeover and unauthorized activities |
|
192.200.148.242 |
Source IP address |
Observed operational infrastructure used by attackers for account takeover and unauthorized activities |
|
216.131.120.90 |
Source IP address |
Observed operational infrastructure used by attackers for account takeover and unauthorized activities |
|
216.131.120.91 |
Source IP address |
Observed operational infrastructure used by attackers for account takeover and unauthorized activities |

