The latest annual Internet Crime Report from the FBI’s Internet Crime Complaint Center (IC3) states that the United States experienced “an unprecedented increase” in cyber-attacks and other malicious cyber activity in 2021. Among the top incidents reported were business email compromise (BEC) and email account compromise (EAC), which drove $2.4 billion in adjusted losses for businesses and consumers last year.
That figure marks a hefty increase from the $1.8 billion reported in 2020. For the American public, it’s also a new record high in financial losses due to BEC/EAC. These scams represented nearly 35% of all reported cybercrime-related financial losses last year — which was also a 28% increase, year over year.
Victims of cyber-crime reported a record number of complaints to the IC3 in 2021 — 847,376. The potential losses due to these crimes exceeds $6.9 billion. And while the number of filed complaints only rose 7% year over the year, the total reported losses from cyber-crime incidents increased 64% in 2021, up from $4.2 billion in 2020.
Following is a closer look at other key findings from the IC3’s latest “Internet Crime Report,” along with some analysis based on our observations of these cybercrime trends:
Email fraud continues to dominate financial losses
In 2021, the IC3 received 19,954 complaints about BEC/EAC scams. As noted earlier, the adjusted losses related to those incidents totalled nearly $2.4 billion. The average loss per email fraud incident rose from $96,373 to $120,074, which is a year-over-year increase of nearly 25%.
While ransomware attacks continue to dominate the cyber-crime headlines, BEC and EAC accounted for the largest percentage (35%) of financial losses related to cyber-crime in 2021. Ransomware losses last year totalled $49,207,908, the IC3 reports. However, the financial losses that the center attributes to BEC and EAC scams in 2021 is 49 times greater than that figure.
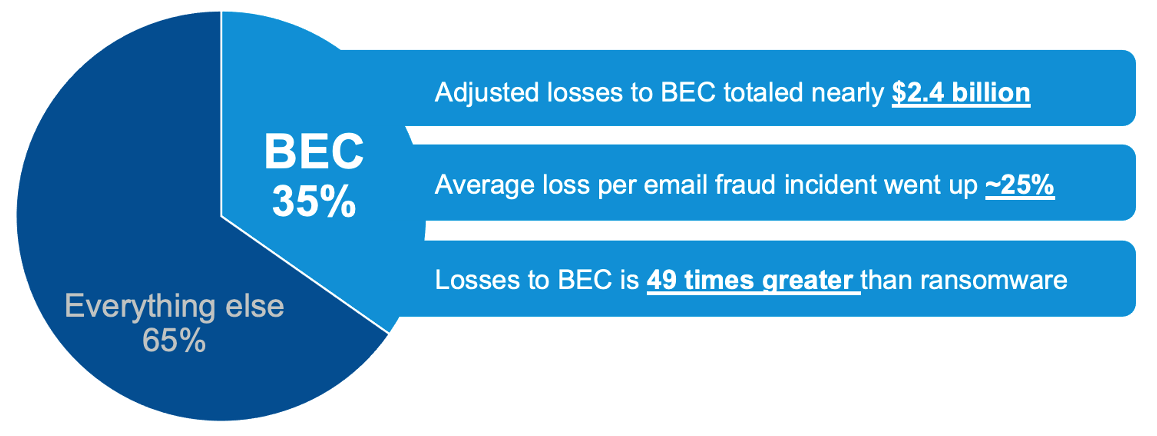
Figure 1. BEC/EAC continued to represent the largest financial loss among all cyber-crime types (Source: FBI IC3’s 2021 “Internet Crime Report.”)
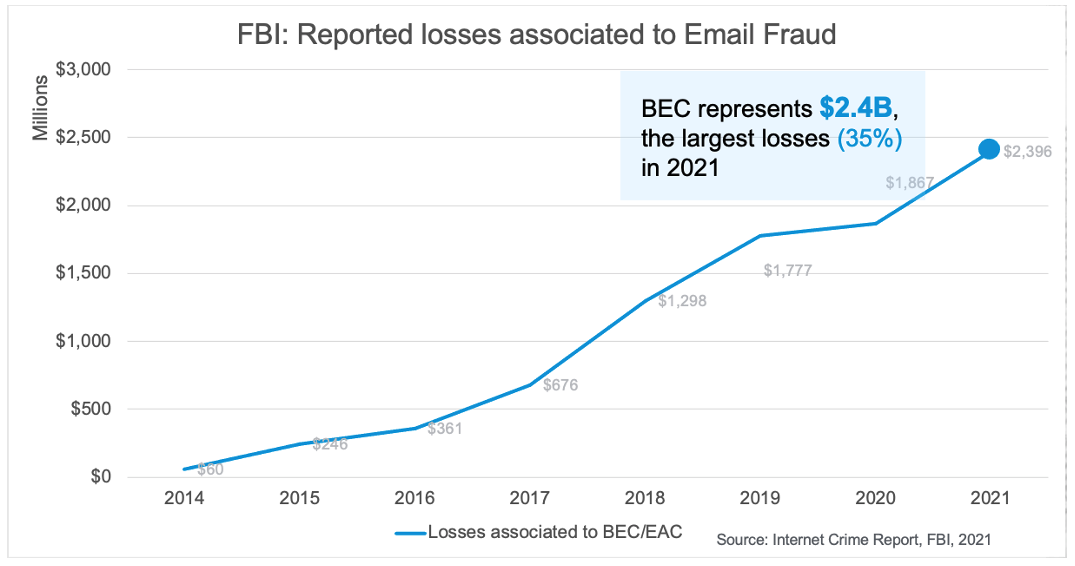
Figure 2. Financial losses due to email fraud attacks increased 28% in 2021 (Source: FBI IC3’s 2021 “Internet Crime Report.”)
The IC3 report’s data also helps to spotlight how highly targeted BEC/EAC scams are — and how, even though attack volume is low compared to other types of cyber-attacks, the resulting financial losses for victims of BEC/EAC can be significant. The “Internet Crime Report” states that the number of complaints filed last year about these scams increased just 3% from 2020. However, financial losses due to BEC/EAC scams increased 28% in 2021, resulting in a 25% year-over-year increase in the average loss per incident.
BEC scheme keeps evolving, along with fraudsters’ tactics
The “Internet Crime Report” for 2021 points out that the BEC/EAC scheme has evolved as fraudsters’ methods have become more sophisticated. The report says these scams used to involve “simple hacking or spoofing of business and personal email accounts and a request to send wire payments to fraudulent bank accounts,” with malicious actors employing compromised vendor emails, requests for W-2 information, real-estate fraud, gift card scams and more. But now, fraudsters are using virtual meeting scams and spoofing business leaders’ emails to initiate fraudulent wire transfers.
Among all the BEC variants in use today, Proofpoint has observed that supplier invoicing fraud often accounts for the largest financial loss because of the business-to-business (B2B) payments involved. Our research also shows that almost all organizations (98%) receive threats from the supplier domain.
Attackers, through their use of vendor impersonation or compromised vendor accounts, are using organizations’ trusted suppliers and business partners to advance their schemes. Despite this trend, Proofpoint finds that most organizations lack visibility into which vendors pose risk.
Phishing soars 280% during COVID-19 pandemic
The number of complaints filed about phishing scams and related techniques, like vishing, smishing and pharming, have soared 280% during the COVID-19 pandemic, which began in early 2020. The “Internet Crime Report” notes that complaints about various kinds of phishing scams accounted for 38% of all cyber-crime complaints reported to the center last year.
As Figure 3 shows, the incident count for this threat type has been rising over the past five years—and significantly so during the past two years. The number of phishing/vishing/smishing pharming incidents grew 34% from 2020 to 2021. Meanwhile, the other four top types of cybercrime—extortion, identity theft, personal data breach and non-payment/non-delivery—have remained stagnant since 2017.
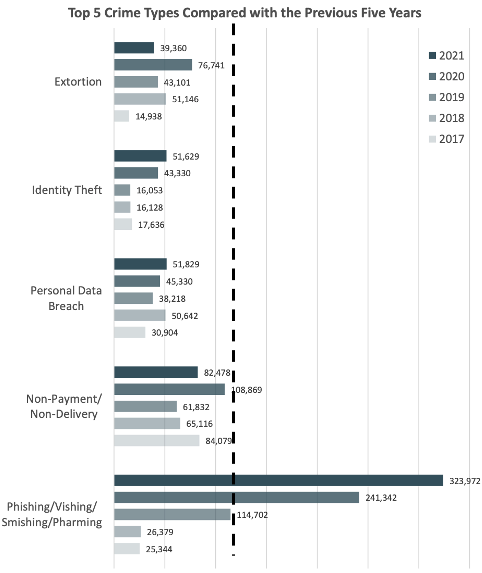
Figure 3. Top five crime types in 2021, compared with the previous five years. (Source: FBI IC3’s 2021 “Internet Crime Report.”)
The significant growth in phishing and related techniques over the past several years suggests that threat actors are continuing to take advantage of people-centric vulnerabilities. Organizations should therefore understand their people risk and implement the necessary controls, since email remains the number one threat vector.
Ransomware sees explosive growth in 2021
The IC3’s data shows that the number of ransomware incidents continued to rise in 2021, with 3,729 incidents reported to the center—an increase of 51% year over year. And the financial losses that the IC3 attributes to ransomware attacks in 2021 (more than $49 million) is 69% higher than 2020’s figure.
Keep in mind, though, that the financial losses for 2021 are artificially low because it doesn’t include losses from wages, files, equipment or remediation services, according to the IC3. The $49 million figure only represents what businesses and consumers reported to the IC3—and it doesn’t include direct reports made to FBI field offices. This suggests that the true number of ransomware incidents and associated losses for 2021 are likely much higher.
The “Internet Crime Report” also states that “Ransomware tactics and techniques continued to evolve in 2021, which demonstrates ransomware threat actors’ growing technological sophistication and an increased ransomware threat to organizations globally.” The top three initial infection vectors for ransomware incidents last year, the IC3 says, were phishing emails, Remote Desktop Protocol (RDP) exploitation, and the exploitation of software vulnerabilities.
With the increase in ransomware-related incidents and the growing participation of opportunistic initial access brokers in delivering the malicious software, organizations should consider “shifting left” and investing in prevention. Protecting the email channel and stopping threats at the early stage of the attack chain is the most effective way to defend against ransomware.
FBI’s IC3 report highlights importance of a people-centric approach to security
Many attackers today rely heavily on social engineering to lay the groundwork for, activate and advance their campaigns—and they’re targeting people all along the way. The findings in the latest “Internet Crime Report” from the FBI’s IC3 help underscore the need for organizations to take a people-centric, multi-layered platform approach to combat human-activated threats.
Proofpoint can help your organization reduce its security risks with an integrated threat protection platform that stops email and cloud threats targeting your people. Our platform also provides visibility into your “people risk” and helps train your users to be more resilient against today’s advanced threats.
To learn more about our solutions for BEC and EAC protection, see this page.

