This blog post is part of a monthly series, Cybersecurity Stop of the Month, which explores the ever-evolving tactics of today’s cybercriminals. It focuses on the critical first three steps in the attack chain in the context of email threats. The goal of this series is to help you understand how to fortify your defenses to protect people and defend data against emerging threats in today’s dynamic threat landscape.
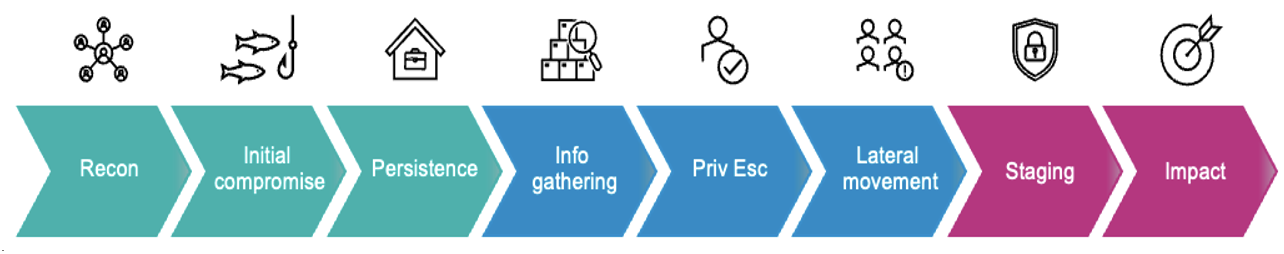
The critical first three steps of the attack chain—reconnaissance, initial compromise and persistence.
So far in this series, we have examined these types of attacks:
- Supplier compromise
- EvilProxy
- SocGholish
- eSignature phishing
- QR code phishing
- Telephone-oriented attack delivery (TOAD)
- Payroll diversion
- MFA manipulation
- Supply chain compromise
- Multilayered malicious QR code attack
In this post, we will look at how adversaries use impersonation via BEC to target the manufacturing supply chain.
Background
BEC attacks are sophisticated schemes that exploit human vulnerabilities and technological weaknesses. A bad actor will take the time to meticulously craft an email that appears to come from a trusted source, like a supervisor or a supplier. They aim to manipulate the email recipient into doing something that serves the attacker’s interests. It’s an effective tactic, too. The latest FBI Internet Crime Report notes that losses from BEC attacks exceeded $2.9 billion in 2023.
Manufacturers are prime targets for cybercriminals for these reasons:
- Valuable intellectual property. The theft of patents, trade secrets and proprietary processes can be lucrative.
- Complex supply chains. Attackers who impersonate suppliers can easily exploit the interconnected nature of supply chains.
- Operational disruption. Disruption can cause a lot of damage. Attackers can use it for ransom demands, too.
- Financial fraud. Threat actors will try to manipulate these transactions so that they can commit financial fraud. They may attempt to alter bank routing information as part of their scheme, for example.
The scenario
Proofpoint recently caught a threat actor impersonating a legitimate supplier of a leading manufacturer of sustainable fiber-based packaging products. Having compromised the supplier’s account, the imposter sent an email providing the manufacturer with new banking details, asking that payment for an invoice be sent to a different bank account. If the manufacturer had complied with the request, the funds would have been stolen.
The threat: How did the attack happen?
Here is a closer look at how the attack unfolded:
1. The initial message. A legitimate supplier sent an initial outreach email from their account to the manufacturing company using an email address from their official account. The message included details about a real invoice that was pending payment.
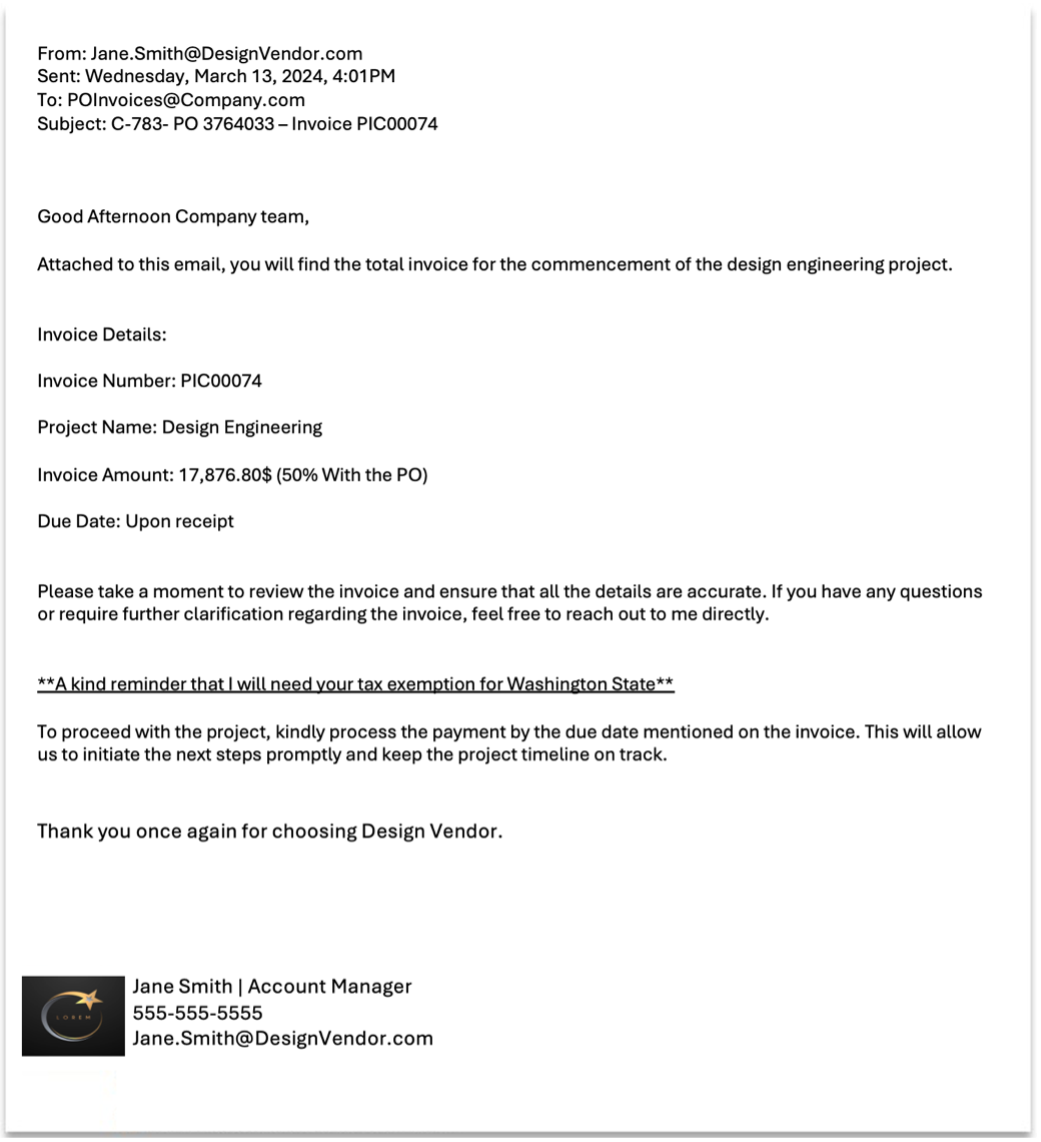
The initial email sent from the supplier.
2. The deceptive message. Unfortunately, subsequent messages were not sent from the supplier, but from a threat actor who was pretending to work there. While this next message also came from the supplier’s account, the account had been compromised by an attacker. This deceptive email included an attachment that included new bank payment routing information. Proofpoint detected and blocked this impersonation email.
In an attempt to get a response, the threat actor sent a follow-up email using a lookalike domain that ended in “.cam” instead of “.com.” Proofpoint also condemned this message.
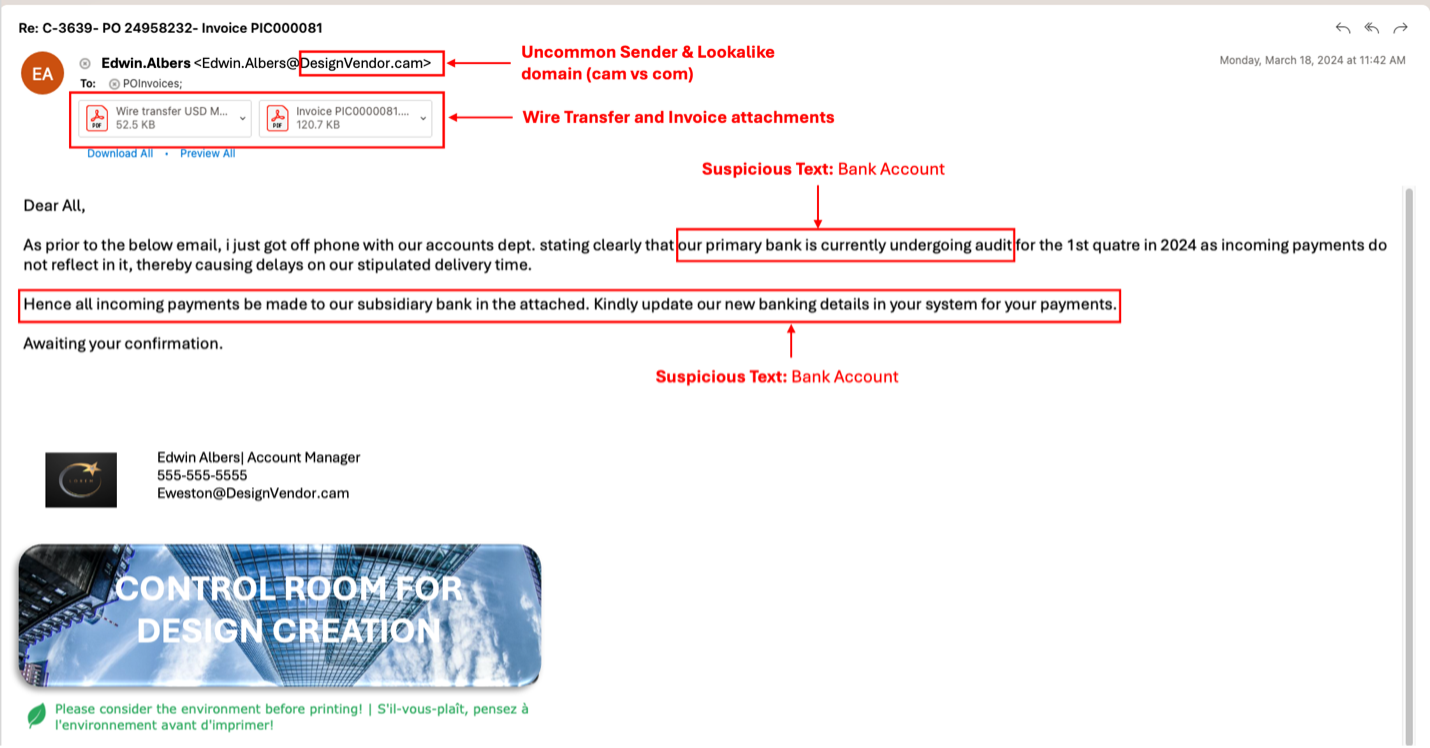
An email the attacker sent to mimic the supplier used a lookalike domain.
Detection: How did Proofpoint prevent this attack?
Proofpoint has a multilayered detection stack that uses a sophisticated blend of artificial intelligence (AI) and machine learning (ML) detection methods to identify and block BEC threats. Our approach integrates domain age analysis, ML algorithms and authentication mechanisms to form a comprehensive defense strategy.
First, we implemented an AI and ML to pinpoint “domain tells.” In this instance, the email included domains that mimicked legitimate ones in the carbon copy (cc) addresses.
The attacker also sent messages that looked like they were being sent from the account owner’s colleagues within the supplier organization. Threat actors will frequently camouflage their fraudulent messages this way.
Attackers design lookalike domains so their messages appear to come from trusted and authentic email domains. They might simply change or add a few characters to create a lookalike domain. This subtle deception can make it difficult for recipients to identify the email as a threat. But Proofpoint can recognize this domain tell and block these emails.
In addition to using lookalike domains, generative AI (GenAI) tools like ChatGPT also allow attackers to write content, clean up context, mimic writing styles and tone to create highly convincing, targeted and automated phishing messages.
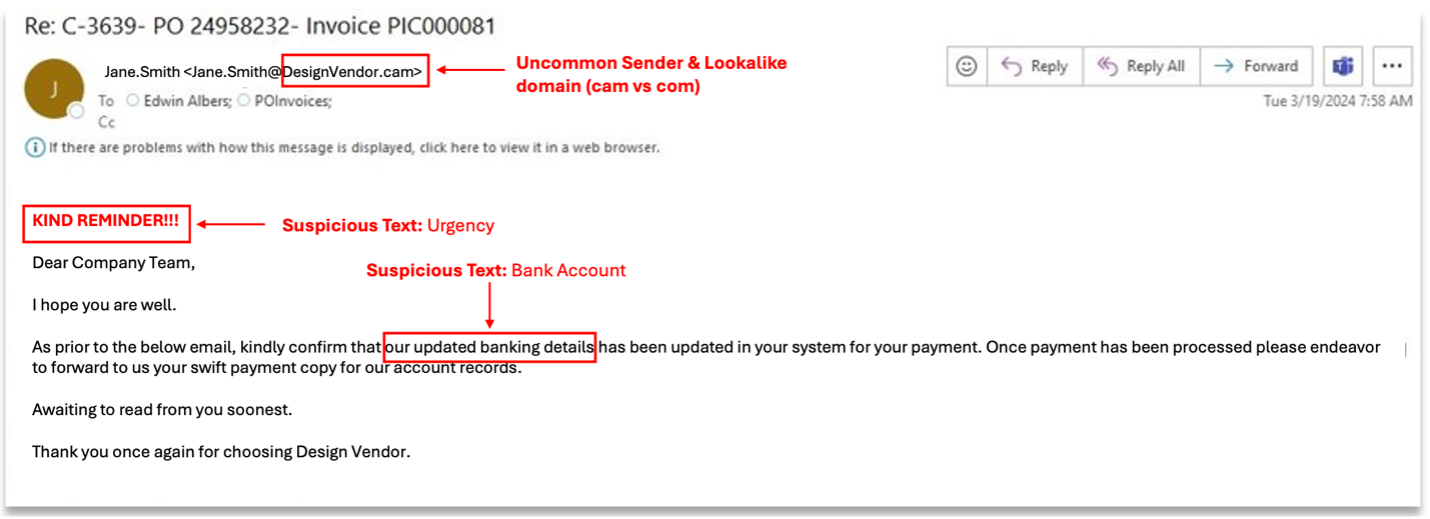
A follow-up email that impersonated the vendor used a lookalike domain.
We used a second detection technique to identify “contextual references of intent.” The email to the manufacturer included attachments and a message that referenced changes to bank routing. This type of request is a major red flag. It indicates a threat actor’s intent to manipulate the routing of financial transactions, likely to an account that they control.
Attachments in emails can carry hidden threats. Proofpoint Threat Protection now includes a pre-delivery semantic analysis large language model (LLM) for an extra layer of threat detection. The new machine learning (ML) threat detection engine understands the intent and context of incoming messages. And it does this before emails are delivered to users. In this case, the reference to bank routing changes suggests an attempt at financial fraud. By identifying contextual references, Proofpoint can prevent hidden threats from reaching their intended targets. In this scenario, the targets were members of the payment team at the manufacturer.
Proofpoint Threat Protection can identify multiple suspicious BEC attack indicators using three key indicators of compromise (IOC). These include:
- Change request. The request to change the destination bank account over email is a key element of suspicion established via text analysis (including now with Pulsar LLM).
- Newly registered domain. The identification of a newly registered domain (with certain registration properties) that is a close lookalike of the supplier’s domain adds to the suspicion.
- Different reply address. Analysis of the ongoing conversation where attackers replaced legitimate addresses with a lookalike address puts the proverbial nail in the coffin.
Remediation: What are the lessons learned?
Here are two key lessons from this scenario:
- Pre-delivery email detection is crucial. To protect your employees and keep your business safe, you need to block malicious messages before they can be delivered. To do this, you need a solution that combines AI and ML algorithms with advanced threat detection to identify and block threats.
- Users need to be empowered to become effective defenders. Your employees, contractors and partners are your last line of defense. That is why it is so important to have a security awareness program in place that can teach them about all types of BEC attacks and how they can avoid and report them. If you help your users learn how to stay alert for deceptive emails, suspicious tasks and unusual requests, it can greatly reduce the risk that they will play a part in a data breach or financial fraud that can impact your business.
Proofpoint delivers human-centric protection
Today's email threat landscape is fragmented with a myriad of advanced attacks emerging daily. From phishing schemes to ransomware attacks, malicious actors constantly evolve their tactics, exploiting vulnerabilities in human behavior. Proofpoint can provide you with human-centric protection to protect your users and your business from these and other types of attacks.
Proofpoint Supplier Threat Protection defends businesses against emails sent from their vendors and partners whose accounts may be compromised. It uses advanced AI and the latest threat intelligence to detect potentially compromised accounts and prioritize which accounts to investigate. And Proofpoint Threat Protection combines semantic analysis with behavioral AI to provide high-fidelity detection and efficacy to stop advanced email threats predelivery.
With a modern approach that provides continuous threat detection and analysis (predelivery to post-delivery to click-time) throughout the email delivery chain, Proofpoint enables you to achieve end-to-end protection even against new threats, like GenAI.
To learn how to protect people and defend data in the world of generative AI, register for our upcoming webinar “How to Protect People and Defend Data in the Age of Generative AI” featuring Forrester research.

