Reducing the risks that people create for their organisations is not a simple task. Every day, users lose their credentials, download and run malware, fall for social engineering attacks, and inadvertently put data at risk. What’s more, users create these risks across the very applications that organisations depend on: email, collaboration tools, cloud apps and the web.
Enter Proofpoint Nexus. With Nexus, security teams now have access to an integrated platform that uses multiple model types trained by trillions of email, web and cloud interactions. We power Nexus with all the right capabilities, from advanced semantic and behavioural AI to threat research-driven detections. This ensures it can solve advanced human-centric cybersecurity challenges so that organisations can protect their people and defend their data.
Nexus delivers insights to help with 4 areas
Proofpoint Nexus transforms massive amounts of raw data into meaningful insights that support our innovative products:
- Threat Defense
- Information Protection
- Security Guide
- App & Identity Posture
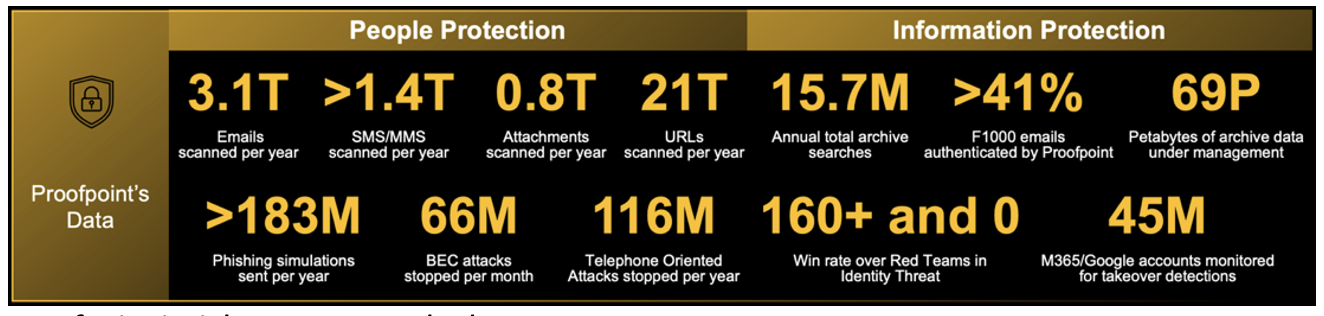
Proofpoint insights are unmatched.
With the launch of Nexus, Proofpoint is focusing on threat defence. Cybercriminals target every step in the attack chain. And they do this across email, collaboration tools and cloud platforms.
Proofpoint Nexus combines semantic and behavioural AI, machine learning (ML), and curated threat intelligence from researchers to create a multi-layered defence. This helps us identify, stop and analyse evolving threats in real time, like MFA phishing, cloud account takeovers, ransomware, and business email compromise (BEC).
Detection technology that drives human-centric security
Today’s threats are constantly changing. That’s why a single layer of defence won’t cut it. Each part of Proofpoint Nexus serves a unique role. It processes vast amounts of data from email, cloud platforms, and collaboration tools to secure all points of communication and interaction. Its modular design covers everything, from stopping threats before they reach users to monitoring risks after delivery.
Here is an overview of its five models.
1: Nexus Language Model (LM) for BEC
This model uses the power of advanced AI language models to combat BEC. It carefully examines email content to detect common elements found in BEC threats, like transactional language or urgency. By recognising subtle linguistic patterns and behavioural cues, Nexus LM for BEC identifies suspicious emails before they can cause harm.
Highlights
- Because it has an LM core, Nexus LM can analyse message intent and context. This enables it to find subtle malicious patterns that might evade traditional detections.
- Nexus LM can detect hidden threats within email, collaboration tools and messaging platforms.
- Nexus LM does not analyse baseline language characteristics on a per-user basis.
Nexus in action
Nexus LM adds a critical layer of defence against advanced email-based attacks. During a BEC attack, a threat actor might impersonate a CEO and request a wire transfer. While the attacker’s message lacks traditional phishing markers, Nexus can still interpret its underlying intent. It understands that there’s an attempt at financial fraud and so it triggers a security alert.
2: Nexus Threat Intelligence (TI)
To stay ahead of threats, you need real-time intelligence that predicts attackers’ tactics. Nexus TI integrates vast amounts of threat data to ensure that Proofpoint solutions are constantly ahead of evolving cyberthreats. This model not only enhances the detection capabilities of all Proofpoint products, but it also provides real-time updates on emerging threats, attacker tactics and system vulnerabilities.
With its focus on advanced threat intelligence, Nexus TI ensures that Proofpoint products can proactively detect and defend against attacks. This system is critical to maintaining a resilient security posture against modern threat actors.
Highlights
- Nexus TI ingests vast amounts of global data and applies ML to turn it into actionable insights.
- This intelligence fuels all Proofpoint solutions.
- Nexus TI adapts continuously to help businesses stay a step ahead of attackers.
Nexus in action
Recently, Nexus identified a phishing campaign that targeted financial institutions. After a policy change, when phishing attempts began to imitate tax authorities, Nexus detected the tactics and alerted security teams. This rapid and intelligent response enabled institutions to move fast to strengthen their defences and block the attack.
3: Nexus Relationship Graph (RG)
Insider threats and compromised accounts can easily slip past traditional security measures. That’s why you must be able to identify subtle behavioural changes in your users. Nexus RG uses AI to monitor and assess user behaviour to bolster your cybersecurity defences. By using behavioural analytics, machine learning, and anomaly detection, Nexus RG spots deviations from normal user interactions that may indicate a potential threat.
Nexus RG integrates seamlessly with Proofpoint threat detection systems. This enables it to enhance your real-time defences and protect your organisation against threats caused by risky user behaviours.
Highlights
- Nexus RG monitors user activity on a continuous basis. It analyses real-time data to detect deviations that may indicate malicious actions.
- Nexus RG issues proactive alerts to enable your security teams to respond fast and prevent damage.
- Nexus RG reinforces a human-centric approach to security by addressing both external and internal risks.
Nexus in action
Nexus RG can play a powerful role in proactive risk management and insider threat prevention. Consider this example. Nexus RG flags an employee who manages marketing data but suddenly downloads financial records during their off-hours. Because his activity is unusual, it triggers an alert. This alert leads the security team to discover a compromised account. As a result, the team can stop data exfiltration before any harm is done.
4: Nexus Machine Learning (ML)
As threats become more complex, traditional rule-based defences fall short. Nexus ML is a core AI technology that ensures Proofpoint products can detect and mitigate a wide range of evolving threats across multiple cybersecurity areas. It uses advanced techniques – like supervised learning, unsupervised learning and ensemble methods – to provide scalable and robust security.
Highlights
- Nexus ML evolves its models based on real-world attack data. This enhances its detection accuracy and minimises false positives.
- It applies AI-driven intelligence to live attack scenarios. This ensures defences stay robust and agile.
- Nexus ML uses advanced machine learning to fortify the threat detection capabilities of Proofpoint products.
Nexus in action
Nexus ML can detect subtle indicators like altered URLs or atypical attachment behaviour within large volumes of email and web traffic. This enables it to identify previously unknown threats, like novel phishing attacks. Nexus ML can then block these threats across the network.
5: Nexus Computer Vision (CV)
Bad actors use visual deceptions like phishing sites, malicious attachments and spoofed websites to bypass traditional defences. Nexus CV detects threats that are hidden in visual elements like images, QR codes, and manipulated emails. By focusing on visual threat vectors, this model enhances security by providing a powerful response to attacks involving embedded images and other graphical content.
Highlights
- Nexus CV identifies and neutralises visually-based threats.
- Through advanced computer vision technology, Nexus CV detects threats hidden in visual elements like phishing sites, QR codes, malicious attachments, and spoofed emails.
Nexus in action
Nexus CV may identify malicious QR codes that are embedded in documents or email attachments. These codes can direct users to dangerous websites or trigger malware downloads. Nexus CV detects these subtle threats and flags them before users engage with them.
Nexus CV can identify images that create compliance risks, too, like inappropriate content or images that are tied to regulatory violations. This type of proactive detection adds a powerful layer of protection beyond the usual text-based methods.
Face tomorrow’s threats more confidently with Proofpoint Nexus
Proofpoint Nexus drives our human-centric approach to security. Nexus models work together to detect hidden threats, neutralise risks and pre-emptively protect your business against new attack vectors. It provides proactive and multi-layered protection that can help you face tomorrow’s threats with greater confidence and resilience.
Contact us today for a personalised demo. See for yourself how our platform can enhance your security posture with AI.