If you’re facing an increased number of attacks that originate from the third parties or suppliers you do business with, you aren’t alone. In our research for our 2023 State of the Phish report, Proofpoint learned that 69% of organizations experienced an attack that originated within their supply chain.
Attackers have turned the supply chain and partner ecosystem into a threat vector. They’re using compromised supplier accounts to steal credentials, send malware and scam organizations with Business Email Compromise (BEC) attacks, such as invoicing fraud. Often, they’re targeting smaller organizations to compromise because their cybersecurity is usually not as robust. Then they leverage the trusted relationships these suppliers have with larger partners.
When it comes to supply chain threats, most security teams play defense because they lack visibility into the third parties their company interacts with. This means they can only respond to compromised supplier accounts after they get an alert. And when there is an investigation, it’s highly manual and time-consuming.
With Proofpoint Supplier Threat Protection, organizations can proactively defend against email-based supply chain attacks. By combining behavioral artificial intelligence (AI) with threat intelligence, it can detect and prioritize which compromised supplier accounts security teams should investigate. Plus, it provides in-depth insights for each of those accounts to make investigating them simpler.
Key benefits
Here’s how Proofpoint Supplier Threat Protection helps you proactively detect the compromised accounts of third parties and suppliers:
- Automating alerts for vendor accounts sending malicious messages
- Prioritizing supplier accounts for teams to investigate and remediate
- Identifying employees who have communicated with a compromised account and the information exchanged
With Proofpoint, security teams can focus on the partners that expose your organization to the greatest risk.
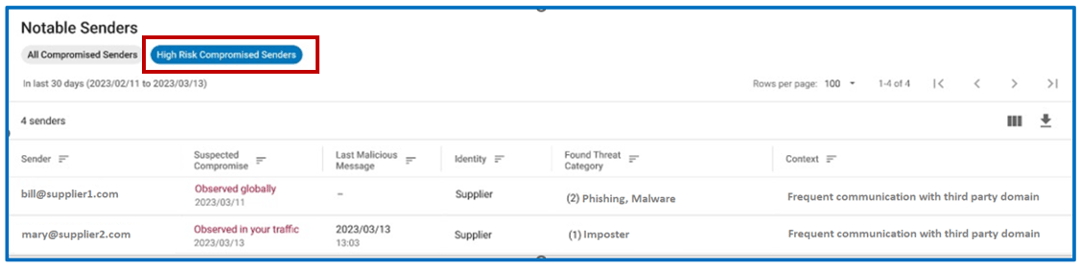
A prioritized list of high-risk senders in Proofpoint Supplier Threat Protection.
Providing proactive defense
Supplier Threat Protection helps organizations take a more proactive stance toward managing supply chain risk. By monitoring data across the Proofpoint ecosystem, the solution can detect compromised account activity from the vendors you interact with, even if you haven’t been the target of an attack—yet.
This is important because your organization might not always be the first target of an attack.
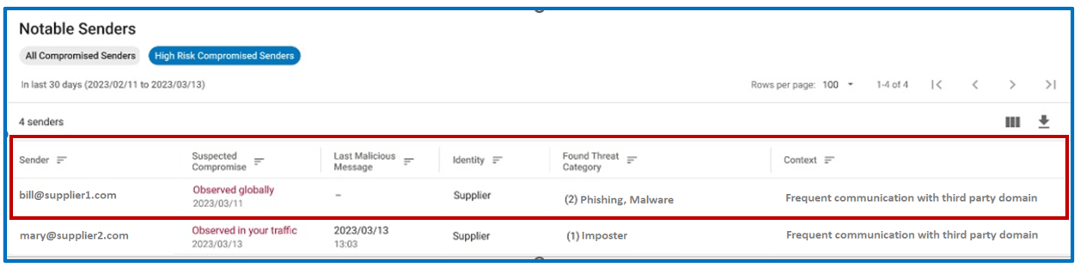 See which supplier accounts are compromised before threats are sent to you with Supplier Threat Protection.
See which supplier accounts are compromised before threats are sent to you with Supplier Threat Protection.
If Supplier Threat Protection spots compromised account activity coming from your partners, you’ll be notified. You can then move quickly to block, quarantine or carry out sender-based URL isolation policies. And if you receive malicious traffic from one of these accounts, you can opt to get an email alert or direct notifications to any SIEM via an API.
Enabling simplified investigations
Supplier Threat Protection provides attack insights for compromised supplier accounts. This means that when there’s an attack, security analysts can quickly understand what happened and what to do next. The platform provides a detailed analysis and a timeline view of activity. It also identifies targeted recipients and what threats were sent to them.
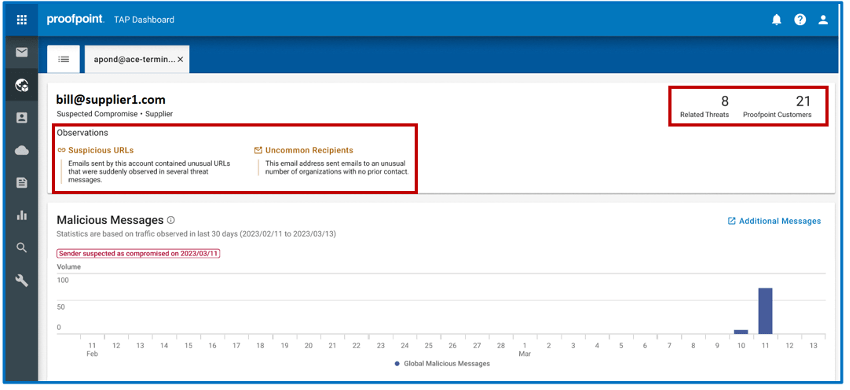
Insights on suspected compromised accounts in Proofpoint Supplier Threat Protection.
Learn more
Proofpoint Supplier Threat Protection can strengthen your overall security posture. Licensed as an add-on to Proofpoint Targeted Attack Protection, Supplier Threat Protection helps strengthen your overall security posture and is now available for immediate purchase. To learn more, check out the Supplier Threat Protection video on our Targeted Attack Protection page. Or contact your Proofpoint sales representative.