As reported in Proofpoint’s 2024 State of the Phish, more than 68 million malicious messages were associated with Microsoft products and brand in 2023, making Microsoft the world’s most abused brand by cybercriminals.
SharePoint and other Microsoft productivity and collaboration tools dominate the market, with over 400 million licenced Microsoft 365 users. Microsoft holds an impressive 88% market share in productivity software (Gartner). As organisations increasingly rely on Microsoft’s integrated security solutions, the concentration of risk rises. Many organisations use Microsoft SharePoint for real-time collaboration with employees, partners, and customers, leveraging its capabilities to move beyond simple content repositories. SharePoint enables the creation of team sites, intranet and extranet portals, wikis, blogs, and social communities.
As a widely used web-based collaborative platform for document management and storage, SharePoint has become a prime target for various cyberattacks, especially those requiring user authentication. These attacks often exploit legitimate credentials to access and manipulate SharePoint environments, leading to data breaches, information theft, and other malicious activities. Verizon’s 2024 Data Breach Investigations Report (DBIR) notes that phishing attacks and compromised credentials are at the root of almost 80% of data breaches. Although vulnerability exploits rose sharply as the preferred attack vector last year, stolen credential use by cybercriminals remains the top attack method today.
Attackers know that breaching Microsoft security can grant them access to thousands of companies. One reason Microsoft is such a high-value target is the broad access its platforms provide. By compromising Microsoft’s platforms, bad actors can gain entry to a company’s email systems, user identities through Active Directory, and cloud environments, enabling them to launch attacks, steal sensitive information, and cause widespread disruptions. Proofpoint recently observed a significant increase in attacks that abuse Microsoft SharePoint infrastructure. In this blog post, we’ll examine what these attacks look like – and how Proofpoint helps to stop them.
What happened?
In this example, Proofpoint identified that threat actors gained access to a legitimate corporate account, uploaded a malicious document, and then shared that document with other corporate contacts connected to the compromised account. Recipients must authenticate to see the document.
Here is a closer look at how the attack unfolded.
1. A supplier’s SharePoint account is compromised. This allows the malicious actor to access the legitimate account and use it to distribute their attack. (Note: The supplier in this scenario is not a Proofpoint customer.)
2. The attacker uploads a document that contains a malicious payload, such as a OneNote file with text that tricks the user into clicking on a malicious URL link.
3. The attacker exploits SharePoint’s ability to share documents with all contacts, using its legitimate infrastructure to distribute the malicious document. They do this by sharing the document with specific recipients and requiring them to authenticate to see the document. (Note: The recipients are Proofpoint customers.)
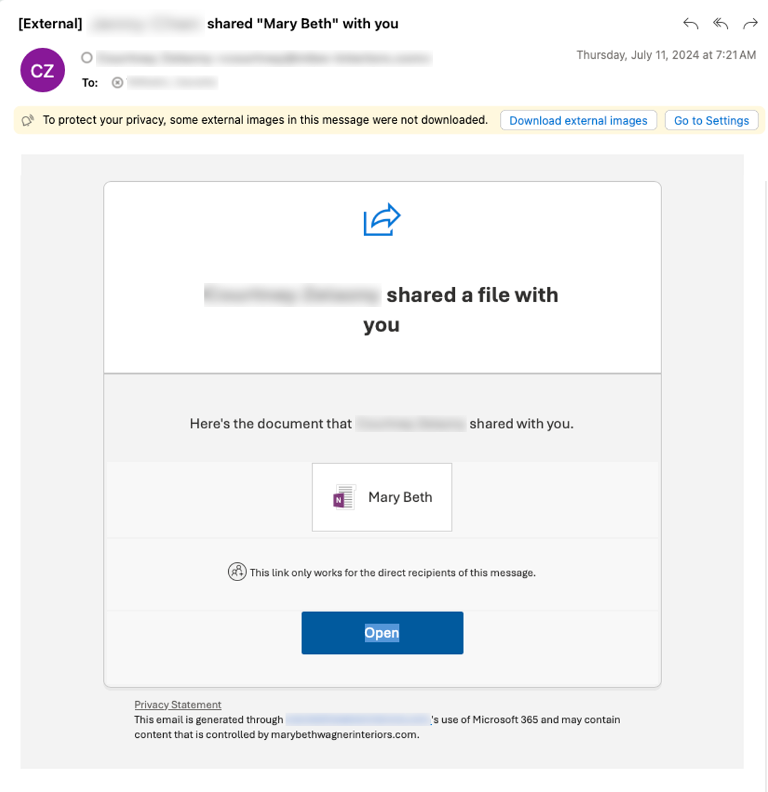
A shared file that contains a malicious payload.
4. The email contains a URL link to a legitimate SharePoint login page. When users enter their credentials, they are exposed to the document shared by the attacker.
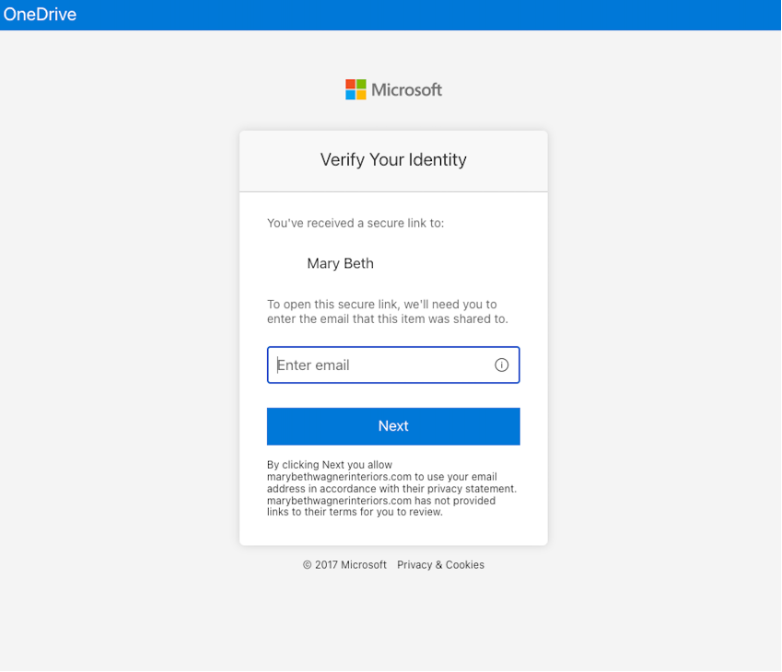
The legitimate SharePoint login page to access the shared file.
5. Once the recipient views the shared document, clicks on the malicious URL inside it and enters their credentials, the attacker steals their credentials. This unauthorised access to SharePoint documents and data can potentially lead to the spread of malware or ransomware.
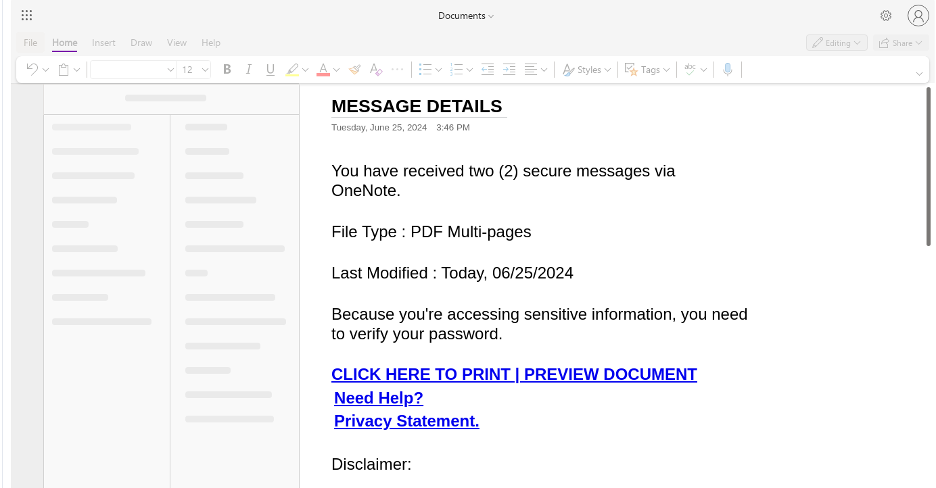
An example of a shared file that contains an embedded phishing URL that attackers use to steal recipients’ credentials after authentication.
6. Other impacts from the SharePoint account takeover include:
- Full control over the compromised account, allowing the attacker to access sensitive data, manipulate documents, and impersonate the user
- Data theft, unauthorised sharing of documents, and the potential for further spear-phishing attacks within the company
- The risk of the attacker making lateral moves within the network to elevate privileges and compromise more accounts and systems
How did Proofpoint prevent this attack?
These multi-pronged SharePoint attacks are notoriously challenging for users to spot and for defenders to stop. Here’s why:
- Threats come from real senders with legitimate accounts and trusted historical relationships.
- Legitimate SharePoint URLs and templates are shared.
- The malicious document is masked behind corporate user authentication.
Proofpoint has seen numerous SharePoint attacks not detected behind other email security solutions in our recent proof of concept (POC) data. These organisations have reported that API-based post-delivery tools are struggling to stop these types of attacks.
While no detection ensemble is 100% perfect, we make it extremely hard for threat actors to evade our email security defences. In this scenario, with the help of our threat research team, we moved quickly to enhance our existing behavioural artificial intelligence (AI) detection indicators to improve the identification and blocking of SharePoint abuse emails.
Our continuously evolving machine learning techniques and behavioural AI play a pivotal role in our ability to detect this type of threat. Our enhanced detection classifier can identify a SharePoint message as malicious based on multiple behavioural clues. These include:
- Volume of messages shared by the same account
- Presence of a SharePoint URL
- Number of customers targeted by the threat actor
- Existence of other malicious messages with similar characteristics
- Customisable text in the message
Our multi-layered detection stack, real-time threat intelligence, and behavioural AI ensure that we continue to increase our SharePoint abuse detection efficacy and deliver on our industry-leading continuous detection and analysis for people protection.
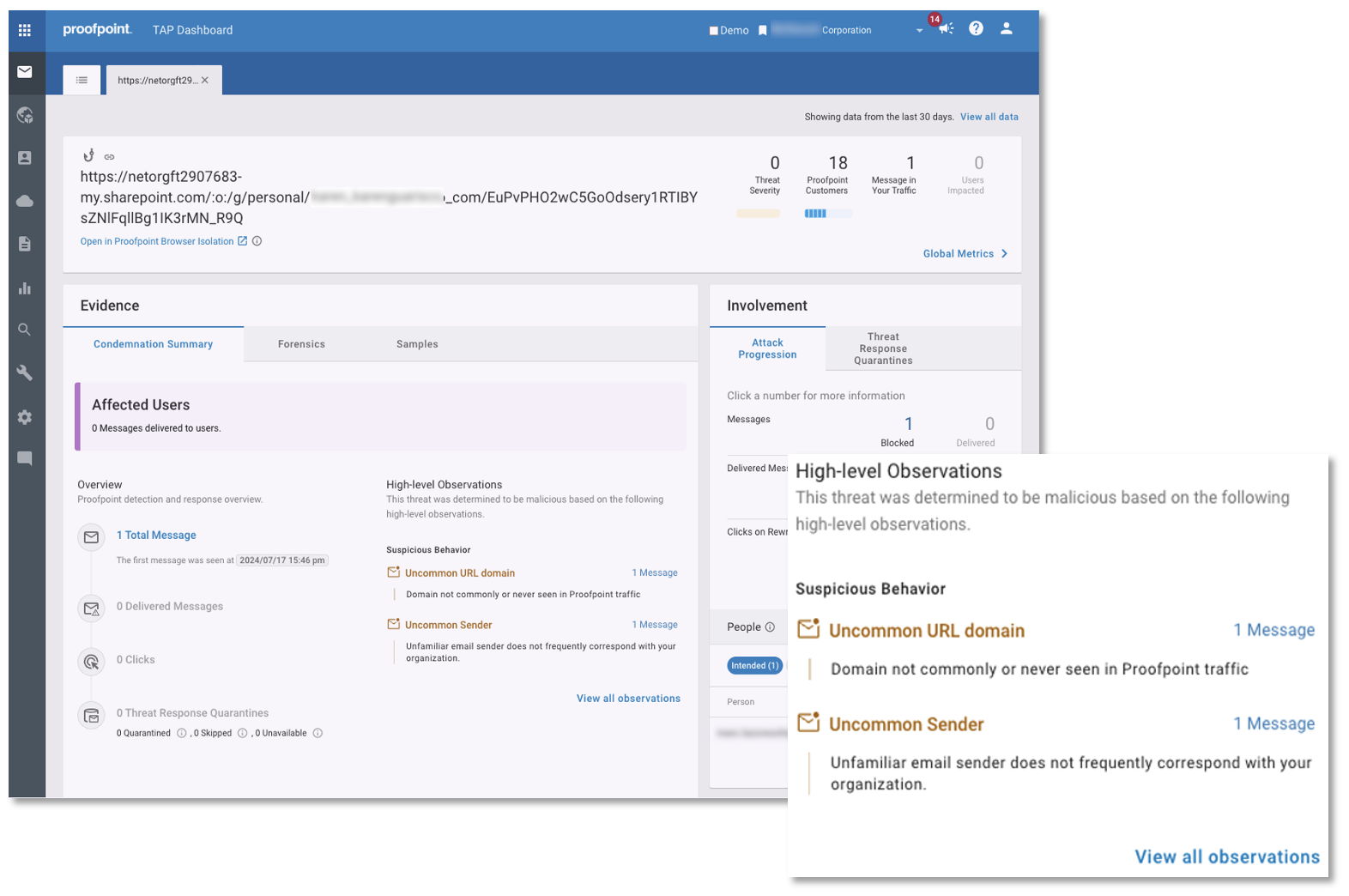
High-level observations in the Proofpoint TAP Dashboard explaining our behavioural analysis and why we deemed the threat to be malicious.
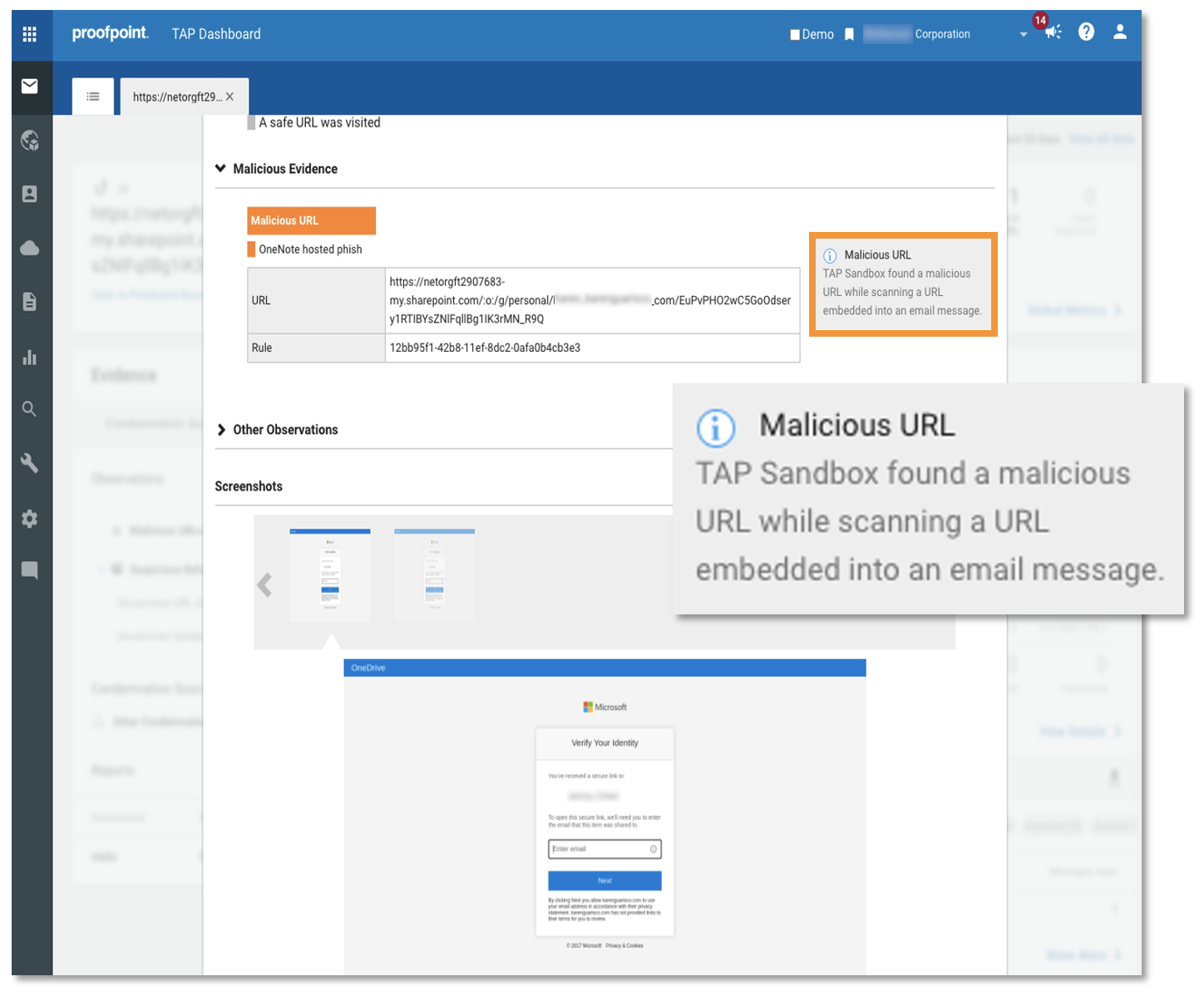
Indicators of compromise and forensics from the threat in TAP Dashboard noting a malicious URL in the SharePoint file.
What are the lessons learned?
Mitigating credential phishing and account takeover attacks requires a proactive, multifaceted approach that combines technology, user education, and robust security policies. Here are some effective strategies:
- Predelivery email protection. The average time for a user to fall for a phishing attack is less than 60 seconds – that’s 60 seconds from when a user opens an email to when they give over their credentials. To keep users safe, it is critical to intercept harmful emails before they arrive in users’ inboxes. Seek a solution that leverages AI-powered machine learning techniques with comprehensive threat intelligence to identify and block sophisticated attacks before malicious messages are delivered.
- Multi-factor authentication (MFA). MFA adds an extra layer of security by requiring users to provide two or more verification factors to gain access to an account. However, it is not a “silver bullet” to prevent account takeover attacks. Businesses must ensure that MFA is enabled for all user accounts, particularly those with access to sensitive information.
- User education and awareness. Regular training programmes can help users to recognise and respond to phishing attempts. Educated users are less likely to fall for phishing scams, which means there is less risk of their credentials being compromised. Consider conducting regular phishing simulations and providing feedback to improve user awareness.
Proofpoint delivers human-centric security
This surge in credential phishing and account takeover abuse of Microsoft SharePoint infrastructure is a good reminder of how the threat landscape evolves all the time. To combat new and advanced cyberthreats, you need to be vigilant and take a proactive stance toward security. Cybercriminals persistently devise new and innovative methods to circumvent your existing security measures.
Proofpoint provides a comprehensive solution that continuously detects and analyses threats. And we do this throughout the entire email delivery lifecycle. Unlike traditional email security tools and API-based point products, Proofpoint Threat Protection offers an AI-driven solution that intercepts 99.99% of threats from pre-delivery to post-delivery and at click-time.
This multi-layered approach can help you mitigate risk. It can also alleviate the burden on your security teams with precise detections and automated remediation workflows. Proofpoint’s unique insights into people risks and extensive threat intelligence allow your teams to focus on the areas with the highest risk.
With Proofpoint, you can achieve end-to-end protection against threats before they reach users’ inboxes so you can better protect your people and business. To learn more about how you can defend against evolving threats, read our solution brief about Proofpoint Threat Protection or register for a Proofpoint Protect event in New York, London, Austin, or Chicago.

