
As much as Insider Threat involves malicious employees trying to steal data, trade secrets and other information, many forget that the Insider Threat is also comprised of employees who make simple mistakes; mistakes that can cost your company millions of dollars. These mistakes include responding to phishing attempts. For context, a phishing email is an attempt to obtain sensitive information such as usernames, passwords, sensitive files, bank account information, money transfers, etc. Phishing attempts usually come in the form of an instant message, email, and sometimes a phone call or text. Messages will contain a link to a fake website or contain a malicious attachment and will attempt to trick the user with social engineering techniques. Aside from the fact that this email appears to be real, these message works because it carries with it a sense of urgency.
For example, it asks the Finance Department to transfer money immediately to a third-party, perhaps outside of the normal chain of events and approvals that lead to a wire transfer. The Finance employee, in a panic, fails to properly assess the potential threat, and begins the paperwork for the transfer. The employee then sends details of the transaction to the C-Level Manager for approval by responding to the false email. The third-party (the criminal acting as the C-Level Manager) will, of course, approve the transaction. Soon, the money is transferred – perhaps to a bank account in Switzerland or the Cayman Islands – never to be seen again.
In 2017, we have seen numerous examples of elaborate phishing plots, but just this week, a sophisticated phishing scam targeted millions of Netflix subscribers. According to the report, the attackers are sending emails to subscribes with the subject line “Your suspension notification” to millions of users. If a user falls for this and clicks on the link, they will be redirected to a fake Netflix page and asked to enter their login credentials and credit card information.
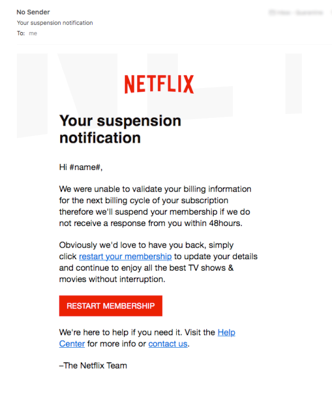
Talk about urgency, with Season 2 of Stranger Things out how could anyone afford to have an interruption in service. Joking aside, this is a prime example of the manipulative strategies attackers will use to trick their victims. Users have to remain vigilant and extremely skeptical of emails asking for this type of information.
How to Prevent Phishing Attacks
Provide Awareness
Awareness training is really going to be key for your employees. Whether it is an all-hands-on-deck meeting, or a high-priority reminder email, your business is at risk if your employees are not given the information or the risk assessment tools to help them look out for these types of scams. There are even companies that offer fun engaging ways to properly train your employees on the dangers of phishing attempts.
Impact Training
Running through a mock scenario where an administrator runs a mock phishing campaign on users, is a way to safety expose employees to phishing scams. These exercises act as a hands-on training mechanisms to present statistics, show what these types of attacks looks like, and educate users. Just remember to get executive sign-off and not to shame people that fall for the attack.
Filter emails and Sandboxing
Solutions are available that will check the safety of emails, attachments, and links. This way, a person will never even have a chance to interact with a suspicious email-borne threat.
Establish a Policy to Handle Phishing Attacks
What happens when you catch an attempt? Develop a policy on how to handle the situation: Should the employee notify a manger, department, or your internal security department?
Who handles the communication chain to the entire organisations? Think through how you can shift to a proactive policy and stay ahead of these attempts on your user base.
Monitor User Activity
Monitoring user activity can help administrators understand exactly what users are doing and alert them to when users are breaking policy. Additionally, attackers like to gain access to user accounts by a phishing attack because it is an easy way in the door. Having technology that can detect unauthorised activity quickly as well as provide ability to respond fast is crucial to stop data loss.
