Quick Warning. This post contains spoilers from Mr. Robot Season 3-Episode 3
In Season 3, episode 3 of Mr. Robot, at the end of the episode, we see the FBI monitoring Elliot's Linux Mint 17.2 system by pulling screen captures. We had to look into how the FBI was able to pull off this type of monitoring. So, let’s take a closer look and see how they pulled this off.
When the scene begins, Elliot boots his system from a live Kali Linux USB. He does this so he can scan his Linux Mint system for a rootkit. Elliot uses rkhunter, an open source rootkit scanner, and the scan results show the system looks clean:
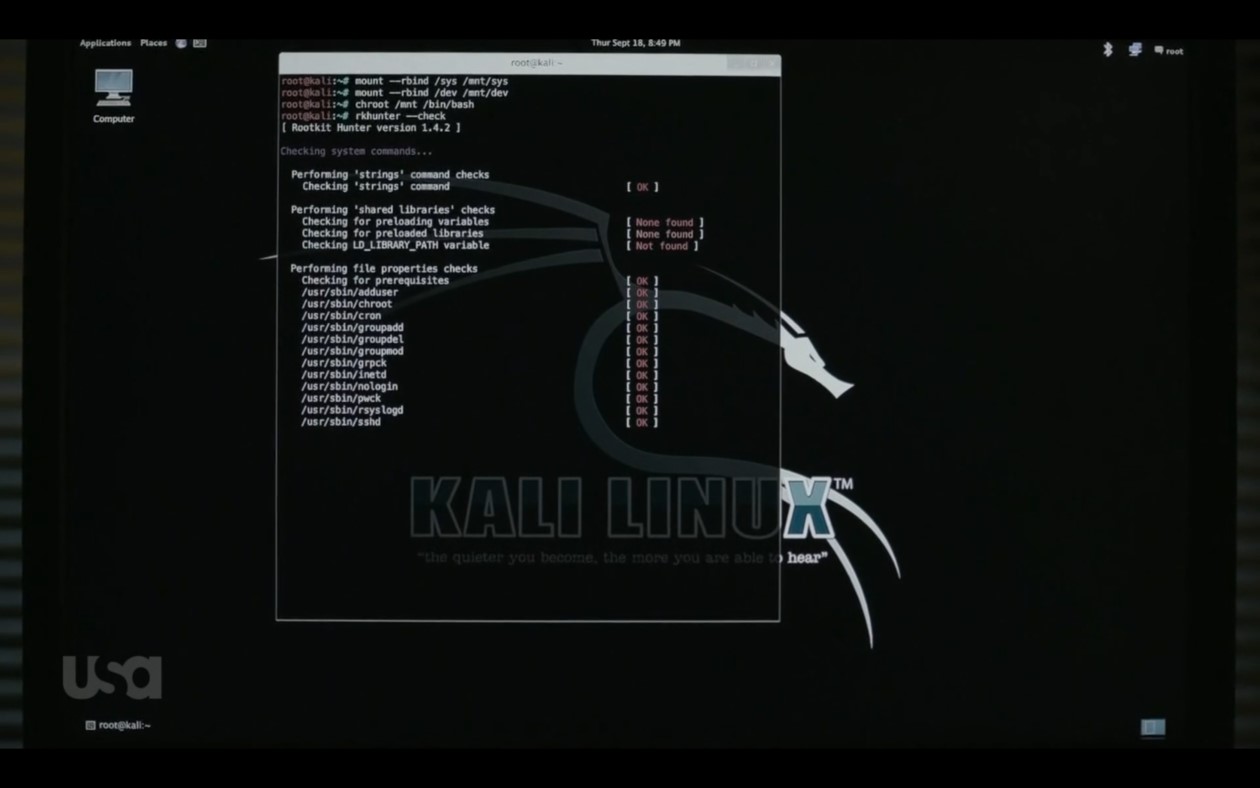
Based on the scan output, it doesn’t seem like a rootkit. So, let’s take a closer look at the terminal in the scene where the FBI is monitoring Elliot’s System:
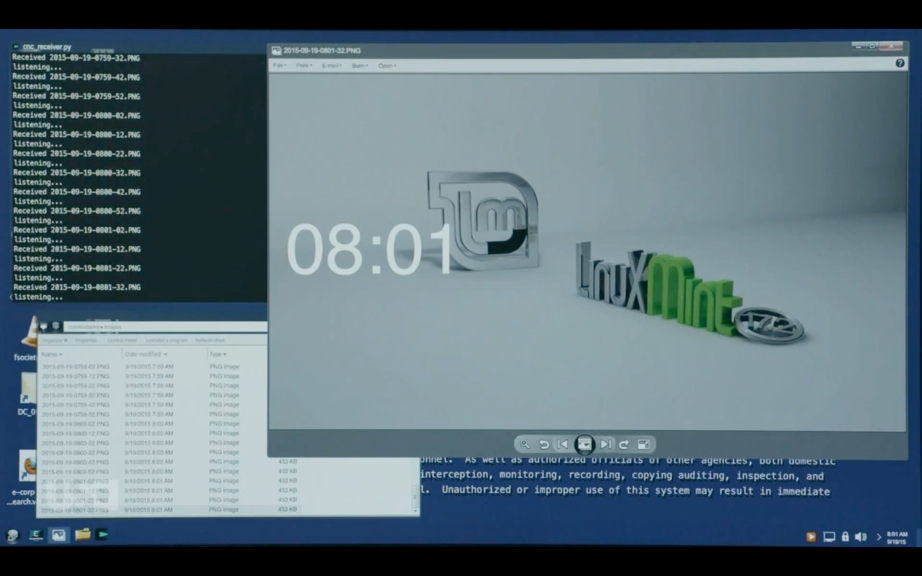
It seems the program is a python script called cnc_receiver.py and this is listening and receiving PNG images every few seconds from Elliot's system. If you look at the folder directory, you see that the screen captures are being outputted to a folder called "Monitor Darkly".
We did a quick google search on monitor darkly, and the first hit takes you to a GitHub page:
https://github.com/RedBalloonShenanigans/MonitorDarkly
Monitor darkly was actually a cool and impressive Command-and-Control proof of concept that was seen at Defcon. The github description reads:
The command-and-control demo shows how an attacker might use the ability to read and modify pixels for malicious purposes. src/cnc.py is a small script that executes a payload located in payloads/cnc.s. cnc.s hooks a few locations in the monitor's firmware in order to receive packets through a hard-coded three-pixel-large area. It can then do several things based on the packet received, including write to memory, execute code, and display images. The modifications it makes won't persist across reboots, but they could be made to do so through writing to the flash.
You can watch the full presentation here:
https://www.youtube.com/watch?v=zvP2FEfOSsk
Monitor darkly was capturing screen captures and required a physical device to capture this information. Elliot must have been able to discover the physical device to figure out the FBI was watching. With this knowledge Elliot then sends out an encrypted email with a link in the body:
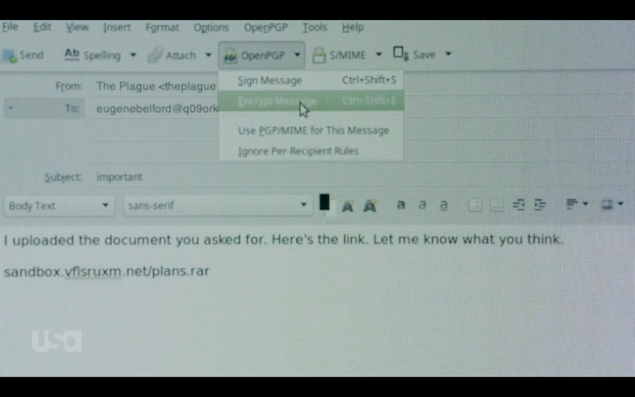
The FBI seems to believe that they have caught Elliot communicating with Tyrell. As they look into this email further, the FBI agents follow the link they see in the images and, in turn, fall for a phishing attempt by Elliot. So Elliot phished the people watching him.
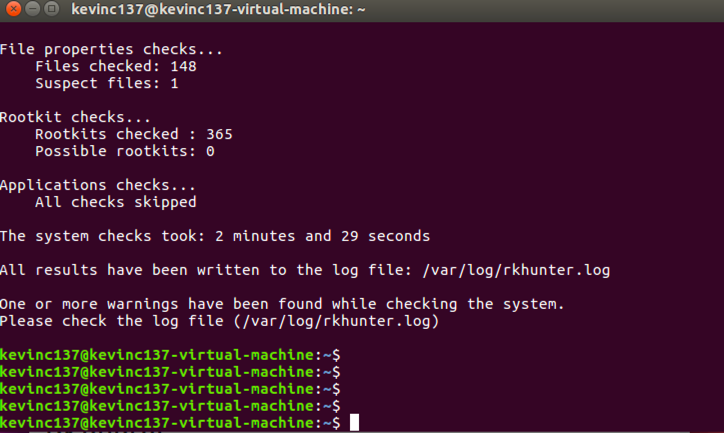
We believe our Proofpoint linux agent would have had the correct metadata to tip off the FBI to what Elliot was actually doing. They would have seen him creating the payload he dropped into the email and every action leading up to the phishing attempt. We also believe our agent would have hidden itself well enough to get past Elliot’s rkhunter scan, here is a scan of an Ubuntu system with our agent on it:
If you’re looking to get comprehensive visibility into your Linux users, put our agent and solution test today.

