Entering its second year in effect, GDPR’s biggest impact has been to raise awareness of customer and user privacy among employees, companies and governments. In our increasingly interconnected world, maintaining employee privacy while also ensuring employees are aware of and adhering to cybersecurity policies is critical for companies, vendors, and governments.
GDPR has provided guidance on what user data is permissible to collect and use and has established requirements regarding breach notification policies. And the regulations have generated significant time and resource investments on the part of many organisations working to comply with the policies. Over the course of the first year in which GDPR was in effect, organisations were generating, on average, two data breach notifications every three minutes according to data collected by the European Data Protection Board. Pause for a second - that rate is for confirmed incidents, which are a subset of all the potential incidents that security teams investigate daily. No wonder, security operations and incident response teams feel so underwater and overworked.
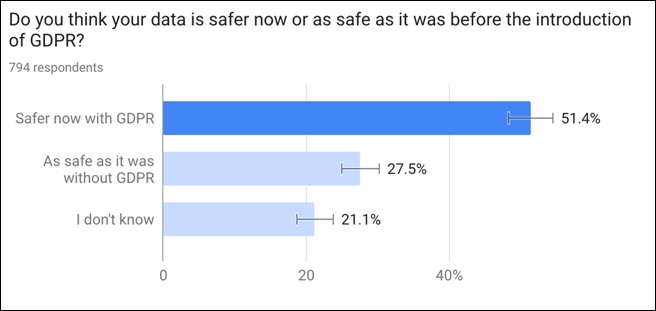
In light of the first anniversary of GDPR, we commissioned a Privacy and Cybersecurity study polling 2,100 respondents in the U.S. and U.K. to understand how users understand the two topics. While GDPR may not be easy for organisations to adhere to, the good news is more than 50% of respondents feel safer after GDPR went live.
We’re witnessing a global movement that has seen countries around the world adopt new privacy laws that are modeled on GDPR. California and Vermont (in the U.S.), Brazil, China, India, Japan, South Korea and Thailand are among the nations and states that have passed new laws, proposed new legislation, or are considering changes to existing privacy and security laws.
GDPR Impact on Cybersecurity
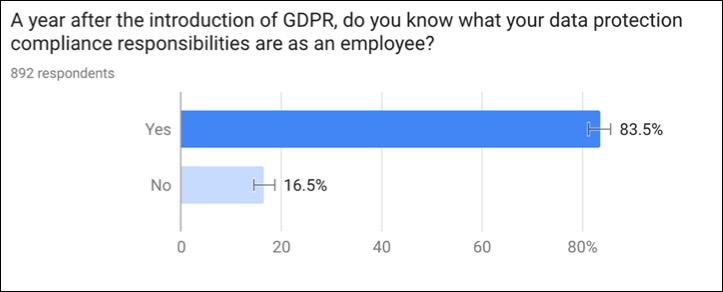
In a business environment, online privacy is the idea that users should have the freedom to avoid unauthorised intrusion into their personal data while doing their job on any device. Cybersecurity is about maintaining the confidentiality, integrity and availability of organisational assets and customer data – including people, information, facilities, intellectual property, and brand reputation. The need to protect online privacy involves using cybersecurity processes and tools. Even in the U.S., many regulations require protecting customer and user data as part of cybersecurity compliance. Thus, online privacy and cybersecurity are very intertwined. This realisation is much further along in the U.K. than in the U.S. Our study shows that in the U.K. 83% of employees and contractors know their data protection and compliance responsibilities as an employee, whereas, 51% of respondents in the U.S. are not aware of any regulations that apply to them.
The greater awareness comes in the form of improved technology to detect threats, greater employee training, and tighter cybersecurity policies. The majority of employees (51%) recognised a mix of all three will protect against information loss. Within the space of insider threats, this maturity is even more pertinent as the problem centers around people. After all, it’s people – employees, contractors and 3rd party vendors – accidentally leaking data while using their technology within the workplace or remotely, or worse, misusing legitimate access to cause harm. The causes are also human in nature – perhaps someone who is disgruntled at work, unaware of security policies, motivated by personal circumstances (often debt) or influenced by external parties.
What is Next for Insider Threat
While some expected a clash between detecting suspicious user and data activity and maintaining employee privacy, GDPR has helped mature insider threat management as a security space.
Years ago, few security tools paid attention to user anonymisation and other features to protect a users' privacy. They simply assumed those accessing security data would be on the "good side". The idea of malicious users within a firm was not recognised. As an aside, Proofpoint is proud that our insider threat management product has kept privacy front and center from the beginning.
Security teams have adapted in two main ways. The first has been to put administrative controls put in place to meet compliance requirements. Many of our customers anonymise all user data in the platform such that an initial alert triage doesn’t require knowing the user’s identity. Once a confirmed investigation, only senior analysts within our customers will unmask the user identity. Our customers usually require that analyst to input a secondary authentication, which maintains an audit trail and controls access to viewing user identities.
The second adaptation has been to scrutinise and communicate the user data collected and used to keep the company safe. A Fortune 500 CISO at one of our recent Customer Advisory Board meetings shared that many days she feels like a marketer wearing a cybersecurity hat! Marketing the value of her security teams and their processes, especially with potentially malicious users within the firm, beyond the C-suite and board is a significant change over the last year for her. In previous years, this topic was only brought up by the board in case of an insider related data breach in the industry.
Impact on United States Companies and Employees
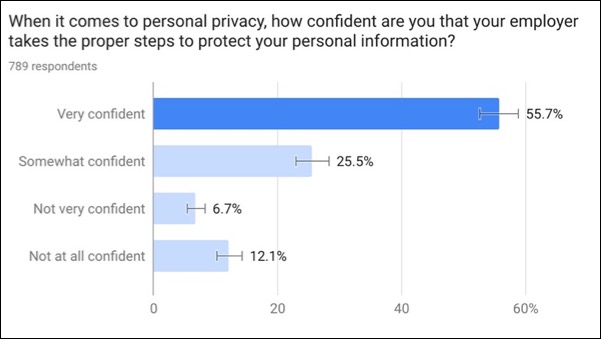
The California Consumer Privacy Act laws are modeled after GDPR in many respects. Other states are following California's lead by either proposing to update their existing laws or bringing significant additions to the table. Increasingly, we are seeing more of our customers communicating the value of implementing insider threat programs to protect users and data as well as cybersecurity practices to employees while also addressing protecting employee privacy. Healthcare, financial services, retail, and technology industries are leading the charge in establishing strong cybersecurity policies and insider threat programs. Even if U.S. employees don’t have GDPR-like regulations across the country, a strong majority (57%) of respondents in the U.S. are recognising their company’s efforts in protecting personal privacy.
GDPR Continues to Demystify Privacy, and Cybersecurity
We can thank GDPR for playing a role in raising the clarion call on privacy and cybersecurity within politics, business, among employees and individual consumers. Grudgingly, security teams will admit that their security policies and practices have strengthened due to the wide-ranging nature of GDPR laws. Privacy and cybersecurity are intertwined. A data breach exposes customer or employee data (sometimes both!), thereby diminishing one's privacy. The balance lies in staying away from draconian security measures that impact user productivity in the name of protecting the firm and its employees. Outside cybersecurity and regulated industries, employees are learning the complexity of maintaining privacy on top of the basics of cybersecurity in our always connected and always on world. At Proofpoint, we take a privacy centric approach to helping our customers to protect their users and IP; we are passionate about showcasing how privacy and cybersecurity are successfully brought together for organisations.

